Security Service Edge Market by Offering, Solutions (ZTNA, CASB, SWG, FWaaS), Services, Vertical (BFSI, Government, Retail & eCommerce, IT & ITeS), & Region (North America, Europe, Asia Pacific, Middle East & Arica, Latin America) - Global Forecast to 2028
Security Service Edge (SSE) Market Statistics - Size, Share & Growth
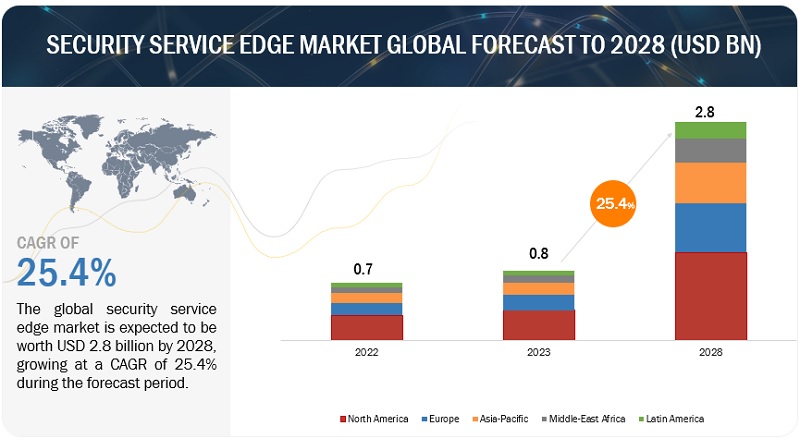
[235 Pages Report] The Security Service Edge Market size worth approximately $0.8 billion in 2023. It is expected to grow at an effective Compound Annual Growth Rate (CAGR) of 25.4% from 2023 to 2028. The revenue projections for 2028 is poised to rise over $2.8 billion. The base year considered for estimation is 2022 and the historical data span ranges from 2023 to 2028.
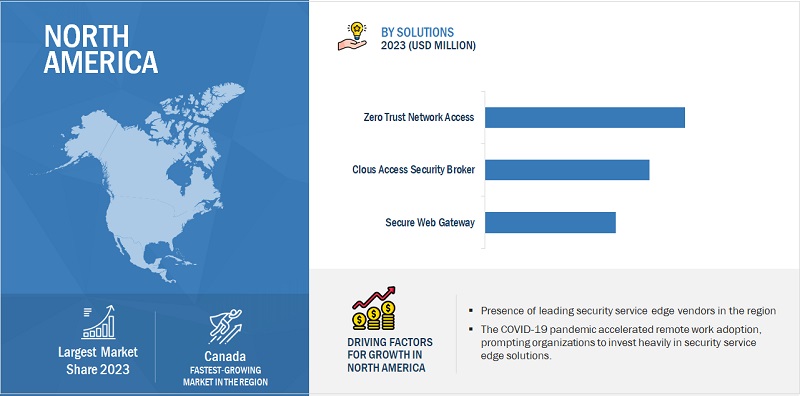
The adoption of the Zero Trust Network Access (ZTNA) framework is a significant driver in the SSE market. It offers adaptive access controls, micro-segmentation, and enhanced data protection, aligning well with the dynamic nature of remote work. This framework ensures that access is based on real-time risk assessments and can restrict access in unusual situations, reducing the risk of data breaches and unauthorized sharing. Overall, ZTNA is recognized for its effectiveness in mitigating security risks associated with remote work, making it a key factor in the Security Service Edge market’s growth.
