TABLE OF CONTENTS
1 INTRODUCTION (Page No. - 38)
1.1 STUDY OBJECTIVES
1.2 MARKET DEFINITION
1.2.1 INCLUSIONS AND EXCLUSIONS
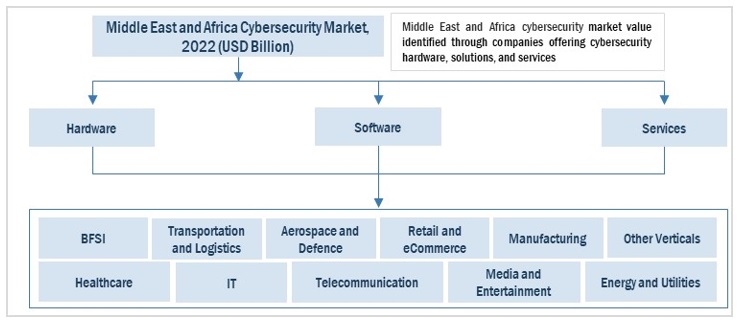
1.3 MARKET SCOPE
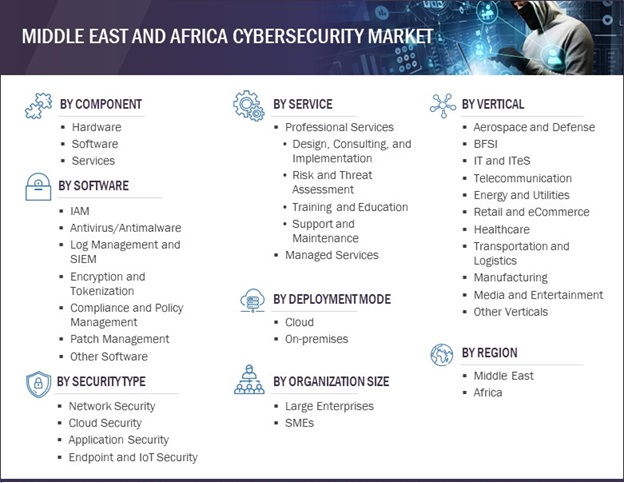
1.3.1 MARKET SEGMENTATION
1.3.2 REGIONS COVERED
1.4 YEARS CONSIDERED
1.5 CURRENCY CONSIDERED
TABLE 1 USD EXCHANGE RATES, 2018–2022
1.6 STAKEHOLDERS
1.7 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY (Page No. - 44)
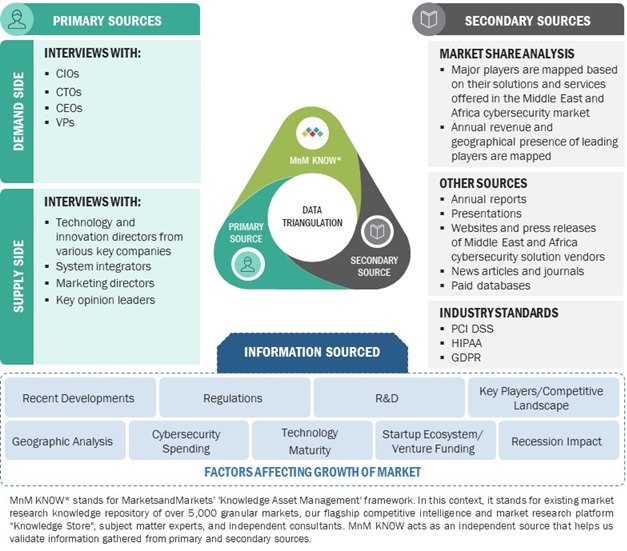
2.1 RESEARCH DATA
FIGURE 1 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: RESEARCH DESIGN
2.1.1 SECONDARY DATA
2.1.2 PRIMARY DATA
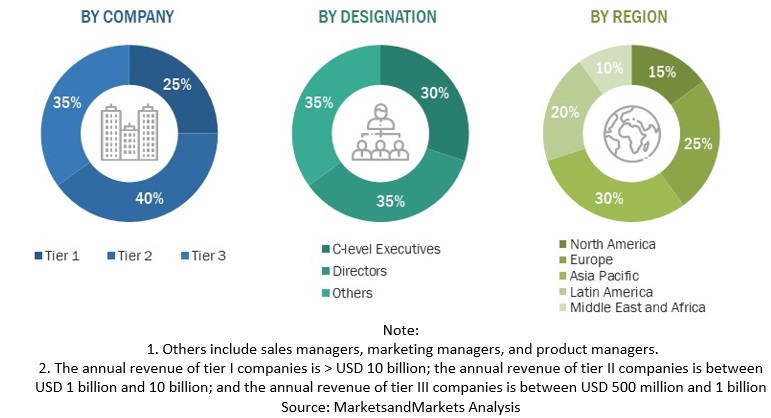
2.1.2.1 Breakup of primary profiles
2.1.2.2 Key industry insights
2.2 DATA TRIANGULATION
FIGURE 2 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: RESEARCH FLOW
2.3 MARKET SIZE ESTIMATION
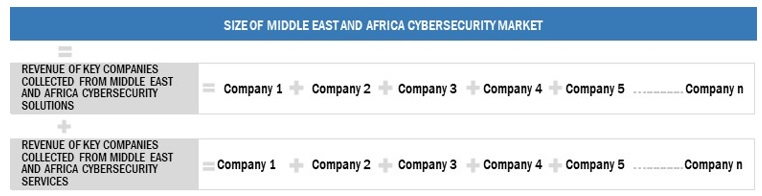
2.3.1 REVENUE ESTIMATES
FIGURE 3 MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 1 (SUPPLY-SIDE): REVENUE OF SOLUTIONS/SERVICES OF MIDDLE EAST AND AFRICA CYBERSECURITY VENDORS
FIGURE 4 MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 1, SUPPLY-SIDE ANALYSIS
FIGURE 5 MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 2, BOTTOM-UP (SUPPLY-SIDE): COLLECTIVE REVENUE FROM SOLUTIONS AND SERVICES OF MIDDLE EAST AND AFRICA CYBERSECURITY VENDORS
2.3.2 DEMAND-SIDE ANALYSIS
FIGURE 6 MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 3, TOP-DOWN (DEMAND-SIDE)
2.4 COMPANY EVALUATION QUADRANT METHODOLOGY
FIGURE 7 COMPANY EVALUATION QUADRANT: CRITERIA WEIGHTAGE
2.5 STARTUP EVALUATION QUADRANT METHODOLOGY
FIGURE 8 STARTUP EVALUATION QUADRANT: CRITERIA WEIGHTAGE
2.6 MARKET FORECAST
TABLE 2 FACTOR ANALYSIS
2.7 RECESSION IMPACT AND RESEARCH ASSUMPTIONS
2.7.1 RECESSION IMPACT
2.7.2 RESEARCH ASSUMPTIONS
2.8 LIMITATIONS
3 EXECUTIVE SUMMARY (Page No. - 57)
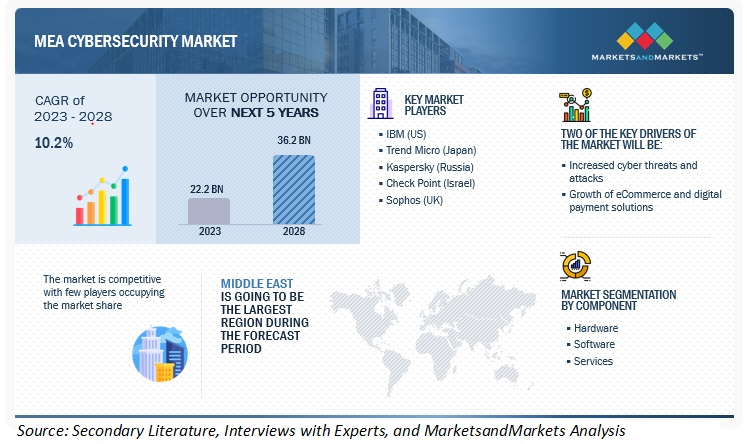
TABLE 3 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET SIZE AND GROWTH, 2023–2028 (USD MILLION, Y-O-Y GROWTH)
FIGURE 9 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET TO WITNESS SIGNIFICANT GROWTH DURING FORECAST PERIOD
FIGURE 10 MIDDLE EAST TO ACCOUNT FOR LARGER MARKET SHARE IN 2023
4 PREMIUM INSIGHTS (Page No. - 60)
4.1 ATTRACTIVE OPPORTUNITIES IN MIDDLE EAST AND AFRICA CYBERSECURITY MARKET
FIGURE 11 GROWING INSTANCES OF TARGET-BASED CYBERATTACKS AND ADOPTION OF CLOUD-BASED CYBERSECURITY SOLUTIONS TO DRIVE MARKET
4.2 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY COMPONENT, 2023
FIGURE 12 SOFTWARE SEGMENT TO HOLD LARGEST MARKET SHARE IN 2023
4.3 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028
FIGURE 13 LOG MANAGEMENT AND SIEM SEGMENT TO HOLD LARGEST MARKET SIZE DURING FORECAST PERIOD
4.4 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028
FIGURE 14 ENDPOINT AND IOT DEVICE SECURITY SEGMENT TO HOLD LARGEST MARKET SIZE DURING FORECAST PERIOD
4.5 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY VERTICAL, 2023–2028
FIGURE 15 AEROSPACE AND DEFENSE SEGMENT TO HOLD LARGEST MARKET SIZE DURING FORECAST PERIOD
4.6 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028
FIGURE 16 MIDDLE EAST TO HOLD LARGER MARKET SIZE DURING FORECAST PERIOD
4.7 MARKET INVESTMENT SCENARIO
FIGURE 17 AFRICA TO EMERGE AS BEST MARKET FOR INVESTMENTS IN NEXT FIVE YEARS
5 MARKET OVERVIEW AND INDUSTRY TRENDS (Page No. - 64)
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
FIGURE 18 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET
5.2.1 DRIVERS
5.2.1.1 Increased cyber threats and attacks
5.2.1.2 Growth of eCommerce and digital payment solutions
5.2.1.3 Stringent regulations and compliance requirements
5.2.1.4 Digital transformation initiatives
5.2.2 RESTRAINTS
5.2.2.1 Lack of awareness and understanding
5.2.2.2 Inadequate infrastructure and lack of skilled professionals
5.2.2.3 Rapidly evolving threat landscape
5.2.3 OPPORTUNITIES
5.2.3.1 Cross-sector collaboration
5.2.3.2 International cooperation
5.2.4 CHALLENGES
5.2.4.1 Limited cybersecurity budgets
5.2.4.2 Insufficient regulatory frameworks
5.3 ECOSYSTEM
FIGURE 19 ECOSYSTEM: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET
5.4 TECHNOLOGY ANALYSIS
5.4.1 ARTIFICIAL INTELLIGENCE/MACHINE LEARNING
5.4.2 BIG DATA ANALYTICS
5.4.3 CLOUD COMPUTING
5.4.4 INTERNET OF THINGS
5.5 REGULATORY IMPLICATIONS
5.5.1 PAYMENT CARD INDUSTRY DATA SECURITY STANDARD
5.5.2 HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT
5.5.3 FEDERAL INFORMATION SECURITY MANAGEMENT ACT
5.5.4 GRAMM-LEACH-BLILEY ACT
5.5.5 SARBANES-OXLEY ACT
5.5.6 INTERNATIONAL ORGANIZATION FOR STANDARDIZATION (ISO) STANDARD 27001
5.5.7 EUROPEAN UNION GENERAL DATA PROTECTION REGULATION
5.5.8 SERVICE ORGANIZATION CONTROL 2 (SOC2)
5.5.9 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 4 LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
5.6 PATENT ANALYSIS
FIGURE 20 PATENT ANALYSIS
5.7 VALUE CHAIN ANALYSIS
FIGURE 21 VALUE CHAIN ANALYSIS
5.8 PORTER’S FIVE FORCES MODEL ANALYSIS
FIGURE 22 PORTER’S FIVE FORCE ANALYSIS
TABLE 5 IMPACT OF PORTER’S FIVE FORCES ON MIDDLE EAST AND AFRICA CYBERSECURITY MARKET
5.8.1 THREAT FROM NEW ENTRANTS
5.8.2 THREAT FROM SUBSTITUTES
5.8.3 BARGAINING POWER OF SUPPLIERS
5.8.4 BARGAINING POWER OF BUYERS
5.8.5 INTENSITY OF COMPETITIVE RIVALRY
5.9 USE CASES
5.9.1 USE CASE 1: SYMANTEC HELPED SAUDI ARAMCO BY PROVIDING COMPREHENSIVE VISIBILITY AND CONTROL OVER IT INFRASTRUCTURE
5.9.2 USE CASE 2: PALO ALTO NETWORKS HELPED SABB BY PROVIDING REAL-TIME THREAT DETECTION AND RESPONSE CAPABILITIES
5.9.3 USE CASE 3: FORTINET’S UNIFIED THREAT MANAGEMENT HELPED NBK PREVENT PHISHING ATTACKS ON ITS BANKING INFRASTRUCTURE
5.9.4 USE CASE 4: MCAFEE ENABLED QATAR AIRWAYS TO ESTABLISH COMPLETE CONTROL OVER ENDPOINT DEVICES
5.10 PRICING ANALYSIS
5.10.1 CYBERSECURITY SOLUTIONS AND SERVICES PRICED ACCORDING TO FOLLOWING METHODS:
5.11 TRENDS AND DISRUPTIONS IMPACTING CUSTOMERS
