Security Orchestration Market by Component (Solution and Service), Application (Threat Intelligence, Network Forensics, Ticketing Solutions, and Compliance Management), Deployment Mode, End User, and Vertical, Region - Global Forecast to 2021
[142 Pages Report] The security orchestration market size is estimated to grow from USD 826.1 million in 2016 to USD 1682.4 million by 2021, at Compound Annual Growth Rate (CAGR) of 15.3%.

The base year considered for the study is 2015 and the market size is calculated from 2016 to 2021. Security orchestration enables organizations to automatically detect and respond to security operations from a single console. The platform also helps to automatically manage, design, and provision any network security changes. This platform includes the set of security technologies & solutions, tools, policies, security concepts, guidelines, risk management approaches, and professional & managed services, which helps to protect networks, computers, programs, and data from cyber-attacks, damages, security breaches, or unauthorized access. The implementation of security orchestration, in public and private organizations, can help to manage security alerts and prevent further cyber-attacks. As the sophistication level in cyber-attacks is increasing, security vendors are trying to develop better orchestration platforms to provide proactive, holistic security to critical business applications.
Market Dynamics
Drivers
- Rise in security breaches and incidents
- Dramatic growth in the BYOD trend affecting SMEs
- Increasing network complexity and frequent changes in network infrastructure
Restraints
- Lack of knowledge about security orchestration
Opportunities
- Convergence of security analytics with security orchestration
Challenges
- Lack of awareness of advanced cyber threats
- Managing security alerts
- Growing demand for cloud computing
- Increasing network complexity and frequent changes in network infrastructure
Increasing network complexity and frequent changes in network infrastructure
Computers and networking have become inseparable by now. Various organizations have admitted that network complexity has increased over the past few years, and will continue to increase over the next five years. Therefore, there is high need for network security to stop hacking and cyber-attacks to secure industrial processes. Moreover, as businesses are growing day by day, the network architecture and network complexity is also becoming denser in nature. Along with this, organizations are continuously undertaking frequent changes in the network architecture according to business needs. To overcome these issues, organizations need a single security solution, which can easily adopt the network changes and can easily manage the network complexity though a single console.
Objectives of the study
- To define, describe, and forecast the security orchestration market by component (solution and services), application, deployment mode, organization size, industry vertical, and region.
- To provide detailed information regarding the major factors (drivers, restraints, opportunities, and challenges) influencing the growth of security orchestration market.
- To analyze the micromarkets1 with respect to individual growth trends, prospects, and contributions to the total market.
- To analyze opportunities in the market for stakeholders by identifying high-growth segments of the security orchestration market.
- To forecast the market size of the market segments with respect to the 5 main regions, namely, North America, Europe, Asia Pacific (APAC), Middle East and Africa (MEA), and Latin America
- To profile the key players of the security orchestration market and comprehensively analyze their market size and core competencies in the market.
- To track and analyze competitive developments, such as new product launches; mergers and acquisitions; and partnerships, agreements, and collaborations in the global security orchestration market.
The research methodology used to estimate and forecast the security orchestration market begins with capturing data on key security vendors through secondary sources such as the Department of Homeland Security (DHS), Information Security Research Association (ISRA), SANS Institute, and other sources such as company financials, journals, press releases, paid databases, and annual reports. The vendor products and services offerings are also taken into consideration to determine the market segmentation. The bottom-up procedure was employed to arrive at the overall security orchestration market size from the revenue of the key players in the market. After arriving at the overall market size, the total market was split into several segments and subsegments, which were then verified through primary research by conducting extensive interviews with key people such as CEOs, VPs, directors, executives, and security orchestration technologists. The data triangulation and market breakdown procedures were employed to complete the overall market engineering process and to arrive at the exact statistics for all segments & sub-segments. The breakdown of primary profiles is depicted in the below figure.
