Middle East Cybersecurity Market by Offering (Solutions and Services), Solution Type, Security Type, Deployment Mode (On-Premises, Cloud, Hybrid), Organization Size (Large Enterprises, SME), Vertical and Region - Global Forecast to 2028
Middle East Cybersecurity Market Size, Share - Worldwide
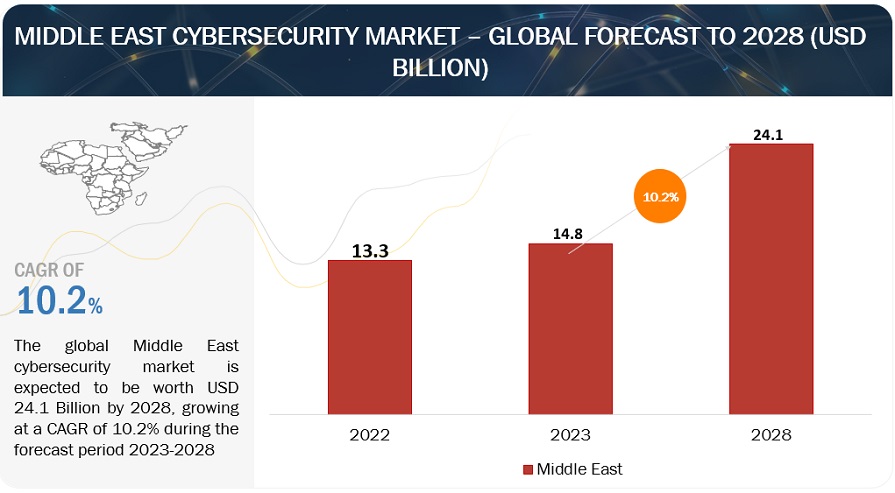
[422 Pages Report] The Middle East Cybersecurity Market size was worth around approximately $14.8 billion in 2023. Over the course of projection period, the middle east cybersecurity industry is anticipated to increase at a CAGR of 9.6% to grow $23.4 billion in 2028. The base year for estimation is 2022 and market size available for the years 2017 to 2028. The expansion of the Middle East cybersecurity industry can be attributed to digital and transformation initiatives by governments and businesses to grow cybersecurity infrastructure. Moreover, the Middle East cybersecurity market is experiencing growth due to the regulatory initiatives evolving threat environment, widespread cloud technology adoption, booming startup ecosystem, rise in demand for cyber-insurance and cyber threats among businesses, government investments, and KSA Vision 2030 to drive the Middle East cybersecurity market dynamics.
To know about the assumptions considered for the study, Request for Free Sample Report
To know about the assumptions considered for the study, download the pdf brochure
Middle East Cybersecurity Market Dynamics
Driver: Security Solutions for Startup.
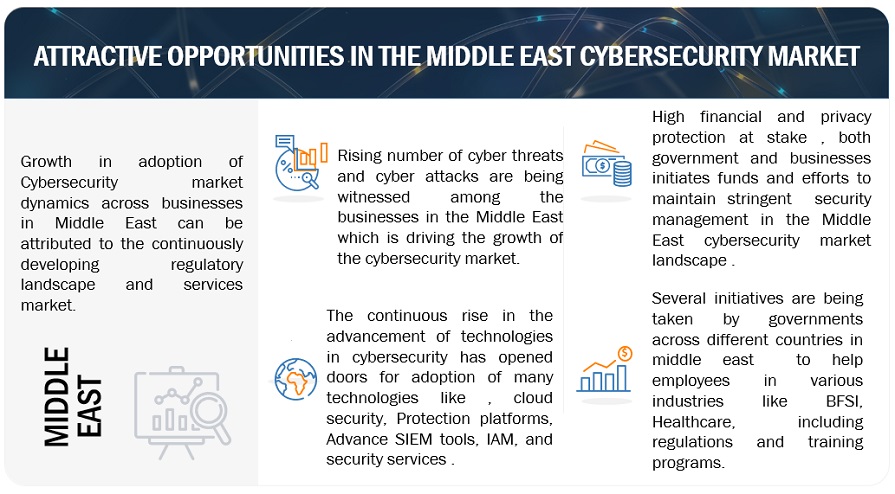
Security solutions encompass a spectrum of tools and tactics crucial for safeguarding burgeoning companies from diverse cyber threats prevalent in the digital landscape. These hazards range from data breaches involving unauthorized access to sensitive information to malware attacks, phishing scams, insider threats, and concerns related to cloud security. Tailoring these solutions for the Middle East's startup ecosystem necessitates addressing regional nuances such as regulatory compliance, resource constraints, and emerging threats. Pertinent security measures include endpoint security, network security, cloud security, identity and access management, penetration testing, security awareness training, and managed security services. Crafting an effective security strategy demands a thoughtful blend of solutions, layered defenses, and vigilant adaptation to the evolving threat landscape within a startup's size, industry, data sensitivity, and budget constraints.