FIGURE 23 TRENDS AND DISRUPTIONS IMPACTING CUSTOMERS
5.12 KEY STAKEHOLDERS AND BUYING CRITERIA
5.12.1 KEY STAKEHOLDERS IN BUYING PROCESS
FIGURE 24 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS (%)
TABLE 6 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS (%)
5.13 KEY CONFERENCES & EVENTS, 2023–2024
TABLE 7 KEY CONFERENCES & EVENTS, 2023–2024
6 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY COMPONENT (Page No. - 87)
6.1 INTRODUCTION
FIGURE 25 SOFTWARE SEGMENT TO DOMINATE DURING FORECAST PERIOD
TABLE 8 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 9 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
6.2 HARDWARE
6.2.1 DEVELOPMENTS IN HARDWARE DEVICES TO DRIVE MARKET GROWTH
6.2.2 HARDWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 10 HARDWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 11 HARDWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
6.3 SOFTWARE
6.3.1 SMART TECHNOLOGIES FOR MITIGATING ADVANCED CYBERATTACKS TO PROPEL MARKET
6.3.2 SOFTWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 12 SOFTWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 13 SOFTWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
6.4 SERVICES
6.4.1 HUGE PRESENCE OF CYBERSECURITY SERVICE PROVIDERS TO BOOST MARKET
6.4.2 SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 14 SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 15 SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SOFTWARE (Page No. - 94)
7.1 INTRODUCTION
FIGURE 26 LOG MANAGEMENT AND SIEM SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
TABLE 16 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 17 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
7.2 IAM
7.2.1 REDUCTION IN RISK OF UNAUTHORIZED ACCESS TO SECURE CRITICAL SYSTEMS TO BOOST MARKET
7.2.2 IAM: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 18 IAM: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 19 IAM: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7.3 ANTIVIRUS/ANTIMALWARE
7.3.1 INNOVATIVE SOLUTIONS TO OFFER SECURED TEST ENVIRONMENT TO PROPEL MARKET
7.3.2 ANTIVIRUS/ANTIMALWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 20 ANTIVIRUS/ANTIMALWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 21 ANTIVIRUS/ANTIMALWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7.4 LOG MANAGEMENT AND SIEM
7.4.1 360-DEGREE APPROACH TO FIGHT AGAINST CYBER THREATS TO BOOST MARKET
7.4.2 LOG MANAGEMENT AND SIEM: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 22 LOG MANAGEMENT AND SIEM: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 23 LOG MANAGEMENT AND SIEM: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7.5 FIREWALL
7.5.1 EXTENSIVE ADOPTION OF FIREWALL ACROSS INDUSTRIES TO BOOST MARKET
7.5.2 FIREWALL: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 24 FIREWALL: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 25 FIREWALL: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7.6 ENCRYPTION AND TOKENIZATION
7.6.1 TO SAFEGUARD SENSITIVE DATA OUTSIDE INTERNAL SYSTEMS TO PROPEL MARKET
7.6.2 ENCRYPTION AND TOKENIZATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 26 ENCRYPTION AND TOKENIZATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 27 ENCRYPTION AND TOKENIZATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7.7 COMPLIANCE AND POLICY MANAGEMENT
7.7.1 STRICT LAWS AND REGULATIONS FOR HELPING COMPANIES IDENTIFY CRITICAL IT ASSETS TO DRIVE MARKET
7.7.2 COMPLIANCE AND POLICY MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 28 COMPLIANCE AND POLICY MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 29 COMPLIANCE AND POLICY MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7.8 PATCH MANAGEMENT
7.8.1 SHORT-TERM SOLUTIONS FOR DETECTION AND PREVENTION TO BOOST MARKET
7.8.2 PATCH MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 30 PATCH MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 31 PATCH MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
7.9 OTHER SOFTWARE
TABLE 32 OTHER SOFTWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 33 OTHER SOFTWARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
8 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SERVICE (Page No. - 107)
8.1 INTRODUCTION
FIGURE 27 PROFESSIONAL SERVICES SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
TABLE 34 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 35 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
8.2 PROFESSIONAL SERVICES
8.2.1 EXTENSIVE PRESENCE OF SERVICE PROVIDERS FOR FACILITATING SECURITY CONCERNS TO BOOST MARKET
8.2.2 PROFESSIONAL SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 36 SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 37 SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 38 PROFESSIONAL SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 39 PROFESSIONAL SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
8.2.3 DESIGN, CONSULTING, AND IMPLEMENTATION
TABLE 40 DESIGN, CONSULTING, AND IMPLEMENTATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 41 DESIGN, CONSULTING, AND IMPLEMENTATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
8.2.4 RISK AND THREAT MANAGEMENT
TABLE 42 RISK AND THREAT MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 43 RISK AND THREAT MANAGEMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
8.2.5 TRAINING AND EDUCATION
TABLE 44 TRAINING AND EDUCATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 45 TRAINING AND EDUCATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
8.2.6 SUPPORT AND MAINTENANCE
TABLE 46 SUPPORT AND MAINTENANCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 47 SUPPORT AND MAINTENANCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
8.3 MANAGED SERVICES
8.3.1 HIGHER ADOPTION OF SERVICES DUE TO HIGH COST AND RESOURCE CONSTRAINTS TO DRIVE MARKET
8.3.2 MANAGED SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 48 MANAGED SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 49 MANAGED SERVICES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
