
Endpoint Security Market Size, Share, Growth & Trends Report
Endpoint Security Market by Solution (Firewall, Patch Management, Web Content Filtering, Antivirus), Service (Professional, Managed), Enforcement Point (Workstations, Mobile Devices, Server, POS Terminal), Vertical, Region - Global Forecast to 2030




OVERVIEW
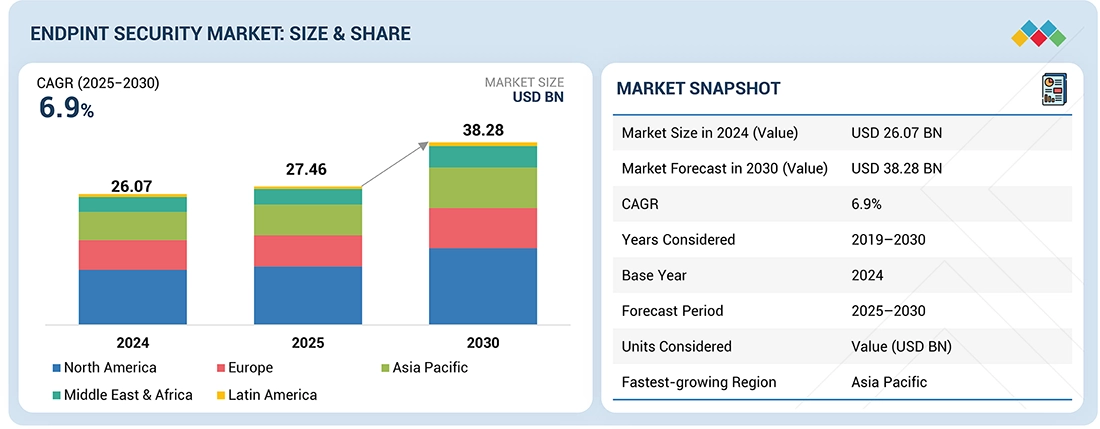
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
The global endpoint security market is projected to grow from USD 27.46 billion in 2025 to USD 38.28 billion by 2030, registering a CAGR of 6.9% during the forecast period. Endpoint security plays a crucial role in addressing the growing threats associated with non-traditional endpoints such as ATMs, kiosks, industrial systems, and POS systems. These devices often operate on outdated software within less secure environments, making them highly vulnerable to cyber threats and unauthorized access.
KEY TAKEAWAYS
-
BY OFFERINGThe Solutions segment dominates with advanced antivirus, EDR, and patch management tools, ensuring real-time detection and compliance, while Services grow fastest as enterprises increasingly outsource security operations and maintenance for agility.
-
BY DEPLOYMENT MODEOn-premises deployment remains preferred in regulated and large enterprises for control and compliance, whereas Cloud solutions witness faster growth due to scalability, cost efficiency, and remote workforce adaptability.
-
BY ORGANIZATION SIZELarge enterprises drive major revenue through comprehensive endpoint architectures and strong compliance mandates, while SMEs show stronger CAGR growth, adopting cost-effective managed and cloud-based endpoint protection to counter rising cyber risks.
-
BY ENFORCEMENT POINTWorkstations dominate endpoint enforcement due to their ubiquity in enterprise environments, while POS terminals exhibit high CAGR as retail and service sectors adopt stronger security to safeguard financial and transaction systems.
-
BY VERTICALBFSI leads in market size driven by stringent compliance and high-value data protection, whereas Healthcare records the highest CAGR due to digitized medical records, IoMT devices, and rising data privacy regulations.
-
BY REGIONNorth America leads with strong regulatory frameworks and early technology adoption, while Asia Pacific achieves the highest CAGR, propelled by digital transformation, growing cyber threats, and expanding cloud security investments.
-
COMPETITIVE LANDSCAPEThe endpoint security market is highly competitive and dynamic, led by players such as Microsoft, Palo Alto Networks, CrowdStrike, SentinelOne, and Trend Micro. Companies are focusing on innovation through AI-driven threat detection, cloud-native solutions, and integrated platforms, while strengthening customer support, strategic partnerships, and mergers & acquisitions to expand regional presence and differentiate offerings amid increasing cyber threats and regulatory pressures globally.
