Privileged Access Management Market by Offering, Deployment Mode (On-Premises and Cloud), Vertical (BFSI, Government, IT & Ites, Healthcare, Telecommunications, Manufacturing, Energy & Utilities, Retail & Ecommerce) and Region - Global Forecast to 2028
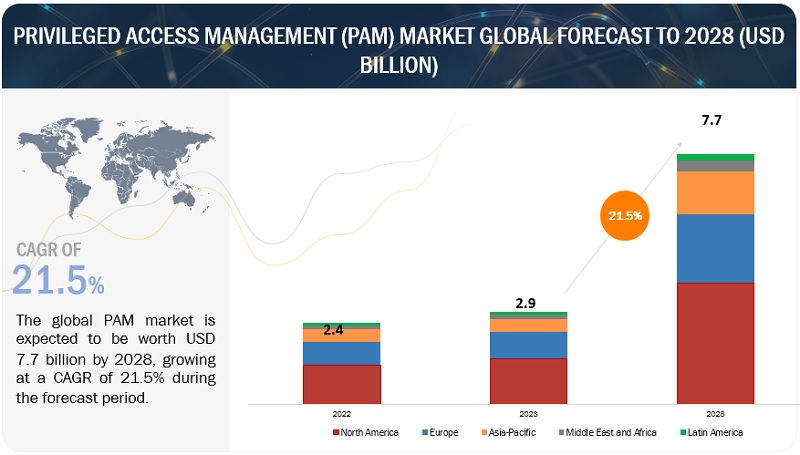
The global Privileged Access Management (PAM) Market size is projected to grow from USD 2.9 billion in 2023 to USD 7.7 billion by 2028 at a CAGR of 21.5% during the forecast period.
The PAM market has witnessed significant expansion, primarily fueled by the ongoing wave of digital advancements and the rapid inclination towards cloud-centric strategies. This growth is further accentuated by mounting concerns over the potential misuse of accounts and shared passwords. Additionally, the escalating threat of internal actors breaching security measures underscores the critical need for robust PAM solutions. Furthermore, as organizations increasingly prioritize compliance with regulatory frameworks, the demand for sophisticated PAM solutions continues to soar, reinforcing the market’s upward trajectory.
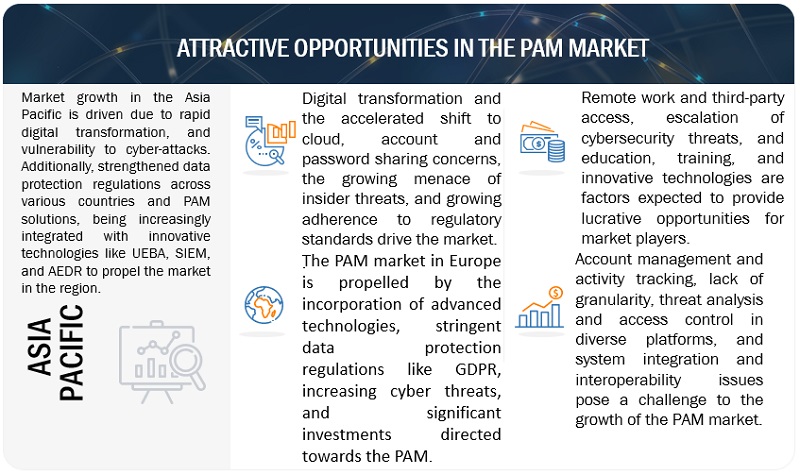
The privileged access management market benefits from opportunities driven by remote work & third-party access, escalation of cybersecurity threats, education, training, and innovative technologies. These factors create favorable conditions for the market’s growth, with organizations seeking advanced solutions to safeguard their systems and valuable data, further contributing to the rising demand for PAM solutions.
To know about the assumptions considered for the study, Request for Free Sample Report
To know about the assumptions considered for the study, download the pdf brochure
In times of a potential worldwide recession, as suggested by indicators like the European Central Bank’s rate hikes and soaring inflation rates in major economies like the EU and UK, the PAM market is poised for a complex trajectory. Historically, downturns often result in tightened IT budgets; however, the increasing significance of cybersecurity amidst a digital transformation era, combined with escalating concerns surrounding insider threats, tends to counterbalance this trend in the PAM sector. As organizations seek cost-effective solutions, they tend to gravitate towards optimizing the existing systems rather than large-scale new implementations. Moreover, with increased account and password sharing concerns, regulatory compliance demands, and the intrinsic value of safeguarding critical data, investments in PAM solutions will remain a priority for businesses, even in strained economic times. Still, the broader financial strain will slow the adoption rate for smaller enterprises or those in severely impacted sectors.
Privileged Access Management Market Dynamics
Driver: Digital transformation and the accelerated shift to the cloud
Businesses rapidly undergo digital transformation, reshaping their goals, workflows, and culture. As per Gartner, 91% of businesses participate in a digital initiative, with 87% of senior leaders prioritizing digitalization. With a significant shift to integrating digital technologies, 89% of companies are implementing or planning a digital-first strategy. A substantial component of this transformation is the move to cloud environments, prized for scalability, agility, and cost-efficiency. Gartner predicts cloud IT spending will surpass traditional IT by 2025, with investments expected to rise from USD 1.3 trillion in 2022 to USD 1.8 trillion in 2025. By 2023, global public cloud spending will reach nearly USD 600 billion. As cloud adoption increases, so does the complexity of access points and potential cyber threats. The decentralized nature of the cloud presents various security issues, making PAM crucial for safeguarding critical resources. As businesses embrace cloud services and prioritize digital agility, the role of PAM extends beyond security, facilitating digital transformation while maintaining data integrity, confidentiality, and compliance. The continued ascent of digital transformation and cloud adoption underscores PAM’s growing significance in the enterprise security framework, propelling its market growth.
Restraint: Complex implementation
Integrating new systems, particularly PAM solutions, into large organizations with existing digital infrastructures is a significant restraint, especially when legacy systems are in place. These older systems have hurdles due to distinct configurations, outdated architectures, and deeply ingrained processes. Integrating PAM requires careful planning, resource dedication, and often specialized skills. According to a Keeper Security survey, while 91% of firms utilize a PAM product, many find them too complicated. Specifically, 68% of IT managers find their PAM products unnecessarily complex or filled with extra features. IT teams tend to use only 62% of PAM features, and 56% have abandoned full PAM implementation because of its complexity. The intricacies involved in PAM and the interlinked nature of long-standing systems and applications make its implementation daunting. This complexity is a restraint for companies reluctant to undergo significant technological revamps.