9 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SECURITY TYPE (Page No. - 116)
9.1 INTRODUCTION
FIGURE 28 APPLICATION SECURITY SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
TABLE 50 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 51 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
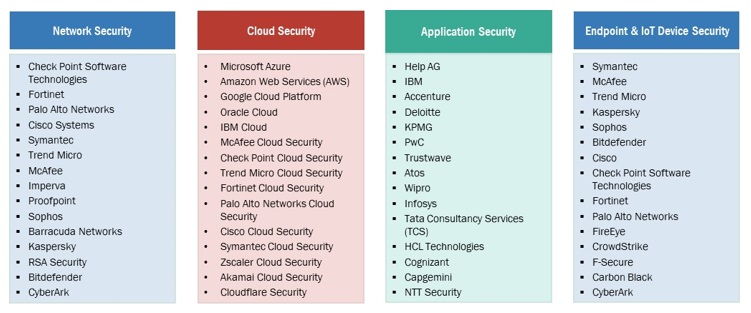
9.2 NETWORK SECURITY
9.2.1 INCREASING BYOD TREND TO GENERATE GREATER DEMAND FOR CYBERSECURITY SOLUTIONS
9.2.2 NETWORK SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 52 NETWORK SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 53 NETWORK SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
9.3 CLOUD SECURITY
9.3.1 INCREASED ADOPTION OF CLOUD SOLUTIONS ACROSS ENTERPRISES TO DRIVE DEMAND FOR CYBERSECURITY SOLUTIONS
9.3.2 CLOUD SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 54 CLOUD SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 55 CLOUD SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
9.4 APPLICATION SECURITY
9.4.1 RISING DEMAND FOR CYBERSECURITY SOLUTIONS TO REDUCE ATTACKS ON BUSINESS-SENSITIVE APPLICATIONS
9.4.2 APPLICATION SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 56 APPLICATION SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 57 APPLICATION SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
9.5 ENDPOINT AND IOT SECURITY
9.5.1 INCREASING NUMBER OF MOBILE DEVICES EXPOSING NETWORKS VULNERABLE TO CYBERATTACKS TO DRIVE MARKET
9.5.2 ENDPOINT AND IOT SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 58 ENDPOINT AND IOT SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 59 ENDPOINT AND IOT SECURITY: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
10 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY DEPLOYMENT MODE (Page No. - 124)
10.1 INTRODUCTION
FIGURE 29 ON-PREMISES SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
TABLE 60 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 61 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
10.2 CLOUD
10.2.1 GROWING ADOPTION OF CLOUD DEPLOYMENT MODE DUE TO EASY MAINTENANCE AND UPGRADE
10.2.2 CLOUD: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 62 CLOUD: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 63 CLOUD: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
10.3 ON-PREMISES
10.3.1 ON-PREMISES DEPLOYMENT TO MAKE ADOPTION OF CYBERSECURITY SOLUTIONS FLEXIBLE
10.3.2 ON-PREMISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 64 ON-PREMISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 65 ON-PREMISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
11 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY ORGANIZATION SIZE (Page No. - 129)
11.1 INTRODUCTION
FIGURE 30 LARGE ENTERPRISES SEGMENT TO HOLD LARGER MARKET SIZE DURING FORECAST PERIOD
TABLE 66 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 67 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
11.2 SMALL AND MEDIUM-SIZED ENTERPRISES
11.2.1 DIGITAL TRANSFORMATION AND LEVERAGED CLOUD COMPUTING TO HELP SMALL AND MEDIUM-SIZED ENTERPRISES GROW
11.2.2 SMALL AND MEDIUM-SIZED ENTERPRISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 68 SMALL AND MEDIUM-SIZED ENTERPRISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 69 SMALL AND MEDIUM-SIZED ENTERPRISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
11.3 LARGE ENTERPRISES
11.3.1 LARGE ORGANIZATIONS TO FACILITATE PRIVILEGED ACCESS TO SERVERS AND WEB APPLICATIONS
11.3.2 LARGE ENTERPRISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 70 LARGE ENTERPRISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 71 LARGE ENTERPRISES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY VERTICAL (Page No. - 134)
12.1 INTRODUCTION
FIGURE 31 AEROSPACE AND DEFENSE VERTICAL TO ACCOUNT FOR LARGEST MARKET SIZE DURING FORECAST PERIOD
TABLE 72 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 73 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
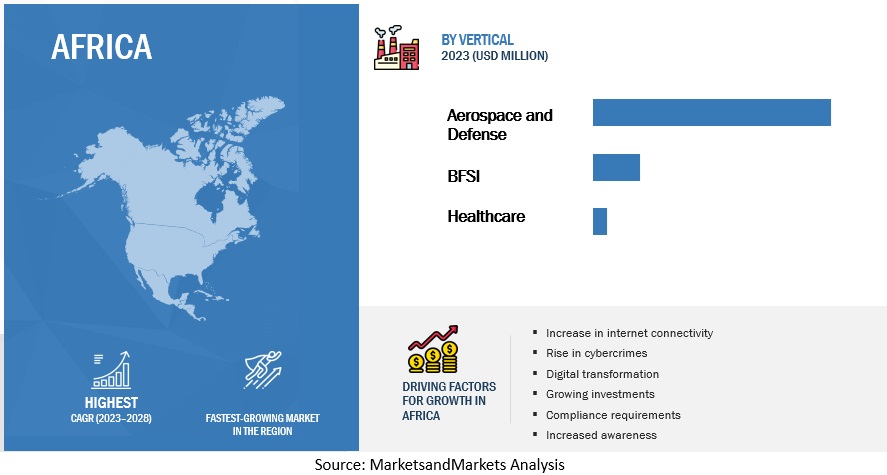
12.2 AEROSPACE AND DEFENSE
12.2.1 INCREASING DIGITALIZATION TO LEAD TO GREATER ATTACKS ON CONFIDENTIAL AND SENSITIVE DATA
12.2.2 AEROSPACE AND DEFENSE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 74 AEROSPACE AND DEFENSE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 75 AEROSPACE AND DEFENSE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.3 BANKING, FINANCIAL SERVICES, AND INSURANCE
12.3.1 RISING DEMAND FOR NEW AND IMPROVED FINANCIAL PRODUCTS TO PRIORITIZE ADOPTION OF CYBERSECURITY SOLUTIONS
12.3.2 BANKING, FINANCIAL SERVICES, AND INSURANCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 76 BANKING, FINANCIAL SERVICES, AND INSURANCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 77 BANKING, FINANCIAL SERVICES, AND INSURANCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.4 IT AND ITES
12.4.1 PRESENCE OF LARGE AMOUNTS OF DATA MAKING ORGANIZATIONS PRONE TO CYBERATTACKS TO BOOST MARKET
12.4.2 IT AND ITES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 78 IT AND ITES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 79 IT AND ITES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.5 HEALTHCARE
12.5.1 SECURITY BREACHES AND UNAUTHORIZED ACCESS TO PERSONAL PATIENT INFORMATION TO CREATE DEMAND FOR SOLUTIONS
12.5.2 HEALTHCARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 80 HEALTHCARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 81 HEALTHCARE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.6 RETAIL AND ECOMMERCE
12.6.1 NEED TO PROTECT STORES, WAREHOUSES, AND FULFILMENT CENTERS FROM THREATS TO DRIVE MARKET
12.6.2 RETAIL AND ECOMMERCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 82 RETAIL AND ECOMMERCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 83 RETAIL AND ECOMMERCE: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.7 MANUFACTURING