To mitigate these risks, organizations are increasingly adopting specialized endpoint security solutions equipped with live monitoring, automated threat response, and centralized management capabilities. These solutions enable a risk-based approach, allowing endpoint security teams to safeguard a diverse range of assets, from a few hospital ATMs to thousands of kiosks, gaming machines, and digital signs, while ensuring compliance with evolving and complex regulatory requirements.
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
The figure highlights the key trends and disruptions in the endpoint security market, including the rising adoption of AI and machine learning for faster threat detection, the shift toward Zero Trust Architecture for continuous verification, and increased demand for cloud-delivered solutions driven by remote work. Stricter regulatory compliance is also prompting organizations to modernize defenses, collectively driving more agile, intelligent, and integrated endpoint security solutions.
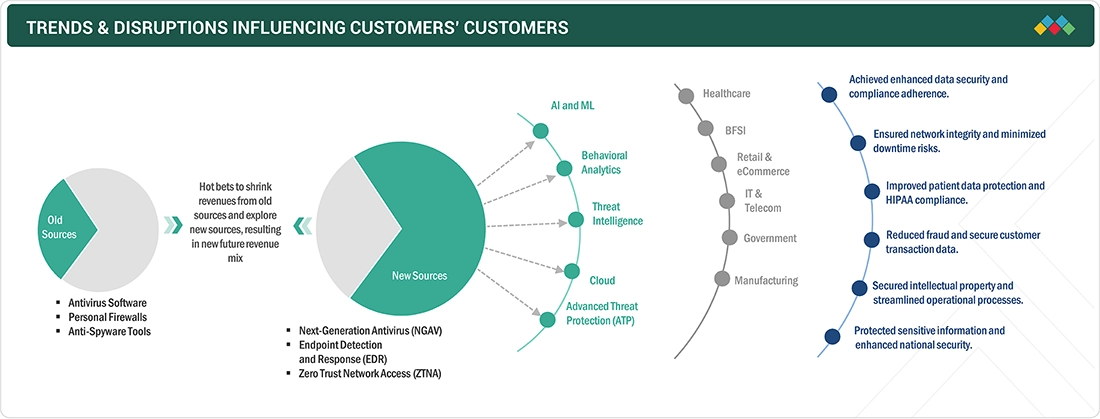
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Growing surge of cyberattacks

-
Increasing shift toward remote work
Level
-
High deployment costs
-
Impact on device performance
Level
-
Growing adoption of cloud
-
Integration of AI/ML into endpoint security solutions
Level
-
Shortage of skilled cybersecurity professionals
-
Zero-day vulnerabilities
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Growing surge of cyberattacks
Cyber threats are escalating globally, with Q3 2024 witnessing a 75% surge in weekly cyberattacks compared to Q2. Education, government, and healthcare sectors faced the most attacks, while Africa saw a 90% rise. Ransomware remained dominant, particularly in North America and Europe, highlighting growing vulnerabilities in organizational cybersecurity defenses.
Restraint: Limited control over data
High deployment costs constrain the endpoint security market, especially for SMEs with limited IT budgets. Significant investments in software, upgrades, personnel, and maintenance, along with integration across laptops, mobile, and IoT devices, make implementing robust endpoint security financially challenging.
Opportunity: Integration of AI/ML into endpoint security solutions
The integration of AI and ML in endpoint security is driving significant market growth by enabling real-time threat detection, predictive analysis, and automated response. These intelligent systems adapt to evolving attacks, reduce manual intervention, and enhance overall efficiency in identifying, containing, and remediating cyber threats.
Challenge: Zero-day vulnerabilities
Zero-day vulnerabilities pose a critical challenge for endpoint security, as unknown exploits can bypass traditional signature-based defenses. Protecting against them requires adaptive solutions using AI, ML, behavioral analysis, and continuous monitoring through EDR tools, emphasizing real-time threat intelligence and proactive, layered defenses.