Restraint: Budgetary Constraints on Allocation of Resources
Budgetary constraints in the Middle East cybersecurity market present a hurdle for organizations, particularly startups, struggling to allocate adequate resources to fortify their defenses against cyber threats. This financial limitation often results in insufficient investment in essential security solutions, leaving companies susceptible to common attacks. Challenges in hiring and retaining cybersecurity talent exacerbate the problem, hindering the effective implementation of protective measures. The difficulty in justifying the return on investment for cybersecurity initiatives further complicates matters. This restraint impacts market growth, elevates cyber risks, and puts companies at a competitive disadvantage. Mitigating strategies include prioritization, exploring cost-effective solutions, and adopting a risk-based approach to optimize limited resources and enhance overall regional cybersecurity resilience.
Opportunity: Enhancing the Cybersecurity landscape through initiatives and investments by government and businesses
The ongoing commitment to bolster cybersecurity infrastructure in the Middle East involves government and businesses' sustained financial and resource investments. This dedication is essential due to the region's rapid digitalization, exposing an expanded attack surface. Continuous investments address the sophistication of evolving cyber threats, contributing to the adoption of cutting-edge security solutions. Given the complex geopolitical landscape, robust cybersecurity infrastructure safeguards against potential attacks aimed at economic disruption or political influence. The economic benefits include a stable digital environment that attracts foreign investments and stimulates regional innovation, fostering economic growth. Such investments include national cybersecurity strategies, business adoption of security best practices, and public-private partnerships, all working towards improved defense capabilities, increased trust, and stronger regional cooperation. Despite challenges like budgetary constraints and talent shortages, these ongoing investments are vital for shaping a secure digital future in the Middle East.
Challenge:Lack of cybersecurity professionals
The scarcity of adept cybersecurity professionals in the Middle East cybersecurity market stems from an expanding demand for skilled personnel that surpasses the region's educational capacity to produce qualified graduates. Challenges include a lack of specialized skills among graduates, intensified competition from global regions with more attractive opportunities, and insufficient awareness among the youth regarding lucrative careers in cybersecurity. This scarcity results in unfilled cybersecurity roles, increased reliance on foreign talent, limited understanding of cybersecurity threats, suboptimal security implementations, and a hindrance to the regional market's growth potential. Addressing this shortage requires collaborative investments in education, industry-academia partnerships, competitive talent retention strategies, and heightened awareness to cultivate a robust cybersecurity ecosystem and fortify the region's digital infrastructure.
Middle East Cybersecurity Market Ecosystem

By end user, healthcare and Life Sciences are expected to grow at the highest CAGR during the forecast period.
The forecasted highest compound annual growth rate (CAGR) in the Middle East's cybersecurity market for the healthcare and life sciences sector between 2023 and 2028 suggests a heightened reliance on technology in these fields. This increased dependency encompasses electronic health records, medical devices, and research databases, rendering these sectors more susceptible to cyber threats. Growing awareness of cybersecurity risks prompts heightened investments in protective measures, ranging from data protection initiatives to employee training and security software implementation.
