Public Key Infrastructure (PKI) Market by Component (HSM, Solutions, and Services), Deployment Mode (On-premises and Cloud), Organization Size, Vertical (BFSI, Healthcare, IT and Telecom), Application Region - Global Forecast to 2028
Public Key Infrastructure (PKI) Market Summary
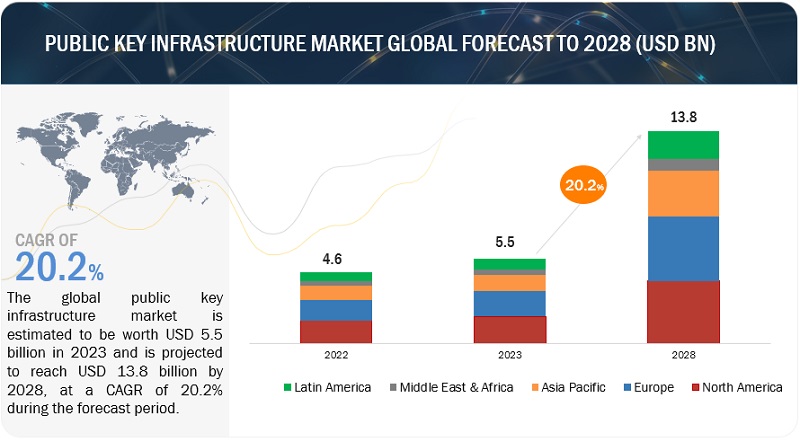
The global Public Key Infrastructure (PKI) Market size is projected to grow from USD 5.5 billion in 2023 to USD 13.8 billion by 2028 at a CAGR of 20.2% during the forecast period. The market is driven by the increasing demand for robust digital security amid rising cyber threats, stringent data privacy regulations such as GDPR and HIPAA, and the expanding digital landscape including remote work and the Internet of Things (IoT). PKI solutions offer encryption, authentication, and digital signature capabilities to secure sensitive data, protect digital identities, and ensure integrity in digital transactions, strengthening its role in cybersecurity and digital trust.
Key Trends & Insights
- Driver: Growing demand for strong digital security and compliance with data privacy regulations is fueling the adoption of PKI solutions.
- Restraint: Complexity in implementation, integration challenges, and scalability concerns may limit adoption across industries.
- Opportunity: Securing the rapidly expanding IoT ecosystem presents a significant growth opportunity for PKI adoption.
- Challenge: Managing a large volume of digital certificates while maintaining robust security standards is a key operational challenge.
- By Offering: Services segment is expected to register the highest growth rate, as organizations increasingly rely on expert support for implementation and management.
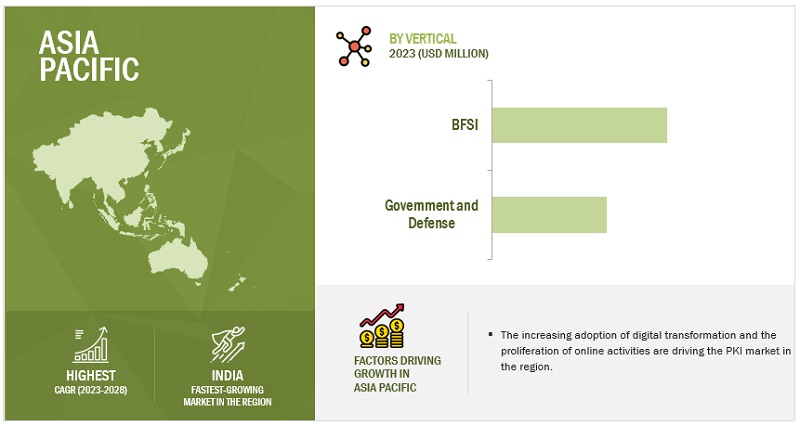
- By Vertical: Banking, Financial Services, and Insurance (BFSI) vertical holds the largest market size due to high regulatory scrutiny and sensitive data handling.
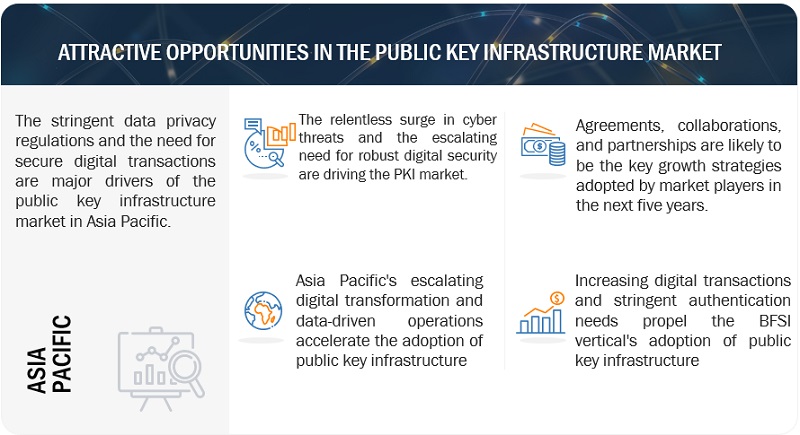
- By Region: Asia Pacific is anticipated to witness the highest growth rate due to increasing digital transactions, e-commerce adoption, and rising cybersecurity awareness.
