5G Security Market by Offering (Solution and Services), End User (Telecom Operators and Enterprises), Network Component Security (RAN and Core Security), Architecture, Application, Vertical and Region - Global Forecast to 2028
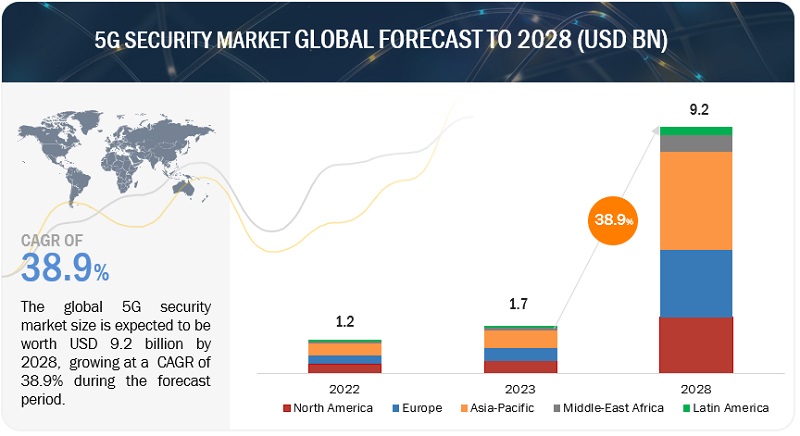
[253 Pages Report] The 5G security market is estimated at USD 1.7 billion in 2023 and is projected to reach USD 9.2 billion by 2028, at a CAGR of 38.9% from 2023 to 2028. The increasing sophistication of cyberattacks, which are becoming more targeted and difficult to defend against, is driving the growth of the market. As cyberattacks become more sophisticated, organizations are forced to invest in better security measures to protect themselves. This includes investing in new security technologies, such as artificial intelligence (AI) and machine learning (ML), and in training their employees on security best practices.
To know about the assumptions considered for the study, Request for Free Sample Report
To know about the assumptions considered for the study, download the pdf brochure
5G Security Market Dynamics
Driver: Security concerns in the 5G network
CIOs are mainly concerned with a network that has the potential to cause significant losses for both corporations and service providers. SD, NV, and cloud-native architecture were used to construct the new network infrastructure. Network functions are spread across local, regional, and central data centers and are decoupled from supporting infrastructure. The majority of network functions in a 5G network based on the cloud are distributed over public and private cloud infrastructure. The existing legacy networks (2G, 3G, and 4G) and internet service networks, as well as vertical industrial networks for things like cars, factories, and loT devices, are all connected to the 5G network. It will build a sophisticated, heterogeneous network connection structure with a 5G network at its center.
Restraint: Delay in standardization of spectrum allocation
One of the biggest benefits of developing the 5G network is the utilization of higher frequencies. But all high frequencies (radio spectrum) are already in use for a variety of purposes, including telecommunications and government operations. Having access to these high-frequency spectrums is essential for building 5G infrastructure. There are conflicts when trying to access these frequency bands since they have already been assigned to various uses. However, it is unclear exactly when wireless operators will be granted access to these spectrums in order to deploy 5G infrastructure. Different government entities are currently establishing various legislation throughout the world.
Opportunity: Increasing operator investments for dynamic infrastructure
Numerous operators have concentrated on securing their carrier network due to an increase in network threats. For instance, the Spanish operator employed 1,000 security personnel and 650 analysts in seven Security Operations Centers (SOCs) around the world following the 02 Telefonica bank hack. Additionally, British Telecom (BT) employs 3,000 security experts in 15 SOCs throughout the world and is qualified to accredit its systems and networks for use by the UK government. BT indicates that it uses Al to protect the data of its clients. Its solution for automatically detecting and comprehending cybersecurity dangers for massive volumes of data makes use of visual interfaces. These expenditures are made to strengthen network security controls, which opens up a big market for the development of 5G security solutions.
Challenge: Uncertainty around ROI and other unprecedented challenges
With standalone solution-related migrating still needing a lot of effort, 5G deployments are in the early stages of their product life cycles. CUPS and network slicing are just two benefits that 5G promises. To deliver the broad services that customers anticipate with efficiency and to give operators a competitive edge, end-to-end 5G networks must be elongable, high-performing, and flexible. To match with the company's long-term interest in entering the industry and gaining the target market segment's trust in the value offer, however, is one of the difficulties telcos confront with 5G rollouts. The amount of money invested also affects the market's level of success. However, carriers do not want to make excessive investments until they achieve ROl or significant traction.
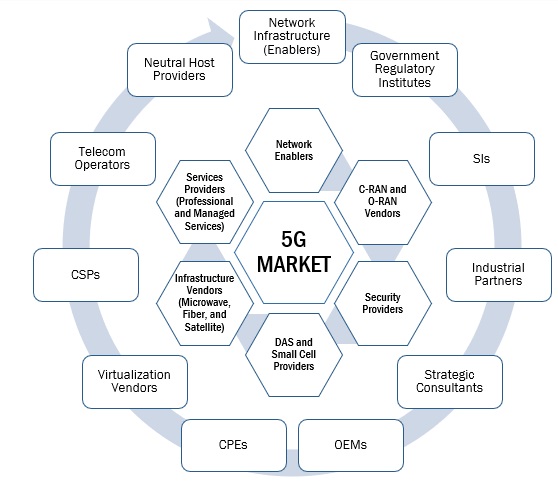
5G security market Ecosystem
The 5G security market comprises several manufacturers, service providers, system integrators, platform providers, and end users working together to deliver 5G security solutions for large-scale advanced network deployments.
By offering, the services segment holds the highest growth rate during the forecast period.
Services have a crucial role to play in the 5G security sector. The demand for services among end users has increased as a result of shifting technological trends. The management of a 5G security network from beginning to end is necessary because it is new to telecom operators and business clients. Expertise and specialized skill sets are needed for the development of 5G security networks, which fuels the demand for consultancy, implementation, and support & maintenance services. In order to achieve desired business goals, these services assist end users in successfully securing their 5G network infrastructure.
