Hardware Security Modules Market Size, Share & Trends, 2025 To 2030
Hardware Security Modules Market by Technology (General Purpose Cryptography, Quantum Cryptography), Type (LAN Based /Network Attached, PCI Based/Embedded Plugins, USB Based, Smart Cards), Deployment Type (Cloud, On-premise) - Global Forecast to 2030




OVERVIEW
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
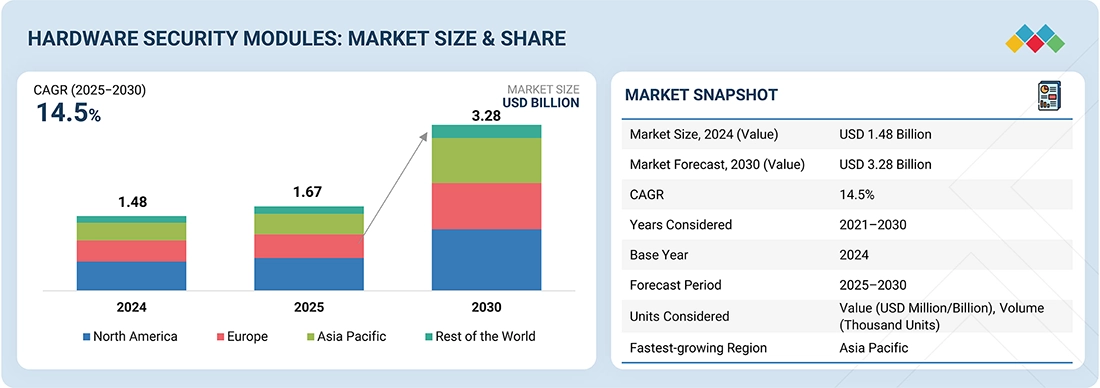
The hardware security modules market is projected to reach USD 3.28 billion by 2030, up from USD 1.67 billion in 2025, growing at a CAGR of 14.5%. Hardware security modules (HSMs) are dedicated, tamper-resistant devices designed to securely generate, manage, and store cryptographic keys, as well as perform encryption, decryption, and authentication functions to protect sensitive digital assets. The hardware security modules market is experiencing strong growth, driven by rising cybersecurity threats, digital transformation, and stricter data protection regulations, such as the GDPR and PCI-DSS. The increasing adoption of cloud services, digital payments, and post-quantum cryptography solutions is further accelerating demand for scalable and compliant HSM deployments across various industries.
KEY TAKEAWAYS
- North America is estimated to dominate the hardware security modules (HSM) market with a share of 39.0% in 2025.
- The LAN-based/network-attached segment is expected to dominate the market due to its scalability, centralized key management, and widespread deployment across data centers and enterprise networks.
- By deployment type, the on-premises segment accounted for a share of 68.0% in terms of value in 2024.
- By technology, the quantum cryptography segment is projected to grow at a CAGR of 28.5% during the forecast period.
- By application, payment processing is estimated to account for a significant share of the hardware security modules (HSM) market in 2025.
- By vertical, medical & life sciences is projected to grow at the highest CAGR during the forecast period.
- Thales, Futurex, IBM, Entrust Corporation, and Utimaco Management Services GmbH were identified as star players in the hardware security modules market, given their broad industry coverage and strong operational & financial strength.
- Sansec, Securosys, and Fortanix have distinguished themselves among startups and SMEs due to their well-developed marketing channels and extensive funding to build their product portfolios.
The hardware security modules (HSM) market is witnessing strong growth driven by the rising need for data protection, regulatory compliance, and secure cryptographic key management across industries. The proliferation of digital payments, cloud-based services, and IoT devices has amplified demand for hardware-based security to safeguard sensitive information. Additionally, the transition toward post-quantum cryptography and cloud HSM solutions is further accelerating adoption.