Public Key Infrastructure Market Size & Forecast
- 2022 Market Size: USD 4.6 Billion
- 2023 Market Size: USD 5.5 Billion
- 2028 Projected Market Size: USD 13.8 Billion
- CAGR (2023–2028): 20.2%
- Largest Market in 2022: Banking, Financial Services, and Insurance (BFSI) vertical
To know about the assumptions considered for the study, Request for Free Sample Report
To know about the assumptions considered for the study, download the pdf brochure
Public Key Infrastructure Market Trends
Driver: The PKI market is propelled by the critical demand for strong digital security amid increasing cyber threats and evolving data privacy regulations
The Public key infrastructure market is escalating with the need for robust digital security in an increasingly interconnected world. The relentless surge in cyberattacks, data breaches, and digital fraud underscores the urgency of securing sensitive information and digital identities. PKI, with its encryption, authentication, and digital signature capabilities, offers a trusted framework to counter these evolving threats. Stringent data privacy regulations and mandates regarding secure data handling and encryption compelling organizations to adopt PKI solutions. As businesses embark on digital transformation journeys, the demand for PKI to secure digital assets, facilitate secure access, and ensure the integrity of digital transactions continues to soar. PKI's role as a bedrock of cybersecurity and digital trust firmly positions it as the linchpin driving the market's growth.
Restraint: Complexity in implementation, integration challenges, and scalability concerns pose significant restraints for the PKI market, potentially limiting its adoption across industries
A significant restraint for the Public key infrastructure market is the complexity associated with its implementation and management. PKI involves intricate cryptographic processes, digital certificate issuance, and key management, which can be challenging for organizations to navigate, especially those with limited expertise or resources. Integrating PKI seamlessly into existing systems and applications can be cumbersome, potentially causing disruptions. Scalability is another concern, as some organizations may find it difficult to expand PKI infrastructure to accommodate growing needs. These complexities and potential integration hurdles can deter some businesses from adopting PKI, limiting its widespread adoption across industries.
Opportunity: Securing the rapidly growing Internet of Things (IoT) ecosystem to drive adoption across industries.
An immense opportunity for the Public key infrastructure market lies in its potential to address the growing need for securing the Internet of Things ecosystem. As IoT devices proliferate across industries, robust authentication, encryption, and secure communication become paramount. PKI's ability to provide trust and security in IoT networks positions it as a key enabler for IoT adoption, offering a reliable framework for ensuring the integrity of data transmitted between devices, safeguarding critical infrastructure, and protecting against emerging cyber threats. As organizations seek to harness the full potential of IoT while mitigating security risks, PKI emerges as a pivotal solution with the potential to drive its adoption in the expanding IoT landscape.
Challenge: Managing a large volume of digital certificates while upholding security standards presents a notable operational challenge for the PKI market as adoption expands across industries and IoT ecosystems.
A notable challenge for the Public key infrastructure market is the management of digital certificates at scale. As PKI adoption expands across industries and IoT ecosystems, the sheer volume of certificates to issue, renew, and revoke can become overwhelming. This challenge is exacerbated by the need for stringent security protocols and adherence to regulatory standards, necessitating meticulous certificate management practices. Organizations must grapple with certificate lifecycle management, which includes ensuring timely renewals, addressing potential vulnerabilities, managing certificate revocation lists, or utilizing online certificate status protocol services. The complexity of maintaining a vast number of certificates while maintaining robust security standards can pose a significant operational challenge for PKI adopters.
Public Key Infrastructure Market Ecosystem
The major players in the public key infrastructure market are Thales, Entrust Datacard, DigiCert, ManageEngine, Microsoft, and so on. The public key infrastructure market is driven by prominent companies that have established themselves as leaders in the industry. These companies are well-established, financially stable, and have a proven track record of providing innovative solutions and services in public key infrastructure. Their diverse product portfolio spans infrastructure, solutions, applications, and services, enabling them to cater to the market’s evolving needs. With state-of-the-art technologies and extensive capabilities, these companies are at the forefront of advancing public key infrastructure technology.
By offering, the services segment to register the highest growth rate during the forecast period
The projected highest growth rate within the services segment of the PKI market underscores the critical role that expert services play in ensuring the successful deployment and management of PKI solutions. In today’s digital landscape, PKI has become indispensable for securing data transmission, protecting sensitive information, and establishing trust in online interactions. The complexity associated with PKI implementation, management, and optimization can be daunting for many organizations, especially those lacking in-house expertise. This complexity encompasses cryptographic key management, digital certificate issuance, secure communication setup, and the need to stay vigilant against ever-evolving cybersecurity threats. PKI service providers fill this crucial gap by offering a wide range of services tailored to meet the specific needs of organizations. These services encompass consultation, implementation support, managed PKI services, and ongoing support. They bring specialized knowledge and experience, helping organizations navigate the intricacies of PKI effectively. Service providers can customize PKI solutions to align with an organization’s unique infrastructure, ensuring seamless integration with existing systems and applications.
Based on vertical, the Banking, Financial Services, and Insurance industry vertical accounts for the largest market size in the PKI market
The dominance of the Banking, Financial Services, and Insurance industry verticals in the PKI market reflects the sector’s unyielding commitment to fortify digital security and establish trust in a landscape characterized by immense data sensitivity and regulatory scrutiny. Within the BFSI sector, safeguarding highly confidential customer data, securing financial transactions, and preserving the integrity of critical information are not just priorities; they are prerequisites. In this context, PKI’s suite of security solutions, encompassing encryption, authentication, and digital signatures, plays an indispensable role. The BFSI industry is under the constant watch of stringent regulatory bodies, with compliance standards such as the Payment Card Industry Data Security Standard and the Dodd-Frank Wall Street Reform and Consumer Protection Act. These regulations necessitate the highest levels of data protection and privacy. PKI provides a proven framework to meet these requirements, enabling organizations to encrypt sensitive data, verify the identity of users and entities, and ensure the integrity of financial transactions.
Asia Pacific to register the highest growth rate during the forecast period.
