Embedded Security Market Size, Share & Industry Trends Growth Analysis Report by Offering (Hardware (Secure Element, Embedded Sim, Hardware Token), Software, Services), Security Type (Authentication and Access Management, Payment, Content Protection), Application and Region - Global Forecast to 2028
Updated on : Oct 22, 2024
Embedded Security Market Size & Share
The embedded security market size has been estimated to be valued at USD 7.4 Billion in 2023 and is projected to reach USD 9.8 Billion by 2028, growing at a CAGR of 5.7% during the forecast period from 2023 to 2028.
The growth of the embedded security market is attributed to several key factors. Firstly, the increased connectivity of devices and gadgets to the Internet, known as IoT, makes them vulnerable to cyberattacks. Security tools integrated into these devices play a role in safeguarding them from such attacks. Secondly, the use of advanced AI, specifically generative AI, to create malicious content that can harm devices is on the rise. Security tools are effective in detecting and preventing these harmful actions.
Thirdly, the need for safeguarding devices like smartwatches used for payments against fraudulent activities is driving market growth. Additionally, regulations in different countries are mandating the use of security tools, which are becoming more affordable, user-friendly, and powerful. These combined factors contribute significantly to the expansion of the embedded security industry.
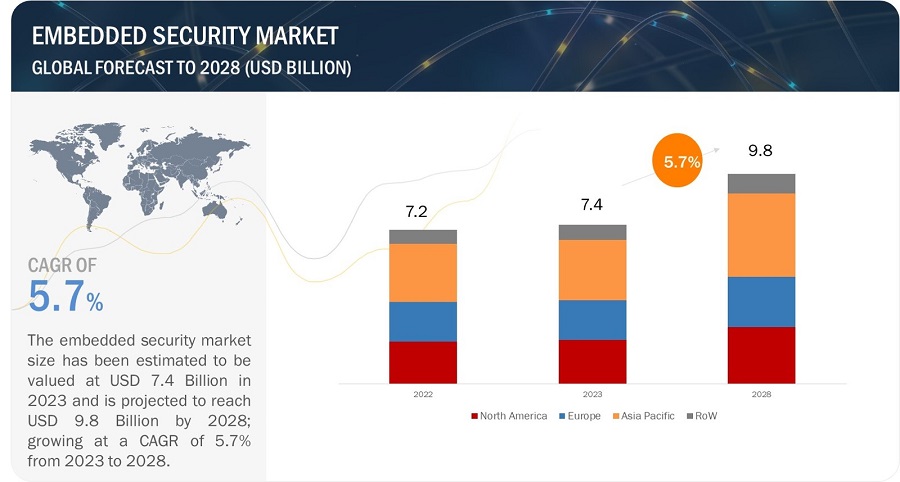

Embedded Security Market Forecast to 2028
To know about the assumptions considered for the study, Request for Free Sample Report
Embedded Security Market Trends
Driver: Growing adoption of generative AI in various applications
In recent years, the global embedded security market has witnessed a significant surge in growth, primarily attributed to the increasing adoption of generative artificial intelligence (AI) across various applications.
This burgeoning trend is reshaping the cybersecurity landscape and is driven by the ever-evolving need for enhanced data protection, privacy, and threat mitigation. Generative AI, leveraging advanced algorithms and deep learning techniques, has demonstrated unparalleled capabilities in generating realistic data, images, and even text.
While its application spans across numerous sectors, such as creative content generation and predictive modeling, its infusion into security applications has been particularly transformative. Industries such as finance, healthcare, automotive, and IoT have embraced generative AI-powered solutions to fortify their security frameworks against emerging cyber threats.
Restraint: Costs associated with hardware security modules
Hardware security modules designed with older-generation expertise present substantial barriers to adoption. First, they are developed using commercial hardware that have a high preliminary acquisition cost. Second, they bring substantial complexity and cost of operations. In many cases, the staff costs to handle and control these modules greatly surpass the module's cost.
The total cost and complexity prove to be unaffordable for many companies, leading to critical gaps in encryption key management for data protection. However, newer technologies can enable businesses to reassess their cost/benefit analysis and implement more robust security controls with low initial investments. Organizations are finding that next-generation hardware security modules and key management capabilities offered as a subscription-based approach deliver powerful data protection and reduce the total cost of ownership.
Opportunity: Introduction of 5G and development of 5G-enabled embedded devices
The advent of 5G technology is expected to serve as an opportunity for growth of the market for embedded security systems. The GSM Association (GSMA) estimates that by 2034, the 5G sector will have contributed USD 2.2 trillion to the global economy, accounting for 5.3% of the global GDP growth.
As a result, the production of embedded devices based on 5G architecture is expected to grow in the future. Embedded devices used in automotive smart camera surveillance systems deliver faster response rates due to the integration of 5G in their design. Additionally, 5G technology is expected to help address the challenges faced during industrial automation and smart farming as it enables faster image processing. Therefore, embedded devices that support 5G infrastructure are expected to further the market growth.
Challenge: Complexities involved in designing embedded systems
While some embedded systems are quite simple, they are gradually becoming complex, and an increasing number of them can either replace human decision-making or provide capabilities beyond what a human can deliver. For example, some aviation systems, such as those used in drones, can integrate sensor data and act on it faster than a human, allowing for new types of operating characteristics. Designing of such applications that offer so many features poses a challenge that can reduce the effectiveness of an embedded system.
Embedded Security Market Ecosystem
An embedded security system is a set of computer hardware, software, firmware, and operating system designed to perform a specific function. These systems may be configurable or fixed to perform certain tasks.
Embedded systems can be found in industrial machinery, consumer electronics, agricultural and processing equipment, automobiles, medical equipment, cameras, smartwatches, household items, aircraft, commercial equipment, toys, and mobile devices. Key players in embedded security system ecosystem includes Infineon Technologies AG, NXP Semiconductors, Qualcomm Technologies, Inc., Texas Instruments Incorporated, STMicroelectronics, Thales Group, Samsung, Broadcom, Cisco, Rambus, IBM, Microchip Technology, Inc., . IDEMIA, and Renesas.