Endpoint Security Market: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
Europe Energy faced challenges securing sensitive customer data and high-value transactions, with in-house security being slow and costly. The company deployed CrowdStrike Falcon Complete for comprehensive, cloud-based endpoint protection. | The solution automated security, enabled real-time threat detection, streamlined management, ensured continuous monitoring, and enhanced customer trust and brand reputation. |
 |
Domain Group faced security challenges across its hybrid cloud and on-premises environment with limited visibility and remote access issues. It deployed Palo Alto Prisma Access, NGFWs, and Cortex XDR for integrated, cloud-delivered protection. | The solution unified security across all users, improved secure access, enhanced visibility and incident response, and strengthened overall cybersecurity while supporting scalability. |
 |
The University of Oxford needed to secure and streamline management of 3,000 endpoints while migrating its Windows environment. The company deployed Symantec Client and Server Management Suites for unified, flexible, and efficient endpoint management. | The solution enhanced security, accelerated status reporting and patch deployment, prevented outages, reduced server CPU usage, and improved overall IT performance and cost efficiency. |
 |
MaineGeneral Health modernized security for 3,800 users with Sophos Intercept X, XG Firewalls, SafeGuard Encryption, Sandstorm, and Sophos Central to protect data, ensure HIPAA compliance, and secure the network. | The solution automated threat detection, simplified management, strengthened protection against advanced threats, improved compliance, and enabled seamless cloud security. |
 |
The Bolshoi Theatre strengthened IT security to protect operations, customer data, intellectual property, and sensitive employee information amid rising sophisticated cyberattacks. They deployed Kaspersky MDR, Secure Mail Gateway, and endpoint protection for comprehensive coverage. | The solution provided automated protection, 24/7 managed monitoring, reduced the need for an in-house SOC, enhanced resilience against cyberthreats, optimized resource use, and improved overall IT security. |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The endpoint security market ecosystem consists of solution providers and service providers working together to secure devices against cyber threats. Solution providers offer tools like EPP, EDR, XDR, encryption, and device management platforms, while service providers deliver managed security services, threat detection and response, compliance support, and incident remediation. Together, they enable organizations to protect distributed endpoints across on-premises, cloud, and hybrid environments.

Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
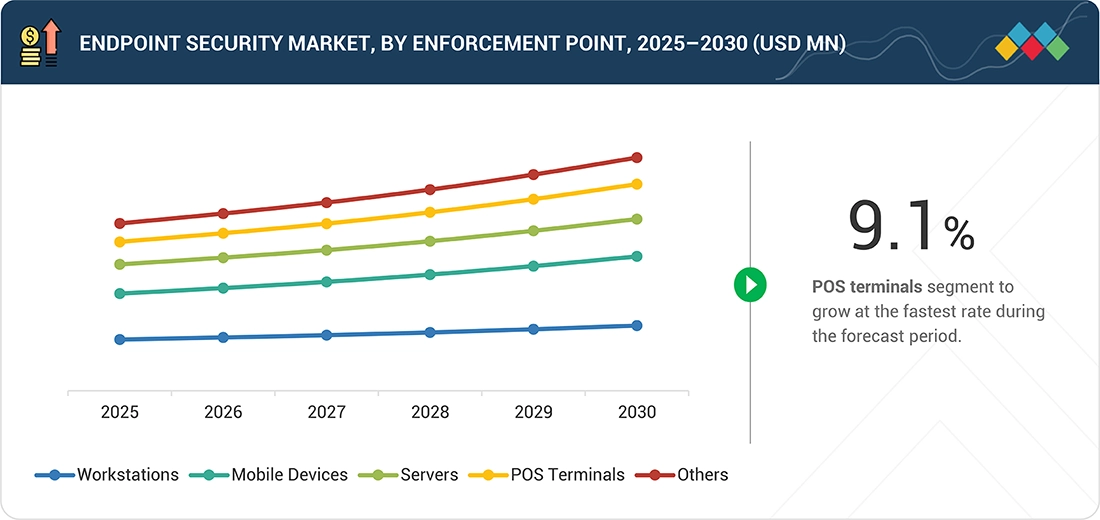
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Endpoint Security Market, By Offering
The Solutions segment dominates the endpoint security market because comprehensive tools such as antivirus, patch management, firewalls, EDR, MDM, and encryption, provide real-time threat detection, automated response, data protection, and policy enforcement, addressing risks from remote work, mobile devices, and both internal and external threats.