Factors fueling this growth include the escalating adoption of digital technologies, stringent data privacy regulations, increased healthcare spending, and a focus on medical innovations. This anticipated surge underscores burgeoning opportunities for specialized cybersecurity solutions in healthcare, necessitating collaboration between healthcare and cybersecurity industries for tailored defense strategies.
By deployment mode, the cloud is expected to grow at the highest CAGR during the forecast period.
Anticipating the highest compound annual growth rate (CAGR) for cloud-based security solutions in the Middle East cybersecurity market indicates a notable shift towards adopting cloud-centric cybersecurity strategies. This surge is propelled by factors such as cost-effectiveness, scalability, ease of deployment, and continuous innovation offered by cloud solutions. The expected rise in organizations adopting cloud-based cybersecurity solutions presents substantial market opportunities for vendors in the Middle East. This trend signifies a broader transformation in cybersecurity approaches, emphasizing cloud-centric strategies, and will likely elevate the demand for professionals skilled in cloud security expertise, reinforcing the region's commitment to addressing evolving cyber threats through advanced and adaptable solutions.
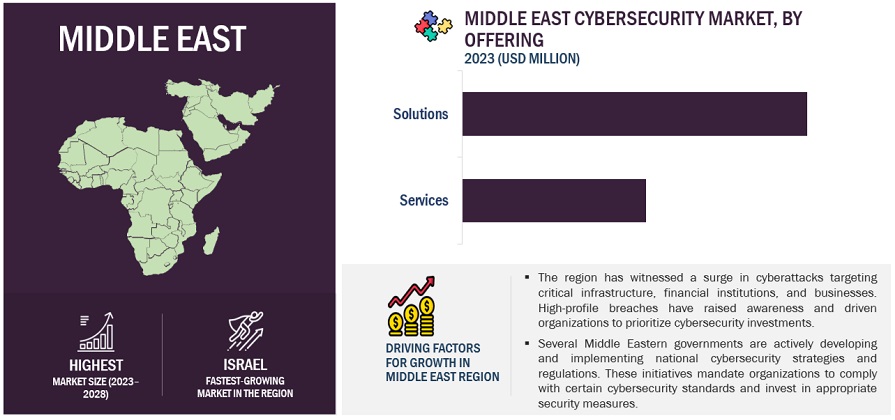
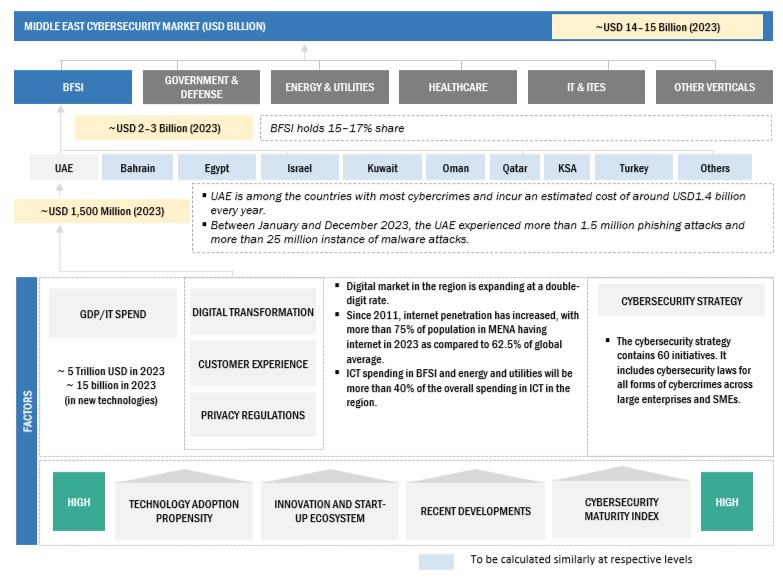
By region, KSA accounts for the second-highest market size during the forecast period.