Embedded Security Market Segment
Based on security type, payment segment likely to dominate the overall embedded security market between 2023 and 2028
The prevalence of embedded security in payment applications can be attributed to several pivotal factors. Firstly, it safeguards sensitive data like credit card details and bank account numbers, shielding them from unauthorized access, usage, or exposure.
Additionally, it acts as a bulwark against fraudulent activities by verifying the legitimacy of payment initiators through techniques like biometric authentication, device fingerprinting, and transaction scrutiny. Moreover, embedded security aids businesses in adhering to the escalating global governmental regulations concerning payment application security. Lastly, it plays a crucial role in bolstering customer assurance, addressing the mounting apprehensions around payment data security and ensuring that users feel their information is well-protected.
Hardware segment likely to account for largest market share for embedded security market from 2023 to 2028
Hardware-embedded security is essential to protect sensitive data in a variety of applications. As the number of connected devices and the amount of sensitive data continues to grow, the need for hardware-embedded security will only become more critical.
The most commonly used hardware security are secure elements, embedded SIM, trusted platform modules, hardware security modules, and hardware tokens. A secure element is a tamper-resistant microchip that is used to store cryptographic keys and perform cryptographic operations. Secure elements are often used in payment cards, mobile devices, and other IoT devices to protect sensitive data. An embedded SIM (eSIM) is a digital SIM card that is embedded in a device. eSIMs are becoming increasingly popular as they offer a more secure and convenient way to manage cellular connectivity.
Smart Identity Cards application segment to witness the largest market share in the overall embedded security market during the forecast period
The widespread adoption of embedded security in smart identity card applications can be attributed to several key factors. Firstly, the increasing popularity of smart identity cards for verifying individuals’ identities, driven by the growing need for secure identification in areas such as e-government services, border control, and access management.
Secondly, the advancing sophistication of cyberattacks that traditional security measures struggle to counter, making embedded security essential for protecting smart identity cards from these evolving threats.
Additionally, the rising regulatory emphasis on the security of smart identity cards worldwide necessitates the integration of embedded security to ensure compliance. Lastly, there's a demand for seamless user experiences, prompting the inclusion of embedded security features that enhance security without compromising user-friendliness or convenience.
Embedded Security Market Regional Analysis
APAC to lead the embedded security market between 2023 and 2028 owing to the surging adoption of embedded security devices in end-use applications such as consumer IoT Devices, wearables, and automobiles
A combination of influential factors is propelling the embedded security market in the Asia Pacific region. There's a significant surge in the adoption of embedded security in various end-use applications, including IoT devices, automotive systems, and wearables.
This is due to the increasing recognition of embedded security's crucial role in safeguarding sensitive data and ensuring the integrity of these interconnected technologies. Additionally, the growing prevalence of cyber threats and sophisticated attacks in the region necessitates more robust security measures, leading to an increased demand for embedded security solutions. Moreover, regulatory requirements and standards set by governments are compelling businesses to implement powerful security mechanisms, thus driving the market forward.
The rise in digital transformation initiatives and the proliferation of online transactions further emphasize the importance of embedded security, boosting its market growth. Furthermore, the increasing consumer awareness regarding data privacy and security is prompting companies to prioritize embedded security solutions to build and maintain customer trust. Lastly, advancements in embedded security technologies, such as hardware-based encryption and authentication methods, encourage organizations to invest in cutting-edge solutions to stay ahead in the evolving threat landscape.

Embedded Security Market by Region
To know about the assumptions considered for the study, download the pdf brochure
Top Embedded Security Comapnies - Key Market Players
The embedded security companies is dominated by a few globally established players such as
- Infineon (Germany),
- STMicroelectronics (Switzerland),
- NXP (Netherlands),
- Qualcomm (US),
- Thales Group (France),
- Microchip Technology (US), and
- Texas Instruments (US).
Embedded Security Market Report Scope
|
Report Metric |
Details |
| Estimated Market Size | USD 7.4 Billion in 2023 |
| Projected Market Size | USD 9.8 Billion by 2028 |
| Growth Rate | CAGR of 5.7% |
|
Market size available for years |
2019–2028 |
|
Base year considered |
2022 |
|
Forecast period |
2023–2028 |
|
Forecast units |
Value (USD Million) and Volume (Thousand Units) |
|
Segments covered |
By Offering, By Security Type, By Application, By Region |
|
Geographies covered |
Asia Pacific, Europe, North America and Rest of World |
|
Companies covered |
The key players in the embedded security market are Infineon (Germany), STMicroelectronics (Switzerland), NXP (Netherlands), Qualcomm ((US), Thales Group (France), Microchip Technology (US), Samsung (South Korea), Texas Instruments (US), IDEMIA (France), Renesas (Japan). |
Embedded Security Market Highlights
The study categorizes the embedded security market based on offering, security type, application, and region.
|
Segment |
Subsegment |
|
By Offering: |
|
|
By Security type: |
|
|
By Application: |
|
|
By Region: |
|
Recent Developments in Embedded Security Industry
- In July 2023, Thales signed an agreement with Thoma Bravo, a prominent software investment firm, for the complete acquisition of Imperva, a leading data and application cybersecurity company based in the US.
- In June 2023, Thales unveiled a collaborative initiative with Google Cloud to create advanced data security capabilities utilizing generative AI technology.
- In May 2023, STMicroelectronics introduced the STM32Trust TEE Secure Manager, a pioneering microcontroller system-on-chip security solution that streamlines the development of embedded applications, ensuring effortless out-of-the-box protection.
- In May 2023, Renesas Electronics introduced three new MCU groups specifically designed for motor control applications.
- In April 2023, Texas Instruments launched a new SimpleLink family of Wi-Fi 6 companion integrated circuits (ICs), designed to facilitate the implementation of reliable, secure, and efficient Wi-Fi connections at a budget-friendly price.
- In March 2023, Microchip Technology Inc. introduced six new products in its CryptoAuthentication and CryptoAutomotive IC families, significantly expanding its secure authentication device portfolio.
- In March 2023, STMicroelectronics unveiled its latest STM32H5 microcontroller (MCU) series, designed for enhanced performance, and fortified with cutting-edge security features that STM32Trust TEE Security Manager enabled.
- In February 2023, Infineon Technologies AG introduced its SECORA Connect portfolio, comprising sturdy chips that come in compact sizes, some of which are less than half the size of ladybugs.