Opportunity: Escalation of cybersecurity threats
The digital realm is witnessing a spike in cybersecurity threats, particularly those targeting privileged accounts, which are pivotal to an organization’s IT setup. These accounts cause severe data leaks, financial losses, and reputation damage when breached. The rise of advanced threats, such as ransomware that leverages privileged credentials, highlights this vulnerability. Vectra’s report shows a significant security gap, indicating traditional methods, which often depend on one-time decisions or set privilege lists, are becoming obsolete. From July to December 2019, detections of potentially harmful behaviors spiked, with 74% being suspicious privilege accesses similar to the Capital One breach pattern. Moreover, Forrester states that 80% of breaches involve privileged accounts. This evolving threat environment offers the PAM market many opportunities, emphasizing the need for PAM solutions in securing digital assets against modern cyber threats.
Challenge: Lack of granularity
In the PAM market, one of the predominant challenges is a lack of granularity. PAM solutions are designed to manage and monitor privileged access across an organization. However, not all PAM systems offer the same degree of detail in their management capabilities. Some lack the granularity to provide fine-tuned control over specific areas of privileged access. For example, a system might allow database access but not specify which parts of the database are accessible. This broad approach exposes more data, elevating the risk of unauthorized access. Especially for entities like financial or healthcare institutions managing sensitive data, imprecise access controls pose considerable compliance and security challenges.
Privileged Access Management Market Ecosystem

By services, the managed services segment accounts for the highest CAGR during the forecast period.
The managed services segment is anticipated to hold the highest CAGR during the forecasted period. This dominance is attributed to the increasingly complex threat of the environment. As cyber threats become more intricate and persistent, organizations seek specialized solutions, especially those lacking in-house expertise. Managed services in the PAM sector offer agility and profound knowledge, allowing businesses to address emerging threats promptly. Furthermore, as enterprises scale and diversify continuous monitoring, timely updates, and adaptive strategies become paramount, and the managed PAM services fulfill these needs. Moreover, the cost efficiencies and a focus on core competencies have driven organizations to lean heavily on managed PAM providers, propelling their growth in the privileged access management market.
By solution, the access control solution segment accounts for the largest market size during the forecast period
The access control solution segment is anticipated to hold the largest market size during the forecasted period. As organizations grapple with an expanding digital footprint, robust access controls become paramount. The access control solution in the PAM framework ensures that only authorized personnel have the right to access specific resources based on their roles and responsibilities. This minimizes the risk of insider threats and thwarts external adversaries from exploiting weak access points. Additionally, with the rising prevalence of regulations demanding stringent data protection measures, such as GDPR and CCPA, businesses increasingly recognize the value of having a robust access control mechanism. As a result, the investment into these solutions has seen an uptick, thus contributing to its dominant market size. The proliferation of cloud technologies, remote work, and the IoT further accentuates the need for meticulous access control, driving demand in the PAM market.
By solution, the privileged identity management solution accounts for the highest CAGR during the forecast period.
The privileged identity management solution segment is anticipated to hold the highest CAGR during the forecasted period. This growth trajectory is attributed to the heightened awareness of the threats associated with mishandled privileged identities. As organizations expand and digital transformations continue, there is an increase in the number of privileged accounts, be it administrators, service accounts, or system-specific super users. Each of these accounts, if left unchecked, presents a potential attack vector for cyber adversaries. The privileged identity management solution provides a comprehensive framework for managing and monitoring these privileged identities, ensuring that only authenticated users access critical systems.
Furthermore, the solution offers session recording, real-time monitoring, and privileged access, fortifying the organization’s defense mechanisms. The surge in breaches associated with privileged account misuse further amplifies the demand. Furthermore, in the regulatory landscape, where compliance mandates like GDPR and HIPAA enforce rigorous data protection standards, organizations are not only adopting but also investing heavily in privileged identity management solutions. This amalgamation of security imperatives and regulatory compliance is driving the exceptional growth rate anticipated for this segment in the PAM market.
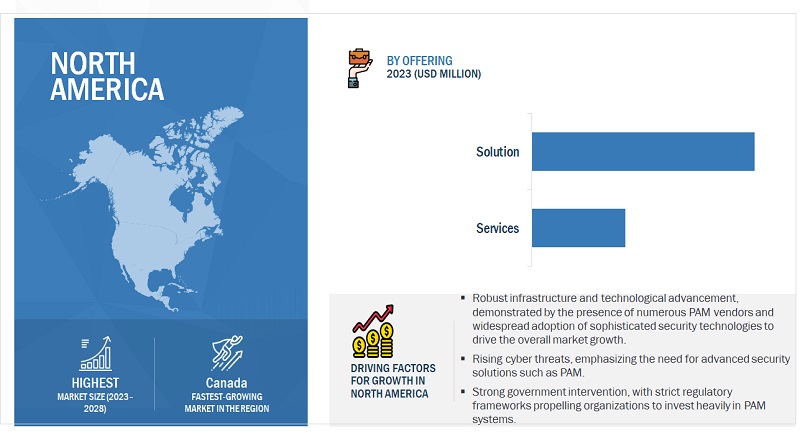
By region, North America accounts for the largest market size during the forecast period.
North America, primarily driven by the US, continues to dominate the PAM market during the forecasted period. Several key factors underpin this dominance. Firstly, the region is home to many global enterprises, particularly in sectors like technology, finance, and healthcare, which prioritize robust cybersecurity measures due to the sensitivity and value of their data. Secondly, North America has a mature IT infrastructure necessitates advanced PAM solutions to counter sophisticated cyber threats. Regulatory mandates, such as the SOX and the HIPAA, further propel businesses to adopt stringent access controls, pushing demand for PAM solutions. Moreover, leading PAM vendors and continuous R&D investments in the region catalyze innovation and market growth. Furthermore, the increased awareness of insider threats and the potential risks associated with cloud environments have spurred organizations to re-evaluate and reinforce their privileged access strategies, solidifying North America’s position in the privileged access management market.
Key Market Players
Some of the well-established and key market players in the PAM market include Fortinet (US), Beyond Trust (US), CyberArk (US), Broadcom (US), Imprivata (US), Optiv Security (US), Okta (US), IBM (US), Micro Focus (OpenText) (UK), ManageEngine (Zoho) (US), Hashi Corporation (US), One Identity (US), ARCON (India), Netwrix (US), Delinea (US), Wallix (France), Saviynt (US), Senhasegura (Brazil), KronTech (Turkey), miniOrange (US), EmpowerID (US), StrongDM (US), CyberSolve (US), Opal Security (US), Foxpass (US), Secureden (US), RevBits (US), Silverfort (Israel), and IDM Technologies (UAE).
Scope of the Report
|
Report Metrics |
Details |
|
Market size available for years |
|
|
Base year considered |
|
|
Forecast period |
|
|
Forecast units |
|
|
Segments Covered |
|
|
Geographies covered |
|
|
Companies covered |
|
The study categorizes the PAM market by offering, deployment mode, verticals, and regions.

By Region:
Recent Developments
- In September 2023, BeyondTrust formed a strategic partnership with Jamf (US). This collaboration enhances Mac endpoint security, a critical aspect of PAM solutions. The integration streamlines privilege management and application control for Apple devices, offering improved access control and operational efficiency.
