TABLE OF CONTENTS
1 INTRODUCTION (Page No. - 53)
1.1 STUDY OBJECTIVES
1.2 MARKET DEFINITION
1.2.1 INCLUSIONS AND EXCLUSIONS
1.3 MARKET SCOPE
1.3.1 MARKET SEGMENTATION
1.3.2 REGIONS COVERED
1.4 YEARS CONSIDERED
1.5 CURRENCY CONSIDERED
TABLE 1 USD EXCHANGE RATES, 2018–2022
1.6 STAKEHOLDERS
1.7 SUMMARY OF CHANGES
2 RESEARCH METHODOLOGY (Page No. - 58)
2.1 RESEARCH DATA
FIGURE 1 IDENTITY AND ACCESS MANAGEMENT MARKET: RESEARCH DESIGN
2.1.1 SECONDARY DATA
2.1.2 PRIMARY DATA
2.1.2.1 Breakup of primary profiles
2.1.2.2 Key industry insights
2.2 DATA TRIANGULATION
FIGURE 2 MARKET: RESEARCH FLOW
2.3 IAM MARKET SIZE ESTIMATION
2.3.1 REVENUE ESTIMATES
FIGURE 3 IAM MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 1, SUPPLY-SIDE ANALYSIS: REVENUE OF SOLUTIONS AS SERVICE IN MARKET
FIGURE 4 IAM MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 1, SUPPLY-SIDE ANALYSIS
FIGURE 5 IAM MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 2, BOTTOM-UP (SUPPLY SIDE): COLLECTIVE REVENUE FROM ALL SOLUTIONS IN IDENTITY AND ACCESS MANAGEMENT MARKET
2.3.2 DEMAND-SIDE ANALYSIS
FIGURE 6 IAM MARKET SIZE ESTIMATION METHODOLOGY—APPROACH 3, BOTTOM-UP (DEMAND SIDE)
2.4 COMPANY EVALUATION QUADRANT METHODOLOGY
FIGURE 7 COMPANY EVALUATION QUADRANT: CRITERIA WEIGHTAGE
2.5 STARTUP EVALUATION QUADRANT METHODOLOGY
FIGURE 8 STARTUP EVALUATION QUADRANT: CRITERIA WEIGHTAGE
2.6 MARKET FORECAST
TABLE 2 FACTOR ANALYSIS
2.7 ASSUMPTIONS OF THE STUDY
2.8 LIMITATIONS OF THE STUDY
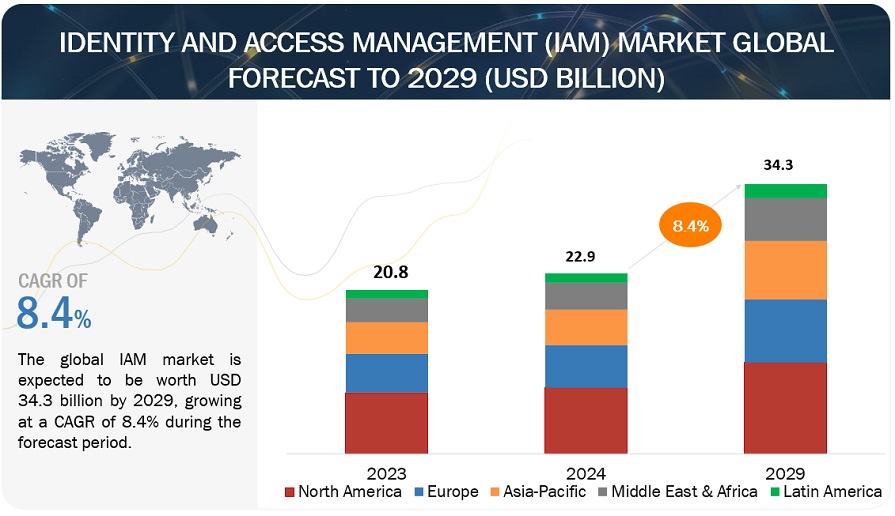
3 EXECUTIVE SUMMARY (Page No. - 69)
TABLE 3 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE AND GROWTH, 2017–2022 (USD MILLION, Y-O-Y %)
TABLE 4 MARKET SIZE AND GROWTH, 2023–2028 (USD MILLION, Y-O-Y %)
FIGURE 9 MARKET TO GROW MODERATELY FROM 2023 TO 2028 DUE TO RECESSION
FIGURE 10 NORTH AMERICA TO ACCOUNT FOR LARGEST MARKET SHARE IN 2023
4 PREMIUM INSIGHTS (Page No. - 72)
4.1 OVERVIEW OF IDENTITY AND ACCESS MANAGEMENT INDUSTRY
FIGURE 11 RISING INSTANCES OF SECURITY BREACHES AND IDENTITY RELATED FRAUD TO DRIVE MARKET
4.2 IAM MARKET, BY TYPE
FIGURE 12 CONSUMER IAM SEGMENT TO ACCOUNT FOR LARGER SHARE IN 2023
4.3 IAM MARKET, BY OFFERING
FIGURE 13 SOLUTIONS SEGMENT TO ACCOUNT FOR LARGER SHARE IN 2023
4.4 IAM MARKET, BY SOLUTION
FIGURE 14 IDENTITY LIFECYCLE MANAGEMENT SEGMENT TO ACCOUNT FOR LARGEST SHARE IN 2023
4.5 IAM MARKET, BY IDENTITY LIFECYCLE MANAGEMENT
FIGURE 15 PROVISIONING SEGMENT TO ACCOUNT FOR LARGER SHARE IN 2023
4.6 IAM MARKET, BY SERVICE
FIGURE 16 INTEGRATION AND DEPLOYMENT SEGMENT TO ACCOUNT FOR LARGEST SHARE IN 2023
4.7 IAM MARKET, BY DEPLOYMENT MODE
FIGURE 17 CLOUD SEGMENT TO ACCOUNT FOR LARGER SHARE IN 2023
4.8 IAM MARKET SHARE OF TOP THREE VERTICALS AND REGIONS, 2023
FIGURE 18 BFSI VERTICAL AND NORTH AMERICA REGION TO ACCOUNT FOR LARGEST SHARE IN 2023
4.9 MARKET INVESTMENT SCENARIO
FIGURE 19 ASIA PACIFIC TO EMERGE AS BEST MARKET FOR INVESTMENTS IN NEXT FIVE YEARS
5 MARKET OVERVIEW AND INDUSTRY TRENDS (Page No. - 77)
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
FIGURE 20 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES: CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET
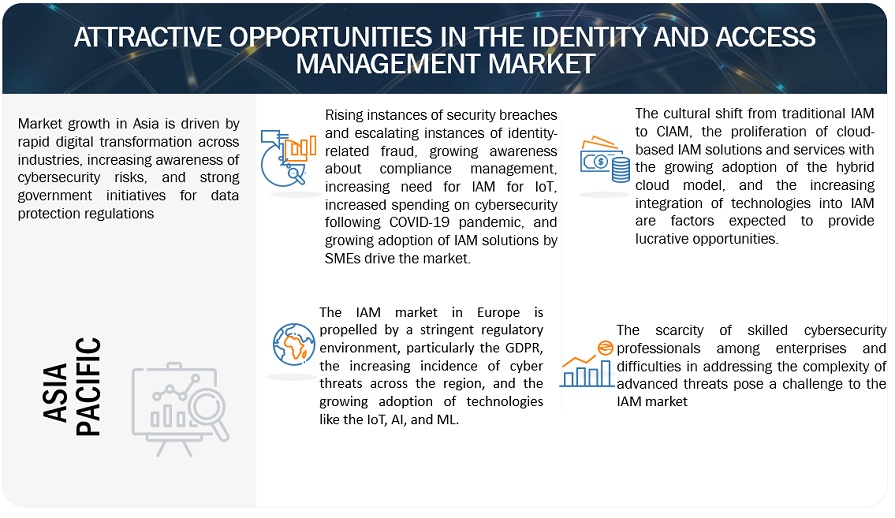
5.2.1 DRIVERS
5.2.1.1 Rising instances of security breaches and identity-related fraud
FIGURE 21 IDENTITY THEFT REPORT IN US
5.2.1.2 Growing awareness about compliance management
5.2.1.3 Increasing need for IAM for IoT
5.2.1.4 Increased spending on cybersecurity following COVID-19 pandemic
5.2.2 RESTRAINTS
5.2.2.1 Lack of identity standards and budgetary constraints in deploying IAM solutions
5.2.3 OPPORTUNITIES
5.2.3.1 Cultural shift from traditional IAM to CIAM
5.2.3.2 Proliferation of cloud-based IAM solutions and services and growing adoption of hybrid cloud model
5.2.3.3 Increasing integration of technologies into IAM
5.2.4 CHALLENGES
5.2.4.1 Scarcity of skilled cybersecurity professionals among enterprises
5.2.4.2 Difficulties in addressing complexity of advanced threats
5.3 VALUE CHAIN ANALYSIS
FIGURE 22 VALUE CHAIN ANALYSIS OF IDENTITY AND ACCESS MANAGEMENT MARKET
5.4 ECOSYSTEM: IDENTITY AND ACCESS MANAGEMENT
5.5 AVERAGE SELLING PRICE/PRICING MODEL OF IDENTITY AND ACCESS MANAGEMENT SOLUTIONS
5.6 TECHNOLOGY ANALYSIS
5.6.1 ARTIFICIAL INTELLIGENCE
5.6.2 BLOCKCHAIN
5.7 PATENT ANALYSIS
FIGURE 23 MARKET: PATENT ANALYSIS
TABLE 5 LIST OF PATENTS IN MARKET, 2022
5.8 TRENDS AND DISRUPTIONS IMPACTING CUSTOMERS
FIGURE 24 MARKET: TRENDS AND DISRUPTIONS IMPACTING CUSTOMERS
5.9 PORTER’S FIVE FORCES ANALYSIS
FIGURE 25 PORTER’S FIVE FORCES MODEL FOR MARKET
TABLE 6 PORTER'S FIVE FORCES IMPACT ON IDENTITY AND ACCESS MANAGEMENT MARKET
5.9.1 THREAT OF NEW ENTRANTS
5.9.2 THREAT OF SUBSTITUTES
5.9.3 BARGAINING POWER OF SUPPLIERS
5.9.4 BARGAINING POWER OF BUYERS
5.9.5 INTENSITY OF COMPETITIVE RIVALRY
5.10 KEY STAKEHOLDERS
5.10.1 KEY STAKEHOLDERS IN BUYING PROCESS
FIGURE 26 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS (%)
TABLE 7 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS (%)
5.11 TARIFF AND REGULATORY LANDSCAPE
5.11.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 8 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 9 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 10 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 11 REST OF THE WORLD: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
5.11.2 PAYMENT CARD INDUSTRY-DATA SECURITY STANDARD (PCI-DSS)
5.11.3 HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT (HIPAA)