To know about the assumptions considered for the study, Request for Free Sample Report
To know about the assumptions considered for the study, download the pdf brochure
Security Service Edge Market Dynamics
Driver: Zero Trust Access Driving Security Service Edge (SSE) Adoption
Enabling secure Zero Trust access to data and applications based on user identity, context, and least privileged access has emerged as a pivotal driver for the adoption of Security Service Edge solutions. This approach signifies a significant departure from conventional security models, emphasizing continuous user and device verification. SSE's core principle revolves around meticulous scrutiny of user identities and the context in which they seek access, granting them the minimum necessary privileges in a highly personalized manner. By adopting this user-centric and context-aware security strategy, SSE effectively reduces the potential attack surface, substantially lowering the risk of unauthorized or malicious access. Furthermore, SSE's ability to adapt access decisions in real time by considering variables such as user location, device health, and resource sensitivity enhances its efficacy in thwarting security breaches. This user-centric, context-aware approach safeguards data and applications and seamlessly aligns with contemporary work environments, offering secure access solutions tailored to the evolving digital landscape.
Restraint: Integration Complexity
Integrating SSE into an organization's existing IT infrastructure often requires intricate planning and execution. Organizations must assess the compatibility of Security Service Edge with their current technology stack and identify areas where adjustments or updates are needed. Interoperability issues may arise during integration, as SSE solutions need to seamlessly interact with various components of the existing IT ecosystem. Minimizing disruption to ongoing business operations is a primary concern, and customization and configuration of SSE solutions to align with organizational requirements may be necessary. Adequate expertise in cloud security, network architecture, and cybersecurity is essential, and organizations may need to allocate significant resources and engage third-party support to navigate the integration complexities effectively.
Opportunity: Cost savings by combining multiple security and network access
The integration of multiple security and network access technologies into a unified platform, often delivered through subscription pricing, represents a significant opportunity within the Security Service Edge market. This opportunity centers on cost efficiency, where organizations stand to realize substantial savings. By consolidating various security and networking tools into a single SSE platform, businesses can streamline their IT expenditure. This not only leads to financial savings but also optimizes resource allocation by enabling IT teams to focus their efforts on a centralized and integrated solution. The subscription-based pricing model ensures predictability in costs, facilitating better financial planning and budget management. Furthermore, the scalability offered by SSE solutions allows organizations to adapt to changing needs without incurring significant additional expenses. In essence, the SSE market presents an opportunity for cost-conscious organizations to bolster their security and networking capabilities while maintaining control over their spending.
Challenge: Traffic Aggregation and User Experience
SSE offers advanced security measures; it must also ensure that the network and applications perform optimally to provide a seamless user experience. The changing traffic patterns and the shift to remote work have exacerbated this challenge, as users need reliable and high-quality access to applications from various locations. The issue of packet loss affecting commonly used video and voice-based applications highlights the importance of maintaining application performance. Additionally, the rapidly changing WAN/5G accessibility adds complexity to the equation, as it doesn't guarantee consistent application and network performance and availability. SSE providers must address these challenges by optimizing traffic routing, implementing Quality of Service (QoS) measures, and ensuring that security measures do not compromise network performance. Balancing security and user experience is a critical aspect of SSE deployment, and addressing these challenges is essential for the successful adoption of SSE solutions in the evolving remote work landscape.
Ecosystem Of Security Service Edge Market
The Zero Trust Network Access solution to register the highest CAGR in the security service edge market during the forecast period.
The core principle of ZTNA is to "never trust, always verify". ZTNA uses identity-based and context-based access restrictions in this method to protect both on-premises and cloud-based resources. This security framework allows privileged users to access necessary resources but effectively prevents unauthorized users from accessing them. Zero Trust Network Access is essential for creating a dynamic network perimeter in the context of SSE technology. It meticulously monitors all users and linked devices to ensure all access requests abide by strict security guidelines. No network traffic is allowed to pass over the network or related cloud services without first completing the required authentication in accordance with ZTNA guidelines. ZTNA plays a vital role in SSE by ensuring that no user or device is presumed trustworthy, regardless of where they are, and by imposing identity verification and access controls to grant access to only authorised users and devices.
The implementation & integration services are expected to register a higher CAGR during the forecast period.