- In March 2023, FortiPAM introduced privileged remote access management for OT ecosystems and critical assets, integrating with various Fortinet products to provide single sign-on, multi-factor authentication, and zero trust network access.
- In June 2022, CyberArk introduced new functionality for CyberArk Endpoint Privilege Manager, extending its capabilities to support Linux platforms. This enhancement allows security and IT professionals to enforce the least privilege and implement just-in-time security controls across Linux endpoints in various environments.
- In April 2022, Imprivata strategically acquired SecureLink, a move aimed at strengthening its presence in the PAM market. This acquisition underscores Imprivata’s commitment to advancing secure, friction-free digital identity solutions tailored explicitly to PAM.
- In March 2021, Optiv Security introduced a new service. This PMaaS offering provides comprehensive planning, implementation, and ongoing management to assist organizations in safeguarding their privileged accounts from cyber threats. It includes services such as architecture and design, software implementation, and strategy and assessment, all supported by Optiv’s security and operations (SecOps) team. It aims to enhance privileged access management and identity security, helping organizations protect their critical assets effectively
Frequently Asked Questions (FAQ):
What are the opportunities in the global privileged access management market?
Remote work & third-party access, escalation of cybersecurity threats, education, training, and innovative technologies create market opportunities for the global PAM market.
What is the definition of the PAM market?
The PAM market is defined as a specialized cybersecurity sector focusing on solutions and strategies that manage and monitor privileged access to critical digital assets. It ensures that only authorized users can access specific resources, reducing potential security risks and safeguarding an organization’s sensitive information and systems.
Which region is expected to show the highest market share in the PAM market?
North America is expected to account for the largest market share during the forecast period.
What are the challenges in the global PAM market?
The challenges in the PAM market are account management and activity tracking, lack of granularity, threat analysis, access control in diverse platforms, and system integration and interoperability issues.
What are the major market players covered in the report?
Major vendors, namely, include Fortinet (US), Beyond Trust (US), CyberArk (US), Broadcom (US), Imprivata (US), Optiv Security (US), Okta (US), IBM (US), Micro Focus (OpenText) (UK), ManageEngine (Zoho) (US), Hashi Corporation (US), One Identity (US), ARCON (India), Netwrix (US), Delinea (US), Wallix (France), Saviynt (US), Senhasegura (Brazil), KronTech (Turkey), miniOrange (US), EmpowerID (US), StrongDM (US), CyberSolve (US), Opal Security (US), Foxpass (US), Secureden (US), RevBits (US), Silverfort (Israel), and IDM Technologies (UAE).
To know about the assumptions considered for the study, Request for Free Sample Report


- 5.1 INTRODUCTION
-
5.2 MARKET DYNAMICSDRIVERS- Focus on digital transformation and accelerated shift to cloud- Increase in account and password-sharing concerns- Rise in menace of insider threats- Greater adherence to regulatory standardsRESTRAINTS- Complex implementation of legacy systems or solutions- Adaptability and budgetary issuesOPPORTUNITIES- Privilege for remote work & third-party access- Escalation of cybersecurity threats- Provision of education, training, and innovative technologiesCHALLENGES- Difficulty in account management and activity tracking- Lack of granularity- Insufficient threat analysis and access control in diverse platforms- Issues in system integration and interoperability
- 5.3 PRIVILEGED ACCESS MANAGEMENT: EVOLUTION
- 5.4 PRIVILEGED ACCESS MANAGEMENT: FRAMEWORK
-
5.5 CASE STUDY ANALYSISVLI INTEGRATED WITH IBM’S PAM SUITE FOR PROTECTION AGAINST UNAUTHORIZED PRIVILEGED ACCESS AND ENHANCED AUDIT TRAILSKRON TECHNOLOGIES’ AGENTLESS “SINGLE CONNECT” SOLUTION OFFERED SEAMLESS, UNIFIED ACCESS MANAGEMENT, REDUCING PROJECT IMPLEMENTATION TIMEBEYONDTRUST’S ENDPOINT PRIVILEGE MANAGEMENT OFFERED POLICY-DRIVEN CONTROLS FOR ROBUST SECURITY TO ZENSARDELINEA HELPED ROBERT WEED CORPORATION ENSURE BETTER PROCESS CONTROL AND INCREASE PROTECTION FOR ASSETS
-
5.6 PRIVILEGED ACCESS MANAGEMENT MARKET: BEST PRACTICESBENEFITS OF USING PRIVILEGED ACCESS MANAGEMENT
- 5.7 VALUE CHAIN ANALYSIS
-
5.8 ECOSYSTEM ANALYSIS
-
5.9 PORTER’S FIVE FORCES MODEL ANALYSISTHREAT OF NEW ENTRANTSBARGAINING POWER OF SUPPLIERSBARGAINING POWER OF BUYERSTHREAT OF SUBSTITUTESINTENSITY OF COMPETITIVE RIVALRY
-
5.10 PRICING ANALYSISAVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY OFFERINGINDICATIVE PRICING ANALYSIS, BY SOLUTION
-
5.11 TECHNOLOGY ANALYSISAI AND ML TECHNOLOGIES INTEGRATED WITH PAMZERO-TRUST SECURITY MODEL AND PAMINTEGRATION OF CLOUD TECHNOLOGY IN PAMADVANCEMENTS IN PAM WITH BEHAVIORAL ANALYTICSBLOCKCHAIN TECHNOLOGY INTEGRATED WITH PAM
-
5.12 PATENT ANALYSIS
-
5.13 TRENDS/DISRUPTIONS IMPACTING CUSTOMER’S BUSINESS
- 5.14 BUSINESS MODEL
-
5.15 REGULATORY LANDSCAPEPAYMENT CARD INDUSTRY-DATA SECURITY STANDARD (PCI-DSS)HEALTH INSURANCE PORTABILITY AND ACCOUNTABILITY ACT (HIPAA)FEDERAL INFORMATION SECURITY MANAGEMENT ACT (FISMA)SARBANES-OXLEY ACT (SOX)SOC2REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
-
5.16 KEY STAKEHOLDERS AND BUYING CRITERIAKEY STAKEHOLDERS IN BUYING PROCESSBUYING CRITERIA
- 5.17 KEY CONFERENCES AND EVENTS
-
6.1 INTRODUCTIONOFFERINGS: MARKET DRIVERS
-
6.2 SOLUTIONSPASSWORD MANAGEMENT- Dire need to thwart unauthorized access and potential breaches to drive marketSESSION MANAGEMENT- Heightened threats and insider attacks to boost marketACCESS CONTROL- Rise in cyber threats and business imperatives to drive marketPRIVILEGED ELEVATION & DELEGATION- Leveraging fine-grained policies and real-time decision-making mechanisms to help reduce risk of privileged credential abuseCOMPLIANCE & REPORTING- Need to avoid regulatory penalties and ensuring robust cybersecurity hygiene to propel growthPRIVILEGED IDENTITY MANAGEMENT- Facilitating tracking of ownership and entitlements to ensure clarity and accountability to drive growth
-
6.3 SERVICESPROFESSIONAL- Growing emphasis on expertise-driven implementation and regulatory compliance to drive marketMANAGED- Need for round-clock protection against threats and swift response to issues to encourage market expansion
-
7.1 INTRODUCTIONDEPLOYMENT MODES: MARKET DRIVERS
-
7.2 ON-PREMISESNEED FOR ROBUST, IN-HOUSE PRIVILEGED ACCESS SECURITY IN FINANCE AND HEALTHCARE TO BOLSTER GROWTH
-
7.3 CLOUDEMPHASIS ON ACCESS TO LATEST SECURITY FEATURES AND THREAT INTELLIGENCE WITHOUT MANUAL HASSLE TO BOOST GROWTH
-
8.1 INTRODUCTIONVERTICALS: MARKET DRIVERS
-
8.2 BANKING, FINANCIAL SERVICES, AND INSURANCE (BFSI)FOCUS ON SHIELDING PRIVILEGED CREDENTIALS AND PROVIDING DATA ACCESS TO AUTHORIZED INDIVIDUALS TO FUEL GROWTH
-
8.3 GOVERNMENTEMPHASIS ON NATIONAL SECURITY, PUBLIC TRUST, AND INFRASTRUCTURE PROTECTION TO DRIVE ADOPTION OF PRIVILEGED ACCESS MANAGEMENT
-
8.4 IT & ITESTARGETING PASSWORD VAULTING, SESSION MONITORING, AND GRANULAR ACCESS TO MITIGATE RISK CONTROL TO FUEL GROWTH
-
8.5 HEALTHCAREFOCUS ON SECURING PATIENT’S HEALTH DATA, ENSURING COMPLIANCE, AND MAINTAINING PATIENT TRUST TO PROPEL GROWTH
-
8.6 TELECOMMUNICATIONSENSURING UNINTERRUPTED SERVICE AND SAFEGUARD CRITICAL DATA TO PROPEL GROWTH
-
8.7 MANUFACTURINGADOPTION OF SOLUTIONS AS ESSENTIAL TOOLS TO PROVIDE MFA AND RBAC CAPABILITIES TO FUEL MARKET
-
8.8 ENERGY & UTILITIESGRANULAR CONTROL OVER PRIVILEGED USER ACCESS TO SAFEGUARD AGAINST MALICIOUS THREATS WITH AGING INFRASTRUCTURE TO FUEL MARKET
-
8.9 RETAIL & ECOMMERCEEXPANDING ECOMMERCE PLATFORMS AND NEED FOR ROBUST DATA SECURITY TO DRIVE DEMAND
-
8.10 MEDIA & ENTERTAINMENTRISE IN TRAFFIC IN ONLINE STREAMING SITES TO DRIVE ADOPTION OF PRIVILEGED ACCESS MANAGEMENT