Endpont Security Market, By Deploymet Mode
On-premises deployments hold a significant share in the endpoint security market because they give organizations full control over their security environment. These solutions, including antivirus, firewalls, intrusion detection, and EDR, allow customization, strict data privacy, and compliance, though they require substantial infrastructure, skilled staff, and maintenance, making them essential for enterprises with sensitive data and stringent regulatory requirements.
Endpoint Security Market, By Organization Size
Large enterprises dominate the endpoint security market due to their vast and distributed IT infrastructures, thousands of endpoints, and complex supply chains, which increase cyberattack risks. Advanced solutions, including EDR, XDR, behavioral analytics, application control, and device management, provide unified visibility, real-time threat detection, automated response, and regulatory compliance, making endpoint security essential for scalability, resilience, and protection in hybrid and cloud environments.
Endpoint Security Market, By Enforcement Point
Workstations hold the largest market share in endpoint security because they are widely used across enterprises and remain primary targets for malware, ransomware, and phishing attacks. Continuous monitoring, advanced threat detection, application and device control, patch management, and centralized management make workstation security critical for protecting sensitive data and ensuring operational continuity, while evolving multi-platform threats further reinforce their strategic importance.
Endpoint Security Market, By Vertical
BFSI vertical lead the endpoint security market due to their need to protect vast amounts of sensitive financial and personal data across devices like laptops, ATMs, and POS terminals. Advanced solutions for threat detection, malware protection, encryption, and access control help prevent breaches, safeguard customer information, maintain regulatory compliance, and preserve trust amid growing cyber threats and high-profile security incidents.
REGION
Asia Pacific to be fastest-growing region in global endpoint security market during forecast period
The Asia Pacific region is emerging as a key growth hub for endpoint security, driven by rising cyberattacks, rapid digitalization, and expanding cloud and IoT infrastructures. Governments are investing heavily, exemplified by Australia’s USD 1.6 billion cybersecurity initiative, while vendors like CrowdStrike and McAfee enhance regional access to AI-based threat detection. Growing work-from-home trends and scalability needs further strengthen the region’s demand for advanced endpoint protection.

Endpoint Security Market: COMPANY EVALUATION MATRIX
In the endpoint security market matrix, Microsoft (Star) leads with its Defender suite, offering integrated protection across cloud, identity, and devices for large enterprises. Broadcom (Emerging Leader) is strengthening its position through Symantec’s advanced threat prevention and encryption solutions, showing strong potential as hybrid security adoption rises.