12.7.1 CYBERSECURITY SOLUTIONS AND SERVICES TO SMOOTHEN BUSINESS FUNCTIONS IN MANUFACTURING ORGANIZATIONS
12.7.2 MANUFACTURING: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 84 MANUFACTURING: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 85 MANUFACTURING: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.8 ENERGY AND UTILITIES
12.8.1 RAPID ADOPTION OF INNOVATIVE TECHNOLOGIES TO ENABLE MORE FLEXIBILITY AND SECURITY
12.8.2 ENERGY AND UTILITIES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 86 ENERGY AND UTILITIES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 87 ENERGY AND UTILITIES: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.9 TELECOMMUNICATION
12.9.1 CYBERSECURITY SOLUTIONS AND SERVICES TO HELP ORGANIZATIONS MANAGE RISKS AND COMPLIANCES EFFICIENTLY
12.9.2 TELECOMMUNICATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 88 TELECOMMUNICATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 89 TELECOMMUNICATION: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.10 TRANSPORTATION AND LOGISTICS
12.10.1 TECHNOLOGIES TO PROVIDE INNOVATIVE SERVICES RELATED TO DIFFERENT MODES OF TRANSPORT AND TRAFFIC MANAGEMENT
12.10.2 TRANSPORTATION AND LOGISTICS: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 90 TRANSPORTATION AND LOGISTICS: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 91 TRANSPORTATION AND LOGISTICS: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.11 MEDIA AND ENTERTAINMENT
12.11.1 NEW DIGITAL TECHNOLOGIES TO DRIVE DEMAND FOR CYBERSECURITY SOLUTIONS
12.11.2 MEDIA AND ENTERTAINMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
TABLE 92 MEDIA AND ENTERTAINMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 93 MEDIA AND ENTERTAINMENT: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
12.12 OTHER VERTICALS
TABLE 94 OTHER VERTICALS: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 95 OTHER VERTICALS: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
13 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION (Page No. - 151)
13.1 INTRODUCTION
FIGURE 32 AFRICA TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
TABLE 96 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 97 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
13.2 MIDDLE EAST
13.2.1 MIDDLE EAST: MIDDLE EAST AND AFRICA CYBERSECURITY MARKET DRIVERS
13.2.2 MIDDLE EAST: RECESSION IMPACT
TABLE 98 MIDDLE EAST: REGULATORY LANDSCAPE
TABLE 99 MIDDLE EAST: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 100 MIDDLE EAST: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 101 MIDDLE EAST: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 102 MIDDLE EAST: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 103 MIDDLE EAST: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 104 MIDDLE EAST: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 105 MIDDLE EAST: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 106 MIDDLE EAST: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 107 MIDDLE EAST: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 108 MIDDLE EAST: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 109 MIDDLE EAST: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 110 MIDDLE EAST: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 111 MIDDLE EAST: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 112 MIDDLE EAST: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 113 MIDDLE EAST: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 114 MIDDLE EAST: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
TABLE 115 MIDDLE EAST: CYBERSECURITY MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
TABLE 116 MIDDLE EAST: CYBERSECURITY MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
13.2.3 BAHRAIN
13.2.3.1 Rising demand for cybersecurity to strengthen critical infrastructure and build resilient digital ecosystem
TABLE 117 BAHRAIN: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 118 BAHRAIN: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 119 BAHRAIN: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 120 BAHRAIN: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 121 BAHRAIN: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 122 BAHRAIN: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 123 BAHRAIN: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 124 BAHRAIN: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 125 BAHRAIN: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 126 BAHRAIN: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 127 BAHRAIN: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 128 BAHRAIN: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 129 BAHRAIN: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 130 BAHRAIN: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 131 BAHRAIN: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 132 BAHRAIN: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.4 EGYPT
13.2.4.1 Presence of major vendors to drive demand for cybersecurity solutions
TABLE 133 EGYPT: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 134 EGYPT: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 135 EGYPT: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 136 EGYPT: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 137 EGYPT: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 138 EGYPT: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 139 EGYPT: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 140 EGYPT: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 141 EGYPT: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 142 EGYPT: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 143 EGYPT: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 144 EGYPT: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 145 EGYPT: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 146 EGYPT: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 147 EGYPT: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 148 EGYPT: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.5 ISRAEL