- 8.11 OTHER VERTICALS
- 9.1 INTRODUCTION
-
9.2 NORTH AMERICANORTH AMERICA: MARKET DRIVERSNORTH AMERICA: REGULATORY LANDSCAPEUS- Increase in emphasis on adopting advanced solutions such as MFA and policy-based remote access control to drive growthCANADA- Integration of ML and AI for predictive threat analysis and real-time response to drive demand
-
9.3 EUROPEEUROPE: MARKET DRIVERSEUROPE: REGULATORY LANDSCAPEUK- Heightened DDoS risks, ransomware, and data extortion to drive demand for privileged access managementGERMANY- Adoption of security tools such as identity governance, MFA, and threat analytics to boost growthFRANCE- Shift from static to dynamic cybersecurity postures and higher adoption of IAM technologies to encourage market expansionITALY- Influence of technological investments, regulatory imperatives, and evolving work nature to boost growthREST OF EUROPE
-
9.4 ASIA PACIFICASIA PACIFIC: MARKET DRIVERSASIA PACIFIC: REGULATORY LANDSCAPECHINA- Technological prowess and evolving regulatory measures to drive marketJAPAN- Growth in complexity of cyberattacks in various organizations to bolster growthINDIA- Strong government initiative on digital India to secure stored and accessed data to fuel growthSINGAPORE- Singapore's digital ambitions amplify imperative for PAM amid rising cybersecurity threats to drive marketAUSTRALIA & NEW ZEALAND- Surging cyber threats and data security concerns to drive adoption of Privileged Access Management Market solutionsREST OF ASIA PACIFIC
-
9.5 MIDDLE EAST & AFRICAMIDDLE EAST & AFRICA: MARKET DRIVERSMIDDLE EAST & AFRICA: RECESSION IMPACTMIDDLE EAST & AFRICA: REGULATORY LANDSCAPEMIDDLE EAST- Gulf Cooperation Council (GCC)- Rest of Middle EastAFRICA- Rise in digital transformation coupled with escalating cyber threats and awareness to propel growth
-
9.6 LATIN AMERICALATIN AMERICA: MARKET DRIVERSLATIN AMERICA: REGULATORY LANDSCAPEBRAZIL- Need for advanced security solutions to deal with ransomware attacks on high-profile institutions to propel growthMEXICO- Surge in digitalization and increasing shift towards cloud-based solutions to spur growthREST OF LATIN AMERICA

- 10.1 OVERVIEW
- 10.2 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 10.3 REVENUE ANALYSIS
- 10.4 MARKET SHARE ANALYSIS
-
10.5 COMPANY EVALUATION MATRIXSTARSEMERGING LEADERSPERVASIVE PLAYERSPARTICIPANTSCOMPETITIVE FOOTPRINT
-
10.6 STARTUP/SME EVALUATION MATRIXPROGRESSIVE COMPANIESRESPONSIVE COMPANIESDYNAMIC COMPANIESSTARTING BLOCKSCOMPETITIVE BENCHMARKING
-
10.7 COMPETITIVE SCENARIO AND TRENDSPRODUCT LAUNCHESDEALS
-
11.1 KEY PLAYERSFORTINET- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewBEYONDTRUST- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewCYBERARK- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewBROADCOM- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewIMPRIVATA- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewOPTIV SECURITY- Business overview- Products/Solutions/Services offered- Recent developmentsOKTA- Business overview- Products/Solutions/Services offered- Recent developmentsIBM- Business overview- Products/Solutions/Services offered- Recent developmentsMICRO FOCUS (OPENTEXT)- Business overview- Products/Solutions/Services offered- Recent developmentsMANAGEENGINE (ZOHO)- Business overview- Products/Solutions/Services offered- Recent developmentsHASHI CORPORATION- Business overview- Products/Solutions/Services offered- Recent developments
-
11.2 OTHER PLAYERS (SMES AND STARTUPS)ONE IDENTITYARCONNETWRIXDELINEAWALLIXSAVIYNTSENHASEGURAKRONTECHMINIORANGEEMPOWERIDSTRONGDMCYBERSOLVEOPAL SECURITYFOXPASSSECUREDENREVBITSSILVERFORTIDM TECHNOLOGIES
- 12.1 INTRODUCTION TO ADJACENT MARKETS
- 12.2 LIMITATIONS
-
12.3 PRIVILEGED ACCESS MANAGEMENT MARKET ECOSYSTEM AND ADJACENT MARKETSIDENTITY AND ACCESS MANAGEMENT (IAM) MARKETROLE-BASED ACCESS CONTROL MARKET
- 13.1 DISCUSSION GUIDE
- 13.2 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
- 13.3 CUSTOMIZATION OPTIONS
- 13.4 RELATED REPORTS
- 13.5 AUTHOR DETAILS
- TABLE 1 USD EXCHANGE RATES, 2017–2021
- TABLE 2 FACTOR ANALYSIS
- TABLE 3 PAM MARKET: RESEARCH ASSUMPTIONS
- TABLE 4 PAM MARKET: LIMITATIONS AND RISK ASSESSMENT
- TABLE 5 PRIVILEGED ACCESS MANAGEMENT MARKET: ECOSYSTEM
- TABLE 6 PORTER’S FIVE FORCES IMPACT ON PAM MARKET
- TABLE 7 AVERAGE SELLING PRICE TREND OF KEY PLAYERS, BY OFFERING
- TABLE 8 MINIORANGE PAM SOLUTION
- TABLE 9 EMPOWERID PAM SOLUTION
- TABLE 10 LIST OF FEW PATENTS IN PRIVILEGED ACCESS MANAGEMENT MARKET, 2021–2023
- TABLE 11 PAM MARKET: BUSINESS MODEL
- TABLE 12 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 13 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 14 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 15 MIDDLE EAST & AFRICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 16 LATIN AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 17 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR TOP THREE APPLICATIONS
- TABLE 18 KEY BUYING CRITERION FOR TOP THREE APPLICATIONS
- TABLE 19 PRIVILEGED ACCESS MANAGEMENT MARKET: DETAILED LIST OF CONFERENCES & EVENTS, 2023–2025
- TABLE 20 MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 21 MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 22 MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 23 PRIVILEGED ACCESS MANAGEMENT MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 24 SOLUTIONS: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 25 SOLUTIONS: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 26 MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 27 PRIVILEGED ACCESS MANAGEMENT MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 28 SERVICES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 29 SERVICES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 30 PROFESSIONAL SERVICES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 31 PROFESSIONAL SERVICES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 32 MANAGED SERVICES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 33 MANAGED SERVICES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 34 PRIVILEGED ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 35 MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 36 ON-PREMISES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 37 ON-PREMISES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 38 CLOUD: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 39 CLOUD: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 40 PRIVILEGED ACCESS MANAGEMENT MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 41 MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 42 BFSI: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 43 BFSI: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 44 GOVERNMENT: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 45 GOVERNMENT: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 46 IT & ITES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 47 IT & ITES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 48 HEALTHCARE: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 49 HEALTHCARE: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 50 TELECOMMUNICATIONS: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 51 TELECOMMUNICATIONS: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 52 MANUFACTURING: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 53 MANUFACTURING: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 54 ENERGY & UTILITIES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 55 ENERGY & UTILITIES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 56 RETAIL & ECOMMERCE: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 57 RETAIL & ECOMMERCE: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 58 MEDIA & ENTERTAINMENT: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 59 MEDIA & ENTERTAINMENT: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 60 PRIVILEGED ACCESS MANAGEMENT MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 61 MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 