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
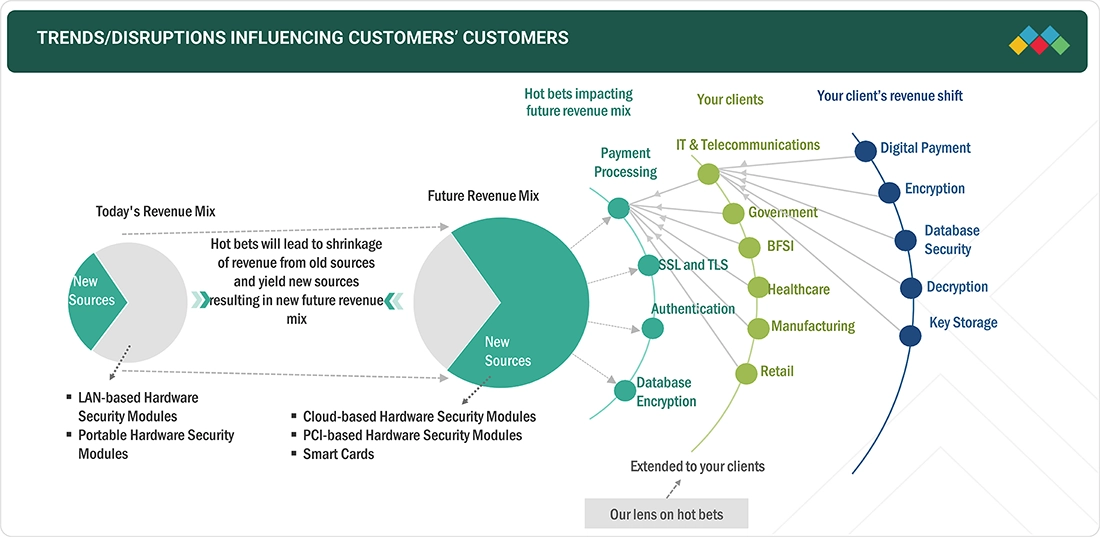
The hardware security modules market is experiencing rapid growth driven by the increasing demand for secure cryptographic key management, regulatory compliance requirements, and the rising adoption of digital payment systems. HSMs play a critical role in safeguarding sensitive data by providing a dedicated, tamper-resistant environment for encryption, authentication, and key management processes. As security threats evolve, the market is witnessing a shift from traditional LAN-based and portable HSMs to cloud-based and PCI-based solutions, ensuring scalable and compliant data protection strategies.
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Increasing data breaches and cyberattacks

-
Need to comply with stringent data security regulations and standards
Level
-
High ownership costs associated with hardware security modules
-
Susceptibility to cyberattacks and security breaches
Level
-
Rising volume of data generated by websites and mobile apps
-
Rise of telemedicine and remote healthcare services
Level
-
Discovering and protecting sensitive data
-
Complexities associated with HSM integration process
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Increasing data breaches and cyberattacks
The growing frequency and sophistication of cyberattacks have heightened the need for robust data protection and encryption mechanisms across industries. Hardware security modules (HSMs) provide a trusted root of security by safeguarding cryptographic keys and sensitive information against unauthorized access. As organizations adopt digital transformation and cloud technologies, HSMs are becoming critical for ensuring data integrity and regulatory compliance.
Restraint: High ownership costs associated with hardware security modules
The initial investment and maintenance costs associated with deploying HSMs are relatively high compared to those of software-based security solutions. Expenses related to specialized hardware, integration, compliance, and skilled personnel can limit adoption, particularly among small and medium enterprises. These high costs often act as a barrier, restraining market penetration in cost-sensitive sectors.
Opportunity: Rise of telemedicine and remote healthcare services
The rapid expansion of telemedicine and remote healthcare services is creating new demand for secure data exchange and identity protection. HSMs play a vital role in encrypting patient records, managing digital identities, and ensuring the authenticity of connected medical devices. As healthcare systems increasingly adopt cloud-based platforms and IoT-enabled tools, the need for HSM-backed encryption and trust frameworks is expected to surge.
Challenge: Complexities associated with HSM integration process
Integrating HSMs into existing IT infrastructures can be complex due to compatibility issues, legacy systems, and diverse cryptographic requirements. Many organizations face challenges in aligning HSM deployments with multi-cloud and hybrid environments while maintaining operational efficiency. This integration complexity can slow down implementation timelines and increase overall project costs, posing a key challenge for vendors and end users alike.