- In August 2022, Infineon Technologies AG announced the launch of its groundbreaking SECORA Pay software. This cutting-edge solution sets the stage for the future of payments, catering to the latest trends in the industry.
- In August 2022, Microchip Technology Inc. (Nasdaq: MCHP) announced the expansion of its MPU System-on-Modules (SOMs) portfolio with the addition of the SAM9X60D1G-SOM.
Frequently Asked Questions (FAQ):
How big is the global embedded security market?
The embedded security market size has been estimated to be valued at USD 7.4 Billion in 2023 and is projected to reach USD 9.8 Billion by 2028, growing at a CAGR of 5.7% from 2023 to 2028.
Where is embedded security solutions primarily used?
Embedded security solutions are used to protect the software that runs on top of embedded systems from any significant threats. An embedded system is made up of programmable hardware that is integrated with the operating system and software.
Which region is likely to offer lucrative opportunities in the embedded security market?
Asia Pacific is lkely to offer lucrative opportunities in the global embedded security market. Due to the ever-growing threat landscape, APAC is highly focused on increasing its security spending. APAC comprises emerging economies such as South Korea, China, Australia, and Hong Kong. Factors such as continual growth in the mobile workforce, the unregulated nature of the internet, increasing complexity of businesses, and consolidating BYOD trends require strong security solutions, which, in turn, are expected to encourage such SMBs to adopt various security solutions.
What are the latest technological trends in the embedded security market?
Embedded security solutions are being increasingly used in automotive and wearables applications. Payment functionality is an emerging trend in the field of embedded security solutions. Contactless payments are made with contactless cards or mobile apps. Consumers can pay with a wearable device, such as a smartwatch, or with e-wallets on their smartphones. FinTech organizations have already begun using innovative techniques such as cryptograms to prevent cyberattacks and verify that the data they receive comes from the customer’s mobile device. Fintech companies have used a technique known as AI fuzzing to detect software vulnerabilities such as insecure APIs.
Who are the winners in the embedded security market?
Infineon (Germany), STMicroelectronics (Switzerland), NXP (Netherlands), Qualcomm (US), Thales Group (France), Microchip Technology (US), Samsung (South Korea), Texas Instruments (US), IDEMIA (France), Renesas (Japan) are the players dominating the global embedded security market.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst


- 5.1 INTRODUCTION
-
5.2 MARKET DYNAMICSDRIVERS- Growing IoT applications- Inclusion of payments functionality in wearables- Growing adoption of generative AI in various applications- Digitalization initiatives by governments worldwide- Increase in data breaches and cyberattacks- Rising demand for robust security solutions for electric and hybrid vehicles- Need for more secure crypto-based transactionsRESTRAINTS- Non-compliance with government regulations due to lack of auditing- Susceptibility of embedded systems to cyberthreats and security breaches- Inclination of customers toward renting hardware security modulesOPPORTUNITIES- Integration of embedded security in electric vehicles- Growing importance of IoT security in development of smart cities- Growing adoption of embedded security in healthcare systems- Emergence of 5G and advancements in 5G-enabled embedded devicesCHALLENGES- Lack of safety awareness regarding embedded systems and limited security budget- High energy consumption associated with compact embedded systems- Designing complexities associated with embedded systems- Shortage in supply of semiconductors
- 5.3 VALUE CHAIN ANALYSIS
-
5.4 ECOSYSTEM MAPPING
- 5.5 REVENUE SHIFTS AND NEW REVENUE POCKETS FOR PLAYERS IN EMBEDDED SECURITY MARKET
-
5.6 TECHNOLOGY TRENDSGROWING EMPHASIS ON AUTOMOBILE SECURITYINCREASING CONTACTLESS PAYMENTRISING USE OF WEARABLESINCREASING NUMBER OF IOT DEVICESEMERGENCE OF 5G
- 5.7 PRICING ANALYSIS
-
5.8 PORTER’S FIVE FORCES ANALYSISBARGAINING POWER OF SUPPLIERSBARGAINING POWER OF BUYERSTHREAT OF NEW ENTRANTSTHREAT OF SUBSTITUTESINTENSITY OF COMPETITIVE RIVALRY
- 5.9 CASE STUDY ANALYSIS
-
5.10 TRADE ANALYSISEXPORT SCENARIO FOR HS CODE 8471, BY COUNTRY, 2018–2022IMPORT SCENARIO FOR HS CODE 8471, BY COUNTRY, 2018–2022
-
5.11 PATENT ANALYSISLIST OF MAJOR PATENTS, 2019–2023
-
5.12 KEY STAKEHOLDERS AND BUYING CRITERIAKEY STAKEHOLDERS IN BUYING PROCESSBUYING CRITERIA
- 5.13 KEY CONFERENCES AND EVENTS, 2023–2024
-
5.14 TARIFFS AND REGULATORY LANDSCAPETARIFFSREGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS- North America- Europe- Asia Pacific- RoWSTANDARDSREGULATIONS- Global- North America- Europe- Asia Pacific
- 6.1 INTRODUCTION
-
6.2 AUTHENTICATION & ACCESS MANAGEMENTABILITY TO BLOCK UNAUTHORIZED USERS FROM ACCESSING DEVICES TO GENERATE DEMAND FOR AUTHENTICATION & ACCESS MANAGEMENT
-
6.3 PAYMENTSNEED TO ENSURE SECURE TRANSACTIONS AND PROTECT SENSITIVE CONSUMER DATA TO FUEL DEMAND FOR PAYMENT SECURITY
-
6.4 CONTENT PROTECTIONNEED TO PROTECT SENSITIVE ORGANIZATIONAL DATA FROM FRAUDULENT ACTIVITIES AND PRIVACY BREACHES TO DRIVE MARKET FOR CONTENT PROTECTION
- 7.1 INTRODUCTION
-
7.2 HARDWARESECURE ELEMENTS- Extensive use of secure elements in e-Government applications such as e-passports and smart identity cards to drive marketEMBEDDED SIM- Increasing machine-to-machine connections globally to propel marketTRUSTED PLATFORM MODULES- Increasing number of cybersecurity attacks to fuel market growthHARDWARE SECURITY MODULES- Rising need for information and data security to drive marketHARDWARE TOKENS- Rising demand for secure internet-based transactions to propel market
-