62 NORTH AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 63 NORTH AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 64 NORTH AMERICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 65 NORTH AMERICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 66 NORTH AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 67 NORTH AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 68 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 69 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 70 NORTH AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 71 NORTH AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 72 NORTH AMERICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 73 NORTH AMERICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 74 US: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 75 US: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 76 US: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 77 US: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 78 US: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 79 US: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 80 US: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 81 US: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 82 US: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 83 US: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 84 CANADA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 85 CANADA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 86 CANADA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 87 CANADA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 88 CANADA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 89 CANADA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 90 CANADA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 91 CANADA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 92 CANADA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 93 CANADA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 94 EUROPE: PRIVILEGED ACCESS MANAGEMENT MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 95 EUROPE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 96 EUROPE: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 97 EUROPE: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 98 EUROPE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 99 EUROPE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 100 EUROPE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 101 EUROPE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 102 EUROPE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 103 EUROPE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 104 EUROPE: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 105 EUROPE: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 106 UK: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 107 UK: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 108 UK: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 109 UK: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 110 UK: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 111 UK: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 112 UK: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 113 UK: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 114 UK: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 115 UK: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 116 GERMANY: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 117 GERMANY: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 118 GERMANY: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 119 GERMANY: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 120 GERMANY: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 121 GERMANY: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 122 GERMANY: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 123 GERMANY: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 124 GERMANY: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 125 GERMANY: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 126 FRANCE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 127 FRANCE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 128 FRANCE: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 129 FRANCE: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 130 FRANCE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 131 FRANCE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 132 FRANCE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 133 FRANCE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 134 FRANCE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 135 FRANCE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 136 ITALY: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 137 ITALY: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 138 ITALY: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 139 ITALY: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 140 ITALY: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 141 ITALY: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 142 ITALY: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 143 ITALY: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 144 ITALY: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 145 ITALY: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 146 REST OF EUROPE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 147 REST OF EUROPE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 148 REST OF EUROPE: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 149 REST OF EUROPE: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 150 REST OF EUROPE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 151 REST OF EUROPE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 152 REST OF EUROPE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 153 REST OF EUROPE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 154 REST OF EUROPE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 155 REST OF EUROPE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 156 ASIA PACIFIC: PRIVILEGED ACCESS MANAGEMENT MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 157 ASIA PACIFIC: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 158 ASIA PACIFIC: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 159 ASIA PACIFIC: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 160 ASIA PACIFIC: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 161 ASIA PACIFIC: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 162 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 163 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 164 ASIA PACIFIC: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 165 ASIA PACIFIC: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 166 ASIA PACIFIC: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 167 ASIA PACIFIC: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 168 CHINA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 169 CHINA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 170 CHINA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 171 CHINA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 172 CHINA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 173 CHINA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 174 CHINA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 175 CHINA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 176 CHINA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 177 CHINA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 178 JAPAN: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 179 JAPAN: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 180 JAPAN: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 181 JAPAN: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 182 JAPAN: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 183 JAPAN: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 184 JAPAN: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 185 