Hardware Security Modules Market: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
Deployed Excrypt series payment HSMs and Excrypt Touch management devices to modernize EPX’s cryptographic infrastructure, enabling centralized remote management, enhanced automation, and seamless scalability across global operations | Enabled launch of first-to-market virtual terminal service, improved cryptographic throughput, achieved P2P compliance, simplified upgrades, and ensured long-term, future-proof payment processing |
 |
Delivered DSM SaaS for centralized encryption key management and unified security across AWS, GCP, and Azure, integrating external key management and tokenization for multi-cloud data protection | Strengthened global data security, reduced operational complexity, provided zero-downtime key management, and ensured consistent, policy-driven protection across hybrid and multi-cloud environments |
 |
Implemented VirtuCrypt cloud-based payment HSMs to secure card issuance and transaction processing for physical, virtual, and crypto-linked payments, ensuring regulatory compliance and encrypted data handling | Met PCI-DSS requirements, expanded services to include card issuance and identity verification, enhanced transaction security, and accelerated digital payment infrastructure scalability |
 |
Migrated the bank’s payment security infrastructure from ARX to Futurex HSMs to protect encryption processes for ATMs, kiosks, and mobile payment systems | Strengthened encryption and key management, improved transaction security, and modernized digital banking operations with reliable cryptographic processing |
 |
Deployed Luna HSMs as the cryptographic root of trust for the national Interoperable Digital Transaction Platform (IDTP “Binimoy”) to secure real-time digital fund transfers | Enabled secure, real-time transactions across 125 branches, ensured compliance with FIPS 140-2 standards, enhanced audit readiness, and supported Bangladesh’s transition toward a cashless economy |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The hardware security module market ecosystem is a complex network of stakeholders working together to ensure secure cryptographic operations across industries. The hardware security module (HSM) ecosystem consists of HSM manufacturers and vendors that offer both on-premises and cloud solutions. These solutions are distributed to end-users across a variety of industries, including banking, financial services, and insurance (BFSI), information technology (IT), government, healthcare, and retail. There is a noticeable shift in client revenue toward areas such as digital payments, encryption, data security, decryption, and key storage.

Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Hardware Security Modules Market, by Product Type
The LAN-based/network-attached HSM segment is estimated to dominate the market due to its widespread adoption across enterprises for centralized, high-performance encryption operations. These HSMs provide seamless scalability, remote management, and integration with multiple applications across corporate networks, making them ideal for large-scale deployments. Their ability to deliver continuous key protection and fast transaction processing positions them as the preferred choice for data centers, financial institutions, and government organizations driving digital transformation.
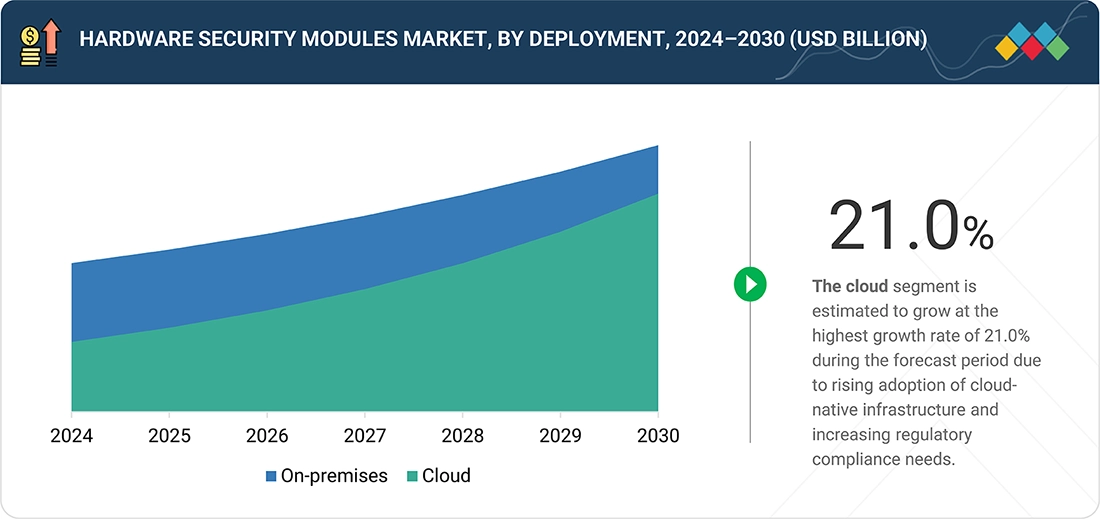
Hardware Security Modules Market, by Deployment Type
The cloud-based HSM segment is projected to grow at the highest rate, driven by the rising adoption of cloud-native applications and multi-cloud infrastructures. Organizations are increasingly opting for cloud HSMs to achieve flexibility, scalability, and cost efficiency while meeting stringent regulatory requirements. With growing reliance on digital identities, remote access, and SaaS platforms, cloud HSMs are becoming the backbone of secure cryptographic key management in virtualized environments.