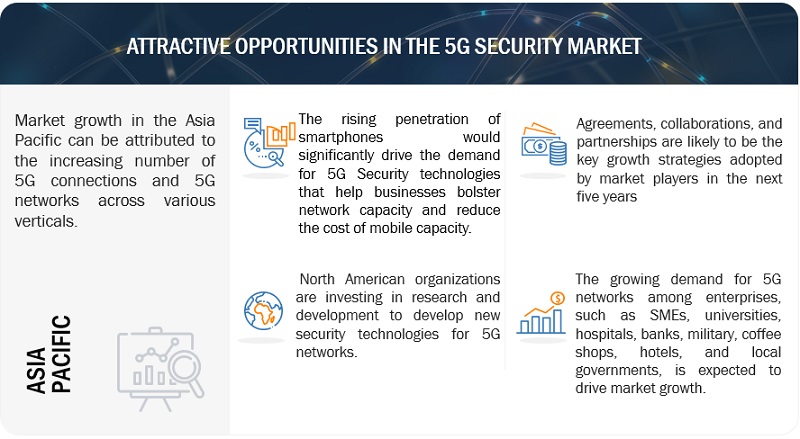
By vertical, media and entertainment are expected to register the fastest growth rate during the forecast period.
Companies in the media and entertainment industry have adapted cutting-edge software to serve a vast consumer base from a single location. DDoS assaults, malware, ransomware, and advanced persistent threats (APTs) are all threats to the media & entertainment vertical's essential infrastructure. For improved defense against these constantly developing assaults, strict 5G security solutions and services are necessary. Companies in the media and entertainment industry work to provide customers with a quick and safe online entertainment experience, a rich media experience, and the ability to trace their usage patterns across numerous applications. Inadequate web performance, slow frame rates, bad graphics, allowed user access, customer data leaks, and undesirable webpage latency times can all result in a loss of online subscribers and consumers for online entertainment organizations. 5G security solutions can help.
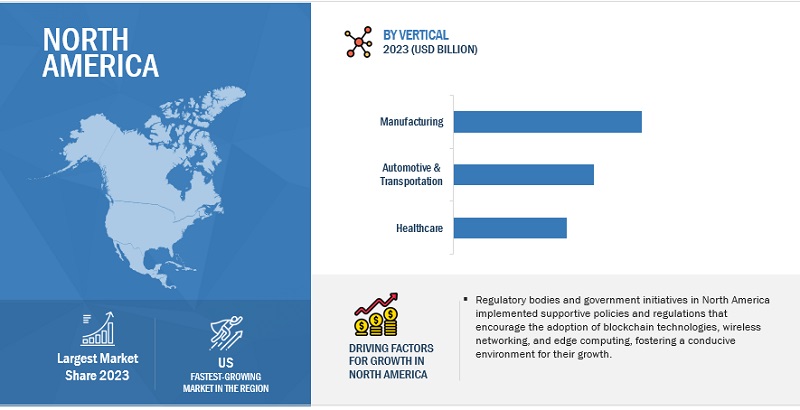
North America is expected to hold the largest market size during the forecast period.
In terms of technology, North America is among the world's most developed areas. This region is now one of the most developed and established mobile markets in the world because of the quick adoption of 4G smartphones by local consumers. In North America, LTE penetration has reached 91%, according to the Ericsson Mobility Report. The market for 5G security would be driven by the rising number of internet users, increased mobile data traffic, and increasing government focus on improving telecommunications infrastructure to meet consumer demand for continuous connectivity and rising cyberattacks. As a result of the quick uptake of 5G services, providers of security solutions for 5G networks would have plenty of room to develop in the US and Canada.
Market Players:
The major players in the 5G security market are Ericsson (Sweden), Palo Alto Networks (US), Cisco (US), Allot (Israel), Huawei (China), A10 Networks (US), Nokia (Finland), F5 Networks (US), Juniper Networks (US), Spirent (US), Fortinet (US), Mobileum (US), Trend Micro (US), ZTE (China), Akamai (US), Colt Technology (UK), CLAVISTER (Sweden), Radware (Israel), AT&T (US), Riscure (Netherlands), Avast (Czech Republic), G+D Mobile Security (Germany), Check Point (US), ForgeRock (US), Positive Technologies (UK), Cellwise (US), Banu Networks (US), Suavei (US), Cachengo (US), BroadForward (Netherlands), Trilogy (US), Movandi (US), Deepsig (US), EdgeQ (US), Alcan systems (Germany), Mixcomm (Colombia), and Microamp Solutions (Poland). These players have adopted various growth strategies, such as partnerships, agreements and collaborations, new product launches and enhancements, and acquisitions to expand their footprint in the 5G security market.

Want to explore hidden markets that can drive new revenue in 5G Security Market?
 Scope of the Report
Scope of the Report

Want to explore hidden markets that can drive new revenue in 5G Security Market?

|
Report Metrics |
Details |
|
Market size available for years |
2021-2028 |
|
Base year considered |
2022 |
|
Forecast period |
2023–2028 |
|
Forecast units |
Value (USD) Billion |
|
Segments Covered |
Offering (Platform and Services), Type, End User, and Region |
|
Region covered |
North America, Europe, Asia Pacific, Middle East and Africa, and Latin America |
|
Companies covered |
Ericsson (Sweden), Palo Alto Networks (US), Cisco (US), Allot (Israel), Huawei (China), A10 Networks (US), Nokia (Finland), F5 Networks (US), Juniper Networks (US), Spirent (US), Fortinet (US), Mobileum (US), Trend Micro (US), ZTE (China), Akamai (US), Colt Technology (UK), CLAVISTER (Sweden), Radware (Israel), AT&T (US), Riscure (Netherlands), Avast (Czech Republic), G+D Mobile Security (Germany), Check Point (US), ForgeRock (US), Positive Technologies (UK), Cellwise (US), Banu Networks (US), Suavei (US), Cachengo (US), BroadForward (Netherlands), Trilogy (US), Movandi (US), Deepsig (US), EdgeQ (US), Alcan systems (Germany), Mixcomm (Colombia), and Microamp Solutions (Poland). |
This research report categorizes the 5G security market to forecast revenues and analyze trends in each of the following submarkets:
Based on Offering:
- Solutions
- Services
Based on Architecture:
- 5G NR Standalone
- 5G NR Non-standalone
Based on Network Security:
- RAN Security
- Mobile Core Security
Based on End User:
- Telecom Operators
- Enterprises
Based on Application:
- Virtual and Augmented Reality
- Connected Automotive
- Smart Manufacturing
- Wireless eHealth
- Smart Cities
Based on Vertical:
- Manufacturing
- Healthcare
- Energy & Utilities
- Retail
- Automotive & Transportation
- Public Safety
- Media & Entertainment
- Other Verticals
By Region:
-
North America
- United States (US)
- Canada
-
Europe
- United Kingdom (UK)
- Germany
- France
- Rest of Europe
-
Asia Pacific
- China
- Japan
- South Korea
- Rest of Asia Pacific
-
Middle East and Africa
- United Arab Emirates
- Kingdom of Saudi Arabia
- South Africa
- Rest of Middle East and Africa
-
Latin America
- Brazil
- Mexico
- Rest of Latin America
Recent Developments
- In July 2023, Ericsson partnered with Spark, one of New Zealand’s largest telecommunications and digital services providers. To supply its 5G Core solution to power Spark’s 5G Standalone (SA) network in New Zealand.
