Zero Trust Security Market by Offering (Solution and Services), Security Type (Network Security, Application Security, Cloud Security, and Endpoint Security and IoT Security), Authentication Type, Vertical and Region - Global Forecast to 2028
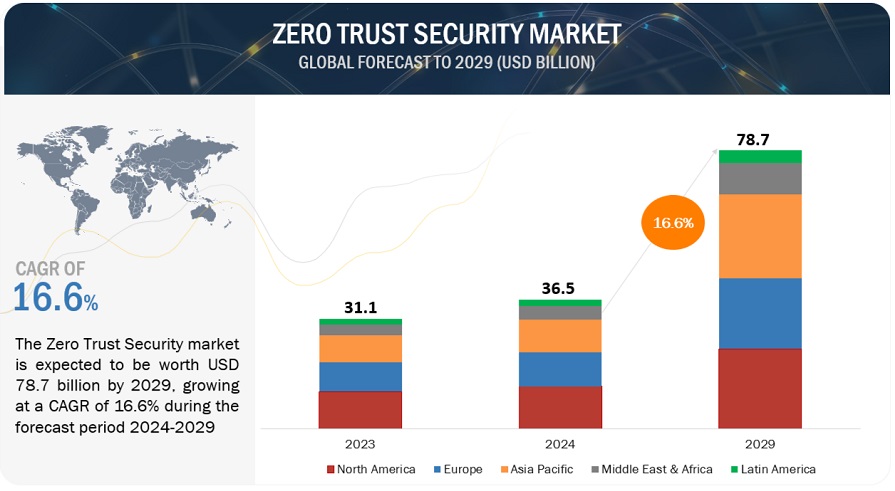
[319 Pages Report] The global Zero Trust Security market size is projected to grow from USD 31.1 billion in 2023 to USD 67.9 billion by 2028 at a Compound Annual Growth Rate (CAGR) of 16.9% during the forecast period. The rising threat of sophisticated cyberattacks is pushing organizations to seek advanced security measures such as zero trust security. With attackers continually evolving their tactics, the need for robust defenses against self-propagating malware and ransomware has become paramount. Additionally, the rapid adoption of cloud technology and digital transformation is expanding the attack surface, necessitating the adoption of a “never trust, always verify” approach.
Furthermore, stringent regulatory compliance demands are compelling businesses to embrace Zero Trust to ensure data protection and mitigate potential breaches. Finally, the diminishing effectiveness of traditional perimeter security in a mobile and interconnected world is driving the shift toward zero-trust security.
To know about the assumptions considered for the study, Request for Free Sample Report

To know about the assumptions considered for the study, download the pdf brochure
Zero Trust Security Market Dynamics
Driver: Decline of perimeter security clearing the path for zero trust security
Traditional perimeter-based security is proving insufficient in the face of contemporary workplace dynamics, such as remote work, mobile device usage, and cloud computing. The concept of a well-defined network perimeter is fading as the workforce becomes increasingly mobile and interconnected. In the conventional security model, once users gain network access, they often enjoy broad access to various resources within the perimeter, creating vulnerabilities for lateral movement by attackers. Zero Trust security addresses this challenge by implementing rigorous access controls and authentication processes at every access point, regardless of user location or device. Access is granted on a need-to-know basis, reducing the risk of data breaches. As organizations adapt to evolving cybersecurity threats, the shift from perimeter-based security to Zero Trust is becoming imperative for enhanced protection.
Restraint: Resistance to change within an organization
Adopting zero trust security often encounters resistance within organizations, including pushback from employees and stakeholders. This resistance stems from the need for a fundamental cultural shift from traditional perimeter-based security practices to a continuous verification and authentication approach. Some individuals may be reluctant to depart from the familiar trust-based model within their corporate network. This resistance can impede the organization's efforts to fully implement Zero Trust security. Successful adoption of this security paradigm requires technological changes and a shift in mindset and organizational culture. To overcome resistance, organizations must foster a collaborative approach to security, ensure user-friendly security controls, and communicate the changes effectively, enhancing the chances of successful adoption and overall cybersecurity enhancement.