13.2.5.1 Advancement in cybersecurity industry through strategies and partnerships to propel market
TABLE 149 ISRAEL: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 150 ISRAEL: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 151 ISRAEL: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 152 ISRAEL: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 153 ISRAEL: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 154 ISRAEL: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 155 ISRAEL: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 156 ISRAEL: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 157 ISRAEL: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 158 ISRAEL: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 159 ISRAEL: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 160 ISRAEL: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 161 ISRAEL: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 162 ISRAEL: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 163 ISRAEL: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 164 ISRAEL: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.6 KUWAIT
13.2.6.1 Rising cyber threats in government sector to propel market
TABLE 165 KUWAIT: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 166 KUWAIT: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 167 KUWAIT: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 168 KUWAIT: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 169 KUWAIT: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 170 KUWAIT: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 171 KUWAIT: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 172 KUWAIT: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 173 KUWAIT: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 174 KUWAIT: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 175 KUWAIT: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 176 KUWAIT: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 177 KUWAIT: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 178 KUWAIT: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 179 KUWAIT: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 180 KUWAIT: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.7 OMAN
13.2.7.1 Rising instances of sabotaging critical infrastructure in oil and gas industry to boost market
TABLE 181 OMAN: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 182 OMAN: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 183 OMAN: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 184 OMAN: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 185 OMAN: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 186 OMAN: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 187 OMAN: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 188 OMAN: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 189 OMAN: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 190 OMAN: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 191 OMAN: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 192 OMAN: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 193 OMAN: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 194 OMAN: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 195 OMAN: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 196 OMAN: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.8 QATAR
13.2.8.1 Government initiatives and adoption of cybersecurity solutions in critical sectors to drive market
TABLE 197 QATAR: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 198 QATAR: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 199 QATAR: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 200 QATAR: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 201 QATAR: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 202 QATAR: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 203 QATAR: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 204 QATAR: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 205 QATAR: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 206 QATAR: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 207 QATAR: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 208 QATAR: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 209 QATAR: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 210 QATAR: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 211 QATAR: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 212 QATAR: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.9 KSA
13.2.9.1 Growing investment in cybersecurity solutions for securing oil infrastructure to boost market
TABLE 213 KSA: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 214 KSA: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 215 KSA: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 216 KSA: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 217 KSA: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 218 KSA: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 219 KSA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 220 KSA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 221 KSA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 222 KSA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 223 KSA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 224 KSA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 225 KSA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 226 KSA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 227 KSA: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 228 KSA: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.10 TURKEY
13.2.10.1 Rising efforts for enhancing cyber defense techniques to propel market