- In June 2023, Cisco Systems and Indian system integrator Wipro Technologies partnered to deploy private fifth-generation (5G) networks to enterprise customers worldwide.
- In September 2022, Palo Alto Networks partnered with Telus, one of the largest 5G network operators in Canada. Telus will use the security vendor’s hardware and software firewalls to protect high-capacity network interfaces across its 5G stand-alone core and internet perimeter while providing security to its IoT customers.
- In September 2021, A10 Networks enhanced its solutions to help customers meet and accelerate its Zero Trust strategies. The company added Zero Trust architecture to the existing security portfolio. The features that will be enhanced are infiltration visibility and protection, automated DDoS protection, granular operational micro-segmentation, advanced user authorization and verification, and real-time observability and central management.
Frequently Asked Questions (FAQ):
What is the definition of the 5G security market?
The 5G security market includes solutions and services that are provided to secure the network of connected devices and critical enterprise applications relying on 5G networks and minimize the losses caused by threats and cyberattacks on networks, applications, and devices.
What is the market size of the 5G security market?
The 5G security market is estimated at USD 1.7 billion in 2023 and is projected to reach USD 9.2 billion by 2028, at a CAGR of 38.9% from 2023 to 2028.
What are the major drivers in the 5G security market?
The major drivers in the 5G security market are Security concerns in the 5G network, increasing IoT connections to pave the way from mMTC with enhanced security requirements, increasing ransomware attacks on IoT devices, and rising attacks on critical infrastructure.
Who are the key companies operating in the 5G security market?
The key companies profiled in the 5G security market Ericsson (Sweden), Palo Alto Networks (US), Cisco (US), Allot (Israel), Huawei (China), A10 Networks (US), Nokia (Finland), F5 Networks (US), Juniper Networks (US), Spirent (US), Fortinet (US), Mobileum (US), Trend Micro (US), ZTE (China), Akamai (US), Colt Technology (UK), CLAVISTER (Sweden), Radware (Israel), AT&T (US), Riscure (Netherlands), Avast (Czech Republic), G+D Mobile Security (Germany), Check Point (US), ForgeRock (US), Positive Technologies (UK), Cellwise (US), Banu Networks (US), Suavei (US), Cachengo (US), BroadForward (Netherlands), Trilogy (US), Movandi (US), Deepsig (US), EdgeQ (US), Alcan systems (Germany), Mixcomm (Colombia), and Microamp Solutions (Poland).
What are the key technology trends prevailing in the 5G security market?
Artificial intelligence, edge computing, and security orchestration are the key technology trends for the 5G security market.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst


- 5.1 INTRODUCTION
-
5.2 MARKET DYNAMICSDRIVERS- Rise in security concerns in 5G network- Increase in demand for IoT connections- Rise in ransomware attacks on IoT devices- Rise in threat to critical infrastructureRESTRAINTS- Delay in standardization of spectrum allocation- Expensive security solutionsOPPORTUNITIES- Growth in operator investments for dynamic infrastructure- Demand for private 5G services across sectors and governmentsCHALLENGES- Uncertainty around return on investment
-
5.3 INDUSTRY TRENDSHISTORY OF 5G SECURITY TECHNOLOGY- Evolution of 5G securityVALUE CHAIN ANALYSIS- Telecom equipment manufacturers- Technologies studiedECOSYSTEM ANALYSISPATENT ANALYSIS- Methodology- Document type- Innovation and patent applications- List of major patentsPRICING ANALYSIS- Average selling price trend of key players, by enterprise- Indicative pricing analysis of key players, by solutionPORTER’S FIVE FORCES MODEL ANALYSIS- Threat of new entrants- Threat of substitutes- Bargaining power of buyers- Bargaining power of suppliers- Intensity of competitive rivalryETHICAL CONSIDERATIONS REGARDING 5G SECURITY- Biases and fairness- Privacy and security- Intellectual property- Accountability and responsibility- Societal and economic impactTECHNOLOGY ANALYSIS- Technologies related to 5G securityCURRENT AND EMERGING BUSINESS MODELS- Subscription-based- Pay-per-use- Managed servicesREGULATORY LANDSCAPE- Regulatory bodies, government agencies, and other organizationsKEY CONFERENCES & EVENTSCASE STUDY ANALYSIS- Mobile service provider implemented A10 Networks’ solutions to scale out security for massive 5G rollout- City of Williamsburg implemented Palo Alto Networks’ solutions to prevent cyber threats- Ericsson helped Erillisverkot provide next-generation public safety networksFUTURE OF 5G SECURITY MARKET- 5G security technology roadmapKEY STAKEHOLDERS AND BUYING CRITERIA- Key stakeholders in buying process- Buying criteriaTRENDS/DISRUPTIONS IMPACTING CUSTOMERS’ BUSINESSES
-
6.1 INTRODUCTIONOFFERING: 5G SECURITY MARKET DRIVERS
-
6.2 SOLUTIONSNEED TO SAFEGUARD CONFIDENTIALITY OF DATA TRANSMITTED OVER NETWORK TO DRIVE GROWTH
-
6.3 SERVICESREQUIREMENT OF 5G SECURITY SERVICES TO ENCOMPASS IDENTITY AND ACCESS MANAGEMENT TO BOOST MARKET
- 7.1 INTRODUCTION
- 7.2 SOLUTION: 5G SECURITY MARKET DRIVERS
-
7.3 NEXT-GENERATION FIREWALLFOCUS ON PERFORMANCE OF 5G NETWORKS TO DRIVE DEMAND FOR NEXT-GENERATION FIREWALL SOLUTIONS
-
7.4 DATA LOSS PREVENTIONNEED TO MITIGATE RISK OF CYBERATTACKS AND DATA BREACHES TO PROPEL MARKET
-
7.5 ANTIVIRUS/ANTIMALWAREGROWING CYBER THREATS TO DRIVE POPULARITY OF ANTIVIRUS/ANTIMALWARE SOLUTIONS
-
7.6 DISTRIBUTED DENIAL OF SERVICE PROTECTIONEFFORTS TO OVERCOME DDOS ATTACKS ON SYSTEMS LINKED TO INTERNET TO DRIVE MARKET