Opportunity: Expanding opportunities in zero trust solutions for IoT security
The proliferation of IoT devices across various industries is set to amplify IoT traffic, heightening cybersecurity concerns. This trend has prompted a surge in the adoption of the zero-trust security model among organizations dealing with sensitive information. Zero trust enhances visibility into network activities, user access, application usage, and timestamps, which are vital in the face of IoT devices generating a high volume of daily queries. Traditional methods, such as entering data into SIEM systems, prove impractical and lead to a loss of network-level visibility. To counter this, enterprises are turning to zero-trust security solutions to meticulously inspect all network traffic, internal and external, efficiently identifying malicious DNS queries. Key sectors such as banking, IT, retail, healthcare, and government are poised to implement zero trust security, driven by predictive analytics and IoT device monitoring, ushering in growth opportunities for market players amid a heightened need for robust security in the IoT-dominated landscape.
Challenge: Diminishing traditional security boundaries
Traditional security strategies once relied on securing network perimeters and trusting all internal resources and users. However, the modern landscape, shaped by cloud computing and remote work, has blurred these boundaries. In the zero-trust model, the core tenet is to "never trust, always verify." This mandates authentication and verification for every user and device, regardless of location, erasing endpoint or network control assumptions. The challenge is extending this approach to remote and personal device access, highlighting the importance of robust Identity and Access Management (IAM) solutions for securing sensitive data.
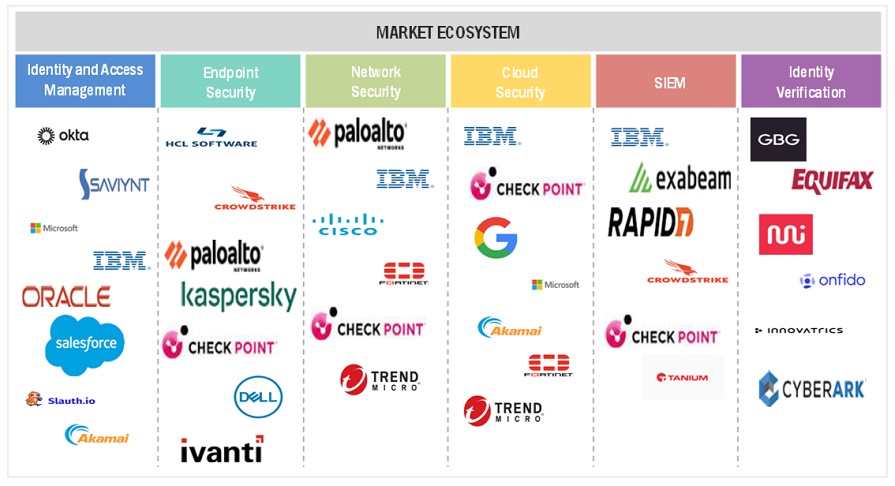
Zero Trust Security Market Ecosystem
By vertical, the Retail and e-commerce segment is to grow at the highest CAGR during the forecast period.
The retail and eCommerce vertical is experiencing remarkable growth in the zero-trust security market due to the sector's extensive online presence, vast customer data storage, and high susceptibility to cyber threats. With the increasing adoption of digital shopping platforms, safeguarding sensitive customer information and transaction data has become paramount. Zero trust security, which focuses on continuous verification and strict access controls, is well-suited to protect these valuable assets. As a result, retail and eCommerce businesses prioritize zero-trust security solutions to fortify their online infrastructure, ensuring customer trust, regulatory compliance, and resilience against evolving cyber threats.
By authentication type, the Multi-factor authentication segment is to grow at the highest CAGR during the forecast period.
Multi-factor authentication is experiencing explosive growth in the zero-trust security market as it addresses critical security concerns. With the heightened awareness of its significance due to prominent data breaches, organizations recognize MFA's pivotal role in safeguarding systems. Government regulations mandating MFA for sensitive transactions further propel its adoption. Within the zero-trust security framework, MFA ensures that only authorized users gain resource access. Additionally, the increasing prevalence of cloud-based applications and mobile devices in workplaces necessitates MFA to fortify security. As cyberattacks become more sophisticated, MFA's multifaceted verification process is a formidable barrier against unauthorized access, rendering it an indispensable element of modern security strategies.