The remarkable growth anticipated in the PKI market within the Asia Pacific region during the forecast period underscores a significant shift in the digital security landscape. As businesses, governments, and individuals increasingly embrace digital technologies, the demand for robust security solutions has surged. PKI, with its capabilities encompassing encryption, authentication, and digital signatures, plays a pivotal role in addressing these security needs. One of the driving forces behind this growth is the escalating volume of digital transactions, data sharing, and online activities in the Asia Pacific region. With a vast and growing population of internet users, coupled with a thriving e-commerce ecosystem, the region has become a hub for online interactions. This surge in digital activities amplifies the need for secure online payments, data protection, and establishing trust in digital identities.
Key Market Players:
The major players in the public key infrastructure market are Thales (France), Entrust Datacard (US), DigiCert (US), ManageEngine (US), Microsoft (US), HID Global (US), Google (US), AWS (US), AppViewX (US), Venafi (US), Nexus (Sweden), Sectigo (US), Futurex (US), GlobalSign (US), WISeKey (Switzerland), Cygnacom Solutions (US), Keyfactor (US), SECARDEO GmbH (Germany), Blue Ridge Networks (US), Softlock (Egypt), SSL.com (US), LAWtrust (South Africa), SecureMetric (Malaysia), Stormshield (France), and Enigma Information Security Systems (US).
Scope of the Report
|
Report Metrics |
Details |
|
Market size available for years |
2017-2028 |
|
Base year considered |
2022 |
|
Forecast period |
2023-2028 |
|
Forecast units |
Value (USD) Million/Billion |
|
Segments Covered |
By offering, deployment mode, organization size, application, and vertical |
|
Region covered |
North America, Europe, Asia Pacific, Middle East and Africa, and Latin America |
|
Companies covered |
Thales (France), Entrust Datacard (US), DigiCert (US), ManageEngine (US), Microsoft (US), HID Global (US), Google (US), AWS (US), AppViewX (US), Venafi (US), Nexus (Sweden), Sectigo (US), Futurex (US), GlobalSign (US), WISeKey (Switzerland), Cygnacom Solutions (US), Keyfactor (US), SECARDEO GmbH (Germany), Blue Ridge Networks (US), Softlock (Egypt), SSL.com (US), LAWtrust (South Africa), SecureMetric (Malaysia), Stormshield (France), and Enigma Information Security Systems (US) |
This research report categorizes the public key infrastructure market to forecast revenues and analyze trends in each of the following submarkets:
Based on offering:
- Hardware Security Modules (HSM)
- Solutions
- Services
Based on services:
- Professional
- Managed
Based on deployment mode:
- Cloud
- On-Premises
Based on organization size:
- Large Enterprises
- SMEs
Based on application:
- Web browsing security
- Email security
- Secure communication
- Authentication
Based on the vertical:
- BFSI
- Government and Defense
- IT and Telecom
- Retail
- Healthcare
- Manufacturing
- Other verticals
Based on the region:
-
North America
- US
- Canada
-
Europe
- UK
- Germany
- France
- Rest of Europe
-
Asia Pacific
- China
- Japan
- India
- Rest of Asia Pacific
-
Middle East and Africa
- United Arab Emirates
- South Africa
-
Latin America
- Brazil
- Mexico
- Rest of Latin America
Recent Developments
- April 2023 - Thales adds new phishing-resistant hybrid authenticators to its Passwordless Authentication for Microsoft Azure Active Directory Customers offering.
- April 2023 - Entrust Introduces Zero Trust Ready Solutions for Multi-Cloud Key Compliance, Next-Generation HSM, and Passwordless Authentication
- January 2023 - A comprehensive digital trust system that combines public key infrastructure (PKI), certificate management, and certificate authority (CA) services was introduced by DigiCert. A significant product launch is Trust Lifecycle Manager, which is currently accessible as a component of the DigiCert ONE platform.
- February 2022 - To increase public trust in the cloud, Thales announced the continuation of its cooperation with Google Cloud. Organizations can confidently use the Google Cloud Platform (GCP) if the connection is stronger. The technique known as ubiquitous data encryption, which combines Thales' Cypher Trust Cloud Key Manager and Google Cloud's Confidential Computing, is activated. Customers can create and manage the encryption keys for data sent to Google Confidential Cloud Computing using the Thales Cypher Trust Data Security Gateway.
Frequently Asked Questions (FAQ):
What is a public key infrastructure?
Public Key Infrastructure constitutes a comprehensive framework for securing digital communication, authentication, and data integrity in the digital realm. At its core, PKI operates through issuing and managing digital certificates, which serve as digital IDs binding a user or entity's identity to a public key. These certificates are signed by trusted entities known as Certificate Authorities (CAs), instilling trust in the authenticity of the associated entity. Central to PKI are public and private key pairs, where the public key is openly shared for encryption and verification, while the private key remains confidential, enabling decryption and digital signatures. PKI plays an instrumental role in securing online transactions, ensuring data privacy, and establishing trust in digital interactions across various domains, including secure web browsing, email security, secure communication, and authentication.
What is the market size of the public key infrastructure market?
The global public key infrastructure market is estimated to be worth USD 5.5 billion in 2023 and is projected to reach USD 13.8 billion by 2028, at a CAGR of 20.2% during the forecast period.
What are the major drivers in the public key infrastructure market?
The Public Key Infrastructure market is driven by various factors, such as escalating cybersecurity threats that organizations face. As cyberattacks grow in frequency and sophistication, businesses and governments recognize the urgency of implementing robust security measures. PKI, with its suite of encryption, authentication, and digital signature capabilities, offers a trusted framework to counter these evolving threats and protect sensitive data. Stringent data privacy regulations and compliance requirements represent another driving force. Regulations mandate secure data handling and encryption to protect individuals' privacy rights and sensitive information. PKI solutions help organizations meet these compliance requirements effectively. The ongoing digital transformation, marked by the proliferation of online transactions, remote work, and IoT devices, amplifies the demand for PKI. The technology ensures the security and integrity of digital interactions, making it essential in today's interconnected world.
Who are the major players operating in the public key infrastructure market?