JAPAN: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 186 JAPAN: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 187 JAPAN: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 188 INDIA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 189 INDIA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 190 INDIA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 191 INDIA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 192 INDIA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 193 INDIA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 194 INDIA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 195 INDIA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 196 INDIA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 197 INDIA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 198 SINGAPORE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 199 SINGAPORE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 200 SINGAPORE: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 201 SINGAPORE: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 202 SINGAPORE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 203 SINGAPORE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 204 SINGAPORE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 205 SINGAPORE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 206 SINGAPORE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 207 SINGAPORE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 208 AUSTRALIA & NEW ZEALAND: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 209 AUSTRALIA & NEW ZEALAND: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 210 AUSTRALIA & NEW ZEALAND: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 211 AUSTRALIA & NEW ZEALAND: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 212 AUSTRALIA & NEW ZEALAND: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 213 AUSTRALIA & NEW ZEALAND: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 214 AUSTRALIA & NEW ZEALAND: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 215 AUSTRALIA & NEW ZEALAND: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 216 AUSTRALIA & NEW ZEALAND: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 217 AUSTRALIA & NEW ZEALAND: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 218 REST OF ASIA PACIFIC: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 219 REST OF ASIA PACIFIC: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 220 REST OF ASIA PACIFIC: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 221 REST OF ASIA PACIFIC: PRIVILEGED ACCESS MANAGEMENT MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 222 REST OF ASIA PACIFIC: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 223 REST OF ASIA PACIFIC: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 224 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 225 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 226 REST OF ASIA PACIFIC: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 227 REST OF ASIA PACIFIC: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 228 MIDDLE EAST & AFRICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 229 MIDDLE EAST & AFRICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 230 MIDDLE EAST & AFRICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 231 MIDDLE EAST & AFRICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 232 MIDDLE EAST & AFRICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 233 MIDDLE EAST & AFRICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 234 MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 235 MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 236 MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 237 MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 238 MIDDLE EAST & AFRICA: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 239 MIDDLE EAST & AFRICA: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 240 MIDDLE EAST: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 241 MIDDLE EAST: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 242 MIDDLE EAST: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 243 MIDDLE EAST: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 244 MIDDLE EAST: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 245 MIDDLE EAST: PRIVILEGED ACCESS MANAGEMENT MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 246 MIDDLE EAST: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 247 MIDDLE EAST: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 248 MIDDLE EAST: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 249 MIDDLE EAST: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 250 AFRICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 251 AFRICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 252 AFRICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 253 AFRICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 254 AFRICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 255 AFRICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 256 AFRICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 257 AFRICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 258 AFRICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 259 AFRICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 260 LATIN AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 261 LATIN AMERICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 262 LATIN AMERICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 263 LATIN AMERICA: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 264 LATIN AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 265 LATIN AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 266 LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 267 LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 268 LATIN AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 269 LATIN AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 270 LATIN AMERICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 271 LATIN AMERICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 272 BRAZIL: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 273 BRAZIL: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 274 BRAZIL: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 275 BRAZIL: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 276 BRAZIL: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 277 BRAZIL: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 278 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 279 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 280 BRAZIL: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 281 BRAZIL: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 282 MEXICO: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 283 MEXICO: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 284 MEXICO: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 285 MEXICO: MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 286 MEXICO: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 287 MEXICO: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 288 MEXICO: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 289 MEXICO: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 290 MEXICO: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 291 MEXICO: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 292 REST OF LATIN AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 293 REST OF LATIN AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 294 REST OF LATIN AMERICA: MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 295 REST OF LATIN AMERICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 296 REST OF LATIN AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 297 REST OF LATIN AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 298 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 299 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 300 REST OF LATIN AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 301 REST OF LATIN AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 302 OVERVIEW OF STRATEGIES ADOPTED BY KEY PAM VENDORS