Hardware Security Modules Market, by Technology
The quantum cryptography segment is expected to grow at a high rate in the hardware security modules market. This growth is driven by increasing concerns over the potential of quantum computers to break traditional encryption methods. Enterprises and governments are increasingly investing in quantum-safe cryptographic solutions to secure sensitive data. Additionally, rising regulatory focus on data protection and the adoption of next-generation secure key management systems are further fueling the demand for quantum cryptography-enabled HSMs.
Hardware Security Modules Market, by Application
Payment processing is estimated to account for the largest market share owing to the critical need for secure transaction authentication and encryption in the financial ecosystem. HSMs are integral to payment networks, safeguarding sensitive data, managing cryptographic keys, and ensuring compliance with PCI DSS and EMV standards. The rapid growth of digital payments, contactless transactions, and e-commerce is further fueling demand for HSM solutions across banks and payment service providers.
Hardware Security Modules Market, by Vertical
The BFSI sector dominated the HSM market, driven by stringent data protection mandates and the need for secure financial transactions. Banks, insurance companies, and fintech firms rely heavily on HSMs for encryption, key management, and digital signing to prevent fraud and ensure data integrity. With the expansion of digital banking and the integration of blockchain-based services, BFSI continues to be the primary growth engine for the HSM industry.
REGION
Asia Pacific to be fastest-growing region in global hardware security modules market during forecast period
The Asia Pacific region is estimated to grow at a high rate due to rapid digitization, expansion of cloud infrastructure, and government-led cybersecurity initiatives. Increasing adoption of online banking, digital payments, and e-governance programs across countries such as China, India, and Japan is driving strong demand for HSMs. The rising awareness of data security and compliance requirements is encouraging regional enterprises to invest in advanced cryptographic hardware solutions.

Hardware Security Modules Market: COMPANY EVALUATION MATRIX
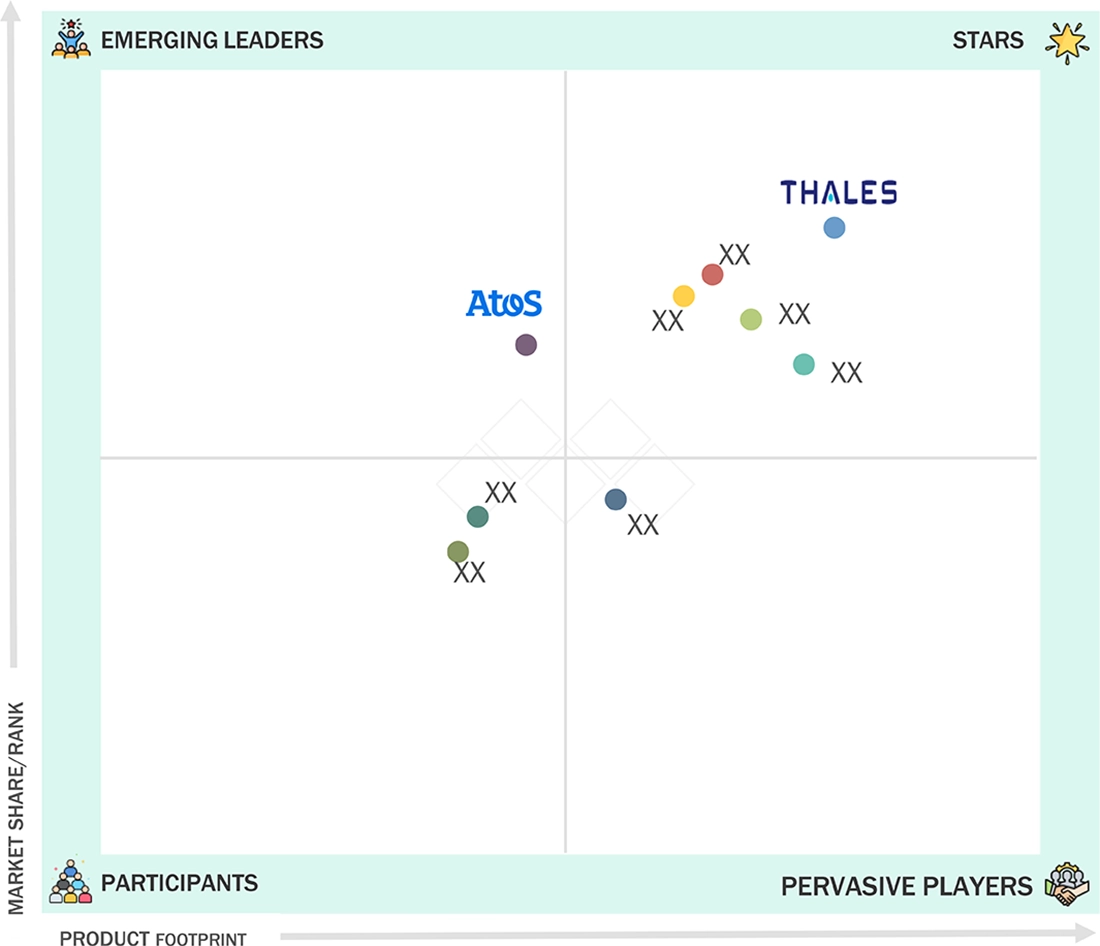
The company evaluation matrix for the hardware security modules (HSM) market highlights the positioning of key players based on their technological innovation, market penetration, and strategic expansion initiatives. In the HSM market matrix, Thales leads with its strong global presence and extensive portfolio of general-purpose and payment HSMs, offering robust, FIPS-certified security solutions that cater to both on-premises and cloud environments. Atos SE is rapidly gaining momentum by expanding its next-generation cybersecurity hardware offerings and cloud-based HSM services, focusing on scalable, high-performance encryption solutions to support digital transformation and data protection across critical industries.