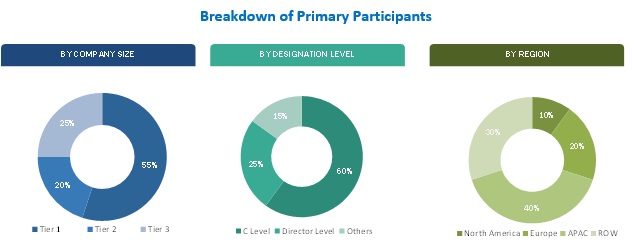
To know about the assumptions considered for the study, download the pdf brochure
The security orchestration ecosystem comprises major vendors such as FireEye, Inc. (U.S.), Cisco Systems, Inc. (U.S.), Intel Security (U.S.), IBM Corporation (U.S.), Huawei Technologies (China), Hexadite (U.S.), Phantom Cyber Corporation (U.S.), Tufin (Israel), Swimlane LLC (U.S.), and CyberSponse Inc. (U.S.), service providers, and system integrators. Other stakeholders include security orchestration solutions providers, consulting firms, IT service providers, value added resellers, enterprise users, and security technology providers.
Major Market Developments:
- In September 2016, Intel Security partnered with Texas Pacific Group to establish one of the largest cybersecurity companies that would focus on developing endpoint and cloud as security control points, actionable threat intelligence analytics, and orchestration solutions.
- In May 2016, FireEye launched FireEye Orchestrator, a new orchestration and automation solution that helps organizations build next-generation Security Operations Center (SOC) reducing the impact of cyber-attacks. In addition, it also enhanced its Global Threat Management Platform providing greater visibility to automate security operations.
- In April 2016, IBM acquired Resilient Systems, a leading provider of incident response solutions. This acquisition would enhance incident response capabilities of IBM helping clients to defend against cyber breaches.
Key target audience of the security orchestration market report is given below:
- Government agencies
- Security orchestration vendors
- Network solution providers
- Independent software vendors
- Consulting firms
- System integrators
- Value-Added Resellers (VARs)
- Managed Security Service Providers (MSSPs)
The study answers several questions for the stakeholders; primarily, which market segments will focus in the next two to five years for prioritizing their efforts and investments.
Scope of the Report
The research report segments the security orchestration market to following submarkets:
By Component:
- Solution
- Services
- Professional services
- Consulting services
- Training and education
- Support and maintenance
- Managed services
- Professional services
By Application:
- Threat intelligence
- Network forensics
- Ticketing solutions
- Compliance management
- Others
By Deployment Mode:
- Cloud
- On-premises
By Organization Size:
- Small and Medium Enterprises (SMEs)
- Large enterprises
By Industry Vertical:
- BFSI
- Energy and utilities
- Government
- Healthcare
- Retail
- IT and Telecom
- Others
By Region:
- North America
- U.S.
- Canada
- Europe
- U.K.
- France
- Germany
- Rest of Europe (ROE)
- Asia-Pacific (APAC)
- China
- Australia
- Japan
- Rest of APAC (ROA)
- Middle East and Africa (MEA)
- Middle East (ME)
- Africa
- Rest of MEA (ROMEA)
- Latin America (LA)
- Mexico
- Brazil
- Rest of LA (ROLA)
Available Customizations
With the given market data, MarketsandMarkets offers customizations as per the companys specific needs. The following customization options are available for the report:
Geographic Analysis
- Further breakdown of the North America security orchestration market
- Further breakdown of the Europe security orchestration market
- Further breakdown of the APAC security orchestration market
- Further breakdown of the MEA security orchestration market
- Further breakdown of the Latin America security orchestration market
Company Information
Detailed analysis and profiling along with vendor DIVE matrix to get detailed information regarding their competitors on the basis of their product offerings and business strategies. The report reviews the major players who offer security orchestration solutions. Additionally, the report will outline the findings and analysis on how well each security orchestration vendor performs within MarketsandMarkets criteria.
The security orchestration market size is expected to grow from USD 826.1 million in 2016 to USD 1682.4 million by 2021, at a Compound Annual Growth Rate (CAGR) of 15.3% during the forecast period.
The security orchestration market is segmented by component, application, deployment mode, organization type, vertical, and region. The major growth drivers of the security orchestration market include the rise in security breaches & incidents, rapid deployment & development of cloud based solutions, and growth in the BYOD trend affecting Small and Medium Enterprises (SMEs). With the adoption of security orchestration solutions, organizations can effectively maintain and secure their critical information from data breaches and respond to cyber incidents more efficiently. As the sophistication level in cyberattacks is increasing, security vendors are trying to develop better orchestration platforms to provide proactive, holistic security to critical business applications.
Security orchestration market by component is segmented into solution and services. Solution segment is estimated to have the largest market size in 2016. Due to the rise in advanced cyber breaches and increased usage of mobile devices, organizations in this region started investing in security orchestration solutions to secure confidential data and applications from present and future attacks; hence, the market is expected to grow with a good rate. Moreover, service segment is expected to grow at the highest CAGR during the forecast period. The market for security orchestration component is growing; consequently, the market for services associated with it is also increasing.