5.11.4 FEDERAL INFORMATION SECURITY MANAGEMENT ACT (FISMA)
5.11.5 SARBANES-OXLEY ACT (SOX)
5.11.6 SOC2
5.12 USE CASES
5.12.1 USE CASE 1: PAMEIJER CONTINUES TO INNOVATE ON CUSTOMER EXPERIENCE WITH HELP OF PING IDENTITY
5.12.2 USE CASE 2: T-MOBILE UPGRADED TO SECURE SOLUTION TO HELP STAFF MEMBERS CONCENTRATE ON CONSUMERS
5.12.3 USE CASE 3: WWK ESTABLISHES FORGEROCK-BASED SINGLE SIGN-ON FOR IMPROVED SERVICE AND SECURITY
5.12.4 USE CASE 4: AVANCER HELPED HOSPITAL WITH SELF-SERVICE ADMINISTRATIVE IT FEATURES AUTOMATE ACCESS GOVERNANCE
5.12.5 USE CASE 5: GENESIS ENERGY INTEGRATED AZURE AD B2C PLATFORM INTO THEIR WEB AND MOBILE APP
5.13 KEY CONFERENCES AND EVENTS IN 2023
TABLE 12 MARKET: LIST OF CONFERENCES AND EVENTS
6 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE (Page No. - 97)
6.1 INTRODUCTION
FIGURE 27 CONSUMER IAM SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
TABLE 13 MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 14 MARKET, BY TYPE, 2023–2028 (USD MILLION)
6.2 WORKFORCE IAM
6.2.1 STRIKING BALANCE BETWEEN SECURITY AND COMPLIANCE
6.2.2 WORKFORCE IAM: MARKET DRIVERS
TABLE 15 WORKFORCE IAM: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 16 WORKFORCE IAM: MARKET, BY REGION, 2023–2028 (USD MILLION)
6.3 CONSUMER IAM
6.3.1 MANAGING AND CONTROLLING CUSTOMER ACCESS
6.3.2 CONSUMER IAM: MARKET DRIVERS
TABLE 17 CONSUMER IAM: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 18 CONSUMER IAM: MARKET, BY REGION, 2023–2028 (USD MILLION)
7 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING (Page No. - 102)
7.1 INTRODUCTION
FIGURE 28 SERVICES SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
TABLE 19 MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 20 MARKET, BY OFFERING, 2023–2028 (USD MILLION)
7.2 SOLUTIONS
7.2.1 CUSTOMIZING USER EXPERIENCE TO ENSURE SMOOTH FUNCTIONING
7.2.2 SOLUTIONS: MARKET DRIVERS
TABLE 21 SOLUTIONS: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 22 SOLUTIONS: MARKET, BY REGION, 2023–2028 (USD MILLION)
7.3 SERVICES
7.3.1 DYNAMIC SERVICES FULFILL CUSTOMIZED REQUIREMENTS
7.3.2 SERVICES: MARKET DRIVERS
TABLE 23 SERVICES: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 24 SERVICES: MARKET, BY REGION, 2023–2028 (USD MILLION)
8 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SOLUTION (Page No. - 107)
8.1 INTRODUCTION
FIGURE 29 VERIFICATION SEGMENT TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
TABLE 25 MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 26 MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
8.2 DATA DIRECTORY
8.2.1 CENTRALIZED INFORMATION REPOSITORY ASSISTING ACCESS MANAGEMENT
8.2.2 DATA DIRECTORY: MARKET DRIVERS
TABLE 27 DATA DIRECTORY: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 28 DATA DIRECTORY: MARKET, BY REGION, 2023–2028 (USD MILLION)
8.3 IDENTITY LIFECYCLE MANAGEMENT
8.3.1 MANAGING EMPLOYEE LIFE CYCLE TO ENSURE SYSTEMATIC FUNCTIONING
8.3.2 IDENTITY LIFECYCLE MANAGEMENT: MARKET DRIVERS
TABLE 29 IDENTITY LIFECYCLE MANAGEMENT: IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 30 IDENTITY LIFECYCLE MANAGEMENT: MARKET, BY REGION, 2023–2028 (USD MILLION)
TABLE 31 IDENTITY LIFECYCLE MANAGEMENT: MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 32 IDENTITY LIFECYCLE MANAGEMENT: MARKET, BY TYPE, 2023–2028 (USD MILLION)
8.3.3 PROVISIONING
TABLE 33 IDENTITY LIFECYCLE MANAGEMENT: PROVISIONING MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 34 IDENTITY LIFECYCLE MANAGEMENT: PROVISIONING MARKET, BY REGION, 2023–2028 (USD MILLION)
8.3.4 DE-PROVISIONING
TABLE 35 IDENTITY LIFECYCLE MANAGEMENT: DE-PROVISIONING MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 36 IDENTITY LIFECYCLE MANAGEMENT: DE-PROVISIONING MARKET, BY REGION, 2023–2028 (USD MILLION)
8.4 AUTHENTICATION
8.4.1 IMPORTANCE OF SAFEGUARDING ORGANIZATION’S NETWORK
8.4.2 AUTHENTICATION: MARKET DRIVERS
TABLE 37 AUTHENTICATION: IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 38 AUTHENTICATION: MARKET, BY REGION, 2023–2028 (USD MILLION)
8.4.3 SINGLE-FACTOR AUTHENTICATION
8.4.4 TWO-FACTOR AUTHENTICATION
8.4.5 MULTI-FACTOR AUTHENTICATION
8.5 VERIFICATION
8.5.1 NEED FOR MULTI-LEVEL VERIFICATION ANALYSIS
8.5.2 VERIFICATION: MARKET DRIVERS
TABLE 39 VERIFICATION: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 40 VERIFICATION: MARKET, BY REGION, 2023–2028 (USD MILLION)
8.6 ACCESS MANAGEMENT AND AUTHORIZATION
8.6.1 IDENTITY AUTHENTICATION AND ITS ASSOCIATED ACCESS RIGHTS
8.6.2 ACCESS MANAGEMENT AND AUTHORIZATION: MARKET DRIVERS
TABLE 41 ACCESS MANAGEMENT AND AUTHORIZATION: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 42 ACCESS MANAGEMENT AND AUTHORIZATION: MARKET, BY REGION, 2023–2028 (USD MILLION)
8.7 AUDIT, COMPLIANCE, AND GOVERNANCE
8.7.1 COMPLIANCE BOOSTING TRANSPARENCY ACROSS ORGANIZATIONS
8.7.2 AUDIT, COMPLIANCE, AND GOVERNANCE: MARKET DRIVERS
TABLE 43 AUDIT, COMPLIANCE, AND GOVERNANCE: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 44 AUDIT, COMPLIANCE, AND GOVERNANCE: MARKET, BY REGION, 2023–2028 (USD MILLION)
9 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE (Page No. - 120)
9.1 INTRODUCTION
FIGURE 30 SUPPORT AND MAINTENANCE SEGMENT TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
TABLE 45 MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 46 MARKET, BY SERVICE, 2023–2028 (USD MILLION)
9.2 INTEGRATION AND DEPLOYMENT
9.2.1 SIGNIFICANCE OF FORMULATING APPROPRIATE IAM STRATEGIES
9.2.2 INTEGRATION AND DEPLOYMENT: MARKET DRIVERS