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size, 2024 (Value) | USD 1.48 Billion |
| Market Forecast, 2030 (Value) | USD 3.28 Billion |
| Growth Rate | CAGR of 14.5% from 2025 to 2030 |
| Years Considered | 2021–2030 |
| Base Year | 2024 |
| Forecast Period | 2025–2030 |
| Units Considered | Value (USD Million/Billion), Volume (Thousand Units) |
| Report Coverage | Revenue Forecast, Company Ranking, Competitive Landscape, Growth Factors, and Trends |
| Segments Covered |
|
| Regional Scope | North America, Europe, Asia Pacific, Rest of the World (RoW) |
WHAT IS IN IT FOR YOU: Hardware Security Modules Market REPORT CONTENT GUIDE
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Local Competitive Landscape | Profiles of key regional HSM providers, including market share, revenue, product portfolio (e.g., on-premises vs. cloud-based modules), and strategic partnerships | Facilitated competitive benchmarking and informed go-to-market positioning |
| Regional Market Entry Strategy | Country- or region-specific HSM deployment strategies, including regulatory hurdles (e.g., data sovereignty laws), certification requirements, and competitive ecosystem | Minimized compliance risks and accelerated secure infrastructure rollout |
| Local Risk & Opportunity Assessment | Identification of regional cybersecurity threats, supply chain vulnerabilities, and untapped opportunities in sectors like finance or healthcare | Enabled proactive threat mitigation and targeted investment in resilient HSM solutions |
| Technology Adoption by Region | Insights on local uptake of advanced HSM features (e.g., FIPS 140-3 compliance, quantum-resistant cryptography, and integration with zero-trust architectures) | Guided R&D prioritization, product customization, and strategic vendor selections |
| Sector-Specific Compliance Mapping | Tailored analysis of HSM alignment with industry standards (e.g., PCI-DSS for payments, GDPR for data protection) across key verticals like government and cloud services | Streamlined certification processes and enhanced trust in multi-sector deployments |
RECENT DEVELOPMENTS
- December 2024 : Futurex collaborated with Cake, Vietnam’s leading digital bank, to pioneer secure payment processing through cloud-based payment HSM technology. This initiative resulted in the launch of Vietnam’s first fully cloud-based card management system, which operates on Visa Cloud Connect and is powered by Futurex’s cloud HSMs.