Among the applications, threat intelligence segment holds the largest share of security orchestration market in 2016. The growth in the threat intelligence market is associated with the rise in the number of security breaches targeting business applications, where hackers try to gain access to sensitive data. As the vulnerabilities have become more complex and sophisticated, the demand for security orchestration solutions with threat intelligence capabilities is expected to increase for countering the growing challenges posed by the threats. Network forensics is expected to grow at the highest CAGR during the forecast period. As an increasing number of companies are adopting network forensics solutions to manage and monitor computer network traffic, the market for network forensics is growing.
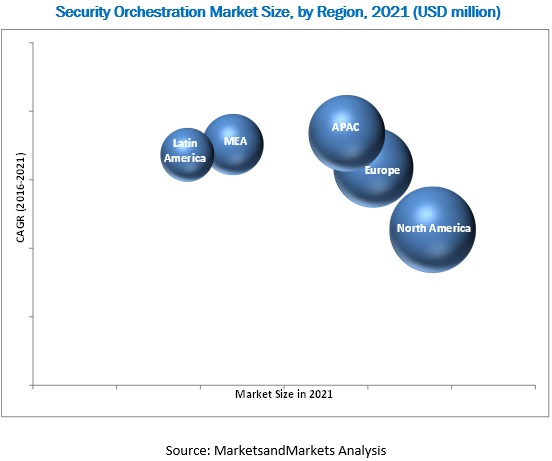
The global security orchestration market has been segmented on the basis of regions into North America, Europe, Asia-Pacific (APAC), Middle East & Africa (MEA), and Latin America to provide a region-specific analysis in the report. The North American region, followed by Europe, is expected to become the largest revenue generating region for security orchestration solution vendors in 2016. This is mainly because, in the developed economies of the U.S. and Canada, there is high focus on innovations obtained from the R&D, and security technology. The APAC region is expected to be the fastest growing region in the security orchestration market. The growth in this region is primarily driven by the need to defend against advanced cyber-attacks and rise in adoption of cloud-based security solutions.
Increased adoption of security orchestration solution and services in Banking, Financial services and Insurance (BFSI), government, and healthcare industry verticals drive the growth of the security orchestration market.
BFSI
Cyber threats in the BFSI industry vertical are increasing at an alarming rate. This sector is continuously upgrading its processing and transaction technologies and requires end-to-end security solutions to optimize operations against both internal and external threats. In addition, the industry frequently keeps introducing new and improved financial products and services to enhance business operations, which makes it attractive for fraudsters to target sensitive customer information. With facilities such as smart banking, internet banking, and mobile banking, the BFSI sector is required to prioritize on security. There is an increasing need for advanced security orchestration solutions in the BFSI industry to fight against the growing number of physical and cyber-attacks on critical infrastructures that are taking place due to the rapid adoption of BYOD, work from home opportunities, and other enterprise mobility trends
Government
Government agencies and institutions across the globe handle critical and sensitive information serving citizens and collecting intelligence. Cyber security has become one of the most important aspects of the government sector. The concept of e-governance has led the government to focus more on cyber security threats. Moreover, as organizations are shifting toward real-time communication, threats from web browsing, email correspondence, peer-to-peer traffic, and file exchange have considerably increased. Hence, the protection of critical information is of the utmost importance. Security orchestration vendors offer solutions to government agencies to secure their data to protect sensitive government data against insider and outsider threats.
Healthcare
Healthcare organizations face several security challenges while maintaining the privacy of Electronic Health Record (EHR) and other related information. Moreover, due to highly proliferated digital medical devices, network management has become essential to save devices from malicious attacks. Security orchestration solutions protect healthcare applications and data against vulnerabilities. In addition, increased government regulations such as HIPAA compliance have also resulted in the rapid adoption of security orchestration solutions in the healthcare sector. With the adoption of technologies such as BYOD and centralized patient information, the healthcare vertical has become susceptible to advanced cyber-attacks.
Key questions
- Which are the substitute products and how big is the threat from them?
- Which are the top use cases where security orchestration solutions and services can be implemented for revenue generation through new advancements such as artificial intelligence, IoT, and cloud computing?