-
7.7 SECURITY GATEWAYINCREASE IN MALICIOUS TRAFFIC OVER NETWORKS TO BOOST GROWTH OF SECURITY GATEWAY
-
7.8 SANDBOXINGNEED TO CONTAIN SPREAD OF MALWARE TO DRIVE USE OF SANDBOXING SOLUTIONS
- 7.9 OTHER SOLUTIONS
- 8.1 INTRODUCTION
- 8.2 SERVICE: 5G SECURITY MARKET DRIVERS
-
8.3 CONSULTINGRAPID ADOPTION OF NETWORK SECURITY SOFTWARE INFRASTRUCTURE TO DRIVE USE OF CONSULTING SERVICES
-
8.4 IMPLEMENTATIONFOCUS ON BETTER NETWORK PERFORMANCE AND RELIABILITY TO DRIVE GROWTH OF IMPLEMENTATION SERVICES
-
8.5 SUPPORT & MAINTENANCESUPPORT & MAINTENANCE SERVICE PROVIDERS TO HELP ENTERPRISES WITH INSTALLATION, MAINTENANCE, AND OTHER SUPPORT ACTIVITIES
-
9.1 INTRODUCTIONNETWORK COMPONENT SECURITY: 5G SECURITY MARKET DRIVERS
-
9.2 RADIO ACCESS NETWORK SECURITYGROWING NEED TO PROTECT ORGANIZATIONS’ RAN FROM CYBERATTACKS TO DRIVE MARKET
-
9.3 MOBILE CORE SECURITYFOCUS ON AUTHENTICATING AND AUTHORIZING USERS BEFORE THEY ACCESS NETWORK TO FUEL SEGMENT
-
10.1 INTRODUCTIONARCHITECTURE: 5G SECURITY MARKET DRIVERS
-
10.2 5G NR STANDALONEDEMAND FOR END-TO-END SUPPORT FOR 5G SERVICES TO PROPEL MARKET GROWTH
-
10.3 5G NR NON-STANDALONENEED TO PROVIDE SERVICES AT LOW COST TO DRIVE DEMAND FOR 5G NR NON-STANDALONE SOLUTIONS
-
11.1 INTRODUCTIONEND USER: 5G SECURITY MARKET DRIVERS
-
11.2 TELECOM OPERATORSRISING EMPHASIS ON SECURING NETWORKS AND IMPROVING CUSTOMER SERVICE TO DRIVE MARKET
-
11.3 ENTERPRISESGROWING DEMAND FOR RELIABLE AND SECURE NETWORK PROVISIONING TO PROPEL ADOPTION OF 5G SECURITY SERVICES AMONG ENTERPRISES
-
12.1 INTRODUCTIONAPPLICATION: 5G SECURITY MARKET DRIVERS
-
12.2 VIRTUAL & AUGMENTED REALITYNEED FOR LOW LATENCY AND HIGH BANDWIDTH FOR REAL-TIME COLLABORATION TO BOOST GROWTH
-
12.3 CONNECTED AUTOMOTIVEINCREASING ROLE OF 5G SERVICES IN CONTROLLING VEHICLES DURING PRODUCTION PHASE TO DRIVE GROWTH
-
12.4 SMART MANUFACTURINGNEED TO CONTROL CRITICAL PROCESSES IN MANUFACTURING TO BOOST ADOPTION OF SMART MANUFACTURING SERVICES
-
12.5 WIRELESS EHEALTHUSE OF EHEALTHCARE SERVICES DUE TO GROWTH OF HEALTHCARE INDUSTRY TO DRIVE SEGMENT
-
12.6 SMART CITIESDEMAND FOR BETTER INFRASTRUCTURE MANAGEMENT AND IMPROVED LOCAL SERVICES TO DRIVE ADOPTION OF 5G SECURITY SERVICES
-
13.1 INTRODUCTIONVERTICAL: 5G SECURITY MARKET DRIVERS
-
13.2 MANUFACTURINGRELIANCE OF MANUFACTURING COMPANIES ON COMPLEX SOFTWARE SOLUTIONS TO DRIVE NEED FOR 5G SECURITY
-
13.3 HEALTHCARERISE IN DEMAND FOR BETTER EMERGENCY SERVICES TO PROPEL MARKET
-
13.4 ENERGY & UTILITIESFOCUS ON BETTERING OPERATION PERFORMANCE IN ENERGY & UTILITIES SECTOR TO ENCOURAGE USE OF 5G SECURITY SERVICES
-
13.5 RETAILNEED FOR SUPERIOR CUSTOMER SERVICE TO AID EXPANSION OF RETAIL SECTOR TO DRIVE MARKET
-
13.6 AUTOMOTIVE & TRANSPORTATION5G SECURITY SOLUTIONS TO HELP NETWORK ADMINISTRATORS MONITOR, ANALYZE, AND SECURE AUTOMOTIVE FACILITIES
-
13.7 PUBLIC SAFETYNEED TO ENHANCE WORKERS’ PRODUCTIVITY AND IMPROVE WORKING OF PUBLIC SAFETY DEPARTMENTS TO DRIVE MARKET
-
13.8 MEDIA & ENTERTAINMENTFOCUS ON REDUCING POOR WEB PERFORMANCE, SLOW FRAME RATES, AND UNWANTED WEBPAGE LAG TIMES TO SUPPORT MARKET GROWTH
- 13.9 OTHER VERTICALS
- 14.1 INTRODUCTION
-
14.2 NORTH AMERICANORTH AMERICA: RECESSION IMPACTNORTH AMERICA: 5G SECURITY MARKET DRIVERSUS- Rapid growth in technology innovation and network infrastructure to drive market growthCANADA- Public-private partnerships and increased government initiatives to drive market
-
14.3 EUROPEEUROPE: RECESSION IMPACTEUROPE: 5G SECURITY MARKET DRIVERSUK- Increased investments and presence of major telecommunication vendors to boost growthITALY- Government worked with private sector to develop and implement innovative 5G security solutionsGERMANY- Need for stringent security across networks due to increase in cyberattacks to fuel marketFRANCE- Demand for robust security measures to drive competitive market for innovative technologies to propel market expansionSPAIN- Government investment in 5G deployment in rural areas to boost demand for 5G security solutionsNORDIC COUNTRIES- Growing reliance on 5G networks for critical infrastructure and stringent regulatory requirements for 5G securityREST OF EUROPE
-
14.4 ASIA PACIFICASIA PACIFIC: RECESSION IMPACTASIA PACIFIC: 5G SECURITY MARKET DRIVERSCHINA- Government initiatives and huge investments in network infrastructure to fuel marketSOUTH KOREA- Rapid growth in technology innovations and need for faster communications to boost demandJAPAN- Rapid expansion due to widespread 5G deployment to encourage growthREST OF ASIA PACIFIC
-
14.5 MIDDLE EAST & AFRICAMIDDLE EAST & AFRICA: RECESSION IMPACTMIDDLE EAST & AFRICA: 5G SECURITY MARKET DRIVERSUAE- Need to protect 5G network and users’ security to drive adoption of 5G security servicesKSA- Greater emphasis on resolving potential cybersecurity weaknesses to drive adoption of security measuresSOUTH AFRICA- Rapid rolling out of 5G infrastructure and rise in emphasis on mitigating cybersecurity concerns to drive marketREST OF MIDDLE EAST & AFRICA
-
14.6 LATIN AMERICALATIN AMERICA: RECESSION IMPACTLATIN AMERICA: 5G SECURITY MARKET DRIVERSBRAZIL- Increase in adoption of cloud computing and big data analytics to fuel growthMEXICO- Growth in awareness regarding importance of cybersecurity among businesses and consumers to propel marketREST OF LATIN AMERICA

- 15.1 INTRODUCTION
- 15.2 STRATEGIES ADOPTED BY KEY PLAYERS
- 15.3 HISTORICAL REVENUE ANALYSIS
- 15.4 MARKET SHARE ANALYSIS
-
15.5 COMPANY EVALUATION MATRIX FOR KEY PLAYERSSTARSEMERGING LEADERSPERVASIVE PLAYERSPARTICIPANTSCOMPANY FOOTPRINT FOR KEY PLAYERS
-