- October 2024 : Eviden launched PQC HSMaaS, a sovereign post-quantum cryptography HSM-as-a-Service. Powered by the Eviden HSM Trustway Proteccio brand, this solution would be unique in the market due to its “reinforced qualification” from the French National Cybersecurity Agency (ANSSI), ensuring the highest level of security for businesses.
- May 2024 : Utimaco Management Services GmbH (Germany) and ShardSecure partnered to provide a holistic data protection solution. ShardSecure protects unstructured data, while Utimaco protects structured data. This combined solution leveraged Utimaco’s HSMs to provide secure at-rest encryption for ShardSecure’s encryption keys, ensuring strong data protection against various threats.
- January 2024 : Entrust Corporation launched its Post-Quantum Ready PKI-as-a-Service (PKIaaS PQ), the first commercially available platform offering composite and pure quantum-safe certificate authority hierarchies. This cloud-based solution enabled businesses to test or implement quantum-safe infrastructure while simplifying scalability by reducing on-premise dependencies. It provided centralized visibility, control, automation, and public SSL/TLS management via the cloud.
- December 2023 : Thales acquired Imperva, expanding its cybersecurity portfolio. This acquisition combined Thales’ existing security solutions with Imperva’s application, data, and identity security offerings, creating a more comprehensive and robust cybersecurity provider for customers facing increasingly complex threats.
Table of Contents

Methodology
The research study involved 4 major activities in estimating the size of the hardware security modules market. Exhaustive secondary research has been done to collect important information about the market and peer markets. The validation of these findings, assumptions, and sizing with the help of primary research with industry experts across the value chain has been the next step. Both top-down and bottom-up approaches have been used to estimate the market size. Post which the market breakdown and data triangulation have been adopted to estimate the market sizes of segments and sub-segments.
Secondary Research
In the secondary research process, various sources were referred to identify and collect information on the hardware security modules market for this study. Secondary sources considered for this research study include government sources, corporate filings (such as annual reports, investor presentations, and financial statements), and trade, business, and professional associations. Secondary research was done to obtain key information about the market’s supply chain, the pool of key market players, and market segmentation according to industry trends, regions, and developments from market and technology-oriented perspectives.
In the hardware security modules market report, the global market size has been estimated using both the top-down and bottom-up approaches, along with several other dependent submarkets. The major players in the market were identified using extensive secondary research, and their presence in the market was determined using secondary and primary research. All the percentage shares splits, and breakdowns have been determined using secondary sources and verified through primary sources.
Primary Research
Primary interviews have been conducted to gather insights such as market statistics, data on revenue collected from the products and services, market breakdowns, market size estimations, market forecasting, and data triangulation. Primary research also helped understand the trends related to technologies, applications, and regions. Stakeholders from the demand side, such as CIOs, CTOs, CSOs, and installation teams of the customers/end users who are using hardware security modules, have been interviewed to understand the buyer’s perspective on the suppliers, manufacturers, service providers, and their current usage of hardware security modules and the outlook of their businesses, which will affect the overall hardware security modules market. Approximately 20% of primary interviews have been conducted with the demand side and 80% with the supply side. The primary data has been collected through telephonic interviews, questionnaires, and emails.
After successful interaction with industry experts, brief sessions were conducted with highly experienced independent consultants to reinforce the findings of our primary research. This, along with the in-house subject matter experts’ opinions, has led us to the findings as described in the report.