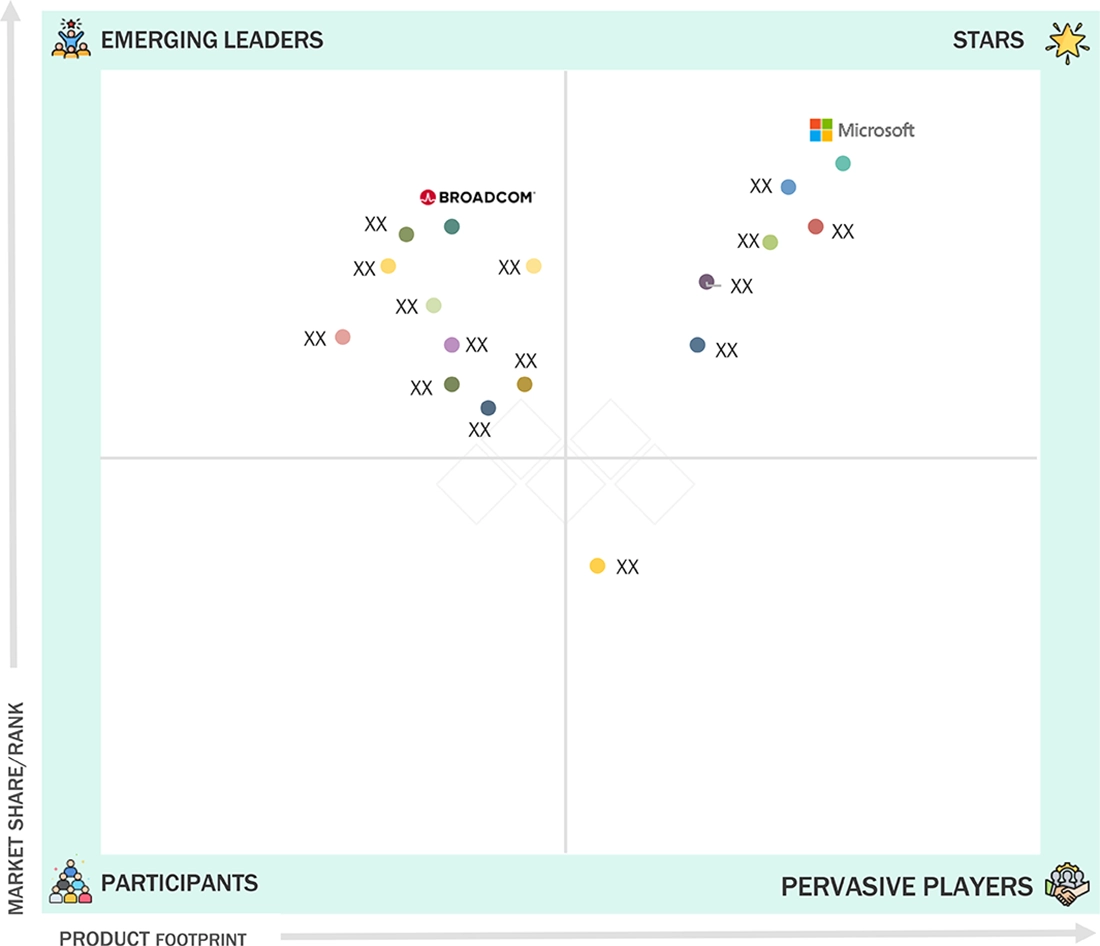
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size in 2024 (Value) | USD 26.07 Billion |
| Market Forecast in 2030 (Value) | USD 38.28 Billion |
| Growth Rate | CAGR of 6.9% from 2025-2030 |
| Years Considered | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/Billion) |
| Report Coverage | Revenue forecast, company ranking, competitive landscape, growth factors, and trends |
| Segments Covered |
|
| Regions Covered | North America, Asia Pacific, Europe, Latin America, Middle East & Africa |
WHAT IS IN IT FOR YOU: Endpoint Security Market REPORT CONTENT GUIDE
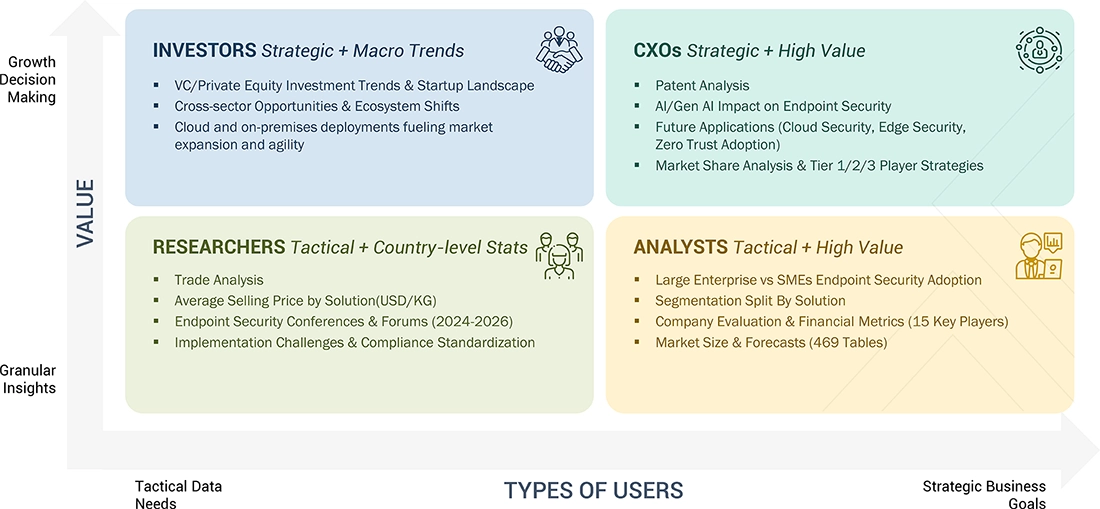
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Whitepaper | Developed a seven-chapter whitepaper covering key challenges, the need for access-centric endpoints, comparative OS environments, GSI-oriented capabilities, integration readiness, and relevant use cases with success stories. | Improved document structure for clarity and coherence, aligned content with GSI-focused objectives, incorporated comparative and integration insights, and included practical examples to support informed decision-making. |
RECENT DEVELOPMENTS
- April 2025 : Microsoft partnered with Proofpoint to enhance human-centric security for joint customers. The partnership builds on existing integrations with Microsoft Defender and expands into creating real economic value. It focuses on deeper API-level integration with Defender to simplify threat protection and improve defense against AI-powered cyber threats
- March 2025 : Kaspersky partnered with TechnoBind to expand its B2B reach in India, offering scalable endpoint security and cyber defense solutions. The partnership aims to accelerate adoption across enterprises and SMBs through TechnoBind’s strong partner ecosystem
- February 2025 : CyberArk and SentinelOne partnered to enhance endpoint and identity security by integrating Singularity with CyberArk's Endpoint Privilege Manager. The partnership improves threat detection and response through AI-driven analytics to prevent misuse of privileged access.
- January 2025 : Cognizant and CrowdStrike partnered to strengthen endpoint security by integrating the AI-native Falcon platform with Cognizant’s Neuro Cybersecurity suite. This streamlines SecOps and enhances real-time threat detection and response across enterprise environments