7.3 SOFTWAREFIREWALLS- Need to prevent unauthorized computer and network access to boost adoption of firewallsANTIVIRUS- Potential to address post-firewall intrusions and mitigate advanced threats to contribute to market growthANTISPYWARE- Utilization in monitoring and detecting unauthorized communications to propel marketNETWORK SECURITY- Higher cost-efficiency of implementing security at network level to boost market
-
7.4 SERVICESSYSTEM INTEGRATION SERVICES- Increasing emphasis on enhancing quality of business operations to propel marketSUPPORT AND MAINTENANCE SERVICES- Increased technological complexities to fuel demand for support and maintenance servicesSECURITY CONSULTING- Focus on enhancing effectiveness of business and IT processes to boost demand for security consulting
- 8.1 INTRODUCTION
-
8.2 WEARABLESRISING INTEGRATION OF WEARBLE DEVICES WITH DIGITAL WALLETS TO INCREASE DEMAND FOR EMBEDDED SECURITY
-
8.3 SMARTPHONESSURGE IN MOBILE PAYMENTS TO NECESSITATE ADOPTION OF EMBEDDED SECURITY
-
8.4 AUTOMOTIVEGROWING DEMAND FOR CONNECTED CARS TO BOOST MARKET
-
8.5 SMART IDENTITY CARDSEMERGENCE OF MULTI-APPLICATION SMART CARDS FOR SHARED STORAGE AND INFORMATION PROCESSING TO FOSTER MARKET GROWTH
-
8.6 INDUSTRIALRISING INTEGRATION OF IOT WITH INDUSTRIAL SYSTEMS TO SUPPORT MARKET GROWTH
-
8.7 PAYMENT PROCESSING & CARDSINCREASING E-COMMERCE SALES AND GROWING INTERNET PENETRATION TO SPUR MARKET GROWTH
- 8.8 OTHERS
- 9.1 INTRODUCTION
-
9.2 NORTH AMERICARECESSION IMPACT ON EMBEDDED SECURITY MARKET IN NORTH AMERICAUS- Rising cost burden of data breaches to fuel demand for embedded securityCANADA- Rapid advancements in next-generation digital technologies to foster market growthMEXICO- Rising adoption of wireless connectivity technologies to contribute to market growth
-
9.3 EUROPERECESSION IMPACT ON EMBEDDED SECURITY MARKET IN EUROPEUK- Sharp increase in cyberattacks to boost demand for embedded security systemsGERMANY- Rising government investments in security projects to fuel market growthFRANCE- Increasing initiatives to boost cybersecurity to accelerate market growthREST OF EUROPE
-
9.4 ASIA PACIFICRECESSION IMPACT ON EMBEDDED SECURITY MARKET IN ASIA PACIFICCHINA- Enforcement of data management and security laws to boost market growthSOUTH KOREA- 5G implementation to boost demand for embedded security solutionsJAPAN- Government focus on strengthening cybersecurity capabilities to boost market growthREST OF ASIA PACIFIC
-
9.5 ROWRECESSION IMPACT ON EMBEDDED SECURITY MARKET IN ROWMIDDLE EAST & AFRICA- Rising focus on ensuring cyber resilience in oil & gas sector to boost marketLATIN AMERICA- Increasing investment in transportation and energy infrastructure to propel market

- 10.1 INTRODUCTION
- 10.2 STRATEGIES ADOPTED BY KEY PLAYERS, 2020–2023
- 10.3 REVENUE ANALYSIS OF KEY PLAYERS, 2018–2022
- 10.4 MARKET SHARE ANALYSIS, 2022
-
10.5 KEY COMPANY EVALUATION MATRIX, 2022STARSPERVASIVE PLAYERSEMERGING LEADERSPARTICIPANTS
- 10.6 COMPETITIVE BENCHMARKING OF KEY PLAYERS
-
10.7 SMALL AND MEDIUM-SIZED ENTERPRISES (SMES)/STARTUPS EVALUATION MATRIX, 2022PROGRESSIVE COMPANIESRESPONSIVE COMPANIESDYNAMIC COMPANIESSTARTING BLOCKS
-
10.8 COMPETITIVE SCENARIOS AND TRENDSPRODUCT LAUNCHESDEALS
- 10.9 COMPETITIVE BENCHMARKING OF STARTUPS/SMES
- 11.1 INTRODUCTION
-
11.2 KEY PLAYERSINFINEON TECHNOLOGIES AG- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewSTMICROELECTRONICS- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewNXP SEMICONDUCTORS- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewTEXAS INSTRUMENTS INCORPORATED- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewQUALCOMM TECHNOLOGIES, INC.- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewRENESAS ELECTRONICS CORPORATION- Business overview- Products/Solutions/Services offered- Recent developmentsTHALES- Business overview- Products/Solutions/Services offered- Recent developmentsMICROCHIP TECHNOLOGY INC.- Business overview- Products/Solutions/Services offered- Recent developmentsSAMSUNG- Business overview- Products/Solutions/Services offered- Recent developmentsIDEMIA- Business overview- Products/Solutions/Services offered- Recent developmentsICTK CO., LTD.- Business overview- Products/Solutions/Services offered- Recent developments
-
11.3 OTHER PLAYERSRAMBUS INC.CISCO SYSTEMS, INC.ETASOVD KINEGRAM AGBAE SYSTEMSLANTRONIX, INC.IBMSWIFTMCAFEE, LLCBROADCOMHITEX GMBHANALOG DEVICES, INCADVANTECH CO., LTD.ETA COMPUTERUNSAFE SECURITY
- 12.1 INSIGHTS FROM INDUSTRY EXPERTS
- 12.2 DISCUSSION GUIDE
- 12.3 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
- 12.4 CUSTOMIZATION OPTIONS
- 12.5 RELATED REPORTS
- 12.6 AUTHOR DETAILS
- TABLE 1 EMBEDDED SECURITY MARKET: RISK ASSESSMENT
- TABLE 2 PARTICIPANTS AND THEIR ROLE IN ECOSYSTEM
- TABLE 3 INDICATIVE PRICING ANALYSIS OF EMBEDDED SECURITY HARDWARE COMPONENTS
- TABLE 4 EMBEDDED SECURITY MARKET: PORTER’S FIVE FORCES ANALYSIS, 2022
- TABLE 5 EMBEDDED SECURITY STRENGTHENED DATA PROTECTION OF MEDICAL TESTING EQUIPMENT
- TABLE 6 GARUDA INDONESIA DEVELOPED CORPORATE MOBILITY MANAGEMENT SYSTEM TO WORK ON ELECTRONIC FLIGHT BAGS FOR PILOTS
- TABLE 7 US-BASED FINANCIAL SERVICES COMPANY CREATED PUBLIC KEY INFRASTRUCTURE INVENTORY USING VENAFI PLATFORM
- TABLE 8 KASPERSKY LAB AND BE.SERVICES GMBH DEVELOPED EMBEDDED SECURITY SHIELD TO SAFEGUARD INDUSTRIAL CONTROL SYSTEMS
- TABLE 9 HEALTHCARE ORGANIZATION PROTECTED EMPLOYEE SAFETY AND SECURITY WITH WASHABLE, RFID-EMBEDDED KEYBOARD
- TABLE 10 EXPORT DATA FOR AUTOMATIC DATA PROCESSING MACHINES FOR HS CODE 8471, BY COUNTRY, 2018–2022 (USD BILLION)
- TABLE 11 IMPORT DATA FOR AUTOMATIC DATA PROCESSING MACHINES FOR HS CODE 8471, BY COUNTRY, 2018–2022 (USD BILLION)
- TABLE 12 TOP 10 PATENT OWNERS IN EMBEDDED SECURITY MARKET
- TABLE 13 EMBEDDED SECURITY MARKET: PATENT REGISTRATIONS, 2019–2023
- TABLE 14 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS, BY OFFERING (%)
- TABLE 15 KEY BUYING CRITERIA, BY OFFERING
- TABLE 16 EMBEDDED SECURITY MARKET: LIST OF CONFERENCES AND EVENTS
- TABLE 17 BASE STANDARDS FOR INFORMATION SECURITY
- TABLE 18 EUROPEAN TELECOMMUNICATIONS STANDARDS INSTITUTE: STANDARDS