- TABLE 303 MARKET: DEGREE OF COMPETITION
- TABLE 304 COMPANY FOOTPRINT OF KEY PLAYERS, BY OFFERING
- TABLE 305 COMPANY FOOTPRINT OF KEY PLAYERS, BY REGION
- TABLE 306 LIST OF STARTUPS/SMES AND FUNDING
- TABLE 307 COMPANY FOOTPRINT OF STARTUPS/SMES, BY REGION
- TABLE 308 PRIVILEGED ACCESS MANAGEMENT MARKET: PRODUCT LAUNCHES, JANUARY 2022–OCTOBER 2023
- TABLE 309 PRIVILEGED ACCESS MANAGEMENT MARKET: DEALS, JANUARY 2022– OCTOBER 2023
- TABLE 310 FORTINET: BUSINESS OVERVIEW
- TABLE 311 FORTINET: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 312 FORTINET: PRODUCT LAUNCHES
- TABLE 313 BEYOND TRUST: BUSINESS OVERVIEW
- TABLE 314 BEYOND TRUST: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 315 BEYONDTRUST: PRODUCT LAUNCHES
- TABLE 316 BEYONDTRUST: DEALS
- TABLE 317 CYBERARK: BUSINESS OVERVIEW
- TABLE 318 CYBERARK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 319 CYBERARK: PRODUCT LAUNCHES
- TABLE 320 CYBERARK: DEALS
- TABLE 321 BROADCOM: BUSINESS OVERVIEW
- TABLE 322 BROADCOM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 323 BROADCOM: PRODUCT LAUNCHES
- TABLE 324 BROADCOM: DEALS
- TABLE 325 IMPRIVATA: BUSINESS OVERVIEW
- TABLE 326 IMPRIVATA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 327 IMPRIVATA: PRODUCT LAUNCHES
- TABLE 328 IMPRIVATA: DEALS
- TABLE 329 OPTIV SECURITY: BUSINESS OVERVIEW
- TABLE 330 OPTIV SECURITY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 331 OPTIV SECURITY: PRODUCT LAUNCHES
- TABLE 332 OPTIV SECURITY: DEALS
- TABLE 333 OKTA: BUSINESS OVERVIEW
- TABLE 334 OKTA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 335 OKTA: PRODUCT LAUNCHES
- TABLE 336 OKTA: DEALS
- TABLE 337 IBM: BUSINESS OVERVIEW
- TABLE 338 IBM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 339 IBM: PRODUCT LAUNCHES
- TABLE 340 IBM: DEALS
- TABLE 341 MICRO FOCUS (OPENTEXT): BUSINESS OVERVIEW
- TABLE 342 MICRO FOCUS (OPENTEXT): PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 343 MICRO FOCUS (OPENTEXT): PRODUCT LAUNCHES
- TABLE 344 MANAGEENGINE (ZOHO): BUSINESS OVERVIEW
- TABLE 345 MANAGEENGINE (ZOHO): PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 346 MANAGEENGINE (ZOHO): PRODUCT LAUNCHES
- TABLE 347 MANAGEENGINE (ZOHO): DEALS
- TABLE 348 HASHI CORPORATION: BUSINESS OVERVIEW
- TABLE 349 HASHI CORPORATION PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 350 HASHI CORPORATION: PRODUCT LAUNCHES
- TABLE 351 ADJACENT MARKETS AND FORECASTS
- TABLE 352 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2017–2022 (USD MILLION)
- TABLE 353 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2023–2028 (USD MILLION)
- TABLE 354 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 355 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 356 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SOLUTION, 2017–2022 (USD MILLION)
- TABLE 357 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SOLUTION, 2023–2028 (USD MILLION)
- TABLE 358 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 359 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 360 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 361 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 362 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 363 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 364 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 365 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 366 ROLE-BASED ACCESS CONTROL MARKET, BY OFFERING, 2018–2021 (USD MILLION)
- TABLE 367 ROLE-BASED ACCESS CONTROL MARKET, BY OFFERING, 2022–2027 (USD MILLION)
- TABLE 368 ROLE-BASED ACCESS CONTROL MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 369 ROLE-BASED ACCESS CONTROL MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 370 ROLE-BASED ACCESS CONTROL MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 371 ROLE-BASED ACCESS CONTROL MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 372 ROLE-BASED ACCESS CONTROL MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 373 ROLE-BASED ACCESS CONTROL MARKET, BY REGION, 2022–2027 (USD MILLION)
- FIGURE 1 PRIVILEGED ACCESS MANAGEMENT MARKET: RESEARCH DESIGN
- FIGURE 2 PRIVILEGED ACCESS MANAGEMENT MARKET: DATA TRIANGULATION
- FIGURE 3 TOP-DOWN (APPROACH 1): MARKET SIZE ESTIMATION METHODOLOGY (SUPPLY-SIDE)
- FIGURE 4 APPROACH 1 (SUPPLY-SIDE) ANALYSIS
- FIGURE 5 PRIVILEGED ACCESS MANAGEMENT MARKET ESTIMATION: RESEARCH FLOW
- FIGURE 6 BOTTOM-UP (APPROACH 2): MARKET SIZE ESTIMATION METHODOLOGY (DEMAND-SIDE)
- FIGURE 7 KEY COMPANY EVALUATION MATRIX: CRITERIA WEIGHTAGE
- FIGURE 8 STARTUP EVALUATION: CRITERIA WEIGHTAGE
- FIGURE 9 KEY COMPONENTS OF PAM
- FIGURE 10 PRIVILEGED ACCESS MANAGEMENT MARKET TO WITNESS SIGNIFICANT GROWTH DURING FORECAST PERIOD
- FIGURE 11 PRIVILEGED ACCESS MANAGEMENT MARKET: SEGMENTAL SNAPSHOT, 2023–2028
- FIGURE 12 PRIVILEGED ACCESS MANAGEMENT MARKET: REGIONAL SNAPSHOT
- FIGURE 13 DIGITAL TRANSFORMATION, ALONG WITH ACCELERATED SHIFT TO CLOUD, TO BOOST MARKET GROWTH
- FIGURE 14 PRIVILEGED ACCESS MANAGEMENT SOLUTIONS TO BE LARGER MARKET THAN SERVICES DURING FORECAST PERIOD
- FIGURE 15 CLOUD DEPLOYMENT TO PREFERRED OVER ON-PREMISE USE DURING FORECAST PERIOD
- FIGURE 16 BFSI VERTICAL TO BE LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 17 ACCESS CONTROL TO BE LARGEST SOLUTION MARKET DURING FORECAST PERIOD
- FIGURE 18 PROFESSIONAL SERVICES TO BE LARGER MARKET THAN MANAGED SERVICES DURING FORECAST PERIOD
- FIGURE 19 ASIA PACIFIC TO EMERGE AS BEST MARKET FOR INVESTMENTS IN NEXT FIVE YEARS
- FIGURE 20 PRIVILEGED ACCESS MANAGEMENT MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 21 STRATEGIC FRAMEWORK FOR COMPREHENSIVE PRIVILEGED ACCESS MANAGEMENT
- FIGURE 22 PRIVILEGED ACCESS MANAGEMENT MARKET: BEST PRACTICES
- FIGURE 23 VALUE CHAIN ANALYSIS
- FIGURE 24 KEY PLAYERS IN PRIVILEGED ACCESS MANAGEMENT MARKET ECOSYSTEM
- FIGURE 25 PORTER’S FIVE FORCES ANALYSIS
- FIGURE 26 AVERAGE SELLING PRICE TREND OF KEY PLAYERS FOR TOP THREE OFFERINGS
- FIGURE 27 INDICATIVE PRICING OF MINIORANGE PAM SOLUTION
- FIGURE 28 INDICATIVE PRICING OF EMPOWERID PAM SOLUTION
- FIGURE 29 NUMBER OF PATENTS GRANTED FOR PRIVILEGED ACCESS MANAGEMENT MARKET, 2013-2023
- FIGURE 30 REGIONAL ANALYSIS OF PATENTS GRANTED FOR PRIVILEGED ACCESS MANAGEMENT MARKET
- FIGURE 31 TRENDS/DISRUPTIONS IMPACTING CUSTOMERS’ BUSINESSES
- FIGURE 32 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR TOP THREE APPLICATIONS
- FIGURE 33 KEY BUYING CRITERIA FOR TOP THREE APPLICATIONS
- FIGURE 34 SOLUTIONS SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 35 CLOUD DEPLOYMENT MODE TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 36 HEALTHCARE VERTICAL TO ACHIEVE HIGHER GROWTH DURING FORECAST PERIOD
- FIGURE 37 ASIA PACIFIC TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 38 NORTH AMERICA: MARKET SNAPSHOT
- FIGURE 39 ASIA PACIFIC: MARKET SNAPSHOT
- FIGURE 40 REVENUE ANALYSIS OF KEY PAM VENDORS, 2017–2022 (USD MILLION)
- FIGURE 41 PRIVILEGED ACCESS MANAGEMENT MARKET SHARE, 2022
- FIGURE 42 KEY COMPANY EVALUATION MATRIX
- FIGURE 43 STARTUP/SME EVALUATION MATRIX
- FIGURE 44 FORTINET: COMPANY SNAPSHOT
- FIGURE 45 CYBERARK: COMPANY SNAPSHOT
- FIGURE 46 BROADCOM: COMPANY SNAPSHOT
- FIGURE 47 OKTA: COMPANY SNAPSHOT
- FIGURE 48 IBM: COMPANY SNAPSHOT
- FIGURE 49 MICRO FOCUS (OPENTEXT): COMPANY SNAPSHOT
- FIGURE 50 HASHI CORPORATION: COMPANY SNAPSHOT
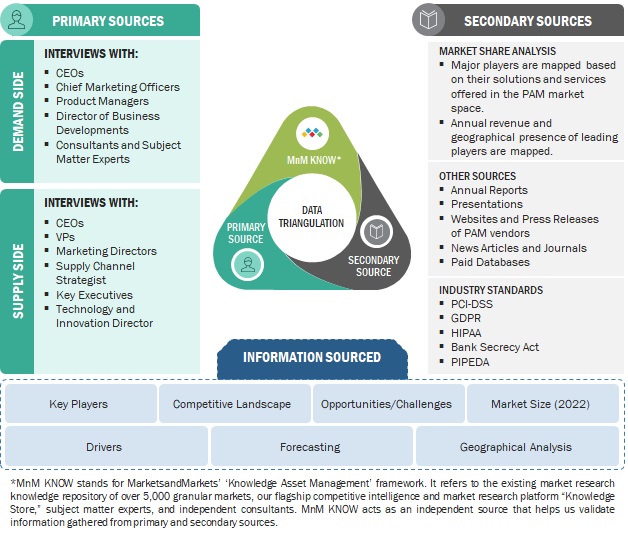
The study involved significant activities in estimating the current market size for PAM. Intensive secondary research was conducted to collect information about PAM and related ecosystems. The industry executives validated these findings, assumptions, and sizing across the value chain using a primary research process as a next step. Top-down and bottom-up market estimation approaches were used to estimate the market size globally, followed by the market breakup and data triangulation procedures to assess the market segment and sub-segments in PAM.