- What should be your go-to-market strategy to expand the reach into developing countries across APAC, MEA, and Latin America?
Major vendors that offer security orchestration across the globe are FireEye, Inc. (U.S.), Cisco Systems, Inc. (U.S.), Intel Security (U.S.), IBM Corporation (U.S.), Huawei Technologies (China), Hexadite (U.S.), Phantom Cyber Corporation (U.S.), Tufin (Israel), Swimlane LLC (U.S.), and CyberSponse Inc. (U.S.). These vendors have adopted different types of organic and inorganic growth strategies such as new product launches, partnerships & collaborations, and mergers & acquisitions to expand their offerings in the security orchestration market.
Frequently Asked Questions (FAQ):
What is Security Orchestration Automation?
What are the top vendors in Security Orchestration Automation market?
What are the applications of Security Orchestration Automation market?
Which industry verticals are adopting Security Orchestration Automation solutions and services?
What is the market size of Security Orchestration Automation?
To speak to our analyst for a discussion on the above findings, click Speak to Analyst

Table of Contents
1 Introduction (Page No. - 15)
1.1 Objectives of the Study
1.2 Security Orchestration Market Definition
1.3 Market Scope
1.3.1 Markets Covered
1.3.2 Years Considered for the Study
1.4 Currency
1.5 Limitations
1.6 Stakeholders
2 Research Methodology (Page No. - 18)
2.1 Introduction
2.2 Research Data
2.2.1 Secondary Data
2.2.1.1 Key Data From Secondary Sources
2.2.2 Primary Data
2.2.2.1 Key Data From Primary Sources
2.2.2.2 Key Industry Insights
2.2.2.3 Breakdown of Primary Interviews
2.3 Market Size Estimation
2.3.1 Bottom-Up Approach
2.3.2 Top-Down Approach
2.4 Market Breakdown and Data Triangulation
2.5 Research Assumptions
3 Executive Summary (Page No. - 26)
4 Premium Insights (Page No. - 31)
4.1 Attractive Market Opportunities in the Global Security Orchestration Market
4.2 Security Orchestration Market, By Component
4.3 Security Orchestration Market, By Industry Vertical and Region
4.4 Lifecycle Analysis, By Region
5 Market Overview (Page No. - 34)
5.1 Introduction
5.2 Market Evolution
5.3 Market Segmentation
5.3.1 By Component
5.3.2 By Application
5.3.3 By Deployment Mode
5.3.4 By End User
5.3.5 By Industry Vertical
5.3.6 By Region
5.4 Market Dynamics
5.4.1 Drivers
5.4.1.1 Rise in Security Breaches and Incidents
5.4.1.2 Dramatic Growth in the Byod Trend Affecting Smes
5.4.1.3 Increasing Network Complexity and Frequent Changes in Network Infrastructure
5.4.2 Restraints
5.4.2.1 Lack of Knowledge About Security Orchestration
5.4.3 Opportunities
5.4.3.1 Convergence of Security Analytics With Security Orchestration
5.4.4 Challenges
5.4.4.1 Lack of Awareness of Advanced Cyber Threats
5.4.4.2 Managing Security Alerts
5.4.4.3 Growing Demand for Cloud Computing
6 Industry Trends (Page No. - 42)
6.1 Introduction
6.2 Value Chain Analysis
6.3 Strategic Benchmarking
6.3.1 Strategic Benchmarking: Contracts, Mergers, and Acquisitions of Top Vendors
7 Security Orchestration Market Analysis, By Component (Page No. - 44)
7.1 Introduction
7.2 Solutions
7.3 Services
7.3.1 Professional Services
7.3.1.1 Consulting
7.3.1.2 Training and Education
7.3.1.3 Support and Maintenance
7.3.2 Managed Services
8 Market Analysis, By Application (Page No. - 52)
8.1 Introduction
8.2 Threat Intelligence
8.3 Network Forensics
8.4 Ticketing Solutions
8.5 Compliance Management
8.6 Others
9 Security Orchestration Market Analysis, By Deployment Mode (Page No. - 58)
9.1 Introduction
9.2 Cloud
9.3 On-Premises
10 Market Analysis, By Organization Size (Page No. - 62)
10.1 Introduction
10.2 Small and Medium Enterprises
10.3 Large Enterprises
11 Security Orchestration Market Analysis, By Industry Vertical (Page No. - 66)
11.1 Introduction
11.2 Banking, Financial Services, and Insurance
11.3 Energy and Utilities
11.4 Government
11.5 Healthcare