- TABLE 19 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 20 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 21 AUTHENTICATION & ACCESS MANAGEMENT: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 22 AUTHENTICATION & ACCESS MANAGEMENT: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 23 PAYMENT: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 24 PAYMENT: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 25 CONTENT PROTECTION: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 26 CONTENT PROTECTION: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 27 EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 28 EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 29 HARDWARE: EMBEDDED SECURITY MARKET, BY PRODUCT, 2019–2022 (USD MILLION)
- TABLE 30 HARDWARE: EMBEDDED SECURITY MARKET, BY PRODUCT, 2023–2028 (USD MILLION)
- TABLE 31 HARDWARE: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 32 HARDWARE: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 33 SOFTWARE: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 34 SOFTWARE: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 35 SERVICES: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 36 SERVICES: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 37 EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 38 EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 39 WEARABLES: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 40 WEARABLES: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 41 SMARTPHONES: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 42 SMARTPHONES: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 43 AUTOMOTIVE: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 44 AUTOMOTIVE: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 45 SMART IDENTITY CARDS: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 46 SMART IDENTITY CARDS: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 47 INDUSTRIAL: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 48 INDUSTRIAL: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 49 PAYMENT PROCESSING & CARDS: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 50 PAYMENT PROCESSING & CARDS: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 51 OTHERS: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 52 OTHERS: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 53 EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 54 EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 55 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 56 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 57 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 58 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 59 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 60 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 61 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY COUNTRY, 2019–2022 (USD MILLION)
- TABLE 62 NORTH AMERICA: EMBEDDED SECURITY MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 63 US: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 64 US: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 65 US: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 66 US: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 67 US: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 68 US: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 69 CANADA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 70 CANADA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 71 CANADA: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 72 CANADA: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 73 CANADA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 74 CANADA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 75 MEXICO: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 76 MEXICO: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION
- TABLE 77 MEXICO: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 78 MEXICO: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 79 MEXICO: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 80 MEXICO: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 81 EUROPE: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 82 EUROPE: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 83 EUROPE: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 84 EUROPE: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 85 EUROPE: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 86 EUROPE: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 87 EUROPE: EMBEDDED SECURITY MARKET, BY COUNTRY, 2019–2022 (USD MILLION)
- TABLE 88 EUROPE: EMBEDDED SECURITY MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 89 UK: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 90 UK: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 91 UK: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 92 UK: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 93 UK: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 94 UK: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 95 GERMANY: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 96 GERMANY: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 97 GERMANY: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 98 GERMANY: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 99 GERMANY: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 100 GERMANY: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 101 FRANCE: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 102 FRANCE: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 103 FRANCE: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 104 FRANCE: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 105 FRANCE: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 106 FRANCE: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 107 REST OF EUROPE: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 108 REST OF EUROPE: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 109 REST OF EUROPE: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 110 REST OF EUROPE: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 111 REST OF EUROPE: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 112 REST OF EUROPE: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 113 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 114 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 115 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 116 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 117 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 118 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 119 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY COUNTRY, 2019–2022 (USD MILLION)