TABLE 229 TURKEY: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 230 TURKEY: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 231 TURKEY: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 232 TURKEY: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 233 TURKEY: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 234 TURKEY: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 235 TURKEY: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 236 TURKEY: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 237 TURKEY: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 238 TURKEY: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 239 TURKEY: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 240 TURKEY: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 241 TURKEY: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 242 TURKEY: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 243 TURKEY: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 244 TURKEY: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.11 UAE
13.2.11.1 Increasing demand for cybersecurity measures and response to cyber threats to drive market
TABLE 245 UAE: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 246 UAE: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 247 UAE: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 248 UAE: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 249 UAE: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 250 UAE: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 251 UAE: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 252 UAE: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 253 UAE: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 254 UAE: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 255 UAE: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 256 UAE: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 257 UAE: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 258 UAE: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 259 UAE: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 260 UAE: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.2.12 REST OF MIDDLE EAST
TABLE 261 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 262 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 263 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 264 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 265 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 266 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 267 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 268 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 269 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 270 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 271 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 272 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 273 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 274 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 275 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 276 REST OF MIDDLE EAST: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.3 AFRICA
13.3.1 AFRICA: CYBERSECURITY MARKET DRIVERS
13.3.2 AFRICA: RECESSION IMPACT
TABLE 277 AFRICA: REGULATORY LANDSCAPE
TABLE 278 AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 279 AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 280 AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 281 AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 282 AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 283 AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 284 AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 285 AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 286 AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 287 AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 288 AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 289 AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 290 AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 291 AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 292 AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 293 AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
TABLE 294 AFRICA: CYBERSECURITY MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
TABLE 295 AFRICA: CYBERSECURITY MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
13.3.3 NORTHERN AFRICA
TABLE 296 NORTHERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 297 NORTHERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 298 NORTHERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 299 NORTHERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 300 NORTHERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 301 NORTHERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 302 NORTHERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 303 NORTHERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 304 NORTHERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 305 NORTHERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 306 NORTHERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 307 NORTHERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 308 NORTHERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 309 NORTHERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 310 NORTHERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 311 NORTHERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.3.4 WESTERN AFRICA