TABLE 47 INTEGRATION AND DEPLOYMENT: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 48 INTEGRATION AND DEPLOYMENT: MARKET, BY REGION, 2023–2028 (USD MILLION)
9.3 SUPPORT AND MAINTENANCE
9.3.1 IMPORTANCE OF STRONG SUPPORT AND MAINTENANCE SERVICES
9.3.2 SUPPORT AND MAINTENANCE: MARKET DRIVERS
TABLE 49 SUPPORT AND MAINTENANCE: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 50 SUPPORT AND MAINTENANCE: MARKET, BY REGION, 2023–2028 (USD MILLION)
9.4 CONSULTING
9.4.1 CONSULTING SERVICES TO ENHANCE INFORMATION SECURITY
9.4.2 CONSULTING: MARKET DRIVERS
TABLE 51 CONSULTING: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 52 CONSULTING: MARKET, BY REGION, 2023–2028 (USD MILLION)
10 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE (Page No. - 126)
10.1 INTRODUCTION
FIGURE 31 CLOUD SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
TABLE 53 MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 54 MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
10.2 CLOUD
10.2.1 EMERGENCE OF SAAS-BASED IAM SERVICES
10.2.2 CLOUD: MARKET DRIVERS
TABLE 55 CLOUD: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 56 CLOUD: MARKET, BY REGION, 2023–2028 (USD MILLION)
10.3 ON-PREMISES
10.3.1 TRADITIONAL PRACTICES STRENGTHENING IN-HOUSE CONTROL
10.3.2 ON-PREMISES: MARKET DRIVERS
TABLE 57 ON-PREMISES: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 58 ON-PREMISES: MARKET, BY REGION, 2023–2028 (USD MILLION)
11 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL (Page No. - 130)
11.1 INTRODUCTION
FIGURE 32 HEALTHCARE SEGMENT TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
TABLE 59 MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 60 MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
11.2 BANKING, FINANCIAL SERVICES, AND INSURANCE
11.2.1 DIGITAL INITIATIVES LEADING TO HIGHER ADOPTION OF IAM
11.2.2 BANKING, FINANCIAL SERVICES, AND INSURANCE: MARKET DRIVERS
TABLE 61 BANKING, FINANCIAL SERVICES, AND INSURANCE: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 62 BANKING, FINANCIAL SERVICES, AND INSURANCE: MARKET, BY REGION, 2023–2028 (USD MILLION)
11.3 TRAVEL, TOURISM, AND HOSPITALITY
11.3.1 CIAM STRENGTHENING INDUSTRY BY ENHANCING BRAND LOYALTY
11.3.2 TRAVEL, TOURISM, AND HOSPITALITY: MARKET DRIVERS
TABLE 63 TRAVEL, TOURISM, AND HOSPITALITY: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 64 TRAVEL, TOURISM, AND HOSPITALITY: MARKET, BY REGION, 2023–2028 (USD MILLION)
11.4 HEALTHCARE
11.4.1 TECHNOLOGICAL ADVANCEMENTS SUPPORTING ADOPTION OF IAM
11.4.2 HEALTHCARE: MARKET DRIVERS
TABLE 65 HEALTHCARE: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 66 HEALTHCARE: MARKET, BY REGION, 2023–2028 (USD MILLION)
11.5 RETAIL AND E-COMMERCE
11.5.1 OPTIMIZING COST AND ENHANCING PRODUCTION WITH ADOPTION OF IAM
11.5.2 RETAIL AND ECOMMERCE: MARKET DRIVERS
TABLE 67 RETAIL AND ECOMMERCE: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 68 RETAIL AND ECOMMERCE: MARKET, BY REGION, 2023–2028 (USD MILLION)
11.6 INFORMATION TECHNOLOGY & INFORMATION TECHNOLOGY-ENABLED SERVICES
11.6.1 DATA EVOLUTION TO BOOST ADOPTION OF IAM
11.6.2 INFORMATION TECHNOLOGY & INFORMATION TECHNOLOGY-ENABLED SERVICES: MARKET DRIVERS
TABLE 69 INFORMATION TECHNOLOGY & INFORMATION TECHNOLOGY-ENABLED SERVICES: IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 70 INFORMATION TECHNOLOGY & INFORMATION TECHNOLOGY-ENABLED SERVICES: MARKET, BY REGION, 2023–2028 (USD MILLION)
11.7 EDUCATION
11.7.1 SAFEGUARDING CRITICAL ASSETS ALONG WITH THEIR CREDENTIALS
11.7.2 EDUCATION: MARKET DRIVERS
TABLE 71 EDUCATION: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 72 EDUCATION: MARKET, BY REGION, 2023–2028 (USD MILLION)
11.8 GOVERNMENT AND DEFENSE
11.8.1 BOLSTERING NEED FOR DATA SECURITY AND COMPLIANCE
11.8.2 GOVERNMENT AND DEFENSE: MARKET DRIVERS
TABLE 73 GOVERNMENT: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 74 GOVERNMENT: MARKET, BY REGION, 2023–2028 (USD MILLION)
11.9 OTHER VERTICALS
TABLE 75 OTHER VERTICALS: MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 76 OTHER VERTICALS: MARKET, BY REGION, 2023–2028 (USD MILLION)
12 MARKET, BY REGION (Page No. - 142)
12.1 INTRODUCTION
FIGURE 33 ASIA PACIFIC TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
TABLE 77 MARKET, BY REGION, 2017–2022 (USD MILLION)
TABLE 78 MARKET, BY REGION, 2023–2028 (USD MILLION)
12.2 NORTH AMERICA
12.2.1 NORTH AMERICA: MARKET DRIVERS
12.2.2 NORTH AMERICA: RECESSION IMPACT
12.2.3 NORTH AMERICA: REGULATORY LANDSCAPE
FIGURE 34 NORTH AMERICA MARKET SNAPSHOT
TABLE 79 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 80 NORTH AMERICA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 81 NORTH AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 82 NORTH AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 83 NORTH AMERICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 84 NORTH AMERICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 85 NORTH AMERICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 86 NORTH AMERICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 87 NORTH AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 88 NORTH AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 89 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 90 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 91 NORTH AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 92 NORTH AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