- TABLE 120 ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 121 CHINA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 122 CHINA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 123 CHINA: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 124 CHINA: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 125 CHINA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 126 CHINA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 127 SOUTH KOREA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 128 SOUTH KOREA: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 129 SOUTH KOREA: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 130 SOUTH KOREA: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 131 SOUTH KOREA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 132 SOUTH KOREA: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 133 JAPAN: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 134 JAPAN: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 135 JAPAN: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 136 JAPAN: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 137 JAPAN: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 138 JAPAN: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 139 REST OF ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 140 REST OF ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 141 REST OF ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 142 REST OF ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 143 REST OF ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 144 REST OF ASIA PACIFIC: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 145 ROW: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2019–2022 (USD MILLION)
- TABLE 146 ROW: EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- TABLE 147 ROW: EMBEDDED SECURITY MARKET, BY OFFERING, 2019–2022 (USD MILLION)
- TABLE 148 ROW: EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 149 ROW: EMBEDDED SECURITY MARKET, BY APPLICATION, 2019–2022 (USD MILLION)
- TABLE 150 ROW: EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 151 ROW: EMBEDDED SECURITY MARKET, BY REGION, 2019–2022 (USD MILLION)
- TABLE 152 ROW: EMBEDDED SECURITY MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 153 OVERVIEW OF STRATEGIES ADOPTED BY KEY PLAYERS, 2020–2023
- TABLE 154 EMBEDDED SECURITY MARKET: DEGREE OF COMPETITION
- TABLE 155 OVERALL COMPANY FOOTPRINT
- TABLE 156 COMPANY FOOTPRINT, BY APPLICATION
- TABLE 157 COMPANY FOOTPRINT, BY OFFERING
- TABLE 158 COMPANY FOOTPRINT, BY REGION
- TABLE 159 EMBEDDED SECURITY MARKET: PRODUCT LAUNCHES AND DEVELOPMENTS, 2021–2023
- TABLE 160 EMBEDDED SECURITY MARKET: DEALS, 2021–2023
- TABLE 161 EMBEDDED SECURITY MARKET: LIST OF KEY STARTUPS/SMES
- TABLE 162 EMBEDDED SECURITY MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES
- TABLE 163 INFINEON TECHNOLOGIES AG: COMPANY OVERVIEW
- TABLE 164 INFINEON TECHNOLOGIES AG: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 165 INFINEON TECHNOLOGIES AG: PRODUCT LAUNCHES
- TABLE 166 INFINEON TECHNOLOGIES AG: DEALS
- TABLE 167 INFINEON TECHNOLOGIES AG: OTHERS
- TABLE 168 STMICROELECTRONICS: COMPANY OVERVIEW
- TABLE 169 STMICROELECTRONICS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 170 STMICROELECTRONICS: PRODUCT LAUNCHES
- TABLE 171 STMICROELECTRONICS: DEALS
- TABLE 172 NXP SEMICONDUCTORS: COMPANY OVERVIEW
- TABLE 173 NXP SEMICONDUCTORS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 174 NXP SEMICONDUCTORS: PRODUCT LAUNCHES
- TABLE 175 NXP SEMICONDUCTORS: DEALS
- TABLE 176 TEXAS INSTRUMENTS INCORPORATED: COMPANY OVERVIEW
- TABLE 177 TEXAS INSTRUMENTS INCORPORATED: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 178 TEXAS INSTRUMENTS INCORPORATED: PRODUCT LAUNCHES
- TABLE 179 TEXAS INSTRUMENTS INCORPORATED: DEALS
- TABLE 180 TEXAS INSTRUMENTS INCORPORATED: OTHERS
- TABLE 181 QUALCOMM TECHNOLOGIES, INC.: COMPANY OVERVIEW
- TABLE 182 QUALCOMM TECHNOLOGIES, INC.: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 183 QUALCOMM TECHNOLOGIES, INC.: PRODUCT LAUNCHES
- TABLE 184 QUALCOMM TECHNOLOGIES, INC.: DEALS
- TABLE 185 RENESAS ELECTRONICS CORPORATION: COMPANY OVERVIEW
- TABLE 186 RENESAS ELECTRONICS CORPORATION: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 187 RENESAS ELECTRONICS CORPORATION: PRODUCT LAUNCHES
- TABLE 188 RENESAS ELECTRONICS CORPORATION: DEALS
- TABLE 189 RENESAS ELECTRONICS CORPORATION: OTHERS
- TABLE 190 THALES: COMPANY OVERVIEW
- TABLE 191 THALES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 192 THALES: PRODUCT LAUNCHES
- TABLE 193 THALES: DEALS
- TABLE 194 MICROCHIP TECHNOLOGY INC.: COMPANY OVERVIEW
- TABLE 195 MICROCHIP TECHNOLOGY INC.: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 196 MICROCHIP TECHNOLOGY INC.: PRODUCT LAUNCHES
- TABLE 197 MICROCHIP TECHNOLOGY INC.: OTHERS
- TABLE 198 SAMSUNG: COMPANY OVERVIEW
- TABLE 199 SAMSUNG: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 200 SAMSUNG: PRODUCT LAUNCHES
- TABLE 201 IDEMIA: COMPANY OVERVIEW
- TABLE 202 IDEMIA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 203 IDEMIA: PRODUCT LAUNCHES
- TABLE 204 IDEMIA: DEALS
- TABLE 205 ICTK CO., LTD.: COMPANY OVERVIEW
- TABLE 206 ICTK CO., LTD.: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 207 ICTK CO., LTD.: DEALS
- FIGURE 1 EMBEDDED SECURITY MARKET SEGMENTATION
- FIGURE 2 EMBEDDED SECURITY MARKET: RESEARCH DESIGN
- FIGURE 3 EMBEDDED SECURITY MARKET: PROCESS FLOW OF MARKET SIZE ESTIMATION
- FIGURE 4 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 1 (SUPPLY SIDE, BY OFFERING)
- FIGURE 5 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 2 (SUPPLY SIDE, BY KEY PLAYERS)
- FIGURE 6 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 3 (DEMAND SIDE—BOTTOM-UP ANALYSIS, BY APPLICATION)