The major players in the public key infrastructure market are Thales (France), Entrust Datacard (US), DigiCert (US), ManageEngine (US), Microsoft (US), HID Global (US), Google (US), AWS (US), AppViewX (US), Venafi (US), Nexus (Sweden), Sectigo (US), Futurex (US), GlobalSign (US), WISeKey (Switzerland), Cygnacom Solutions (US), Keyfactor (US), SECARDEO GmbH (Germany), Blue Ridge Networks (US), Softlock (Egypt), SSL.com (US), LAWtrust (South Africa), SecureMetric (Malaysia), Stormshield (France), and Enigma Information Security Systems (US).
Which key technology trends prevail in the public key infrastructure market?
Several notable technology trends are currently shaping the Public Key Infrastructure market. The adoption of cloud-based PKI solutions is gaining traction. This approach allows organizations to leverage the cloud’s scalability and flexibility, simplifying PKI management while reducing operational costs. Integration of PKI with blockchain technology is an emerging trend. Blockchain’s inherent security and transparency attributes complement PKI by providing an immutable ledger for certificate issuance and management, further enhancing the trust and integrity of digital transactions. The move towards decentralized identities, often referred to as Self-Sovereign Identity, is reshaping the way PKI is applied. SSI allows individuals to control their digital identities, reducing reliance on centralized identity providers and enhancing privacy. The increasing adoption of zero-trust security models drives the need for continuous authentication and dynamic trust assessment, aligning with PKI's role in enhancing user and device authentication.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst


- 5.1 INTRODUCTION
-
5.2 MARKET DYNAMICSDRIVERS- Stringent regulatory standards and data privacy compliances- Rising concerns pertaining to loss of critical data- Increase in penetration of online channels- Rise in malware and file-based attacksRESTRAINTS- Technical complexities involved- Running private certificate authorities or using self-signed certificatesOPPORTUNITIES- Exponential increase in adoption of IoT across industry verticals- Proliferation of cloud-based and virtualization technologiesCHALLENGES- Lack of awareness among organizations about importance of PKI certificates- Limited expertise and resources for deployment of PKI- Entrenched traditional business practices
-
5.3 INDUSTRY TRENDSPKI MARKET EVOLUTIONECOSYSTEM ANALYSISTECHNOLOGY ROADMAP- Short-term roadmap (2023–2025)- Mid-term roadmap (2026–2028)- Long-term roadmap (2029–2030)CASE STUDY ANALYSIS- Finance in Motion collaborated with GlobalSign to supplement Keytalk’s existing certificate and management services- University of Colorado chose Sectigo to manage its digital certificates- Emudhra helped Mauritius government implement National Public Key InfrastructureVALUE CHAIN ANALYSISREGULATORY LANDSCAPE- Regulatory bodies, government agencies, and other organizations- General Data Protection Regulation- Personal Information Protection and Electronic Documents Act (PIPEDA)- Cloud Security Alliance Security Trust Assurance and Risk (STAR)- SOC 2- Digital Millennium Copyright Act (DMCA)- Anti-Cybersquatting Consumer Protection Act (ACPA)PATENT ANALYSISKEY CONFERENCES & EVENTS, 2023–2024AVERAGE SELLING PRICE ANALYSISPORTER’S FIVE FORCES ANALYSIS- Threat of new entrants- Threat of substitutes- Bargaining power of buyers- Bargaining power of suppliers- Intensity of competitive rivalryKEY STAKEHOLDERS & BUYING CRITERIA- Key Stakeholders in buying criteria- Buying criteriaTECHNOLOGY ANALYSIS- Public key infrastructure and Internet of things- Public key infrastructure and cloud- Public key infrastructure and blockchainCURRENT AND EMERGING BUSINESS MODELS- Managed PKI- Federated PKI- Cloud-based PKI- On-premises PKIBEST PRACTICES IN PKI MARKET- Security by design- Secure key management- Certificate lifecycle management- Monitoring and incident response- Redundancy and disaster recoveryTRENDS AND DISRUPTIONS IMPACTING CUSTOMERS- Quantum computing threats- Blockchain and decentralization- IoT and device identity- Cloud-based PKI- Regulatory compliance- Zero-trust architecture- Remote work and secure access- AI and automation- Open-source PKI solutionsHS CODES
- 6.1 INTRODUCTION
-
6.2 HARDWARE SECURITY MODULESINCREASING DEMAND FOR SECURE HARDWARE-BACKED SOLUTIONS TO DRIVE GROWTH OF HARDWARE SECURITY MODELSHARDWARE SECURITY MODULES: MARKET DRIVERS
-
6.3 SOLUTIONSGROWING NEED FOR COMPREHENSIVE SECURITY SOLUTIONS IN EVOLVING DIGITAL LANDSCAPE TO DRIVE SOLUTIONS SEGMENTSOLUTIONS: MARKET DRIVERS
-
6.4 SERVICESINCREASING COMPLEXITY OF PKI IMPLEMENTATION AND NEED FOR EXPERT GUIDANCE AND SUPPORT TO DRIVE SERVICES SEGMENTSERVICES: MARKET DRIVERSPROFESSIONAL SERVICESMANAGED SERVICES
- 7.1 INTRODUCTION
-
7.2 ON-PREMISESDEMAND FOR DATA CONTROL, COMPLIANCE, AND SECURITY IN INDUSTRIES TO DRIVE GROWTH OF ON-PREMISES SEGMENTON-PREMISES: MARKET DRIVERS
-
7.3 CLOUDNEED FOR SCALABILITY, COST-EFFICIENCY, AND FLEXIBILITY IN MODERN IT INFRASTRUCTURE TO DRIVE GROWTH OF CLOUD SEGMENTCLOUD: MARKET DRIVERS
- 8.1 INTRODUCTION
-
8.2 LARGE ENTERPRISESGROWING COMPLEXITY OF CYBERSECURITY THREATS AND REGULATORY COMPLIANCE REQUIREMENTS TO DRIVE LARGE ENTERPRISES TO ADOPT ROBUST PKI SOLUTIONSLARGE ENTERPRISES: MARKET DRIVERS
-
8.3 SMALL AND MEDIUM-SIZED ENTERPRISESINCREASING IMPORTANCE OF DIGITAL SECURITY AND NEED FOR COST-EFFECTIVE SOLUTIONS TO DRIVE SMES TO EMBRACE PKISMALL AND MEDIUM-SIZED ENTERPRISES: MARKET DRIVERS
- 9.1 INTRODUCTION
-
9.2 WEB BROWSING SECURITYESCALATING FREQUENCY OF WEB-BASED THREATS AND IMPERATIVE OF SAFEGUARDING ONLINE INTERACTIONS TO DRIVE GROWTHWEB BROWSING SECURITY: MARKET DRIVERS
-
9.3 EMAIL SECURITYRISING VOLUME OF EMAIL-BASED CYBER THREATS AND CRITICAL NEED FOR SECURING CONFIDENTIAL COMMUNICATIONS TO DRIVE SEGMENTEMAIL SECURITY: MARKET DRIVERS
-
9.4 SECURE COMMUNICATIONGROWING DEMAND FOR SECURE AND PRIVATE COMMUNICATION CHANNELS IN BUSINESS AND PERSONAL CONTEXTS TO DRIVE SEGMENTSECURE COMMUNICATION: MARKET DRIVERS
-
9.5 AUTHENTICATIONINCREASING EMPHASIS ON ROBUST USER AND DEVICE AUTHENTICATION, PARTICULARLY IN REMOTE AND DIGITAL ENVIRONMENTS, TO DRIVE SEGMENTAUTHENTICATION: MARKET DRIVERS
- 10.1 INTRODUCTION
-
10.2 BANKING, FINANCIAL SERVICES, AND INSURANCENEED FOR STRINGENT DATA PROTECTION, REGULATORY COMPLIANCE, AND SECURE FINANCIAL TRANSACTIONS TO DRIVE SEGMENTBANKING, FINANCIAL SERVICES, AND INSURANCE: MARKET DRIVERS
-
10.3 GOVERNMENT AND DEFENSEIMPERATIVE OF NATIONAL SECURITY, DATA PROTECTION, AND SECURE GOVERNMENT OPERATIONS TO DRIVE SEGMENTGOVERNMENT AND DEFENSE: MARKET DRIVERS