TABLE 93 NORTH AMERICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
TABLE 94 NORTH AMERICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
12.2.4 US
12.2.4.1 Technological advancements and presence of key vendors offering IAM solutions
TABLE 95 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 96 US: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 97 US: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 98 US: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 99 US: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 100 US: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 101 US: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 102 US: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 103 US: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 104 US: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 105 US: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 106 US: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 107 US: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 108 US: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.2.5 CANADA
12.2.5.1 Increased adoption of advanced AI- and ML-based identity verification solutions
TABLE 109 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 110 CANADA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 111 CANADA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 112 CANADA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 113 CANADA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 114 CANADA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 115 CANADA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 116 CANADA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 117 CANADA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 118 CANADA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 119 CANADA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 120 CANADA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 121 CANADA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 122 CANADA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.3 EUROPE
12.3.1 EUROPE: MARKET DRIVERS
12.3.2 EUROPE: RECESSION IMPACT
12.3.3 EUROPE: REGULATORY LANDSCAPE
TABLE 123 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 124 EUROPE: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 125 EUROPE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 126 EUROPE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 127 EUROPE: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 128 EUROPE: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 129 EUROPE: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 130 EUROPE: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 131 EUROPE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 132 EUROPE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 133 EUROPE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 134 EUROPE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 135 EUROPE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 136 EUROPE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
TABLE 137 EUROPE: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
TABLE 138 EUROPE: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
12.3.4 UK
12.3.4.1 Strict regulations and government initiatives
TABLE 139 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 140 UK: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 141 UK: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 142 UK: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 143 UK: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 144 UK: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 145 UK: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 146 UK: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 147 UK: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 148 UK: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 149 UK: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 150 UK: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 151 UK: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 152 UK: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.3.5 GERMANY
12.3.5.1 Country’s strong automobile industry to adopt IAM solutions
TABLE 153 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 154 GERMANY: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 155 GERMANY: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 156 GERMANY: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 157 GERMANY: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 158 GERMANY: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 159 GERMANY: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 160 GERMANY: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 161 GERMANY: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 162 GERMANY: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 163 GERMANY: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 164 GERMANY: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 165 GERMANY: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 166 GERMANY: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.3.6 FRANCE
12.3.6.1 Robust economy and high awareness related to identity verification solutions