Implementation and Integration help in the successful deployment of SSE by helping organizations configure and integrate security services efficiently. Implementation services encompass SSE solutions' initial setup and deployment, tailoring them to specific organizational needs and objectives. Integration services focus on aligning SSE with an organization's network architecture, ensuring compatibility and smooth operation. In an increasingly complex digital landscape, where the interplay of data, applications, and users is critical, Implementation and Integration Services are essential for optimizing security, improving operational efficiency, and facilitating a robust cybersecurity posture. Their role extends beyond installation, encompassing ongoing support to ensure that SSE solutions work harmoniously with an organization's IT ecosystem, delivering security and network efficiency.
Based on region, North America is expected to hold the largest market size during the forecast.
The global security service edge market is set to witness North America as its largest contributor in terms of market size, with a significant impact from the United States and Canada. Within the region, organizations heavily invest in cutting-edge technologies like AI, 5G, machine learning, blockchain, big data, and cloud computing. This tech-driven approach is fueling the demand for cloud-based security solutions, including Zero Trust Network Access (ZTNA), Secure Web Gateways (SWG), and Cloud Access Security Brokers (CASB). According to the article published in Security Week in July 2019, Duo Security analyzed data from nearly 24 million devices. It also analyzed that there were more than 1 million applications and services and more than half a billion authentications per month across its customer base in North America and Western Europe, which drives the need for ZTNA under the SASE framework. There is an increasing need for wireless communication solutions across the globe, due to which the Security Service Edge market is growing swiftly.
Market Players:
The major vendors in this market include Netskope (US), ZScaler (US), Palo Alto Networks (US), Cisco (US), Broadcom (US), Forcepoint (US), Lookout (US), iBoss (US), Skyhigh Security (US), Cloudflare (US), Trend Micro (Japan), Akamai (US), Fortinet (US), Aruba Networks (US), Citrix (US), Cato Networks (Israel), Perimeter81 (Israel), Open Systems (Switzerland), Menlo Security (US). These players have adopted various growth strategies, such as partnerships, agreements and collaborations, new product launches and product enhancements, and acquisitions to expand their footprint in the SSE market.
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
Request Sample Scope of the Report
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
|
Report Metrics |
Details |
|
Market size available for years |
2018-2028 |
|
Base year considered |
2022 |
|
Forecast period |
2023–2028 |
|
Forecast units |
Value (USD) Million/Billion |
|
Segments Covered |
By Offering, solutions, services, vertical, and Region |
|
Region covered |
North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
|
Companies covered |
The major players in the SSE market are Netskope (US), ZScaler (US), Palo Alto Networks (US), Cisco (US), Broadcom (US), Forcepoint (US), Lookout (US), iBoss (US), Skyhigh Security (US), Cloudflare (US), Trend Micro (Japan), Akamai (US), Fortinet (US), Aruba Networks (US), Citrix (US), Cato Networks (Israel), Perimeter81 (Israel), Open Systems (Switzerland), Menlo Security (US) |
This research report categorizes the Security Service Edge market to forecast revenues and analyze trends in each of the following submarkets:
Based on Offering:
- Solutions
- Services
Based on Solutions:
- Zero Trust Network Access (ZTNA)
- Cloud Access Security Broker (CASB)
- Secure Web Gateway (SWG)
- Firewall-as-a-Services (FWaaS)
- Other Solutions
Based on Services:
- Managed Security Services
- Implementation & Integration Services
- Support & Maintenance Services
- Other Services
Based on Vertical:
- BFSI
- Government
- Retail & eCommerce
- IT & ITeS
- Healthcare
- Education
- Manufacturing
- Other Verticals
By Region:
-
North America
- United States (US)
- Canada
-
Europe
- United Kingdom (UK)
- Germany
- France
- Italy
- Rest of Europe
-
Asia Pacific
- China
- Japan
- India
- Rest of Asia Pacific
-
Middle East and Africa
- Middle East
- Africa
-
Latin America
- Brazil
- Mexico
- Rest of Latin America
Recent Developments:
- In September 2023, Netskope acquired digital experience monitoring (DEM) startup Kadiska. The acquisition is a bid for Netskope to boost its capabilities on the monitoring side of its secure access service edge (SASE) platform initiatives.