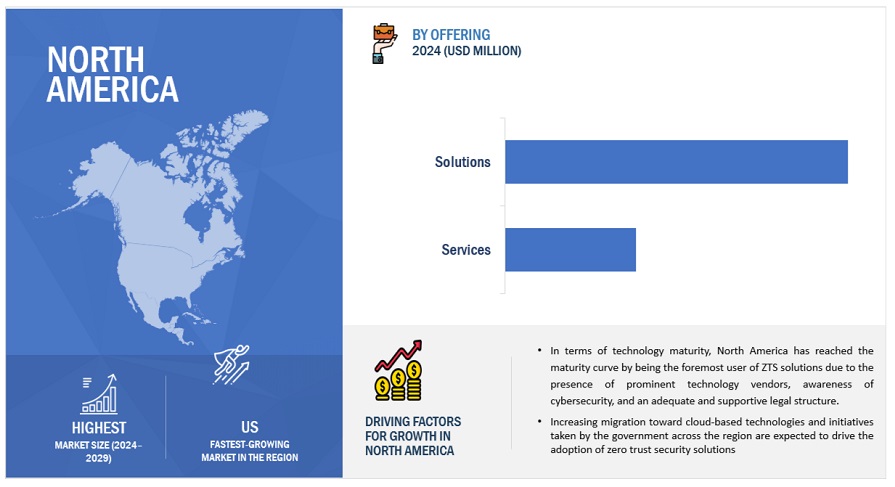
By region, North America accounts for the highest market size during the forecast period.
The zero-trust security market in North America is experiencing rapid growth. The rapid growth is attributed to high cybersecurity awareness as organizations prioritize comprehensive protection. The presence of major market players, including Cisco, Palo Alto Networks, and Okta, gives North American firms early access to cutting-edge zero-trust solutions. Strict regulatory requirements, such as GDPR and CCPA, compel organizations to adopt zero trust for compliance. Additionally, North America's early embrace of cloud computing drives the need for robust security measures in the cloud.
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
Request Sample Scope of the Report
Get online access to the report on the World's First Market Intelligence Cloud
- Easy to Download Historical Data & Forecast Numbers
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
|
Report Metrics |
Details |
|
Market size available for years |
|
|
Base year considered |
|
|
Forecast period |
|
|
Forecast units |
|
|
Segments Covered |
|
|
Geographies covered |
|
|
Companies covered |
|
The study categorizes the Zero Trust Security market by segments - offering, software type, deployment mode, application, vertical, and region.
By Offering:
- Solution
- Services
By Security Type:
- Network Security
- Application Security
- Cloud Security
- Endpoint Security and IoT Security
By Authentication Type:
- Single-Factor Authentication
- Multi-Factor Authentication
Vertical:
- Banking, Financial Services, and Insurance (BFSI)
- Government and Defense
- IT & ITeS
- Healthcare
- Retail and ECommerce
- Energy and Utilities
- Other Verticals
By Region:
- North America
- Europe
- Asia Pacific
- Middle East & Africa
- Latin America
Recent Developments
- In August 2023, Secureworks and Akamai partnered to fortify modern workplace cybersecurity, combining Akamai's zero trust and web security with Secureworks' Taegis XDR for seamless access management and threat response.
- In July 2023, Samsung and Microsoft partnered to bolster mobile device security for enterprises. This partnership enables hardware-backed device attestation via Microsoft Intune on Samsung Galaxy devices, fortifying Zero Trust security and supporting BYOD initiatives.
- In May 2023, Zscaler forged a strategic partnership with the Center for Internet Security (CIS) to bolster cybersecurity for state, local, tribal, and territorial governments by leveraging the CIS CyberMarket. Through this partnership, Zscaler's Zero Trust Exchange brings forth budget-friendly, cutting-edge zero trust solutions aimed at safeguarding against the ever-evolving landscape of cyber threats.
- In April 2023, Palo Alto Networks and Accenture partnered to bolster cyber resilience with integrated Prisma SASE solutions. This partnership streamlines zero trust network access for enhanced security in distributed work environments.
- In September 2022, VMware and Nvidia joined forces to forge an advanced data center platform that seamlessly melds AI capabilities with a robust zero-trust security approach. This strategic collaboration is aimed at elevating the security of workloads by deploying state-of-the-art firewalls on each server, harnessing the power of GPUs for peak performance, and fortifying the zero-trust model.
Frequently Asked Questions (FAQ):
What are the opportunities in the global zero trust security market?
The growing demand for zero-trust security and the adoption of IoT devices are some of the factors contributing to the growth and creating new opportunities for the zero-trust security market.
What is the definition of the zero trust security market?