TABLE 167 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 168 FRANCE: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 169 FRANCE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 170 FRANCE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 171 FRANCE: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 172 FRANCE: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 173 FRANCE: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 174 FRANCE: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 175 FRANCE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 176 FRANCE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 177 FRANCE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 178 FRANCE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 179 FRANCE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 180 FRANCE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.3.7 REST OF EUROPE
TABLE 181 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 182 REST OF EUROPE: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 183 REST OF EUROPE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 184 REST OF EUROPE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 185 REST OF EUROPE: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 186 REST OF EUROPE: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 187 REST OF EUROPE: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 188 REST OF EUROPE: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 189 REST OF EUROPE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 190 REST OF EUROPE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 191 REST OF EUROPE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 192 REST OF EUROPE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 193 REST OF EUROPE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 194 REST OF EUROPE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.4 ASIA PACIFIC
12.4.1 ASIA PACIFIC: MARKET DRIVERS
12.4.2 ASIA PACIFIC: RECESSION IMPACT
12.4.3 ASIA PACIFIC: REGULATORY LANDSCAPE
FIGURE 35 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET SNAPSHOT
TABLE 195 ASIA PACIFIC: MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 196 ASIA PACIFIC: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 197 ASIA PACIFIC: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 198 ASIA PACIFIC: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 199 ASIA PACIFIC: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 200 ASIA PACIFIC: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 201 ASIA PACIFIC: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 202 ASIA PACIFIC: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 203 ASIA PACIFIC: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 204 ASIA PACIFIC: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 205 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 206 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 207 ASIA PACIFIC: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 208 ASIA PACIFIC: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
TABLE 209 ASIA PACIFIC: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
TABLE 210 ASIA PACIFIC: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
12.4.4 CHINA
12.4.4.1 Various government initiatives to drive IAM adoption
TABLE 211 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 212 CHINA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 213 CHINA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 214 CHINA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 215 CHINA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 216 CHINA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 217 CHINA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 218 CHINA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 219 CHINA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 220 CHINA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 221 CHINA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 222 CHINA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 223 CHINA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 224 CHINA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.4.5 JAPAN
12.4.5.1 Initial adopter of high-end technology
TABLE 225 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 226 JAPAN: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 227 JAPAN: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 228 JAPAN: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 229 JAPAN: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 230 JAPAN: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 231 JAPAN: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 232 JAPAN: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 233 JAPAN: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 234 JAPAN: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 235 JAPAN: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 236 JAPAN: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 237 JAPAN: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 238 JAPAN: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.4.6 AUSTRALIA
12.4.6.1 New bills and commissions formed by government to generate IAM awareness