- In April 2023, Palo Alto Networks and Accenture joined forces to offer AI-powered Prisma SASE solutions, enhancing cyber resilience and enabling secure access control for organizations amidst the complexities of remote work and multi-cloud environments.
- In February 2023, Zscaler acquired Canonic Security, a SaaS application security platform innovator. By integrating Caconic’s new supply chain security capabilities into its data protection services, Zscaler strengthens its CASB and SSPM (SaaS Security Posture Management) offerings, enabling companies to consolidate point products, reducing cost and simplifying management.
Frequently Asked Questions (FAQ):
What is security service edge?
Security Service Edge (SSE) is a comprehensive security framework that focuses on securing network and data access at the edge of the network. It is an evolution of traditional network security models that previously centered around protecting a centralized network perimeter. SSE redefines security by providing protection at the point where users, devices, and data connect with cloud services and the internet, regardless of their location.
What is the market size of the security service edge market?
The security service edge market size is projected to grow from USD 0.8 bllion in 2023 to USD 2.8 billion by 2028 at a CAGR of 25.4% during the forecast period.
What are the major drivers in the security service edge market?
The major drivers in the security service edge market include the rising need for unified network security architecture, integration of a Cloud Access Security Broker (CASB), Zero Trust Access Driving Security Service Edge (SSE) Adoption. These factors have led to a rising demand for SSE solutions and services.
Who are the key players operating in the security service edge market?
The key vendors operating in the security service edge market include Netskope (US), ZScaler (US), Palo Alto Networks (US), Cisco (US), Broadcom (US), Forcepoint (US), Lookout (US), iBoss (US), Skyhigh Security (US), Cloudflare (US).
What are the opportunities for new market entrants in the security service edge market?
New entrants in the SSE market have ample opportunities. With the rising demand for SSE solutions driven by cloud adoption and cybersecurity needs, newcomers can innovate and specialize in niche areas, collaborating with key industry players. As SSE solutions mature, there's potential to disrupt the market with cost-effective, agile offerings, making it an attractive space for innovation and growth.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
The research study involved four major activities in estimating the SSE market size. Exhaustive secondary research has been done to collect important information about the market and peer markets. The next step has been to validate these findings, assumptions, and sizing with the help of primary research with industry experts across the value chain. Both top-down and bottom-up approaches have been used to estimate the market size. Post which the market breakdown and data triangulation have been adopted to estimate the market sizes of segments and sub-segments.
Secondary Research
In the secondary research process, various secondary sources were referred to for identifying and collecting information required for this study. The secondary sources include annual reports, press releases, investor presentations of companies, white papers, and articles from recognized authors. Secondary research was mainly done to obtain essential information about the market’s value chain, the pool of key market players, market segmentation according to industry trends, and regional outlook and developments from both market and technology perspectives.
Primary Research
In the primary research, various sources from both the supply and demand sides were interviewed to obtain the qualitative and quantitative insights required for this report. Primary sources from the supply side include experts such as CEOs, vice presidents, marketing directors, equipment manufacturers, technology and innovation directors, end users, and related executives from multiple key companies and organizations operating in the SSE market ecosystem.
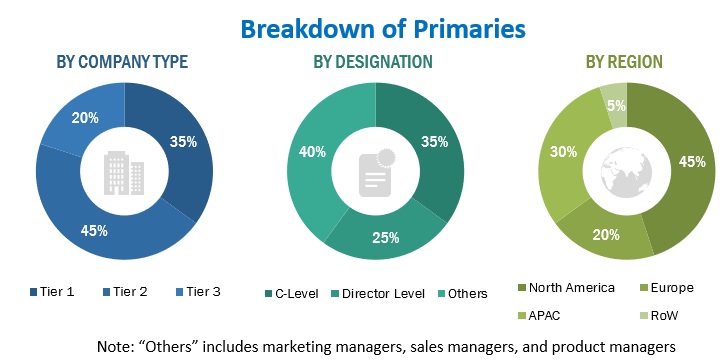
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
In the market engineering process, top-down and bottom-up approaches and data triangulation methods have been used to estimate and validate the size of the SSE market and other dependent submarkets. The research methodology used to estimate the market sizes includes the following:
- Initially, MarketsandMarkets focuses on top-line investments and spending in the ecosystems. Further, major developments in the key market area have been considered.