- FIGURE 7 MARKET SIZE ESTIMATION METHODOLOGY: BOTTOM-UP APPROACH
- FIGURE 8 MARKET SIZE ESTIMATION METHODOLOGY: TOP-DOWN APPROACH
- FIGURE 9 DATA TRIANGULATION
- FIGURE 10 EMBEDDED SECURITY MARKET: RESEARCH ASSUMPTIONS
- FIGURE 11 EMBEDDED SECURITY MARKET: LIMITATIONS
- FIGURE 12 EMBEDDED SECURITY MARKET, 2019–2028 (USD MILLION)
- FIGURE 13 PAYMENTS SEGMENT TO ACCOUNT FOR LARGEST SHARE OF EMBEDDED SECURITY MARKET IN 2028
- FIGURE 14 SMART IDENTITY CARDS SEGMENT TO LEAD EMBEDDED SECURITY MARKET FROM 2023 TO 2028
- FIGURE 15 SERVICES SEGMENT TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 16 ASIA PACIFIC TO BE FASTEST-GROWING EMBEDDED SECURITY MARKET DURING FORECAST PERIOD
- FIGURE 17 INCREASED NEED FOR CYBERSECURITY DUE TO GROWING IOT APPLICATIONS TO DRIVE MARKET DURING FORECAST PERIOD
- FIGURE 18 SOFTWARE SEGMENT TO ACCOUNT FOR LARGEST SHARE OF EMBEDDED SECURITY MARKET IN 2028
- FIGURE 19 PAYMENTS SEGMENT TO HOLD LARGEST SHARE OF EMBEDDED SECURITY MARKET IN 2028
- FIGURE 20 SMART IDENTITY CARDS SEGMENT TO DOMINATE MARKET DURING FORECAST PERIOD
- FIGURE 21 ASIA PACIFIC TO LEAD EMBEDDED SECURITY MARKET DURING FORECAST PERIOD
- FIGURE 22 EMBEDDED SECURITY MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES AND CHALLENGES
- FIGURE 23 EMBEDDED SECURITY MARKET: VALUE CHAIN ANALYSIS
- FIGURE 24 PARTICIPANTS IN EMBEDDED SECURITY ECOSYSTEM
- FIGURE 25 TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- FIGURE 26 EMBEDDED SECURITY MARKET: PORTER’S FIVE FORCES ANALYSIS
- FIGURE 27 EMBEDDED SECURITY MARKET: IMPACT ANALYSIS OF PORTER’S FIVE FORCES
- FIGURE 28 EXPORT SCENARIO FOR AUTOMATIC DATA PROCESSING MACHINES FOR HS CODE 8471, BY COUNTRY, 2018–2022 (USD BILLION)
- FIGURE 29 IMPORT SCENARIO FOR AUTOMATIC DATA PROCESSING MACHINES FOR HS CODE 8471, BY COUNTRY, 2018–2022 (USD BILLION)
- FIGURE 30 NUMBER OF PATENTS GRANTED PER YEAR, 2013–2022
- FIGURE 31 TOP 10 COMPANIES WITH HIGHEST NUMBER OF PATENT APPLICATIONS IN LAST 10 YEARS
- FIGURE 32 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS, BY OFFERING
- FIGURE 33 KEY BUYING CRITERIA FOR OFFERINGS
- FIGURE 34 EMBEDDED SECURITY MARKET, BY SECURITY TYPE, 2023–2028 (USD MILLION)
- FIGURE 35 EMBEDDED SECURITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- FIGURE 36 EMBEDDED SECURITY MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- FIGURE 37 EMBEDDED SECURITY MARKET, BY COUNTRY
- FIGURE 38 NORTH AMERICA: EMBEDDED SECURITY MARKET SNAPSHOT
- FIGURE 39 NORTH AMERICA: RECESSION IMPACT ANALYSIS, 2019–2028
- FIGURE 40 EUROPE: EMBEDDED SECURITY MARKET SNAPSHOT
- FIGURE 41 EUROPE: RECESSION IMPACT ANALYSIS, 2019–2028
- FIGURE 42 ASIA PACIFIC: EMBEDDED SECURITY MARKET SNAPSHOT
- FIGURE 43 ASIA PACIFIC: RECESSION IMPACT ANALYSIS, 2019–2028
- FIGURE 44 ROW: RECESSION IMPACT ANALYSIS, 2019–2028
- FIGURE 45 5-YEAR REVENUE ANALYSIS OF KEY PLAYERS IN EMBEDDED SECURITY MARKET
- FIGURE 46 MARKET SHARE ANALYSIS, 2022
- FIGURE 47 EMBEDDED SECURITY MARKET: KEY COMPANY EVALUATION MATRIX, 2022
- FIGURE 48 EMBEDDED SECURITY MARKET: SMES/STARTUPS EVALUATION MATRIX, 2022
- FIGURE 49 INFINEON TECHNOLOGIES AG: COMPANY SNAPSHOT
- FIGURE 50 STMICROELECTRONICS: COMPANY SNAPSHOT
- FIGURE 51 NXP SEMICONDUCTORS: COMPANY SNAPSHOT
- FIGURE 52 TEXAS INSTRUMENTS INCORPORATED: COMPANY SNAPSHOT
- FIGURE 53 QUALCOMM TECHNOLOGIES, INC.: COMPANY SNAPSHOT
- FIGURE 54 RENESAS ELECTRONICS CORPORATION: COMPANY SNAPSHOT
- FIGURE 55 THALES GROUP: COMPANY SNAPSHOT
- FIGURE 56 MICROCHIP TECHNOLOGY INC.: COMPANY SNAPSHOT
- FIGURE 57 SAMSUNG: COMPANY SNAPSHOT
The study involved four major activities in estimating the size of the embedded security market. Exhaustive secondary research has been done to collect information on the market, peer, and parent markets. Validation of these findings, assumptions, and sizing with industry experts across the value chain through primary research has been the next step. Both top-down and bottom-up approaches have been employed to estimate the global market size. After that, market breakdown and data triangulation have been used to estimate the market sizes of segments and subsegments.
Secondary Research
The secondary sources referred to for this research study includes corporate filings (such as annual reports, press releases, investor presentations, and financial statements); trade, business, and professional associations (such as Consumer Technology Association (CTA), Integrated Systems Europe, the Organisation Internationale des Constructeurs d'Automobiles (OICA), the Society for Information Display (SID), and Touch Taiwan); white papers, AR- and VR-related marketing journals, certified publications, and articles by recognized authors; gold and silver standard websites; directories; and databases.
Secondary research has been conducted to obtain key information about the supply chain of the embedded security industry, the monetary chain of the market, the total pool of key players, and market segmentation according to the industry trends to the bottommost level, regional markets, and key developments from both market- and technology-oriented perspectives. The secondary data has been collected and analyzed to determine the overall market size, further validated by primary research.
Primary Research
Extensive primary research has been conducted after acquiring an understanding of the embedded security market scenario through secondary research. Several primary interviews have been conducted with market experts from both the demand- (consumers, industries) and supply-side (embedded security device manufacturers) players across four major regions, namely, North America, Europe, Asia Pacific, and the Rest of the World (the Middle East & Africa). Approximately 70% and 30% of primary interviews have been conducted from the supply and demand side. Primary data has been collected through questionnaires, emails, and telephonic interviews. In the canvassing of primaries, various departments within organizations, such as sales, operations, and administration, were covered to provide a holistic viewpoint in our report.