TABLE 239 AUSTRALIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 240 AUSTRALIA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 241 AUSTRALIA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 242 AUSTRALIA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 243 AUSTRALIA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 244 AUSTRALIA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 245 AUSTRALIA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 246 AUSTRALIA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 247 AUSTRALIA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 248 AUSTRALIA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 249 AUSTRALIA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 250 AUSTRALIA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 251 AUSTRALIA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 252 AUSTRALIA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.4.7 INDIA
12.4.7.1 Digital KYC solutions in banking and gambling industries to lower cost of onboarding new customers
TABLE 253 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 254 INDIA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 255 INDIA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 256 INDIA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 257 INDIA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 258 INDIA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 259 INDIA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 260 INDIA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 261 INDIA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 262 INDIA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 263 INDIA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 264 INDIA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 265 INDIA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 266 INDIA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.4.8 REST OF ASIA PACIFIC
TABLE 267 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 268 REST OF ASIA PACIFIC: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 269 REST OF ASIA PACIFIC: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 270 REST OF ASIA PACIFIC: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 271 REST OF ASIA PACIFIC: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 272 REST OF ASIA PACIFIC: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 273 REST OF ASIA PACIFIC: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 274 REST OF ASIA PACIFIC: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 275 REST OF ASIA PACIFIC: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 276 REST OF ASIA PACIFIC: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 277 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 278 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 279 REST OF ASIA PACIFIC: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 280 REST OF ASIA PACIFIC: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.5 MIDDLE EAST AND AFRICA
12.5.1 MIDDLE EAST AND AFRICA: MARKET DRIVERS
12.5.2 MIDDLE EAST AND AFRICA: RECESSION IMPACT
12.5.3 MIDDLE EAST AND AFRICA: REGULATORY LANDSCAPE
TABLE 281 MIDDLE EAST AND AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 282 MIDDLE EAST AND AFRICA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 283 MIDDLE EAST AND AFRICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 284 MIDDLE EAST AND AFRICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 285 MIDDLE EAST AND AFRICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 286 MIDDLE EAST AND AFRICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 287 MIDDLE EAST AND AFRICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 288 MIDDLE EAST AND AFRICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 289 MIDDLE EAST AND AFRICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 290 MIDDLE EAST AND AFRICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 291 MIDDLE EAST AND AFRICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 292 MIDDLE EAST AND AFRICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 293 MIDDLE EAST AND AFRICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 294 MIDDLE EAST AND AFRICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
TABLE 295 MIDDLE EAST AND AFRICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
TABLE 296 MIDDLE EAST AND AFRICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
12.5.4 MIDDLE EAST
12.5.4.1 Growing security concerns and rising identity theft attacks
TABLE 297 MIDDLE EAST: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 298 MIDDLE EAST: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 299 MIDDLE EAST: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 300 MIDDLE EAST: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 301 MIDDLE EAST: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 302 MIDDLE EAST: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 303 MIDDLE EAST: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 304 MIDDLE EAST: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 305 MIDDLE EAST: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 306 MIDDLE EAST: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 307 MIDDLE EAST: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 308 MIDDLE EAST: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 309 MIDDLE EAST: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 310 MIDDLE EAST: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.5.5 AFRICA
12.5.5.1 Increase in crimes leading to adoption of several security solutions