-
10.4 HEALTHCARECRITICAL NEED FOR SAFEGUARDING PATIENT DATA, COMPLYING WITH HEALTHCARE REGULATIONS, AND ENSURING SECURE TELEHEALTH SERVICES TO DRIVE SEGMENTHEALTHCARE: MARKET DRIVERS
-
10.5 IT AND TELECOMGROWING DEMAND FOR SECURE AND EFFICIENT DATA COMMUNICATION, NETWORK INTEGRITY, AND DIGITAL SERVICES TO DRIVE SEGMENTIT AND TELECOM: MARKET DRIVERS
-
10.6 RETAILINCREASING RELIANCE ON ECOMMERCE, SECURE PAYMENT PROCESSING, AND CUSTOMER DATA PROTECTION TO DRIVE RETAIL VERTICALRETAIL: MARKET DRIVERS
-
10.7 MANUFACTURINGNEED FOR SECURING INTELLECTUAL PROPERTY, SUPPLY CHAIN INTEGRITY, AND OPERATIONAL DATA TO DRIVE MANUFACTURING VERTICALMANUFACTURING: MARKET DRIVERS
-
10.8 OTHER VERTICALSOTHER VERTICALS: MARKET DRIVERS
- 11.1 INTRODUCTION
-
11.2 NORTH AMERICANORTH AMERICA: MARKET DRIVERSNORTH AMERICA: RECESSION IMPACTNORTH AMERICA: REGULATORY LANDSCAPEUSCANADA
-
11.3 EUROPEEUROPE: PUBLIC KEY INFRASTRUCTURE MARKET DRIVERSEUROPE: RECESSION IMPACTEUROPE: REGULATORY LANDSCAPEUKGERMANYFRANCEREST OF EUROPE
-
11.4 ASIA PACIFICASIA PACIFIC: MARKET DRIVERSASIA PACIFIC: RECESSION IMPACTASIA PACIFIC: REGULATORY LANDSCAPEINDIACHINAJAPANREST OF ASIA PACIFIC
-
11.5 MIDDLE EAST & AFRICAMIDDLE EAST & AFRICA: MARKET DRIVERSMIDDLE EAST & AFRICA: RECESSION IMPACTMIDDLE EAST & AFRICA: REGULATORY LANDSCAPEUNITED ARAB EMIRATESSOUTH AFRICAREST OF MIDDLE EAST & AFRICA
-
11.6 LATIN AMERICALATIN AMERICA: PUBLIC KEY INFRASTRUCTURE MARKET DRIVERSLATIN AMERICA: RECESSION IMPACTLATIN AMERICA: REGULATORY LANDSCAPEBRAZILMEXICOREST OF LATIN AMERICA

- 12.1 OVERVIEW
-
12.2 COMPANY EVALUATION MATRIXDEFINITIONS AND METHODOLOGYSTARSEMERGING LEADERSPERVASIVE PLAYERSPARTICIPANTSPRODUCT FOOTPRINT
-
12.3 STARTUP EVALUATION MATRIXDEFINITIONS AND METHODOLOGYPROGRESSIVE COMPANIESRESPONSIVE COMPANIESDYNAMIC COMPANIESSTARTING BLOCKSCOMPETITIVE BENCHMARKING
- 12.4 REVENUE ANALYSIS
- 12.5 MARKET SHARE ANALYSIS
- 12.6 STRATEGIES ADOPTED BY KEY PLAYERS/RIGHT TO WIN
-
12.7 KEY MARKET DEVELOPMENTSPRODUCT LAUNCHESDEALS
- 12.8 MARKET RANKING
- 13.1 INTRODUCTION
-
13.2 KEY PLAYERSTHALES- Business overview- Solutions and services offered- Recent developments- MnM viewENTRUST DATACARD- Business overview- Solutions offered- Recent developments- MnM viewDIGICERT- Business overview- Solutions and services offered- Recent developments- MnM viewMANAGEENGINE- Business overview- Solutions offered- Recent developments- MnM viewMICROSOFT- Business overview- Solutions offered- Recent developments- MnM viewHID GLOBAL- Business overview- Solutions and services offered- Recent developmentsGOOGLE- Business overview- Solutions offered- Recent developmentsAMAZON WEB SERVICES- Business overview- Solutions offered
-
13.3 OTHER PLAYERSAPPVIEWX- Business overview- Solutions offered- Recent developmentsVENAFI- Business overview- Solutions and services offered- Recent developmentsNEXUS- Business overview- Solutions offered- Recent developmentsSECTIGOFUTUREXGLOBALSIGNWISEKEYCYGNACOM SOLUTIONSKEYFACTORSSL.COMSTORMSHIELDLAWTRUSTSOFTLOCKSECARDEO GMBHBLUE RIDGE NETWORKSSECUREMETRICENIGMA INFORMATION SECURITY SYSTEMS
-
14.1 INTRODUCTION TO ADJACENT MARKETSLIMITATIONS
- 14.2 DIGITAL SIGNATURE MARKET
- 14.3 CERTIFICATE AUTHORITY MARKET
- 15.1 DISCUSSION GUIDE
- 15.2 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
- 15.3 CUSTOMIZATION OPTIONS
- 15.4 RELATED REPORTS
- 15.5 AUTHOR DETAILS
- TABLE 1 USD EXCHANGE RATES, 2020–2022
- TABLE 2 FACTOR ANALYSIS
- TABLE 3 ROLE OF PLAYERS IN MARKET ECOSYSTEM
- TABLE 4 TOP 20 PATENT OWNERS (US) IN LAST 10 YEARS
- TABLE 5 KEY CONFERENCES & EVENTS, 2023–2024
- TABLE 6 AVERAGE SELLING PRICE TRENDS
- TABLE 7 IMPACT OF PORTER’S FORCES ON PKI MARKET
- TABLE 8 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP 3 VERTICALS
- TABLE 9 KEY BUYING CRITERIA FOR TOP 3 VERTICALS
- TABLE 10 EXPORT SCENARIO FOR HS CODE: 847330, BY COUNTRY, 2020–2022
- TABLE 11 IMPORT SCENARIO FOR HS CODE: 847330, BY COUNTRY, 2020–2022
- TABLE 12 PUBLIC KEY INFRASTRUCTURE MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 13 MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 14 HARDWARE SECURITY MODULES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 15 HARDWARE SECURITY MODULES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 16 SOLUTIONS: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 17 SOLUTIONS: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 18 MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 19 MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 20 PROFESSIONAL SERVICES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 21 PROFESSIONAL SERVICES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 22 MANAGED SERVICES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 23 MANAGED SERVICES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 24 MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 25 PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 26 ON-PREMISES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 27 ON-PREMISES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 28 CLOUD: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 29 CLOUD: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 30 MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 31 MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 32 LARGE ENTERPRISES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 33 LARGE ENTERPRISES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 34 SMES: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 35 SMES: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 36 PUBLIC KEY INFRASTRUCTURE MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 37 MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 38 WEB BROWSING SECURITY: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 39 WEB BROWSING SECURITY: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 40 EMAIL SECURITY: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 41 EMAIL SECURITY: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 42 SECURE COMMUNICATION: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 43 SECURE COMMUNICATION: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 44 AUTHENTICATION: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 45 AUTHENTICATION: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 46 MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 47 MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 48 BFSI: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 49 BFSI: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 50 GOVERNMENT AND DEFENSE: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 51 GOVERNMENT AND DEFENSE: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 52 HEALTHCARE: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 53 HEALTHCARE: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 54 IT AND TELECOM: PUBLIC KEY INFRASTRUCTURE MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 55 IT AND TELECOM: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 56 RETAIL: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 57 RETAIL: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 58 MANUFACTURING: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 59 MANUFACTURING: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 60 OTHER VERTICALS: MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 61 OTHER VERTICALS: MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 62 MARKET, BY REGION, 2017–2022 (USD MILLION)