Secondary Research Process:
In the secondary research process, various sources were referred to for identifying and collecting information regarding PAM. These sources include annual reports, press releases, PAM software and service vendor investor presentations, forums, vendor-certified publications, and industry/association white papers. These secondary sources were utilized to obtain key information about PAM’s solutions and services supply & value chain, a list of 100+ key players and SMEs, market classification, and segmentation per the industry trends and regional markets. The secondary research also gives us insights into the key developments from market and technology perspectives, which primary respondents further validated.
The factors considered for estimating the regional market size include technological initiatives undertaken by governments of different countries, gross domestic product (GDP) growth, ICT spending, recent market developments, and market ranking analysis of primary PAM solutions and service vendors.
Primary Research Process:
We have conducted primary research with industry executives from both the supply and demand sides. The primary sources from the supply side include chief executive officers (CEOs), vice presidents (VPs), marketing directors, and technology and innovation executives of key companies operating in the PAM market. We have conducted primary interviews with the executives to obtain qualitative and quantitative information for PAM.
The market engineering process implemented the top-down and bottom-up approaches and various data triangulation methods to estimate and forecast the market segments and subsegments. During the post-market engineering process, we conducted primary research to verify and validate the critical numbers we arrived at. The primary analysis was also undertaken to identify the segmentation types, industry trends, the competitive landscape of the PAM market players, and fundamental market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key strategies.
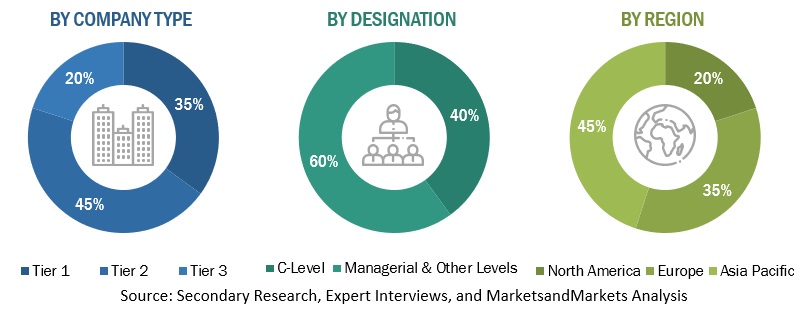
Following is the breakup of the primary research:
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation Process:
Both top-down and bottom-up approaches were implemented for market size estimation to estimate, project, and forecast the size of the global and other dependent sub-segments in the overall PAM market.
The research methodology that has been used to estimate the market size includes these steps:
- The key players, SMEs, and startups were identified through secondary sources. Their revenue contributions in the market were determined through primary and secondary sources.
- Annual and financial reports of the publicly listed market players were considered for the company’s revenue details, and,
- Primary interviews were also conducted with industry leaders to collect information about their companies, competitors, and key players in the market.
- All percentage splits and breakups were determined using secondary sources and verified through primary sources.
Top-down and Bottom-up Approach
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
Data triangulation is a crucial step in the market engineering process for PAM. It involves utilizing multiple data sources and methodologies to validate and cross-reference findings, thereby enhancing the reliability and accuracy of the market segment and subsegment statistics. To conduct data triangulation, various factors and trends related to the PAM market are studied from both the demand and supply sides. It includes analyzing data from diverse sources such as market research reports, industry publications, regulatory bodies, financial institutions, and technology providers. By examining data from different perspectives and sources, data triangulation helps mitigate potential biases and discrepancies. It provides a more comprehensive understanding of the market dynamics, including the size, growth rate, market trends, and customer preferences.
Furthermore, data triangulation aids in identifying any inconsistencies or outliers in the data, enabling researchers to refine their analysis and make informed decisions. It strengthens the credibility of the market engineering process by ensuring that the conclusions drawn are based on robust and corroborated data. Data triangulation is a rigorous and systematic approach that enhances the reliability and validity of market segment and subsegment statistics in PAM. It provides a solid foundation for informed decision-making and strategic planning within the industry.
Market Definition
PAM is a framework designed to oversee and handle privileged accounts and credentials, giving heightened permissions to those accessing vital resources and administrative controls. PAM operates on the least privilege principle, which guarantees that users, software, or processes only receive the essential permissions needed for their operations while segregating and observing user activities. This system assists companies in regulating and monitoring the allocation of administrative access levels to distinct endpoints.
Key Stakeholders
- Government agencies
- PAM solution vendors
- Identity & access management solution and service vendors
- Internet service providers
- Independent software vendors
- Cloud service providers
- Third-party providers
- System integrators
- Value-Added Resellers (VARs)
- Information Technology (IT) security agencies
- Research organizations
Report Objectives
- To define, describe, and forecast the PAM market based on offering, deployment mode, verticals, and regions:
- To predict and estimate the market size of five main regions: North America, Europe, Asia Pacific, Middle East & Africa, and Latin America
- To analyze the subsegments of the market with respect to individual growth trends, prospects, and contributions to the overall market
- To provide detailed information related to the primary factors (drivers, restraints, opportunities, and challenges) influencing the growth of the PAM market
- To analyze opportunities in the market for stakeholders by identifying high-growth segments of the PAM market
- To profile the key players of the PAM market and comprehensively analyze their market size and core competencies.
- Track and analyze competitive developments, such as new product launches, mergers and acquisitions, partnerships, agreements, and collaborations in the global PAM market.
Customization Options
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis
- Further breakup of the Asia Pacific market into countries contributing 75% to the regional market size
- Further breakup of the North American market into countries contributing 75% to the regional market size
- Further breakup of the Latin American market into countries contributing 75% to the regional market size
- Further breakup of the Middle Eastern and African market into countries contributing 75% to the regional market size
- Further breakup of the European market into countries contributing 75% to the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)














Growth opportunities and latent adjacency in Privileged Access Management Market