KSA's dominance in the Middle East cybersecurity market stems from several key factors. As the Gulf region's largest economy, the country's rapid economic expansion fuels increased technology adoption across sectors, necessitating robust cybersecurity solutions. Government initiatives, including the National Cybersecurity Authority and Vision 2030, underscore a commitment to digital transformation and cyber resilience. The nation prioritizes safeguarding critical infrastructure, driving investments in advanced cyber defense. Growing awareness of cyber threats and stringent data privacy regulations further propel cybersecurity spending. This market leadership presents significant vendor opportunities, intensifies competition, and may increase demand for cybersecurity expertise, positioning Saudi Arabia as a regional cybersecurity hub.
Key Market Playrs
The key players in the Middle East cybersecurity market are IBM (US), Cisco (US), Palo Alto Networks(US), Check Point (US), Trend Micro (Japan) and others.
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
Request Sample Scope of the Report
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
|
Report Metrics |
Details |
|
Market size available for years |
|
|
Base year considered |
|
|
Forecast period |
|
|
Forecast units |
|
|
Segments Covered |
|
|
Geographies covered |
|
|
Companies covered |
|
The study categorizes the Middle East cybersecurity market into Offering, Solution Type, Security Type, Deployment mode, Organization Size, Vertical, and Region.
By Offering:
- Solutions
- Services
By Solution Type:
- Identity & Access Management
- Antivirus / Antimalware
- Log Management & SIEM
- Firewall
- Encryption & Tokenization
- Compliance & Policy Management
- Patch Management
- Other Solution Types
By Security Type:
- Network Security
- Endpoint & IoT Security
- Cloud Security
- Application security
By Deployment Mode:
- On-Premises
- Cloud
- Hybrid
- By Organization Size:
- Large Enterprises
- Small and Medium Enterprises (SMEs)
By Vertical:
- Government
- Banking, Financial Services and Insurance (BFSI)
- IT & ITeS
- Healthcare & Life science
- Aerospace & Defense
- Retail & eCommerce
- Manufacturing
- Energy & Utilities
- Telecommunication
- Transportation & Logistics
- Media & Entertainment
- Other Verticals
By Region:
-
Middle East
-
GCC
- UAE
- KSA
- Qatar
- Bahrain
- Oman
- Kuwait
-
Rest of the Middle East
- Israel
- Egypt
- Turkey
- Other Countries
-
GCC
Recent Developments
- In November 2023, Cisco integrated new business metrics into Cloud Observability, enhancing the platform's ability to provide business context for modern applications on Amazon Web Services. This update includes AWS services integration, application performance monitoring (APM) correlation, and comprehensive visibility into cloud-native applications. It enables teams to prioritize tasks based on business impact by offering insights into the relationship between application performance and critical business key performance indicators (KPIs). Cisco Cloud Observability also facilitates easy identification of business transactions configured with metrics and advanced KPI visualization.
- In November 2023, Palo Alto Networks introduced Strata Cloud Manager, a groundbreaking AI-driven Zero Trust management solution. Boasting over 4,400 machine learning models, this innovation underscores Palo Alto Networks' dedication to merging AI and Zero Trust for optimal customer protection. Strata Cloud Manager enhances network security by predicting disruptions, fortifying with AI analysis, and streamlining efficiency across diverse form factors, reinforcing Palo Alto Networks' leadership in modern enterprise security.
- October 2023 Check Point's Horizon Playblocks is a security collaboration platform streamlining network operations. A vital component of the Horizon suite alongside MDR/MPR SOC service and XDR/XPR SOC platform. Playblocks revolutionize team collaboration. It automates preventive measures, deploys swiftly, and consolidates defenses, ensuring a robust, unified response against cyber threats.
- In January 2023, Trend Micro established a new subsidiary, CTOne, which aims to enhance 5G network security. CTOne has been created as a standalone business, drawing upon the intellectual capital and leadership of Trend Micro's innovative culture, and is the latest incubation project to be launched in this way.
- In March 2022, IBM introduced a new cloud service for managing and protecting critical data in hybrid and multi-cloud environments. This service enables businesses to utilize IBM's security features for their data, no matter where it is stored, be it on other clouds, on-premises, or in IBM's cloud. The service aims to reduce the risk of cyberattacks and insider threats to sensitive information.