- Analyzing major original equipment manufacturers (OEMs), studying their product portfolios, and understanding different applications of their solutions.
- Analyzing the trends related to adopting different types of authentications and brand protection equipment.
- Tracking the recent and upcoming developments in the SSE market that include investments, R&D activities, product launches, collaborations, mergers and acquisitions, and partnerships, as well as forecasting the market size based on these developments and other critical parameters.
- Conduct multiple discussions with key opinion leaders to know about different types of authentications and brand protection offerings used and the applications for which they are used to analyze the breakup of the scope of work carried out by major companies.
- Segmenting the market based on technology types with respect to applications wherein the types are to be used and deriving the size of the global application market.
- Segmenting the overall market into various market segments
- Validating the estimates at every level through discussions with key opinion leaders, such as chief executives (CXOs), directors, and operation managers, and finally with the domain experts at MarketsandMarkets
Market Size Estimation Methodology-Bottom-up approach

To know about the assumptions considered for the study, Request for Free Sample Report
Market Size Estimation Methodology-top-down approach

Data Triangulation
The SSE market has been split into several segments and sub-segments after arriving at the overall market size from the estimation process explained above. To complete the overall market engineering process and arrive at the exact statistics for all segments and sub-segments, data triangulation and market breakdown procedures have been used, wherever applicable. The data has been triangulated by studying various factors and trends from both the demand and supply sides.
The SSE market size has been validated using top-down and bottom-up approaches.
Market Definition
Security service edge (SSE) is a comprehensive cloud-based security solution that converges network and security services to protect access to web, cloud, and private applications, regardless of user location or device. SSE capabilities include access control, threat protection, data security, security monitoring, and acceptable-use control. SSE may also include on-premises or agent-based components.
An SSE solution requires four fundamental security capabilities such as zero trust access network (ZTNA), cloud access security broker (CASB), secure web gateway (SWG), and firewall-as-a-service (FWaaS).
Stakeholders
- SSE vendors
- Project Managers
- System Integrators (SIs)
- Managed Service Providers (MSPs)
- Value Added Resellers (VARs)
- Developers
- Business Analysts
- Cybersecurity Specialists
- Third-party vendors
- Technology Providers
- Consulting Firms
- Quality Assurance (QA)/ test engineers
Report Objectives
- To determine and forecast the global SSE market by offering (solutions and services), solutions, services, vertical, and region from 2023 to 2028, and analyze the various macroeconomic and microeconomic factors that affect the market growth.
- To forecast the size of the market segments with respect to five main regions: North America, Europe, Asia Pacific (APAC), Latin America, and the Middle East & Africa (MEA).
- To provide detailed information about the major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the SSE market.
- To analyze each submarket with respect to individual growth trends, prospects, and contributions to the overall SSE market.
- To analyze the opportunities in the market for stakeholders by identifying the high-growth segments of the SSE market.
- To profile the key market players; provide a comparative analysis based on business overviews, regional presence, product offerings, business strategies, and key financials; and illustrate the market’s competitive landscape.
- Track and analyze competitive developments in the market, such as mergers and acquisitions, product developments, partnerships and collaborations, and Research and Development (R&D) activities.
Available Customizations
With the given market data, MarketsandMarkets offers customizations as per the company’s specific needs. The following customization options are available for the report:
Geographic Analysis
- Further break-up of the Asia Pacific market into countries contributing 75% to the regional market size
- Further break-up of the North American market into countries contributing 75% to the regional market size
- Further break-up of the Latin American market into countries contributing 75% to the regional market size
- Further break-up of the Middle East & Africa market into countries contributing 75% to the regional market size
- Further break-up of the European market into countries contributing 75% to the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)











Growth opportunities and latent adjacency in Security Service Edge Market