After interacting with industry experts, brief sessions were conducted with highly experienced independent consultants to reinforce the findings from our primaries. This and the in-house subject matter experts’ opinions have led us to the findings described in the remainder of this report.
To know about the assumptions considered for the study, download the pdf brochure
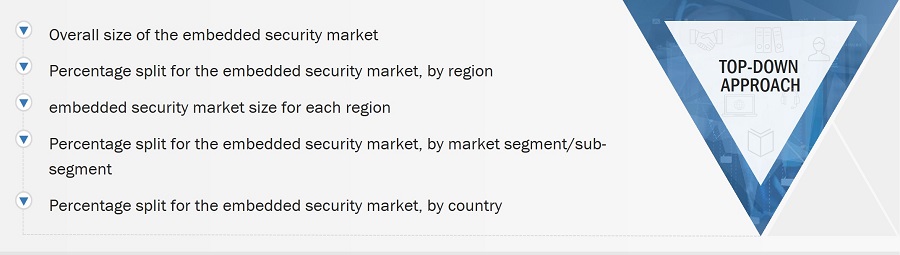
Market Size Estimation
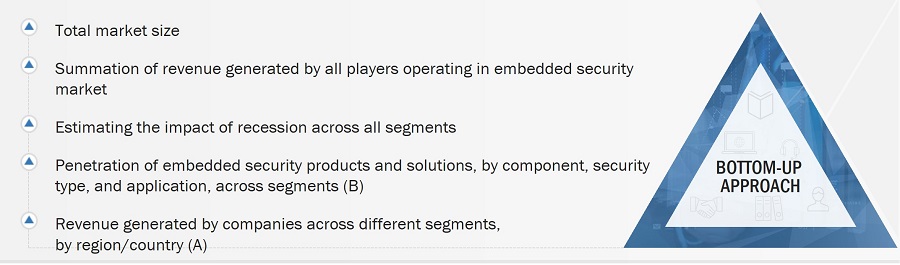
Both top-down and bottom-up approaches have been used to estimate and validate the total size of the embedded security market. These methods have also been extensively used to estimate the sizes of various market subsegments. The research methodology used to estimate the market sizes includes the following:
- Identifying various applications that use or are expected to use the embedded security market.
- Analyzing historical and current data pertaining to the size of the embedded security market, in terms of volume, for each application using their production statistics
- Analyzing the average selling prices of embedded security based on different technologies
- Studying various paid and unpaid sources, such as annual reports, press releases, white papers, and databases
- Identifying leading manufacturers of embedded security, studying their portfolios, and understanding features of their products and their underlying technologies, as well as the types of embedded security offered
- Tracking ongoing and identifying upcoming developments in the market through investments, research and development activities, product launches, expansions, and partnerships, and forecasting the market size based on these developments and other critical parameters
- Carrying out multiple discussions with key opinion leaders to understand the technologies used in embedded security, raw materials used to develop them, and products wherein they are deployed, and analyze the break-up of the scope of work carried out by key manufacturers of embedded security solutions providers
- Verifying and crosschecking estimates at every level through discussions with key opinion leaders, such as CXOs, directors, and operations managers, and finally with domain experts at MarketsandMarkets
Market Size Estimation Methodology-Bottom-up Approach
Market Size Estimation Methodology-Top-Down Approach
Data Triangulation
The market has been split into several segments and subsegments after arriving at the overall market size—using the market size estimation processes explained above. Data triangulation and market breakdown procedures have been employed to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, wherever applicable. The data has been triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
An embedded security system refers to specialized security measures and technologies incorporated directly into electronic devices, software, or hardware components. These measures are designed to protect the integrity, confidentiality, and availability of the device or system and the data it processes and stores. Embedded security systems are commonly used in various applications, such as Internet of Things (IoT) devices, industrial control systems, automotive systems, and more. They help safeguard these systems from threats like unauthorized access, data breaches, malware attacks, and tampering. These security features are deeply integrated into the device’s architecture and operation, making it more resistant to vulnerabilities and potential exploits. Examples of embedded security features include hardware-based encryption, secure boot processes, trusted platform modules, authentication mechanisms (like biometrics or secure keys), secure communication protocols, and intrusion detection systems. The goal is to create a layered defence that protects the device and its data throughout its lifecycle.
Key Stakeholders
- Product designers and fabricators
- Application providers
- Business providers
- Professional services/solutions providers
- Original Equipment Manufacturers
- Third-Party Service Providers
- Communication Network Providers
- Forums, Alliances, and Associations
- End-User Industries
- Research organizations
- Technology standard organizations, forums, alliances, and associations
- Technology investors
The main objectives of this study are as follows:
- To define, describe, segment, and forecast the embedded security market, in terms of value, based on offering, security type, application, and region
- To forecast the embedded security market, in terms of volume, based on application
- To forecast the size of the market and its segments with respect to four main regions, namely, North America, Europe, Asia Pacific (APAC), and the Rest of the World (RoW), along with their key countries
- To strategically analyze micromarkets1 with respect to individual growth trends, prospects, and contributions to the total market
- To provide detailed information regarding the key factors influencing market growth, such as drivers, restraints, opportunities, and challenges
- To provide a detailed analysis of the embedded security supply chain
- To analyze the opportunities in the market for stakeholders and provide a detailed competitive landscape of the market leaders
- To analyze the associated use cases in the embedded security business and their impact on the business strategies adopted by key players
- To analyze the opportunities in the market for stakeholders by identifying the high-growth segments of the global embedded security market
- To forecast and compare the market size of pre-recession with that of the post-recession at global, and regional levels
- To strategically profile the key players and comprehensively analyze their market ranking and core competencies2
- To analyze key growth strategies such as expansions, contracts, joint ventures, acquisitions, product launches and developments, and research and development activities undertaken by players operating in the embedded security market
Available Customizations
MarketsandMarkets offers the following customizations for this market report:
- Further breakdown of the market in different regions to the country-level
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...










Growth opportunities and latent adjacency in Embedded Security Market