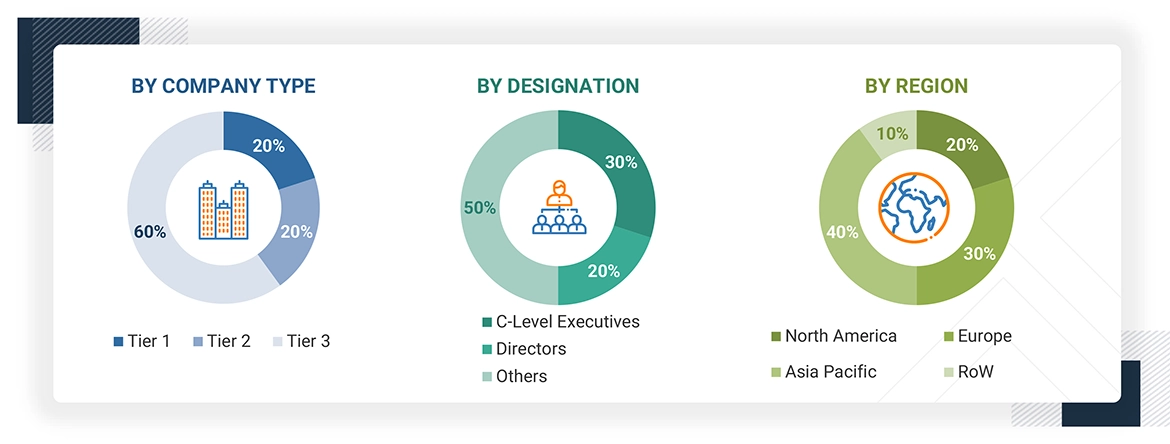
Note: “Others” includes sales, marketing, and product managers
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
In the complete market engineering process, the top-down and bottom-up approaches and several data triangulation methods have been implemented to estimate and validate the size of the hardware security modules market and various other dependent sub-markets. Extensive qualitative and quantitative analyses have been performed on the complete market engineering process to list key information/insights throughout the report. The research methodology used to estimate the market sizes includes the following:
- Identifying top-line investments and spending in the ecosystem and considering segment-level splits and major market developments
- Identifying different stakeholders in the hardware security modules market that influence the entire market, along with participants across the supply chain
- Analyzing major manufacturers in the hardware security modules market and studying their solutions
- Analyzing trends related to the adoption of hardware security modules
- Tracking recent and upcoming market developments, including investments, R&D activities, product launches, expansions, agreements, collaborations, acquisitions, contracts, and partnerships, as well as forecasting the market size based on these developments and other critical parameters
- Carrying out multiple discussions with key opinion leaders to identify the adoption trends of hardware security modules
- Segmenting the overall market into various other market segments
Hardware Security Modules Market: Bottom-Up Approach
The bottom-up approach has been used to arrive at the overall size of the hardware security modules market from the revenues of key players and their shares in the market. Key players have been identified based on several parameters: product portfolio analysis, revenue, R&D expenditure, geographic presence, and recent activities. The overall market size has been calculated based on the revenues of the key players identified in the market.
Market Size Estimation Methodology- Top-down approach
In the top-down approach, the overall size of the hardware security modules market has been used to estimate the size of the individual markets (mentioned in the market segmentation) through percentage splits obtained from secondary and primary research. For calculating the size of the specific market segments, the size of the most appropriate immediate parent market has been used to implement the top-down approach. The bottom-up approach has also been implemented for the data extracted from the secondary research to validate the market size obtained. The size of the parent and individual markets has been determined and confirmed in this study by the data triangulation procedure and the validation of the data through primaries. The data triangulation procedure used for this study has been explained in the next section.
Hardware Security Modules Market : Top-Down and Bottom-Up Approach
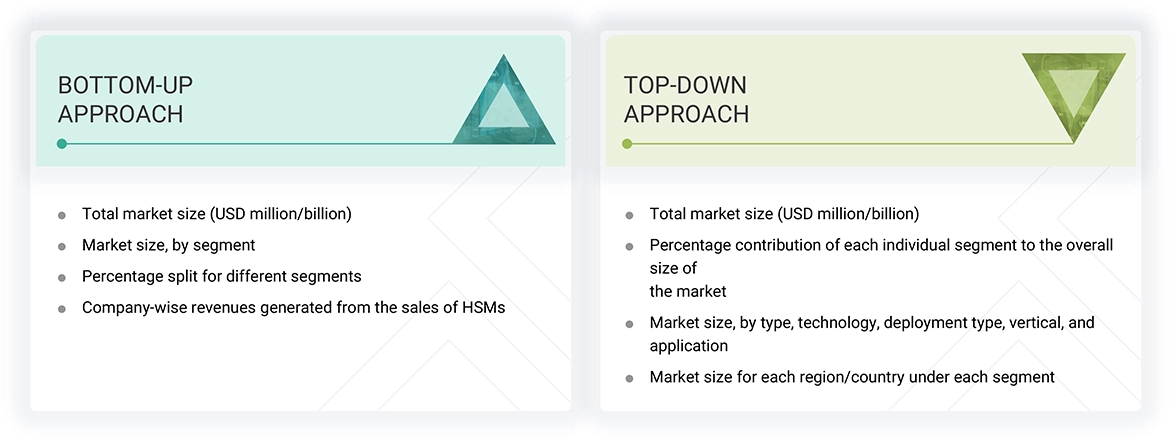
Data Triangulation
After arriving at the overall size of the hardware security modules market through the process explained above, the total market has been split into several segments and sub-segments. Where applicable, market breakdown and data triangulation procedures have been employed to complete the overall market engineering process and arrive at the exact statistics for all segments and sub-segments. The data has been triangulated by studying various factors and trends from the demand and supply sides. The market has also been validated using top-down and bottom-up approaches.