- July 204 : Trend Micro and Intel partnered to boost ransomware and fileless malware detection using Intel Threat Detection Technology. The solution leverages GPU-based memory scanning for better accuracy and performance without slowing devices
Table of Contents

Methodology
Exhaustive secondary research was done to collect information on the endpoint security industry. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, such as top-down and bottom-up, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and subsegments of the endpoint security market.
Secondary Research
The market for companies offering endpoint security solutions and services is arrived at by secondary data available through paid and unpaid sources, analyzing the product portfolios of the major companies in the ecosystem, and rating the companies by their performance and quality. Various sources were referred to in the secondary research process to identify and collect information for this study. The secondary sources include annual reports, press releases, investor presentations of companies, white papers, journals, certified publications, and articles from recognized authors, directories, and databases.
In the secondary research process, various secondary sources were referred to identify and collect information related to the study. Secondary sources included annual reports, press releases, and investor presentations of endpoint security vendors, forums, certified publications, and whitepapers. The secondary research was used to obtain essential information on the industry’s value chain, the total pool of key players, market classification, and segmentation from the market and technology-oriented perspectives.
Primary Research
In the primary research process, various supply and demand sources were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the endpoint security market.
After the complete market engineering (calculations for market statistics, market breakdown, market size estimations, market forecasting, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also undertaken to identify the segmentation types, industry trends, competitive landscape of endpoint security solutions offered by various market players, and fundamental market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key player strategies.
In the complete market engineering process, the top-down and bottom-up approaches and several data triangulation methods were extensively used to perform the market estimation and market forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list the key information/insights throughout the report.