11.6 Retail
11.7 IT and Telecom
11.8 Others (Education and Manufacturing)
12 Geographic Analysis (Page No. - 74)
12.1 Introduction
12.2 North America
12.2.1 United States (U.S.)
12.2.2 Canada
12.3 Europe
12.3.1 United Kingdom (U.K.)
12.3.2 France
12.3.3 Germany
12.3.4 Rest of Europe
12.4 Asia-Pacific
12.4.1 China
12.4.2 Australia
12.4.3 Japan
12.4.4 Rest of APAC
12.5 Middle East and Africa
12.5.1 Middle East
12.5.2 Africa
12.6 Latin America
12.6.1 Mexico
12.6.2 Brazil
12.6.3 Rest of Latin America
13 Competitive Landscape (Page No. - 100)
13.1 Overview
13.2 Competitive Situations and Trends
13.3 Product Portfolio Comparison
13.3.1 Partnerships, Agreements, and Collaborations
13.3.2 Mergers and Acquisitions
13.3.3 New Product Launches
14 Company Profiles (Page No. - 105)
14.1 Introduction
(Overview, Financials, Products & Services, Strategy, and Developments)*
14.2 Fireeye, Inc.
14.3 Cisco Systems, Inc.
14.4 Intel Security
14.5 International Business Machines (IBM) Corporation
14.6 Huawei Technologies Co. Ltd.
14.7 Hexadite
14.8 Phantom Cyber Corporation.
14.9 Tufin
14.10 Swimlane LLC
14.11 Cybersponse, Inc.
*Details on Overview, Financials, Product & Services, Strategy, and Developments Might Not Be Captured in Case of Unlisted Companies.
15 Key Innovator (Page No. - 127)
15.1 Introduction
15.2 Optiv Security, Inc.
15.2.1 Business Overview
15.2.2 Products and Services Offered
15.2.3 Recent Developments
15.3 Ayehu Software Technologies Ltd.
15.3.1 Business Overview
15.3.2 Products and Services Offered
15.3.3 Recent Developments
16 Appendix (Page No. - 131)
16.1 Insights of Industry Experts
16.2 Other Developments
16.3 Discussion Guide
16.4 Knowledge Store: Marketsandmarkets Subscription Portal
16.5 Introducing RT: Real-Time Market Intelligence
16.6 Available Customizations
16.7 Related Reports
List of Tables (76 Tables)
Table 1 Security Orchestration Market Size and Growth, 20142021 (USD Million, Yoy %)
Table 2 Market Size, By Component, 20142021 (USD Million)
Table 3 Solutions: Market Size, By Region, 20142021 (USD Million)
Table 4 Services: Market Size, By Type, 20142021 (USD Million)
Table 5 Professional Services: Market Size, By Region, 20142021 (USD Million)
Table 6 Professional Services: Market Size, By Type, 20142021 (USD Million)
Table 7 Consulting: Market Size, By Region, 20142021 (USD Million)
Table 8 Training and Education: Market Size, By Region, 20142021 (USD Million)
Table 9 Support and Maintenance: Market Size, By Region, 20142021 (USD Million)
Table 10 Managed Services: Market Size, By Region, 20142021 (USD Million)
Table 11 Security Orchestration Market Size, By Application, 20142021 (USD Million)
Table 12 Threat Intelligence: Market Size, By Region, 20142021 (USD Million)
Table 13 Network Forensics: Market Size, By Region, 20142021 (USD Million)
Table 14 Ticketing Solutions: Market Size, By Region, 20142021 (USD Million)
Table 15 Compliance Management: Market Size, By Region, 20142021 (USD Million)
Table 16 Others: Market Size, By Region, 20142021 (USD Million)
Table 17 Security Orchestration Market Size, By Deployment Mode, 20142021 (USD Million)
Table 18 Cloud: Market Size, By Region, 20142021 (USD Million)
Table 19 On-Premises: Market Size, By Region, 20142021 (USD Million)
Table 20 Market Size, By Organization Size, 20142021 (USD Million)
Table 21 Small and Medium Enterprises: Market Size, By Region, 20142021 (USD Million)
Table 22 Large Enterprises: Market Size, By Region, 20142021 (USD Million)
Table 23 Security Orchestration Market Size, By Industry Vertical, 20142021 (USD Million)
Table 24 Banking, Financial Services, and Insurance: Market Size, By Region, 20142021 (USD Million)
Table 25 Energy and Utilities: Market Size, By Region, 20142021 (USD Million)
Table 26 Government: Market Size, By Region, 20142021 (USD Million)
Table 27 Healthcare: Market Size, By Region, 20142021 (USD Million)