The US National Institute of Standards and Technology (NIST), in its current draft of standards for zero trust architecture, defines zero trust in the following manner: “Zero trust is a cybersecurity paradigm focused on resource protection and the premise that trust is never granted implicitly but must be continually evaluated.” Zero trust security is, therefore, not only a product or an approach--it’s a web of connected policies, practices, software, and hardware that create an entire zero-trust ecosystem.
Which region is expected to show the highest market share in the zero trust security market?
North America is expected to account for the largest market share during the forecast period.
What are the major market players covered in the report?
Major vendors in the global zero trust security market include Palo Alto Networks (US), VMware (US), Zscaler (US), Akamai (US), Microsoft (US), Cisco (US), IBM (US), Citrix (US), Check Point (US), Trellix (US), Forcepoint (US), CrowdStrike (US), Cloudflare (US), Fortinet (US), Google (US), Qnext (Canada), Illumio (US), ON2IT (Netherlands), Perimeter 81 (US), ThreatLocker (US), Twingate (US), Appgate (US), Zero Networks (Israel), Zentera (US), Xage (US), and Skyhigh Security (US).
What is the current size of the global zero trust security market?
The global zero trust security market size is projected to grow from USD 31.1 billion in 2023 to USD 67.9 billion by 2028 at a Compound Annual Growth Rate (CAGR) of 16.9% during the forecast period.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst
The study involved major activities in estimating the current market size for the Zero Trust Security market. Exhaustive secondary research was done to collect information on the Zero Trust Security industry. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, such as top-down and bottom-up, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and subsegments of the Zero Trust Security market.
Secondary Research
The market for the companies offering Zero Trust Security and services is arrived at by secondary data available through paid and unpaid sources, analyzing the product portfolios of the major companies in the ecosystem, and rating the companies by their performance and quality. Various sources were referred to in the secondary research process to identify and collect information for this study. The secondary sources include annual reports, press releases, investor presentations of companies, white papers, journals, and certified publications and articles from recognized authors, directories, and databases.
In the secondary research process, various secondary sources were referred to for identifying and collecting information related to the study. Secondary sources included annual reports, press releases, and investor presentations of Zero Trust Security vendors, forums, certified publications, and whitepapers. The secondary research was used to obtain critical information on the industry’s value chain, the total pool of key players, market classification, and segmentation from the market and technology-oriented perspectives.
Primary Research
In the primary research process, various primary sources from both the supply and demand sides were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the Zero Trust Security market.
After the complete market engineering (calculations for market statistics, market breakdown, market size estimations, market forecasting, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also conducted to identify the segmentation types, industry trends, competitive landscape of Zero Trust Security solutions offered by various market players, and key market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key player strategies.
In the complete market engineering process, the top-down and bottom-up approaches were extensively used, along with several data triangulation methods, to perform the market estimation and market forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list the key information/insights throughout the report.
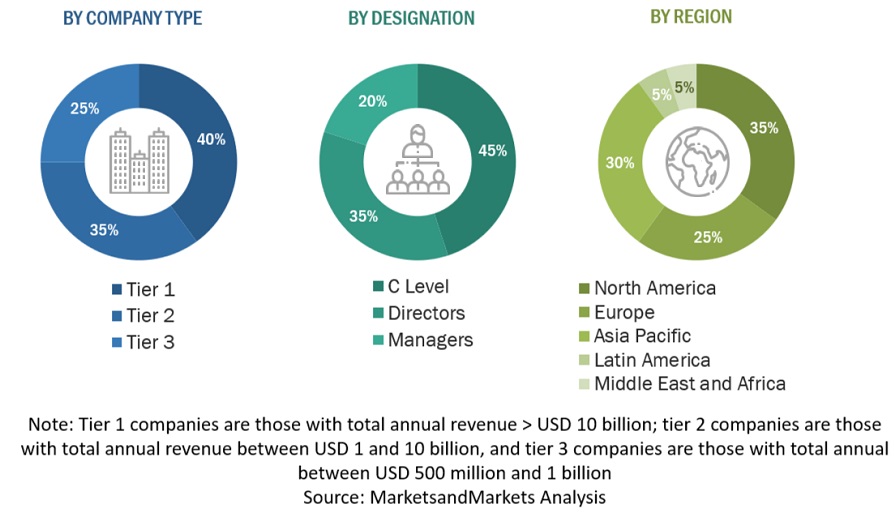
Following is the breakup of the primary study:
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Top-down and bottom-up approaches were used to estimate and validate the size of the global Zero Trust Security market and estimate the size of various other dependent sub-segments in the overall Zero Trust Security market. The research methodology used to estimate the market size includes the following details: key players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure included the study of the annual and financial reports of the top market players, and extensive interviews were conducted for key insights from the industry leaders, such as CEOs, VPs, directors, and marketing executives.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data is consolidated and added to detailed inputs and analysis from MarketsandMarkets.