15.6 COMPANY EVALUATION MATRIX FOR STARTUPS/SMESPROGRESSIVE COMPANIESRESPONSIVE COMPANIESDYNAMIC COMPANIESSTARTING BLOCKSCOMPETITIVE BENCHMARKING
-
15.7 COMPETITIVE SCENARIOPRODUCT LAUNCHES & ENHANCEMENTSDEALSOTHERS
-
16.1 KEY PLAYERSERICSSON- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewPALO ALTO NETWORKS- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewCISCO- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewALLOT- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewHUAWEI- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewA10 NETWORKS- Business overview- Products/Solutions/Services offered- Recent developmentsNOKIA- Business overview- Products/Solutions/Services offered- Recent developmentsF5 NETWORKS- Business overview- Products/Solutions/Services offered- Recent developmentsJUNIPER NETWORKS- Business overview- Products/Solutions/Services offered- Recent developmentsSPIRENT- Business overview- Products/Solutions/Services offered- Recent developmentsFORTINETMOBILEUMTREND MICROZTEAKAMAI TECHNOLOGIESCOLT TECHNOLOGY SERVICESCLAVISTERRADWAREAT&TRISCUREAVASTG+D MOBILE SECURITYCHECK POINT SOFTWARE TECHNOLOGIESFORGEROCK
-
16.2 STARTUPS/SMESPOSITIVE TECHNOLOGIESCELLWIZEBENU NETWORKSSUAVEICACHENGOBROADFORWARDTRILOGYMOVANDIDEEPSIGEDGEQALCAN SYSTEMSMIXCOMMMICROAMP SOLUTIONSCELONA INC.
-
17.1 INTRODUCTION5G IOT MARKET - GLOBAL FORECAST TO 2027- Market definition- Market overview- 5G IoT market, by component- 5G IoT market, by network type- 5G IoT market, by organization size- 5G IoT market, by type- 5G IoT market, by region5G SERVICES MARKET - GLOBAL FORECAST TO 2027- Market definition- Market overview- 5G services market, by end user- 5G services market, by communication type- 5G services market, by enterprise
- 18.1 DISCUSSION GUIDE
- 18.2 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
- 18.3 CUSTOMIZATION OPTIONS
- 18.4 RELATED REPORTS
- 18.5 AUTHOR DETAILS
- TABLE 1 USD EXCHANGE RATES, 2020–2022
- TABLE 2 FACTOR ANALYSIS
- TABLE 3 ROLE OF PLAYERS IN MARKET ECOSYSTEM
- TABLE 4 PATENTS FILED, 2014–2023
- TABLE 5 LIST OF A FEW PATENTS IN 5G SECURITY MARKET, 2022–2023
- TABLE 6 AVERAGE SELLING PRICE TRENDS OF KEY PLAYERS, BY ENTERPRISE
- TABLE 7 INDICATIVE PRICING ANALYSIS OF 5G SECURITY
- TABLE 8 IMPACT OF PORTER’S FIVE FORCES ON 5G SECURITY MARKET
- TABLE 9 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 10 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 11 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 12 ROW: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 13 LIST OF CONFERENCES & EVENTS, 2023–2024
- TABLE 14 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- TABLE 15 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- TABLE 16 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 17 SOLUTIONS: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 18 SERVICES: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 19 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 20 NEXT-GENERATION FIREWALL: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 21 DLP: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 22 ANTIVIRUS/ANTIMALWARE: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 23 DDOS PROTECTION: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 24 SECURITY GATEWAY: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 25 SANDBOXING: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 26 OTHER SOLUTIONS: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 27 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 28 CONSULTING: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 29 IMPLEMENTATION: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 30 SUPPORT & MAINTENANCE: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 31 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 32 RADIO ACCESS NETWORK SECURITY: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 33 MOBILE CORE SECURITY: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 34 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 35 5G NR STANDALONE: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 36 5G NR NON-STANDALONE: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 37 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 38 TELECOM OPERATORS: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 39 ENTERPRISES: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 40 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 41 VIRTUAL & AUGMENTED REALITY: 5G SECURITY MARKET, REGION, 2021–2028 (USD MILLION)
- TABLE 42 CONNECTED AUTOMOTIVE: 5G SECURITY MARKET, REGION, 2021–2028 (USD MILLION)
- TABLE 43 SMART MANUFACTURING: 5G SECURITY MARKET, REGION, 2021–2028 (USD MILLION)
- TABLE 44 WIRELESS EHEALTH: 5G SECURITY MARKET, REGION, 2021–2028 (USD MILLION)
- TABLE 45 SMART CITIES: 5G SECURITY MARKET, REGION, 2021–2028 (USD MILLION)
- TABLE 46 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 47 MANUFACTURING: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 48 HEALTHCARE: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 49 ENERGY & UTILITIES: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 50 RETAIL: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 51 AUTOMOTIVE & TRANSPORTATION: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 52 PUBLIC SAFETY: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 53 MEDIA & ENTERTAINMENT: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 54 OTHER VERTICALS: 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 55 5G SECURITY MARKET, BY REGION, 2021–2028 (USD MILLION)