Table 28 Retail: Market Size, By Region, 20142021 (USD Million)
Table 29 IT and Telecom: Market Size, By Region, 20142021 (USD Million)
Table 30 Others: Market Size, By Region, 20142021 (USD Million)
Table 31 Security Orchestration Market Size, By Region, 20142021 (USD Million)
Table 32 North America: Market Size, By Country, 20142021 (USD Million)
Table 33 North America: Market Size, By Component, 20142021 (USD Million)
Table 34 North America: Market Size, By Service, 20142021 (USD Million)
Table 35 North America: Market Size, By Professional Service, 20142021 (USD Million)
Table 36 North America: Market Size, By Application, 20142021 (USD Million)
Table 37 North America: Market Size, By Deployment Mode, 20142021 (USD Million)
Table 38 North America: Market Size, By Organization Size, 20142021 (USD Million)
Table 39 North America: Security Orchestration Market Size, By Industry Vertical, 20142021 (USD Million)
Table 40 Europe: Market Size, By Country, 20142021 (USD Million)
Table 41 Europe: Market Size, By Component, 20142021 (USD Million)
Table 42 Europe: Market Size, By Service, 20142021 (USD Million)
Table 43 Europe: Market Size, By Professional Service, 20142021 (USD Million)
Table 44 Europe: Market Size, By Application, 20142021 (USD Million)
Table 45 Europe: Market Size, By Deployment Mode, 20142021 (USD Million)
Table 46 Europe: Market Size, By Organization Size, 20142021 (USD Million)
Table 47 Europe: Security Orchestration Market Size, By Industry Vertical, 20142021 (USD Million)
Table 48 Asia-Pacific: Market Size, By Country, 20142021 (USD Million)
Table 49 Asia-Pacific: Market Size, By Component, 20142021 (USD Million)
Table 50 Asia-Pacific: Market Size, By Service, 20142021 (USD Million)
Table 51 Asia-Pacific: Market Size, By Professional Service, 20142021 (USD Million)
Table 52 Asia-Pacific: Market Size, By Application, 20142021 (USD Million)
Table 53 Asia-Pacific: Market Size, By Deployment Mode, 20142021 (USD Million)
Table 54 Asia-Pacific: Market Size, By Organization Size, 2 0142021 (USD Million)
Table 55 Asia-Pacific: Security Orchestration Market Size, By Industry Vertical, 20142021 (USD Million)
Table 56 Middle East and Africa: Market Size, By Country, 20142021 (USD Million)
Table 57 Middle East and Africa: Market Size, By Component, 20142021 (USD Million)
Table 58 Middle East and Africa: Market Size, By Service, 20142021 (USD Million)
Table 59 Middle East and Africa: Market Size, By Professional Service, 20142021 (USD Million)
Table 60 Middle East and Africa: Market Size, By Application, 20142021 (USD Million)
Table 61 Middle East and Africa: Market Size, By Deployment Mode, 20142021 (USD Million)
Table 62 Middle East and Africa: Market Size, By Organization Size, 20142021 (USD Million)
Table 63 Middle East and Africa: Security Orchestration Market Size, By Industry Vertical, 20142021 (USD Million)
Table 64 Latin America: Market Size, By Country, 20142021 (USD Million)
Table 65 Latin America: Market Size, By Component, 20142021 (USD Million)
Table 66 Latin America: Market Size, By Service, 20142021 (USD Million)
Table 67 Latin America: Market Size, By Professional Service, 20142021 (USD Million)
Table 68 Latin America: Market Size, By Application, 20142021 (USD Million)
Table 69 Latin America: Market Size, By Deployment Mode, 20142021 (USD Million)
Table 70 Latin America: Market Size, By Organization Size, 20142021 (USD Million)
Table 71 Latin America: Security Orchestration Market Size, By Industry Vertical, 20142021 (USD Million)
Table 72 Partnerships, Agreements, and Collaborations, 20142016
Table 73 Mergers and Acquisitions, 20142016
Table 74 New Product Launches, 2016
Table 75 Other Developments: New Product Launches, 20142016
Table 76 Other Developments: Partnerships and Collaborations, 20142016
List of Figures (50 Figures)
Figure 1 Global Security Orchestration Market: Research Design