TABLE 311 AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 312 AFRICA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 313 AFRICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 314 AFRICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 315 AFRICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 316 AFRICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 317 AFRICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 318 AFRICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 319 AFRICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 320 AFRICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 321 AFRICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 322 AFRICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 323 AFRICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 324 AFRICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.6 LATIN AMERICA
12.6.1 LATIN AMERICA: MARKET DRIVERS
12.6.2 LATIN AMERICA: RECESSION IMPACT
12.6.3 LATIN AMERICA: REGULATORY LANDSCAPE
TABLE 325 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 326 LATIN AMERICA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 327 LATIN AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 328 LATIN AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 329 LATIN AMERICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 330 LATIN AMERICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 331 LATIN AMERICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 332 LATIN AMERICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 333 LATIN AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 334 LATIN AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 335 LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 336 LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 337 LATIN AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 338 LATIN AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
TABLE 339 LATIN AMERICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
TABLE 340 LATIN AMERICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
12.6.4 MEXICO
12.6.4.1 KYC and digital onboarding procedures to drive demand for IAM solutions
TABLE 341 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 342 MEXICO: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 343 MEXICO: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 344 MEXICO: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 345 MEXICO: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 346 MEXICO: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 347 MEXICO: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 348 MEXICO: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 349 MEXICO: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 350 MEXICO: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 351 MEXICO: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 352 MEXICO: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 353 MEXICO: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 354 MEXICO: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.6.5 BRAZIL
12.6.5.1 Demand for IAM to boost startups
TABLE 355 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 356 BRAZIL: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 357 BRAZIL: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 358 BRAZIL: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 359 BRAZIL: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 360 BRAZIL: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 361 BRAZIL: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 362 BRAZIL: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 363 BRAZIL: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 364 BRAZIL: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 365 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 366 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 367 BRAZIL: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 368 BRAZIL: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
12.6.6 REST OF LATIN AMERICA
TABLE 369 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
TABLE 370 REST OF LATIN AMERICA: MARKET, BY TYPE, 2023–2028 (USD MILLION)
TABLE 371 REST OF LATIN AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
TABLE 372 REST OF LATIN AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
TABLE 373 REST OF LATIN AMERICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
TABLE 374 REST OF LATIN AMERICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
TABLE 375 REST OF LATIN AMERICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2017–2022 (USD MILLION)
TABLE 376 REST OF LATIN AMERICA: MARKET, BY IDENTITY LIFECYCLE MANAGEMENT, 2023–2028 (USD MILLION)
TABLE 377 REST OF LATIN AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
TABLE 378 REST OF LATIN AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
TABLE 379 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
TABLE 380 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
TABLE 381 REST OF LATIN AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
TABLE 382 REST OF LATIN AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
13 COMPETITIVE LANDSCAPE (Page No. - 250)
13.1 OVERVIEW
13.2 REVENUE ANALYSIS OF KEY PLAYERS
FIGURE 36 REVENUE ANALYSIS FOR KEY PLAYERS, 2020–2022 (USD MILLION)
13.3 MARKET RANKING OF KEY PLAYERS
FIGURE 37 MARKET RANKING OF KEY PLAYERS
13.4 MARKET SHARE ANALYSIS
FIGURE 38 MARKET SHARE ANALYSIS, 2022
TABLE 383 INTENSITY OF COMPETITIVE RIVALRY
13.5 EVALUATION QUADRANT FOR KEY PLAYERS, 2023
13.5.1 STARS
13.5.2 EMERGING LEADERS
13.5.3 PERVASIVE PLAYERS