Market Definition
Hardware security modules are cryptoprocessors employed to secure and handle cryptographic keys as well as speed up cryptographic processing utilizing those keys. They provide on-board key generation and storage, accelerated symmetric and asymmetric encryption, and encrypted backup of sensitive information. Hardware security modules additionally provide robust authentication and physical protection against tamper to guard the critical processing data and enforce safety policies and accessibility control. These modules are implemented as plugin cards or stand-alone appliances connected directly to a computer or network server. Organizations are focusing on strong encryption and security solutions to protect their digital assets due to growing cyber threats, data breaches, and strict regulatory environments. Hardware security modules (HSMs) are dedicated hardware appliances that have been designed to execute secure cryptographic functions, such as key generation, storage, encryption, and digital signing. The demand for HSMs is growing due to the expanding digital economy, the use of the cloud, and the increasing activities of cybercrime. The shift towards multi-cloud infrastructures and digital payments has strengthened demand for as-a-service and cloud-based HSMs. As quantum computing risks are changing, businesses are also exploring post-quantum cryptographic HSMs to prepare for the future for their data security infrastructure.
Key Stakeholders
- Suppliers of raw materials and equipment manufacturers
- Vendors of semiconductor wafers
- Fabless players
- Foundry players
- Original equipment manufacturers (OEMs)
- Original design manufacturers (ODMs) and OEM technology providers
- Networking solution providers
- Distributors and retailers of hardware security modules
- Research organizations
- Technology standards organizations, forums, alliances, and associations
- Technology investors
- Software providers
- Value-added resellers (VARs)
Report Objectives
- To describe and forecast the hardware security modules market, in terms of value, based on type, deployment type, technology, application, vertical, and region
- To forecast the hardware security modules market, in terms of volume, based on type
- To provide detailed information on the factors influencing the market dynamics (drivers, restraints, opportunities, and challenges)
- To analyze opportunities for stakeholders by identifying the high-growth segments of the hardware security modules market
- To forecast the market in terms of value for various segments with respect to North America, Europe, Asia Pacific, and RoW
- To give a detailed overview of the industry’s supply chain, along with industry trends, technology trends, case studies, regulatory standards, ecosystem analysis, impact of AI, investment and funding scenario, trade analysis, tariff analysis, patent analysis, and Porter’s five forces analysis
- To strategically analyze the micromarkets with respect to individual growth trends, prospects, and contributions to the total market
- To strategically profile the key players and comprehensively analyze their market rankings and core competencies
- To map the competitive intelligence based on company profiles, key player strategies, and game-changing developments, such as product launches, collaborations, and acquisitions
- To benchmark market players using the proprietary company evaluation quadrant, which analyzes market players on various parameters within the broad categories of business strategy excellence and strength of product portfolio
Available Customizations
With the given market data, MarketsandMarkets offers customizations according to the specific requirements of companies. The following customization options are available for the report:
Country-wise Information:
- Country-wise breakdown for North America, Europe, Asia Pacific, and Rest of the World
Company Information:
- Detailed analysis and profiling of additional market players (up to five)
Key Questions Addressed by the Report
|
Enhanced Cryptographic Performance |
8 |
|
Proactive Threat Detection |
9 |
|
Adaptive Authentication Mechanisms |
7 |
|
Scalability for AI Workloads |
6 |
|
Automation in Key Management |
7 |
Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the Hardware Security Modules Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free Customisation














Growth opportunities and latent adjacency in Hardware Security Modules Market