Figure 2 Breakdown of Primary Interviews: By Company, Designation, and Region
Figure 3 Market Size Estimation Methodology: Bottom-Up Approach
Figure 4 Market Size Estimation Methodology: Top-Down Approach
Figure 5 Data Triangulation
Figure 6 Services Segment is Expected to Grow at A Higher CAGR During the Forecast Period
Figure 7 Network Forensics is Expected to Grow at the Highest CAGR During the Forecast Period
Figure 8 Managed Services Segment Expected to Grow at A Higher CAGR During the Forecast Period
Figure 9 Cloud Deployment Mode is Expected to Grow at A Higher CAGR From During the Forcast Period
Figure 10 Small and Medium Enterprises Segment is Expected to Grow at A Higher CAGR During the Forcast Period
Figure 11 Government Vertical to Grow at the Higher CAGR During the Forcast Period
Figure 12 North America is Expected to Hold the Largest Share of the Market in 2016
Figure 13 Rise in Security Breaches and Incidents is Expected to Drive the Security Orchestration Market
Figure 14 Solution Segment is Expected to Have the Largest Market Share During the Forecast Period
Figure 15 BFSI and North America are Expected to Hold the Largest Share of the Security Orchestration Market
Figure 16 Asia-Pacific has Immense Opportunities for the Growth of Market
Figure 17 Evolution of the Security Orchestration Market
Figure 18 Market Segmentation: By Component
Figure 19 Market Segmentation: By Application
Figure 20 Market Segmentation: By Deployment Mode
Figure 21 Market Segmentation: By End User
Figure 22 Market Segmentation: By Industry Vertical
Figure 23 Security Orchestration Market Segmentation: By Region
Figure 24 Security Orchestration: Drivers, Restraints, Opportunities, and Challenges
Figure 25 Security Orchestration Market: Value Chain
Figure 26 Strategic Benchmarking: Partnerships, Acquisitions, and New Product Launches of Top Vendors
Figure 27 Services Segment is Expected to Grow at A Higher CAGR During the Forecast Period
Figure 28 Managed Services Segment Expected to Grow at A Higher CAGR During the Forecast Period
Figure 29 Network Forensics Application is Expected to Grow at the Highest CAGR During the Forecast Period
Figure 30 Cloud-Based Deployment Mode is Expected to Grow at A Higher CAGR During the Forecast Period
Figure 31 Small and Medium Enterprises Segment is Expected to Grow at A Higher CAGR During the Forecast Period
Figure 32 Banking, Financial Services, and Insurance Vertical is Expected to Have the Largest Market Size During the Forecast Period
Figure 33 North America is Expected to Hold the Largest Market Size During the Forecast Period
Figure 34 Regional Snapshot: Asia-Pacific is the Emerging Region in the Security Orchestration Market
Figure 35 North America: Market Snapshot
Figure 36 Asia-Pacific: Market Snapshot
Figure 37 Companies Adopted the Strategy of Partnerships, Agreements, and Collaborations as the Key Growth Strategy From 2014 to 2016
Figure 38 Market Evaluation Framework
Figure 39 Battle for Market Share: the Strategy of Partnerships, Agreements, and Collaborations is the Key Strategy Adopted By Key Players in the Security Orchestration Market During the Period 20142016
Figure 40 Geographic Revenue Mix of Top Market Players
Figure 41 Fireeye, Inc.: Company Snapshot
Figure 42 Fireeye, Inc.: SWOT Analysis
Figure 43 Cisco Systems, Inc.: Company Snapshot
Figure 44 Cisco Systems, Inc.: SWOT Analysis
Figure 45 Intel Security: Company Snapshot
Figure 46 Intel Security: SWOT Analysis
Figure 47 International Business Machines Corporation: Company Snapshot
Figure 48 International Business Machines Corporation: SWOT Analysis
Figure 49 Huawei Technologies Co. Ltd.: Company Snapshot
Figure 50 Huawei Technologies Co. Ltd.: SWOT Analysis














Growth opportunities and latent adjacency in Security Orchestration Market
Interested in the Security Orchestration Product Market Size and forecast
Understanding the SOAR market and trends