13.5.4 PARTICIPANTS
13.6 COMPETITIVE BENCHMARKING FOR KEY PLAYERS
13.6.1 COMPANY FOOTPRINT
TABLE 384 COMPANY FOOTPRINT, BY SOLUTION
TABLE 385 COMPANY FOOTPRINT, BY VERTICAL
TABLE 386 COMPANY FOOTPRINT, BY REGION
TABLE 387 KEY COMPANY OVERALL FOOTPRINT
FIGURE 39 EVALUATION QUADRANT FOR KEY PLAYERS, 2023
13.7 COMPETITIVE BENCHMARKING FOR STARTUPS/SMES
TABLE 388 LIST OF STARTUPS/SMES
TABLE 389 COMPANY FOOTPRINT FOR STARTUPS/SMES, BY SOLUTION
TABLE 390 COMPANY FOOTPRINT FOR STARTUPS/SMES, BY VERTICAL
TABLE 391 COMPANY FOOTPRINT FOR STARTUPS/SMES, BY REGION
TABLE 392 KEY COMPANY OVERALL FOOTPRINT FOR STARTUPS/SMES
13.8 EVALUATION QUADRANT FOR STARTUPS/SMES, 2023
13.8.1 PROGRESSIVE COMPANIES
13.8.2 RESPONSIVE COMPANIES
13.8.3 DYNAMIC COMPANIES
13.8.4 STARTING BLOCKS
FIGURE 40 EVALUATION QUADRANT FOR STARTUPS/SMES, 2023
13.9 VALUATION AND FINANCIAL METRICS OF IDENTITY AND ACCESS MANAGEMENT VENDORS
FIGURE 41 VALUATION AND FINANCIAL METRICS OF IDENTITY AND ACCESS MANAGEMENT VENDORS
13.10 COMPETITIVE SCENARIO
TABLE 393 MARKET: PRODUCT LAUNCHES, 2020—2022
TABLE 394 IDENTITY AND ACCESS MANAGEMENT MARKET: DEALS, 2020—2023
14 COMPANY PROFILES (Page No. - 271)
14.1 KEY PLAYERS
(Business overview, Products/Solutions/Services offered, Recent developments, MnM view, Right to win, Strategic choices, and Weaknesses and competitive threats)*
14.1.1 MICROSOFT
TABLE 395 MICROSOFT: BUSINESS OVERVIEW
FIGURE 42 MICROSOFT: COMPANY SNAPSHOT
TABLE 396 MICROSOFT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 397 MICROSOFT: PRODUCT LAUNCHES
TABLE 398 MICROSOFT: DEALS
14.1.2 OKTA
TABLE 399 OKTA: BUSINESS OVERVIEW
FIGURE 43 OKTA: COMPANY SNAPSHOT
TABLE 400 OKTA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 401 OKTA: PRODUCT LAUNCHES
TABLE 402 OKTA: DEALS
14.1.3 IBM
TABLE 403 IBM: BUSINESS OVERVIEW
FIGURE 44 IBM: COMPANY SNAPSHOT
TABLE 404 IBM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 405 IBM: PRODUCT LAUNCHES
TABLE 406 IBM: DEALS
14.1.4 ORACLE
TABLE 407 ORACLE: BUSINESS OVERVIEW
FIGURE 45 ORACLE: COMPANY SNAPSHOT
TABLE 408 ORACLE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 409 ORACLE: PRODUCT LAUNCHES
TABLE 410 ORACLE: DEALS
14.1.5 SALESFORCE
TABLE 411 SALESFORCE: BUSINESS OVERVIEW
FIGURE 46 SALESFORCE: COMPANY SNAPSHOT
TABLE 412 SALESFORCE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 413 SALESFORCE: DEALS
14.1.6 PING IDENTITY
TABLE 414 PING IDENTITY: BUSINESS OVERVIEW
FIGURE 47 PING IDENTITY: COMPANY SNAPSHOT
TABLE 415 PING IDENTITY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 416 PING IDENTITY: PRODUCT LAUNCHES
TABLE 417 PING IDENTITY: DEALS
14.1.7 HID GLOBAL
TABLE 418 HID GLOBAL: BUSINESS OVERVIEW
TABLE 419 HID GLOBAL: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 420 HID GLOBAL: PRODUCT LAUNCHES
TABLE 421 HID GLOBAL: DEALS
14.1.8 FORGEROCK
TABLE 422 FORGEROCK: BUSINESS OVERVIEW
FIGURE 48 FORGEROCK: COMPANY SNAPSHOT
TABLE 423 FORGEROCK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 424 FORGEROCK: PRODUCT LAUNCHES
TABLE 425 FORGEROCK: DEALS
14.1.9 CYBERARK
TABLE 426 CYBERARK: BUSINESS OVERVIEW
FIGURE 49 CYBERARK: COMPANY SNAPSHOT
TABLE 427 CYBERARK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 428 CYBERARK: PRODUCT LAUNCHES
TABLE 429 CYBERARK: DEALS
14.1.10 MICRO FOCUS
TABLE 430 MICRO FOCUS: BUSINESS OVERVIEW
TABLE 431 MICRO FOCUS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 432 MICRO FOCUS: DEALS
14.1.11 THALES
TABLE 433 THALES: BUSINESS OVERVIEW
FIGURE 50 THALES: COMPANY SNAPSHOT
TABLE 434 THALES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
TABLE 435 THALES: DEALS
14.2 OTHER PLAYERS
14.2.1 RSA SECURITY
14.2.2 AVATIER
14.2.3 MANAGEENGINE
14.2.4 SECUREAUTH
14.2.5 EMPOWERID
14.2.6 SAP
14.2.7 SIMEIO
14.2.8 ONE IDENTITY
14.2.9 FUSIONAUTH
14.2.10 AUTH0
14.2.11 IDNOW
14.2.12 ZEPHR
14.2.13 SIGNZY
14.2.14 CIVIC
14.2.15 TRUSONA
14.2.16 BEYOND IDENTITY
14.2.17 AKAMAI
14.2.18 DELINEA
14.2.19 OPTIMAL IDM
14.2.20 NETWRIX
14.2.21 ZOHO VAULT
14.2.22 TRANSMIT SECURITY
*Details on Business overview, Products/Solutions/Services offered, Recent developments, MnM view, Right to win, Strategic choices, and Weaknesses and competitive threats might not be captured in case of unlisted companies.
15 ADJACENT MARKETS (Page No. - 325)
15.1 INTRODUCTION TO ADJACENT MARKETS
TABLE 436 ADJACENT MARKETS AND FORECASTS
15.2 LIMITATIONS
15.3 ADJACENT MARKETS
15.3.1 CYBERSECURITY MARKET
TABLE 437 CYBERSECURITY MARKET, BY SOFTWARE, 2016–2021 (USD MILLION)
TABLE 438 CYBERSECURITY MARKET, BY SOFTWARE, 2022–2027 (USD MILLION)
15.3.2 IDENTITY VERIFICATION MARKET
TABLE 439 IDENTITY VERIFICATION MARKET, BY APPLICATION, 2016–2021 (USD MILLION)
TABLE 440 IDENTITY VERIFICATION MARKET, BY APPLICATION, 2022–2027 (USD MILLION)
15.3.3 DIGITAL IDENTITY SOLUTIONS MARKET
TABLE 441 DIGITAL IDENTITY SOLUTIONS MARKET, BY SOLUTION TYPE, 2016–2021 (USD MILLION)
TABLE 442 DIGITAL IDENTITY SOLUTIONS MARKET, BY SOLUTION TYPE, 2022–2027 (USD MILLION)
15.3.4 CONSUMER IAM MARKET
TABLE 443 CONSUMER MARKET SIZE, BY SOLUTION, 2015–2020 (USD MILLION)
TABLE 444 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SOLUTION, 2021–2026 (USD MILLION)
16 APPENDIX (Page No. - 329)
16.1 DISCUSSION GUIDE
16.2 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
16.3 CUSTOMIZATION OPTIONS
16.4 RELATED REPORTS
16.5 AUTHOR DETAILS




 Generating Response ...
Generating Response ...







Growth opportunities and latent adjacency in Identity and Access Management (IAM) Market