- TABLE 56 NORTH AMERICA: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 57 NORTH AMERICA: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 58 NORTH AMERICA: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 59 NORTH AMERICA: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 60 NORTH AMERICA: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 61 NORTH AMERICA: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 62 NORTH AMERICA: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 63 NORTH AMERICA: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 64 NORTH AMERICA: 5G SECURITY MARKET, BY COUNTRY, 2021–2028 (USD MILLION)
- TABLE 65 US: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 66 US: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 67 US: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 68 US: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 69 US: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 70 US: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 71 US: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 72 US: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 73 CANADA: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 74 CANADA: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 75 CANADA: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 76 CANADA: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 77 CANADA: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 78 CANADA: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 79 CANADA: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 80 CANADA: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 81 EUROPE: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 82 EUROPE: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 83 EUROPE: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 84 EUROPE: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 85 EUROPE: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 86 EUROPE: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 87 EUROPE: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 88 EUROPE: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 89 EUROPE: 5G SECURITY MARKET, BY COUNTRY/REGION, 2021–2028 (USD MILLION)
- TABLE 90 UK: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 91 UK: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 92 UK: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 93 UK: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 94 UK: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 95 UK: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 96 UK: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 97 UK: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 98 ITALY: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 99 ITALY: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 100 ITALY: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 101 ITALY: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 102 ITALY: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 103 ITALY: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 104 ITALY: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 105 ITALY: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 106 ASIA PACIFIC: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 107 ASIA PACIFIC: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 108 ASIA PACIFIC: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 109 ASIA PACIFIC: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 110 ASIA PACIFIC: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 111 ASIA PACIFIC: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 112 ASIA PACIFIC: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 113 ASIA PACIFIC: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 114 ASIA PACIFIC: 5G SECURITY MARKET, BY COUNTRY, 2021–2028 (USD MILLION)
- TABLE 115 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 116 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 117 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 118 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 119 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 120 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 121 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 122 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 123 MIDDLE EAST & AFRICA: 5G SECURITY MARKET, BY COUNTRY, 2021–2028 (USD MILLION)
- TABLE 124 LATIN AMERICA: 5G SECURITY MARKET, BY OFFERING, 2021–2028 (USD MILLION)
- TABLE 125 LATIN AMERICA: 5G SECURITY MARKET, BY SOLUTION, 2021–2028 (USD MILLION)
- TABLE 126 LATIN AMERICA: 5G SECURITY MARKET, BY SERVICE, 2021–2028 (USD MILLION)
- TABLE 127 LATIN AMERICA: 5G SECURITY MARKET, BY NETWORK COMPONENT SECURITY, 2021–2028 (USD MILLION)
- TABLE 128 LATIN AMERICA: 5G SECURITY MARKET, BY ARCHITECTURE, 2021–2028 (USD MILLION)
- TABLE 129 LATIN AMERICA: 5G SECURITY MARKET, BY END USER, 2021–2028 (USD MILLION)
- TABLE 130 LATIN AMERICA: 5G SECURITY MARKET, BY VERTICAL, 2021–2028 (USD MILLION)
- TABLE 131 LATIN AMERICA: 5G SECURITY MARKET, BY APPLICATION, 2021–2028 (USD MILLION)
- TABLE 132 LATIN AMERICA: 5G SECURITY MARKET, BY COUNTRY, 2021–2028 (USD MILLION)
- TABLE 133 OVERVIEW OF STRATEGIES ADOPTED BY KEY PLAYERS
- TABLE 134 DEGREE OF COMPETITION IN 5G SECURITY MARKET
- TABLE 135 OFFERING FOOTPRINT
- TABLE 136 VERTICAL FOOTPRINT
- TABLE 137 REGION FOOTPRINT
- TABLE 138 COMPANY FOOTPRINT
- TABLE 139 LIST OF KEY STARTUPS/SMES
- TABLE 140 5G SECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES
- TABLE 141 5G SECURITY MARKET: PRODUCT LAUNCHES & ENHANCEMENTS, MAY 2021–MAY 2023
- TABLE 142 5G SECURITY MARKET: DEALS, JANUARY 2021–JULY 2023