Frequently Asked Questions (FAQ):
What are the opportunities in the Middle East cybersecurity market?
Investment surge poise growth in solution, services and consulting segments, infrastructure upgrades, talent development, and technology adoption advancements like cloud security, network security, cyber-insurance policies and security measures to risk mitigation, market maturity, and innovations creating resilient digital ecosystem are some of the factors contributing to the growth and new opportunities for the middle east cybersecurity market.
What is the definition of the Middle East cybersecurity market?
Cybersecurity is an approach to safeguard endpoints, networks, applications, and cloud-based data from advanced threats and vulnerabilities. It involves a set of security technologies, solutions, tools, policies, security concepts, guidelines, risk management approaches, and professional and managed services to protect critical enterprise information and infrastructure from cyberattacks, damages, or unauthorized access. In the Middle East, evolving developments in digitalization initiatives and growing exposure to sophisticated cyberattacks are significant factors for adopting cybersecurity solutions and services.
Which region is expected to show the highest market share in the Middle East cybersecurity market?
KSA is expected to account for the largest market share during the forecast period.
Which are the prominent market players covered in the report?
Major vendors in the Middle East cybersecurity market include IBM (US), Cisco (US), Palo Alto Networks (US), Check Point (US), Trend Micro (Japan), Fortinet (US), Broadcom (US), Sophos (UK), Trellix (US), EDGE Group (UAE), SecureWorks (US), CPX (UAE), MDS UAE (UAE), Forescout (US), Protiviti (US), Mandiant (US), LogRhythm (US), Help AG (UAE), Moro Hub (UAE), DTS Solution (UAE), Ras Infotech (UAE), spiderSilk (UAE), CyberSec Consulting (US), CodeGreen Systems (UAE), Malwarebytes (US), Safe Decision (KSA), Security Matterz (KSA), Cato Networks (Israel), CyberGate Defense (UAE).
What is the current size of the Middle East cybersecurity market?
The Middle East cybersecurity market size is projected to grow from USD 14.8 billion in 2023 to USD 23.4 billion by 2028 at a Compound Annual Growth Rate (CAGR) of 9.6% during the forecast period. .
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
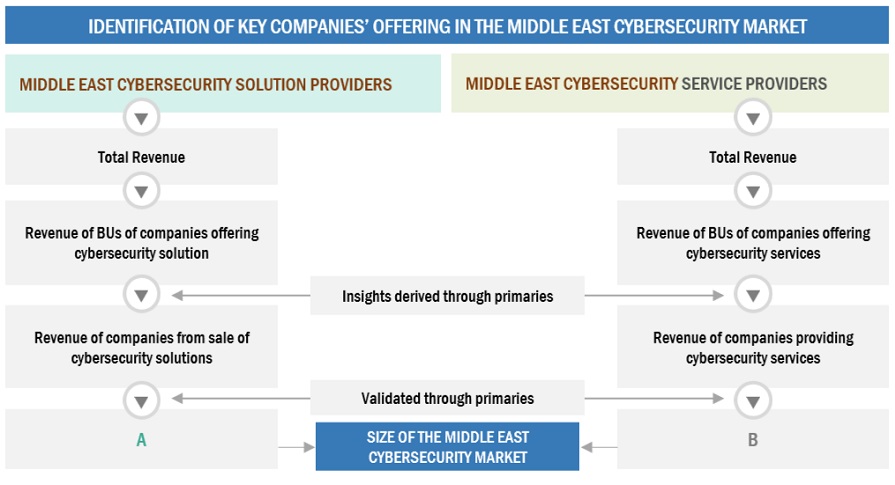
The study involved significant activities in estimating the current market size for the Middle East cybersecurity market. Exhaustive secondary research was done to collect information on the Middle East's cybersecurity industry. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, such as top-down and bottom-up, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and sub-segments of the Middle East cybersecurity market.