- TABLE 63 MARKET, BY REGION, 2023–2028 (USD MILLION)
- TABLE 64 NORTH AMERICA: PUBLIC KEY INFRASTRUCTURE MARKET REGULATIONS/ASSOCIATIONS
- TABLE 65 NORTH AMERICA: MARKET COMPLIANCE AND DESCRIPTION
- TABLE 66 NORTH AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 67 NORTH AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 68 NORTH AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 69 NORTH AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 70 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 71 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 72 NORTH AMERICA: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 73 NORTH AMERICA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 74 NORTH AMERICA: MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 75 NORTH AMERICA: MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 76 NORTH AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 77 NORTH AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 78 NORTH AMERICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 79 NORTH AMERICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 80 US: PUBLIC KEY INFRASTRUCTURE MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 81 US: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 82 US: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 83 US: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 84 US: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 85 US: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 86 US: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 87 US: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 88 US: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 89 US: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 90 CANADA: PUBLIC KEY INFRASTRUCTURE MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 91 CANADA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 92 CANADA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 93 CANADA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 94 CANADA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 95 CANADA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 96 CANADA: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 97 CANADA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 98 CANADA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 99 CANADA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 100 EUROPE: PUBLIC KEY INFRASTRUCTURE MARKET ASSOCIATIONS/REGULATIONS
- TABLE 101 EUROPE: MARKET COMPLIANCE
- TABLE 102 EUROPE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 103 EUROPE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 104 EUROPE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 105 EUROPE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 106 EUROPE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 107 EUROPE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 108 EUROPE: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 109 EUROPE: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 110 EUROPE: MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 111 EUROPE: PUBLIC KEY INFRASTRUCTURE MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 112 EUROPE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 113 EUROPE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 114 EUROPE: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 115 EUROPE: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 116 UK: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 117 UK: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 118 UK: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 119 UK: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 120 UK: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 121 UK: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 122 UK: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 123 UK: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 124 UK: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 125 UK: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 126 GERMANY: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 127 GERMANY: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 128 GERMANY: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 129 GERMANY: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 130 GERMANY: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 131 GERMANY: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 132 GERMANY: PUBLIC KEY INFRASTRUCTURE MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 133 GERMANY: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 134 GERMANY: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 135 GERMANY: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 136 FRANCE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 137 FRANCE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 138 FRANCE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 139 FRANCE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 140 FRANCE: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 141 FRANCE: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 142 FRANCE: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 143 FRANCE: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 144 FRANCE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 145 FRANCE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 146 REST OF EUROPE: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 147 REST OF EUROPE: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 148 REST OF EUROPE: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 149 REST OF EUROPE: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 150 REST OF EUROPE: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 151 REST OF EUROPE: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 152 REST OF EUROPE: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 153 REST OF EUROPE: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 154 REST OF EUROPE: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 155 REST OF EUROPE: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 156 ASIA PACIFIC: MARKET ASSOCIATIONS/REGULATIONS