- TABLE 143 5G SECURITY MARKET: EXPANSIONS, MARCH 2021–NOVEMBER 2023
- TABLE 144 ERICSSON: BUSINESS OVERVIEW
- TABLE 145 ERICSSON: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 146 ERICSSON: PRODUCT LAUNCHES
- TABLE 147 ERICSSON: DEALS
- TABLE 148 ERICSSON: EXPANSIONS
- TABLE 149 PALO ALTO NETWORKS: BUSINESS OVERVIEW
- TABLE 150 PALO ALTO NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 151 PALO ALTO NETWORKS: PRODUCT LAUNCHES
- TABLE 152 PALO ALTO NETWORKS: DEALS
- TABLE 153 CISCO: BUSINESS OVERVIEW
- TABLE 154 CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 155 CISCO: PRODUCT LAUNCHES
- TABLE 156 CISCO: DEALS
- TABLE 157 ALLOT: BUSINESS OVERVIEW
- TABLE 158 ALLOT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 159 ALLOT: PRODUCT LAUNCHES
- TABLE 160 ALLOT: DEALS
- TABLE 161 HUAWEI: BUSINESS OVERVIEW
- TABLE 162 HUAWEI: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 163 HUAWEI: PRODUCT LAUNCHES
- TABLE 164 HUAWEI: DEALS
- TABLE 165 A10 NETWORKS: BUSINESS OVERVIEW
- TABLE 166 A10 NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 167 A10 NETWORKS: PRODUCT LAUNCHES
- TABLE 168 NOKIA: BUSINESS OVERVIEW
- TABLE 169 NOKIA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 170 NOKIA: PRODUCT LAUNCHES
- TABLE 171 NOKIA: DEALS
- TABLE 172 NOKIA: EXPANSIONS
- TABLE 173 F5 NETWORKS: BUSINESS OVERVIEW
- TABLE 174 F5 NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 175 F5 NETWORKS: PRODUCT LAUNCHES
- TABLE 176 F5 NETWORKS: DEALS
- TABLE 177 F5 NETWORKS: EXPANSION
- TABLE 178 JUNIPER NETWORKS: BUSINESS OVERVIEW
- TABLE 179 JUNIPER NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 180 JUNIPER NETWORKS: PRODUCT LAUNCHES
- TABLE 181 JUNIPER NETWORKS: DEALS
- TABLE 182 SPIRENT: BUSINESS OVERVIEW
- TABLE 183 SPIRENT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 184 SPIRENT: PRODUCT LAUNCHES
- TABLE 185 SPIRENT: DEALS
- TABLE 186 5G IOT MARKET, BY COMPONENT, 2020–2028 (USD MILLION)
- TABLE 187 5G IOT MARKET, BY NETWORK TYPE, 2020–2028 (USD MILLION)
- TABLE 188 5G IOT MARKET, BY ORGANIZATION SIZE, 2020–2028 (USD MILLION)
- TABLE 189 5G IOT MARKET, BY TYPE, 2020–2028 (USD MILLION)
- TABLE 190 5G IOT MARKET, BY REGION, 2020–2028 (USD MILLION)
- TABLE 191 5G SERVICES MARKET, BY END USER, 2020–2027 (USD BILLION)
- TABLE 192 5G SERVICES MARKET, BY COMMUNICATION TYPE, 2020–2027 (USD BILLION)
- TABLE 193 5G SERVICES MARKET, BY ENTERPRISE, 2020–2027 (USD BILLION)
- FIGURE 1 5G SECURITY MARKET SEGMENTATION
- FIGURE 2 5G SECURITY MARKET SEGMENTATION, BY REGION
- FIGURE 3 YEARS CONSIDERED
- FIGURE 4 RESEARCH DESIGN
- FIGURE 5 KEY DATA FROM SECONDARY SOURCES
- FIGURE 6 BREAKUP OF PRIMARY INTERVIEWS, BY COMPANY TYPE, DESIGNATION, AND REGION
- FIGURE 7 KEY INDUSTRY INSIGHTS
- FIGURE 8 APPROACH 1 (SUPPLY SIDE): REVENUE OF SOLUTIONS AND SERVICES OFFERED BY 5G SECURITY VENDORS
- FIGURE 9 APPROACH 2 (DEMAND SIDE)
- FIGURE 10 DATA TRIANGULATION
- FIGURE 11 5G SECURITY MARKET TO WITNESS SLIGHT DIP IN Y-O-Y IN 2023
- FIGURE 12 5G SECURITY MARKET, 2021–2028 (USD MILLION)
- FIGURE 13 5G SECURITY MARKET, BY REGION, 2023
- FIGURE 14 RISE IN DEMAND FOR CONNECTED DEVICES TO DRIVE ADOPTION OF 5G SECURITY SOLUTIONS AND SERVICES
- FIGURE 15 5G SECURITY SOLUTIONS TO ACCOUNT FOR LARGER SHARE IN 2023
- FIGURE 16 5G NR NON-STANDALONE SEGMENT TO ACCOUNT FOR LARGER SHARE IN 2023
- FIGURE 17 5G SECURITY MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 18 VALUE CHAIN ANALYSIS
- FIGURE 19 ECOSYSTEM MAP
- FIGURE 20 LIST OF MAJOR PATENTS FOR 5G SECURITY
- FIGURE 21 AVERAGE SELLING PRICE TRENDS OF KEY PLAYERS, BY ENTERPRISE
- FIGURE 22 PORTER’S FIVE FORCES MODEL ANALYSIS
- FIGURE 23 THREE-TIER MODEL FOR CBRS SPECTRUM ACCESS
- FIGURE 24 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- FIGURE 25 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- FIGURE 26 TRENDS/DISRUPTIONS IMPACTING CUSTOMERS’ BUSINESSES
- FIGURE 27 5G SECURITY SERVICES TO EXHIBIT HIGHER GROWTH THAN SOLUTIONS, DESPITE BEING SMALLER
- FIGURE 28 DDOS PROTECTION SEGMENT TO ACHIEVE HIGHEST GROWTH BY 2028
- FIGURE 29 IMPLEMENTATION SEGMENT TO LEAD MARKET BY 2028
- FIGURE 30 MOBILE CORE SECURITY SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
- FIGURE 31 5G NR STANDALONE SEGMENT TO ACCOUNT FOR LARGER SHARE BY 2028
- FIGURE 32 ADOPTION OF 5G SECURITY BY ENTERPRISES TO ACHIEVE MUCH HIGHER GROWTH OVER TELECOM OPERATORS DURING FORECAST PERIOD
- FIGURE 33 USE OF 5G SECURITY IN WIRELESS EHEALTH TO WITNESS HIGHEST GROWTH DURING FORECAST PERIOD
- FIGURE 34 5G SECURITY IN MEDIA & ENTERTAINMENT VERTICAL TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 35 NORTH AMERICA: MARKET SNAPSHOT
- FIGURE 36 ASIA PACIFIC: MARKET SNAPSHOT
- FIGURE 37 HISTORICAL REVENUE ANALYSIS FOR KEY PLAYERS, 2018–2022 (USD BILLION)
- FIGURE 38 5G SECURITY MARKET SHARE ANALYSIS, 2022
- FIGURE 39 COMPANY EVALUATION MATRIX FOR KEY PLAYERS: CRITERIA WEIGHTAGE
- FIGURE 40 COMPANY EVALUATION MATRIX FOR KEY PLAYERS, 2023
- FIGURE 41 COMPANY EVALUATION MATRIX FOR STARTUPS/SMES, 2023
- FIGURE 42 ERICSSON: COMPANY SNAPSHOT
- FIGURE 43 PALO ALTO NETWORKS: COMPANY SNAPSHOT
- FIGURE 44 CISCO: COMPANY SNAPSHOT
- FIGURE 45 ALLOT: COMPANY SNAPSHOT
- FIGURE 46 HUAWEI: COMPANY SNAPSHOT
- FIGURE 47 A10 NETWORKS: COMPANY SNAPSHOT
- FIGURE 48 NOKIA: COMPANY SNAPSHOT
- FIGURE 49 F5 NETWORKS: COMPANY SNAPSHOT
- FIGURE 50 JUNIPER NETWORKS: COMPANY SNAPSHOT
- FIGURE 51 SPIRENT: COMPANY SNAPSHOT
The 5G security market is an attractive market for the providers of 5G security platforms and services. With increasing investments in 5G infrastructure, there has been massive growth in the adoption of IoT devices.