Infographic Depicting Bottom-Up and Top-Down Approaches
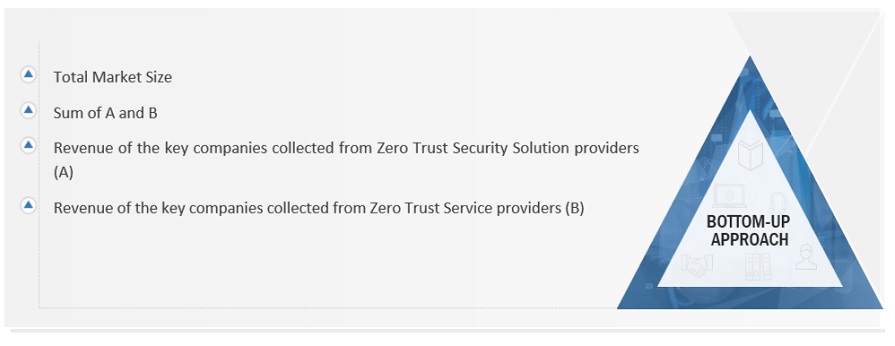
To know about the assumptions considered for the study, Request for Free Sample Report
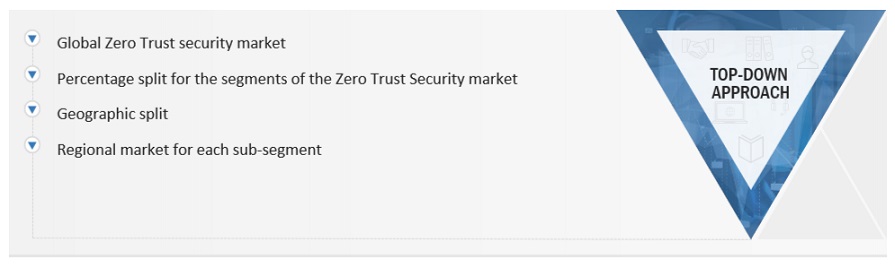
Data Triangulation
After arriving at the overall market size using the market size estimation processes explained above, the market was split into several segments and subsegments. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
The US National Institute of Standards and Technology (NIST), in its current draft of standards for zero trust architecture, defines zero trust in the following manner: “Zero trust is a cybersecurity paradigm focused on resource protection and the premise that trust is never granted implicitly but must be continually evaluated.” Zero trust security is, therefore, not only a product or an approach--it’s a web of connected policies, practices, software, and hardware that create an entire zero-trust ecosystem.
Key Stakeholders
- Government agencies
- Zero trust security solution vendors
- System integrators
- Value-Added Resellers (VARs)
- Information Technology (IT) security agencies
- Research organizations
- Distribution partners
- Privacy specialists
Report Objectives
- To define, describe, and forecast the Zero Trust Security market based on - offering, security type, authentication type, vertical, and region.
- To define, describe, and forecast the market by - offering, security type, authentication type, vertical, and region.
- To forecast the market size of five main regions: North America, Europe, Asia Pacific (APAC), Middle East & Africa (MEA), and Latin America
- To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market
- To provide detailed information related to the major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
- To analyze opportunities in the market for stakeholders by identifying high-growth segments of the market
- To profile the key players of the market and comprehensively analyze their market size and core competencies in the market
- To track and analyze competitive developments, such as new product launches; mergers and acquisitions; and partnerships, agreements, and collaborations in the global Zero Trust Security market.
Customization Options
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis
- Further breakup of the Asia Pacific market into countries contributing 75% to the regional market size
- Further breakup of the North American market into countries contributing 75% to the regional market size
- Further breakup of the Latin American market into countries contributing 75% to the regional market size
- Further breakup of the Middle Eastern and African market into countries contributing 75% to the regional market size
- Further breakup of the European market into countries contributing 75% to the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...







Growth opportunities and latent adjacency in Zero Trust Security Market