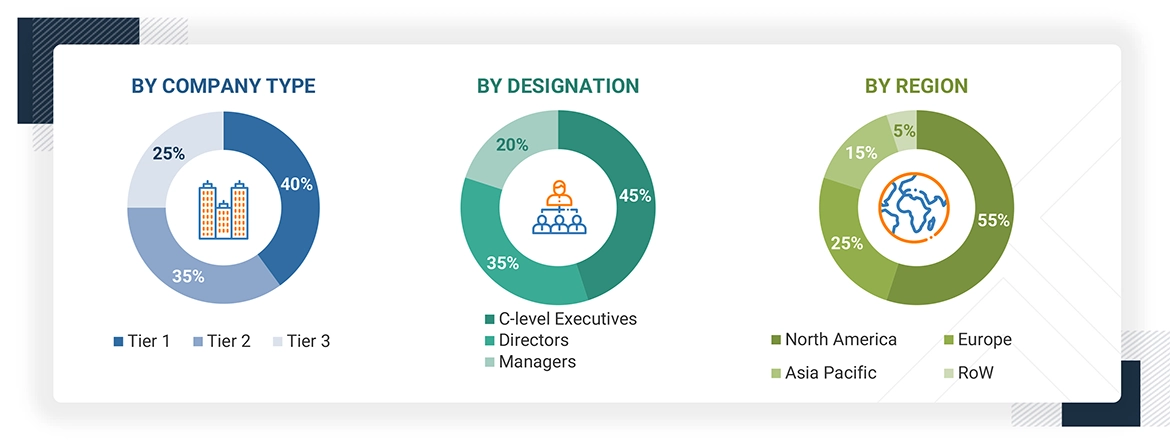
Note: The companies have been categorized based on their total annual revenue; tier 1 companies = revenue
greater than USD 10 billion; tier 2 companies = revenue between USD 1 billion and USD 10 billion; tier 3 companies = revenue
between USD 500 million and USD 1 billion.
Other levels include sales managers, marketing managers, and product managers.
Source: MarketsandMarkets Analysis
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Top-down and bottom-up approaches were used to estimate and validate the size of the global endpoint security market and the size of various other dependent subsegments. The research methodology used to estimate the market size includes the following details: key players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure included the study of the annual and financial reports of the top market players, and extensive interviews were conducted for key insights from the industry leaders, such as CEOs, VPs, directors, and marketing executives.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data is consolidated and added to detailed input and analysis from MarketsandMarkets.
Endpoint Security Market : Top-Down and Bottom-Up Approach
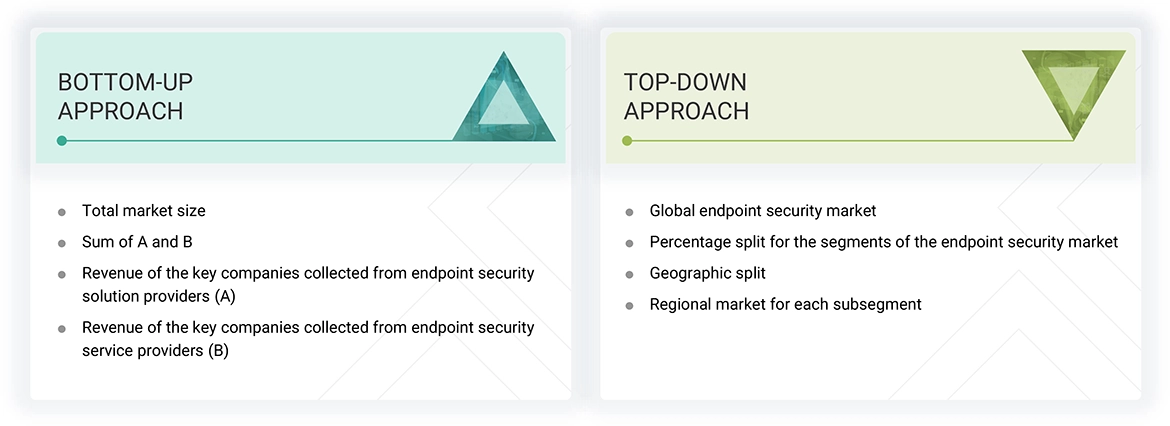
Data Triangulation
After arriving at the overall market size using the market size estimation processes explained above, the market was split into several segments and subsegments. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
According to MnM, “The endpoint security market focuses on protecting endpoint devices like laptops, desktops, servers, and mobile devices from cyber threats such as malware, ransomware, and unauthorized access. It includes solutions like EPP, EDR, and XDR, often enhanced by AI and cloud-based management. As remote work, IoT, and BYOD expand, organizations increasingly rely on endpoint security to safeguard their networks and data.”