Secondary Research
The market for the companies offering Middle East cybersecurity market solutions and services is arrived at by secondary data available through paid and unpaid sources, analyzing the product portfolios of the major companies in the ecosystem, and rating the companies by their performance and quality. Various sources were referred to in the secondary research process to identify and collect information for this study. The secondary sources include annual reports, press releases, investor presentations of companies, white papers, journals, certified publications, and articles from recognized authors, directories, and databases.
In the secondary research process, various secondary sources were referred to for identifying and collecting information related to the study. Secondary sources included annual reports, press releases, and investor presentations of the Middle East cybersecurity market vendors, forums, certified publications, and whitepapers. The secondary research was used to obtain critical information on the industry's value chain, the total pool of key players, market classification, and segmentation from the market and technology-oriented perspectives.
Primary Research
In the primary research process, various supply and demand sources were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the Middle East cybersecurity market.
After the complete market engineering (calculations for market statistics, market breakdown, market size estimations, market forecasting, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also undertaken to identify the segmentation types, industry trends, competitive landscape of Middle East cybersecurity solutions offered by various market players, and fundamental market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key player strategies.
In the complete market engineering process, the top-down and bottom-up approaches and several data triangulation methods were extensively used to perform the market estimation and market forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list the key information/insights throughout the report.
Following is the breakup of the primary study:
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Top-down and bottom-up approaches were used to estimate and validate the size of the Middle East cybersecurity market and the size of various other dependent sub-segments in the overall Middle East cybersecurity market. The research methodology used to estimate the market size includes the following details: critical players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure included the study of the annual and financial reports of the top market players, and extensive interviews were conducted for key insights from the industry leaders, such as CEOs, VPs, directors, and marketing executives.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data is consolidated and added to detailed inputs and analysis from MarketsandMarkets.
Infographic Depicting Bottom-Up and Top-Down Approaches
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
The market was split into several segments and subsegments after arriving at the overall market size using the market size estimation processes explained above. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
The Middle East Cybersecurity market refers to the ecosystem of businesses and technologies within the Middle East region that provide solutions and services to protect critical infrastructure, data, and systems from cyber threats and attacks. In the Middle East, evolving developments in digitalization initiatives and growing exposure to sophisticated cyberattacks are significant factors for adopting cybersecurity solutions and services. Countries across the region are establishing national cybersecurity strategies and critical information infrastructure protection policies to safeguard the protection of vital digital assets.
Key Stakeholders
- Chief technology and data officers
- Consulting service providers
- Managed security services professionals
- Business analysts
- Information Technology (IT) professionals
- Government agencies
- Investors and venture capitalists
- Small and Medium-sized Enterprises (SMEs) and large enterprises
- Third-party providers
- Consultants/consultancies/advisory firms
- Managed and professional service providers
Report Objectives
- To describe and forecast the Middle East cybersecurity market by offering, solution type, security type, deployment mode, organization size, vertical, and region from 2023 to 2028, and analyze the various macroeconomic and microeconomic factors that affect market growth
- To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market
- To provide detailed information regarding major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
- To analyze the opportunities in the market for stakeholders and provide details of the competitive landscape for the major players
- To profile the key market players; provide a comparative analysis based on the business overviews, regional presence, product offerings, business strategies, and critical financials; and illustrate the market's competitive landscape.
- To track and analyze the competitive developments, such as mergers and acquisitions, product developments, partnerships and collaborations, and research development (R&D) activities, in the market
Customization Options
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis
- Further breakup of the Middle Eastern market into countries contributing 75% to the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)











Growth opportunities and latent adjacency in Middle East Cybersecurity Market
Detailed understanding of the cybersecurity strategies for small and mid-size businesses in the Middle East.
Understand the IT Security Market in KSA by Region-wise (Eastern Province, Central, Western), Solution wise (DLP, Vulnerability) and Brand wise (McAfee, CISCO, Symantec, Splunk, Tenable, Fortinet).
Gather insights into pen testing, governance/ risk/compliance, digital forensics and their categories and verticals.
Interseted in the story how level of cyber security in the UAE and GCC countries can be compared to the Europe/ U.S./Israel for Bloomberg News.