- TABLE 157 ASIA PACIFIC: MARKET COMPLIANCE
- TABLE 158 ASIA PACIFIC: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 159 ASIA PACIFIC: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 160 ASIA PACIFIC: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 161 ASIA PACIFIC: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 162 ASIA PACIFIC: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 163 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 164 ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 165 ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 166 ASIA PACIFIC: MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 167 ASIA PACIFIC: MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 168 ASIA PACIFIC: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 169 ASIA PACIFIC: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 170 ASIA PACIFIC: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 171 ASIA PACIFIC: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 172 INDIA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 173 INDIA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 174 INDIA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 175 INDIA: PUBLIC KEY INFRASTRUCTURE MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 176 INDIA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 177 INDIA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 178 INDIA: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 179 INDIA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 180 INDIA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 181 INDIA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 182 CHINA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 183 CHINA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 184 CHINA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 185 CHINA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 186 CHINA: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 187 CHINA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 188 CHINA: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 189 CHINA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 190 CHINA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 191 CHINA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 192 JAPAN: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 193 JAPAN: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 194 JAPAN: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 195 JAPAN: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 196 JAPAN: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 197 JAPAN: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 198 JAPAN: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 199 JAPAN: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 200 JAPAN: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 201 JAPAN: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 202 REST OF ASIA PACIFIC: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 203 EST OF ASIA PACIFIC: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 204 REST OF ASIA PACIFIC: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 205 REST OF ASIA PACIFIC: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 206 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 207 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 208 REST OF ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 209 REST OF ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 210 REST OF ASIA PACIFIC: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 211 REST OF ASIA PACIFIC: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 212 MIDDLE EAST & AFRICA: MARKET REGULATIONS/ ASSOCIATIONS
- TABLE 213 MIDDLE EAST & AFRICA: MARKET COMPLIANCE AND DESCRIPTION
- TABLE 214 MIDDLE EAST & AFRICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 215 MIDDLE EAST & AFRICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 216 MIDDLE EAST & AFRICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 217 MIDDLE EAST & AFRICA: PUBLIC KEY INFRASTRUCTURE MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 218 MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 219 MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 220 MIDDLE EAST & AFRICA: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 221 MIDDLE EAST & AFRICA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 222 MIDDLE EAST & AFRICA: MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 223 MIDDLE EAST & AFRICA: MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 224 MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 225 MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 226 MIDDLE EAST & AFRICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 227 MIDDLE EAST & AFRICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 228 UNITED ARAB EMIRATES: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 229 UNITED ARAB EMIRATES: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 230 UNITED ARAB EMIRATES: PUBLIC KEY INFRASTRUCTURE MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 231 UNITED ARAB EMIRATES: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 232 UNITED ARAB EMIRATES: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 233 UNITED ARAB EMIRATES: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 234 UNITED ARAB EMIRATES: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 235 UNITED ARAB EMIRATES: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 236 UNITED ARAB EMIRATES: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 237 UNITED ARAB EMIRATES: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 238 SOUTH AFRICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 239 SOUTH AFRICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 240 SOUTH AFRICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 241 SOUTH AFRICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 242 SOUTH AFRICA: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 