Stakeholders
- Endpoint Security Vendors
- IT Decision Makers/CISOs
- Managed Security Service Providers (MSSPs)
- Enterprise End Users
- System Integrators/Channel Partners
- Internal IT and Security Operations Teams
- Compliance and Risk Officers
- Cloud Service Providers
- Device Manufacturers/OEMs
Report Objectives
- To define, describe, and forecast the endpoint security market based on offering, enforcement point, deployment mode, organization size, vertical, and region
- To forecast the market size of the five main regions: North America, Europe, Asia Pacific (APAC), Middle East & Africa (MEA), and Latin America
- To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market
- To provide detailed information related to the primary factors (drivers, restraints, opportunities, and challenges) influencing the growth of the endpoint security market
- To analyze opportunities in the market for stakeholders by identifying high-growth segments of the endpoint security market
- To profile the key players of the endpoint security market and comprehensively analyze their market size and core competencies
- Track and analyze competitive developments, such as product launches, mergers and acquisitions, partnerships, agreements, and collaborations in the global endpoint security market
Available Customizations
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis as per Feasibility
- Further breakup of the Asia Pacific market into countries contributing 75% to the regional market size
- Further breakup of the North American market into countries contributing 75% to the regional market size
- Further breakup of the Latin American market into countries contributing 75% to the regional market size
- Further breakup of the Middle Eastern & African market into countries contributing 75% to the regional market size
- Further breakup of the European market into countries contributing 75% to the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)
Key Questions Addressed by the Report
What are the opportunities in the global endpoint security market?
The endpoint security market offers strong growth opportunities, such as remote work, BYOD, and cloud adoption. Rising cyber threats drive demand for integrated, AI-powered solutions that provide real-time protection and centralized management. Key industries like BFSI and healthcare are boosting investments to meet compliance and security needs.
What is the definition of the endpoint security market?
According to MnM, The endpoint security market refers to the ecosystem of technologies, solutions, and services designed to protect endpoints such as desktops, laptops, mobile devices, and servers from cyber threats. It includes antivirus, anti-malware, endpoint detection and response (EDR), extended detection and response (XDR), encryption, and endpoint privilege management tools. These solutions help monitor, detect, and respond to malicious activities at the device level while supporting policy enforcement, access control, and data protection. The market serves a wide range of industries aiming to secure their growing number of distributed and mobile endpoints in both on-premises and cloud environments.
Which region is expected to have the largest market share in the endpoint security market?
North America is expected to account for the largest market share during the forecast period.
Who are the major market players covered in the report?
Major vendors include Microsoft (US), Palo Alto Networks (US), Trellix (US), CrowdStrike (US), Xcitium (US), Optiv (US), Deep Instinct (US), Securden (India), Morphisec (Israel), Coro (US), IBM (US), Trend Micro (Japan), SentinelOne (US), Sophos (UK), Broadcom (US), Elastic (US), Cybereason (US), Vipre Security (US), Acronis (Switzerland), VMware (US), Blackberry (Canada), ESET (Slovakia), Fortinet (US), Cisco (US), Check Point (Israel), and Kaspersky (Russia).
What is the current size of the global endpoint security market?
In 2025, the global endpoint security market is estimated to reach USD 27.46 billion.
Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the Endpoint Security Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free CustomisationGrowth opportunities and latent adjacency in Endpoint Security Market













Ralph
Feb, 2021
I would like to understand the COVID impact on EDR.