Secondary Research
In the secondary research process, various secondary sources were referred to for identifying and collecting information for this study. The secondary sources included annual reports, press releases, and investor presentations of companies; white papers, certified publications, and articles from recognized associations and government publishing sources; journals and various associations have also been referred to for consolidating the report. Secondary research was mainly used to obtain key information about industry insights, the market’s monetary chain, the overall pool of key players, and market classification and segmentation according to industry trends to the bottom-most level, regional markets, and key developments from both market and technology-oriented perspectives.
Primary Research
In the primary research process, various primary sources from both the supply and demand sides of the 5G security market ecosystem were interviewed to obtain qualitative and quantitative information for this study. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various vendors providing 5G security software, associated service providers, and system integrators operating in the targeted regions. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. After the complete market engineering (including calculations for market statistics, market breakdown, market size estimations, market forecast, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also conducted to identify and validate the segmentation types; industry trends; key players; the competitive landscape of the market; and key market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key strategies.
In the complete market engineering process, both top-down and bottom-up approaches and several data triangulation methods were used to perform the market estimation and forecast for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list the key information/insights throughout the report.
The Breakup of Primary Research:
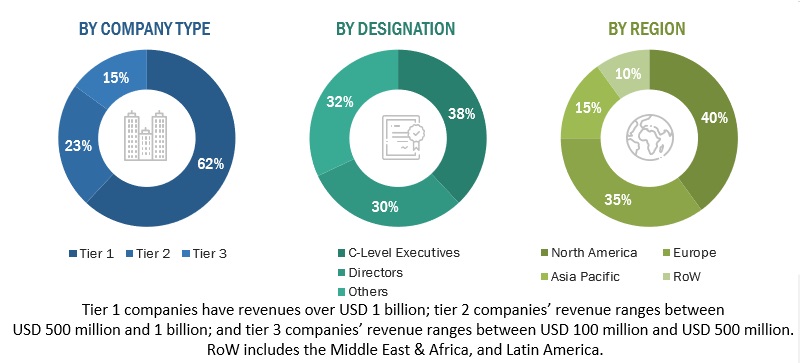
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Multiple approaches were adopted to estimate and forecast the size of the 5G security market. The first approach involves estimating market size by summing up the revenue generated by companies through the sale of 5G security offerings, such as platforms and services.
Both top-down and bottom-up approaches were used to estimate and validate the total size of the 5G security market. These methods were extensively used to estimate the size of various segments in the market. The research methodology used to estimate the market size includes the following:
- Key players in the market have been identified through extensive secondary research.
- In terms of value, the industry’s supply chain and market size have been determined through primary and secondary research processes.
- All percentage shares, splits, and breakups have been determined using secondary sources and verified through primary sources.
5G security Market Size: Bottom-Up Approach
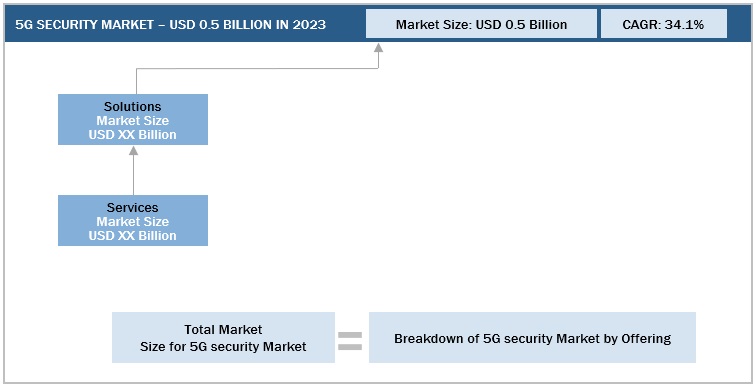
To know about the assumptions considered for the study, Request for Free Sample Report
5G security Market Size: Top-Down Approach
Data Triangulation
After arriving at the overall market size, the 5G security market was divided into several segments and subsegments. A data triangulation procedure was used to complete the overall market engineering process and arrive at the exact statistics for all segments and subsegments, wherever applicable. The data was triangulated by studying various factors and trends from the demand and supply sides. Along with data triangulation and market breakdown, the market size was validated by the top-down and bottom-up approaches.
Market Definition
The 5G security market includes solutions and services that are provided to secure the network of connected devices and critical enterprise applications relying on 5G networks and minimize the losses caused by threats and cyberattacks on networks, applications, and devices. The 5G security market is a segment of the information security market that deals with the security of 5G networks. 5G networks are the fifth generation of cellular networks, and they offer a number of new features and capabilities, such as increased speed, lower latency, and better coverage. These new features and capabilities also introduce new security challenges.
Key Stakeholders
- Technology Vendors
- Mobile Network Operators (MNOs)
- Independent Software Vendors (ISVs)
- Communication Service Providers (CSPs)
- System Integrators (SIs)
- Neutral Host Operators
- Resellers
- Value-added resellers (VARs)
- Managed Service Providers (MSPs)
- Compliance Regulatory Authorities
- Government Authorities
- Investment Firms
- Cloud Service Providers
- 5G Security Alliances/Groups
- Original Design Manufacturers (ODMs)
- Original Equipment Manufacturers (OEMs)
- Enterprises/Businesses
Report Objectives
- To determine and forecast the global 5G security market by component (solutions and services), network component security, architecture, deployment mode, organization size, application, end-user, vertical, and region from 2020 to 2027, and analyze various macro and microeconomic factors that affect the market growth
- To forecast the size of the market’s segments with respect to four main regions: North America, Europe, Asia Pacific, and the Rest of the World (RoW)
- To provide detailed information about the major factors (drivers, opportunities, threats, and challenges) influencing the growth of the market
- To analyze each submarket with respect to individual growth trends, prospects, and contributions to the total market
- To analyze opportunities in the market for stakeholders by identifying the high-growth segments of the 5G security market
- To profile key market players (such as top vendors and startups); provide a comparative analysis based on their business overviews, regional presence, product offerings, business strategies, and key financials; and illustrate the market’s competitive landscape.
- To track and analyze competitive developments, such as mergers and acquisitions (M&As), product developments, partnerships and collaborations, and Research and Development (R&D) activities, in the market
Available Customizations
With the given market data, MarketsandMarkets offers customizations as per the company’s specific needs. The following customization options are available for the report:
Geographic Analysis
- Further breakup of the Asia Pacific market into countries contributing 75% to the regional market size
- Further breakup of the North American market into countries contributing 75% to the regional market size
- Further breakup of the Latin American market into countries contributing 75% to the regional market size
- Further breakup of the Middle East and African market into countries contributing 75% to the regional market size
- Further breakup of the European market into countries contributing 75% to the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...










Growth opportunities and latent adjacency in 5G Security Market