TABLE 312 WESTERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 313 WESTERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 314 WESTERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 315 WESTERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 316 WESTERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 317 WESTERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 318 WESTERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 319 WESTERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 320 WESTERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 321 WESTERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 322 WESTERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 323 WESTERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 324 WESTERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 325 WESTERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 326 WESTERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 327 WESTERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.3.5 CENTRAL AFRICA
TABLE 328 CENTRAL AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 329 CENTRAL AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 330 CENTRAL AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 331 CENTRAL AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 332 CENTRAL AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 333 CENTRAL AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 334 CENTRAL AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 335 CENTRAL AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 336 CENTRAL AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 337 CENTRAL AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 338 CENTRAL AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 339 CENTRAL AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 340 CENTRAL AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 341 CENTRAL AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 342 CENTRAL AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 343 CENTRAL AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.3.6 EASTERN AFRICA
TABLE 344 EASTERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 345 EASTERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 346 EASTERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 347 EASTERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 348 EASTERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 349 EASTERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 350 EASTERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 351 EASTERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 352 EASTERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 353 EASTERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 354 EASTERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 355 EASTERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 356 EASTERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 357 EASTERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 358 EASTERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 359 EASTERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13.3.7 SOUTHERN AFRICA
TABLE 360 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2017–2022 (USD MILLION)
TABLE 361 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY COMPONENT, 2023–2028 (USD MILLION)
TABLE 362 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2017–2022 (USD MILLION)
TABLE 363 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY SOFTWARE, 2023–2028 (USD MILLION)
TABLE 364 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 365 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 366 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2017–2022 (USD MILLION)
TABLE 367 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY PROFESSIONAL SERVICE, 2023–2028 (USD MILLION)
TABLE 368 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2017–2022 (USD MILLION)
TABLE 369 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
TABLE 370 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 371 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 372 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
TABLE 373 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
TABLE 374 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 375 SOUTHERN AFRICA: CYBERSECURITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
14 COMPETITIVE LANDSCAPE (Page No. - 264)
14.1 OVERVIEW
14.2 REVENUE ANALYSIS OF LEADING PLAYERS
FIGURE 33 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: REVENUE ANALYSIS
14.3 MARKET SHARE ANALYSIS OF TOP PLAYERS
TABLE 376 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: DEGREE OF COMPETITION
14.4 HISTORICAL REVENUE ANALYSIS
FIGURE 34 HISTORICAL FIVE-YEAR REVENUE ANALYSIS OF LEADING MIDDLE EAST AND AFRICA CYBERSECURITY PROVIDERS
14.5 RANKING OF KEY PLAYERS IN MIDDLE EAST AND AFRICA CYBERSECURITY MARKET
FIGURE 35 KEY PLAYERS RANKING
14.6 KEY COMPANY EVALUATION QUADRANT
FIGURE 36 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: KEY COMPANY EVALUATION QUADRANT
14.6.1 STARS
14.6.2 EMERGING LEADERS
14.6.3 PERVASIVE PLAYERS
14.6.4 PARTICIPANTS
14.7 COMPETITIVE BENCHMARKING
14.7.1 KEY COMPANY EVALUATION QUADRANT
TABLE 377 REGION FOOTPRINT OF KEY COMPANIES
14.7.2 EVALUATION CRITERIA OF SMES/STARTUPS
TABLE 378 LIST OF STARTUPS/SMES
TABLE 379 REGIONAL FOOTPRINT OF SMES/STARTUP COMPANIES
14.8 SME/STARTUP EVALUATION QUADRANT
FIGURE 37 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: STARTUP/SME EVALUATION QUADRANT
14.8.1 PROGRESSIVE COMPANIES
14.8.2 RESPONSIVE COMPANIES
14.8.3 DYNAMIC COMPANIES
14.8.4 STARTING BLOCKS
14.9 COMPETITIVE SCENARIO AND TRENDS
14.9.1 PRODUCT LAUNCHES AND ENHANCEMENTS
TABLE 380 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: PRODUCT LAUNCHES AND ENHANCEMENTS, 2020–2023
14.9.2 DEALS
TABLE 381 MIDDLE EAST AND AFRICA CYBERSECURITY MARKET: DEALS, 2020–2023
15 COMPANY PROFILES (Page No. - 287)
15.1 KEY PLAYERS
(Business Overview, Products/Solutions/Services offered, Recent Developments, MnM View)*
15.1.1 IBM
TABLE 382 IBM: BUSINESS OVERVIEW
FIGURE 38 IBM: COMPANY SNAPSHOT
TABLE 383 IBM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 384 IBM: PRODUCT LAUNCHES
TABLE 385 IBM: DEALS
15.1.2 CISCO
TABLE 386 CISCO: BUSINESS OVERVIEW
FIGURE 39 CISCO: COMPANY SNAPSHOT
TABLE 387 CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 388 CISCO: PRODUCT LAUNCHES
TABLE 389 CISCO: DEALS
15.1.3 PALO ALTO NETWORKS
TABLE 390 PALO ALTO NETWORKS: BUSINESS OVERVIEW
FIGURE 40 PALO ALTO NETWORKS: COMPANY SNAPSHOT
TABLE 391 PALO ALTO NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 392 PALO ALTO NETWORKS: PRODUCT LAUNCHES
TABLE 393 PALO ALTO NETWORKS: DEALS
15.1.4 CHECK POINT
TABLE 394 CHECK POINT: BUSINESS OVERVIEW
FIGURE 41 CHECK POINT: COMPANY SNAPSHOT
TABLE 395 CHECK POINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 396 CHECK POINT: PRODUCT LAUNCHES
TABLE 397 CHECK POINT: DEALS
15.1.5 TREND MICRO
TABLE 398 TREND MICRO: BUSINESS OVERVIEW
FIGURE 42 TREND MICRO: COMPANY SNAPSHOT
TABLE 399 TREND MICRO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 400 TREND MICRO: PRODUCT LAUNCHES
TABLE 401 TREND MICRO: DEALS
TABLE 402 TREND MICRO: OTHERS
15.1.6 FORTINET
TABLE 403 FORTINET: BUSINESS OVERVIEW
FIGURE 43 FORTINET: COMPANY SNAPSHOT
TABLE 404 FORTINET: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 405 FORTINET: PRODUCT LAUNCHES
TABLE 406 FORTINET: DEALS
15.1.7 NORTONLIFELOCK
TABLE 407 NORTONLIFELOCK: BUSINESS OVERVIEW
FIGURE 44 NORTONLIFELOCK: COMPANY SNAPSHOT
TABLE 408 NORTONLIFELOCK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 409 NORTONLIFELOCK: DEALS
15.1.8 SOPHOS
TABLE 410 SOPHOS: BUSINESS OVERVIEW
TABLE 411 SOPHOS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 412 SOPHOS: PRODUCT LAUNCHES
TABLE 413 SOPHOS: DEALS
15.1.9 KASPERSKY
TABLE 414 KASPERSKY: BUSINESS OVERVIEW
TABLE 415 KASPERSKY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 416 KASPERSKY: PRODUCT LAUNCHES
TABLE 417 KASPERSKY: OTHERS
15.1.10 TRELLIX
TABLE 418 TRELLIX: BUSINESS OVERVIEW
TABLE 419 TRELLIX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
15.1.11 ESET
TABLE 420 ESET: BUSINESS OVERVIEW
TABLE 421 ESET: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 422 ESET: PRODUCT LAUNCHES
TABLE 423 ESET: DEALS
15.1.12 EDGE GROUP
TABLE 424 EDGE GROUP: BUSINESS OVERVIEW
TABLE 425 EDGE GROUP: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 426 EDGE GROUP: PRODUCT LAUNCHES
TABLE 427 EDGE GROUP: DEALS
15.1.13 BEACON RED
TABLE 428 BEACON RED: BUSINESS OVERVIEW
TABLE 429 BEACON RED: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 430 BEACON RED: DEALS
15.1.14 MORO HUB
TABLE 431 MORO HUB: BUSINESS OVERVIEW
TABLE 432 MORO HUB: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 433 MORO HUB: DEALS
15.1.15 INJAZAT- G42
TABLE 434 INJAZAT: BUSINESS OVERVIEW
TABLE 435 INJAZAT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 436 INJAZAT: PRODUCT LAUNCHES
TABLE 437 INJAZAT: DEALS
15.1.16 PARAMOUNT COMPUTER SYSTEMS
TABLE 438 PARAMOUNT COMPUTER SYSTEMS: BUSINESS OVERVIEW
TABLE 439 PARAMOUNT COMPUTER SYSTEMS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 440 PARAMOUNT COMPUTER SYSTEMS: DEALS
15.1.17 SECURELINK
TABLE 441 SECURELINK: BUSINESS OVERVIEW
TABLE 442 SECURELINK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 443 SECURELINK: DEALS
15.1.18 SECUREWORKS
TABLE 444 SECUREWORKS: BUSINESS OVERVIEW
FIGURE 45 SECUREWORKS: COMPANY SNAPSHOT
TABLE 445 SECUREWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 446 SECUREWORKS: PRODUCT LAUNCHES
TABLE 447 SECUREWORKS: DEALS
15.1.19 OBRELA SECURITY INDUSTRIES
TABLE 448 OBRELA SECURITY INDUSTRIES: BUSINESS OVERVIEW
TABLE 449 OBRELA SECURITY INDUSTRIES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 450 OBRELA SECURITY INDUSTRIES: DEALS
15.1.20 CPX
TABLE 451 CPX: BUSINESS OVERVIEW
TABLE 452 CPX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 453 CPX: DEALS
15.1.21 MDS UAE
TABLE 454 MDS UAE: BUSINESS OVERVIEW
TABLE 455 MDS UAE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
*Details on Business Overview, Products/Solutions/Services offered, Recent Developments, MnM View might not be captured in case of unlisted companies.
15.2 OTHER PLAYERS
15.2.1 DTS SOLUTION
15.2.2 RAS INFOTECH
15.2.3 SPIDERSILK
15.2.4 CYBERSEC CONSULTING
15.2.5 AHAD
15.2.6 CODEGREEN
15.2.7 LOGRHYTHM
15.2.8 MALWAREBYTES
15.2.9 SAFE DECISION
15.2.10 SECURITY MATTERZ
15.2.11 INFRATECH
15.2.12 CATO NETWORKS
15.2.13 HELP AG
15.2.14 CYSIV (ACQUIRED BY LIQUID INTELLIGENT TECHNOLOGIES)
15.2.15 CYBERGATE
15.2.16 AUGMENTA CYBER SECURITY
15.2.17 CIPHERWAVE
15.2.18 DEFENDZA
15.2.19 SECURETECH
15.2.20 TACTICAL INTELLIGENCE SECURITY LTD
15.2.21 ZINAD
15.3 OTHER REGIONAL AND GLOBAL PLAYERS
16 APPENDIX (Page No. - 380)
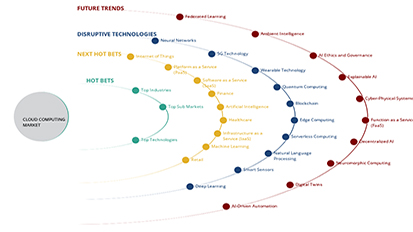
16.1 ADJACENT MARKETS
TABLE 456 ADJACENT MARKETS AND FORECASTS
16.2 LIMITATIONS
16.2.1 CYBER SECURITY MARKET
TABLE 457 CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2016–2021 (USD MILLION)
TABLE 458 CYBERSECURITY MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
TABLE 459 SMALL AND MEDIUM-SIZED ENTERPRISES MARKET, BY REGION, 2016–2021 (USD MILLION)
TABLE 460 SMALL AND MEDIUM-SIZED ENTERPRISES MARKET, BY REGION, 2022–2027 (USD MILLION)
TABLE 461 LARGE ENTERPRISES MARKET, BY REGION, 2016–2021 (USD MILLION)
TABLE 462 LARGE ENTERPRISES MARKET, BY REGION, 2022–2027 (USD MILLION)
16.2.2 THREAT INTELLIGENCE MARKET
TABLE 463 THREAT INTELLIGENCE MARKET, BY DEPLOYMENT MODE, 2014–2019 (USD MILLION)
TABLE 464 POST-COVID-19 THREAT INTELLIGENCE MARKET, BY DEPLOYMENT MODE, 2019–2025 (USD MILLION)
TABLE 465 CLOUD: THREAT INTELLIGENCE MARKET, BY REGION, 2014–2019 (USD MILLION)
TABLE 466 CLOUD: POST-COVID-19 THREAT INTELLIGENCE MARKET, BY REGION, 2019–2025 (USD MILLION)
TABLE 467 ON-PREMISES: THREAT INTELLIGENCE MARKET, BY REGION, 2014–2019 (USD MILLION)
TABLE 468 ON-PREMISES: POST-COVID-19 THREAT INTELLIGENCE MARKET, BY REGION, 2019–2025 (USD MILLION)
16.3 DISCUSSION GUIDE
16.4 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
16.5 CUSTOMIZATION OPTIONS
16.6 RELATED REPORTS
16.7 AUTHOR DETAILS



 Generating Response ...
Generating Response ...







Growth opportunities and latent adjacency in Middle East and Africa Cybersecurity Market