243 SOUTH AFRICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 244 SOUTH AFRICA: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 245 SOUTH AFRICA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 246 SOUTH AFRICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 247 SOUTH AFRICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 248 REST OF MIDDLE EAST & AFRICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 249 REST OF MIDDLE EAST & AFRICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 250 REST OF MIDDLE EAST AND AFRICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 251 REST OF MIDDLE EAST & AFRICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 252 REST OF MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 253 REST OF MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 254 REST OF MIDDLE EAST & AFRICA: PUBLIC KEY INFRASTRUCTURE MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 255 REST OF MIDDLE EAST & AFRICA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 256 REST OF MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 257 REST OF MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 258 LATIN AMERICA: MARKET REGULATIONS/ASSOCIATIONS
- TABLE 259 LATIN AMERICA: MARKET COMPLIANCE AND DESCRIPTION
- TABLE 260 LATIN AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 261 LATIN AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 262 LATIN AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 263 LATIN AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 264 LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 265 LATIN AMERICA: PUBLIC KEY INFRASTRUCTURE MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 266 LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 267 LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 268 LATIN AMERICA: MARKET, BY APPLICATION, 2017–2022 (USD MILLION)
- TABLE 269 LATIN AMERICA: MARKET, BY APPLICATION, 2023–2028 (USD MILLION)
- TABLE 270 LATIN AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 271 LATIN AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 272 LATIN AMERICA: MARKET, BY COUNTRY, 2017–2022 (USD MILLION)
- TABLE 273 LATIN AMERICA: MARKET, BY COUNTRY, 2023–2028 (USD MILLION)
- TABLE 274 BRAZIL: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 275 BRAZIL: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 276 BRAZIL: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 277 BRAZIL: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 278 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 279 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 280 BRAZIL: PUBLIC KEY INFRASTRUCTURE MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 281 BRAZIL: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 282 BRAZIL: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 283 BRAZIL: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 284 MEXICO: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 285 MEXICO: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 286 MEXICO: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 287 MEXICO: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 288 MEXICO: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 289 MEXICO: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 290 MEXICO: MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 291 MEXICO: PUBLIC KEY INFRASTRUCTURE MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 292 MEXICO: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 293 MEXICO: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 294 REST OF LATIN AMERICA: MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 295 REST OF LATIN AMERICA: MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 296 REST OF LATIN AMERICA: MARKET, BY SERVICE, 2017–2022 (USD MILLION)
- TABLE 297 REST OF LATIN AMERICA: MARKET, BY SERVICE, 2023–2028 (USD MILLION)
- TABLE 298 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2017–2022 (USD MILLION)
- TABLE 299 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2023–2028 (USD MILLION)
- TABLE 300 REST OF LATIN AMERICA: PUBLIC KEY INFRASTRUCTURE MARKET, BY ORGANIZATION SIZE, 2017–2022 (USD MILLION)
- TABLE 301 REST OF LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 2023–2028 (USD MILLION)
- TABLE 302 REST OF LATIN AMERICA: MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 303 REST OF LATIN AMERICA: MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- TABLE 304 EVALUATION CRITERIA
- TABLE 305 KEY COMPANY FOOTPRINT, BY OFFERING
- TABLE 306 KEY COMPANY FOOTPRINT, BY DEPLOYMENT MODE
- TABLE 307 KEY COMPANY FOOTPRINT, BY VERTICAL
- TABLE 308 KEY COMPANY FOOTPRINT, BY REGION
- TABLE 309 STARTUP FOOTPRINT, BY OFFERING
- TABLE 310 STARTUP FOOTPRINT, BY DEPLOYMENT MODE
- TABLE 311 STARTUP FOOTPRINT, BY VERTICAL
- TABLE 312 STARTUP FOOTPRINT, BY REGION
- TABLE 313 DEGREE OF COMPETITION
- TABLE 314 OVERVIEW OF STRATEGIES ADOPTED BY KEY PLAYERS IN PKI MARKET
- TABLE 315 MARKET: PRODUCT LAUNCHES, MARCH 2019–SEPTEMBER 2023
- TABLE 316 MARKET: DEALS, JANUARY 2020–AUGUST 2023
- TABLE 317 THALES: BUSINESS OVERVIEW
- TABLE 318 THALES: SOLUTIONS OFFERED
- TABLE 319 THALES: SERVICES OFFERED
- TABLE 320 THALES: PRODUCT LAUNCHES
- TABLE 321 THALES: DEALS
- TABLE 322 ENTRUST DATACARD: BUSINESS OVERVIEW
- TABLE 323 ENTRUST DATACARD: SOLUTIONS OFFERED
- TABLE 324 ENTRUST DATACARD: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 325 ENTRUST DATACARD: DEALS
- TABLE 326 DIGICERT: BUSINESS OVERVIEW
- TABLE 327 DIGICERT: SOLUTIONS OFFERED
- TABLE 328 DIGICERT: SERVICES OFFERED
- TABLE 329 DIGICERT: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 330 DIGICERT: DEALS
- TABLE 331 MANAGEENGINE: BUSINESS OVERVIEW
- TABLE 332 MANAGEENGINE: SOLUTIONS OFFERED
- TABLE 333 MANAGEENGINE: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 334 MANAGEENGINE: DEALS
- TABLE 335 MICROSOFT: BUSINESS OVERVIEW
- TABLE 336 MICROSOFT: SOLUTIONS OFFERED
- TABLE 337 MICROSOFT: PRODUCT LAUNCHES
- TABLE 338 MICROSOFT: DEALS
- TABLE 339 HID GLOBAL: BUSINESS OVERVIEW
- TABLE 340 HID GLOBAL: SOLUTIONS OFFERED
- TABLE 341 HID GLOBAL: SERVICES OFFERED
- TABLE 342 HID GLOBAL: PRODUCT LAUNCHES
- TABLE 343 HID GLOBAL: DEALS
- TABLE 344 GOOGLE: BUSINESS OVERVIEW
- TABLE 345 GOOGLE: SOLUTIONS OFFERED
- TABLE 346 GOOGLE: PRODUCT LAUNCHES
- TABLE 347 GOOGLE: DEALS
- TABLE 348 AMAZON WEB SERVICES: BUSINESS OVERVIEW
- TABLE 349 AMAZON WEB SERVICES: SOLUTIONS OFFERED
- TABLE 350 APPVIEWX: BUSINESS OVERVIEW
- TABLE 351 APPVIEWX: SOLUTIONS OFFERED
- TABLE 352 APPVIEWX: DEALS
- TABLE 353 APPVIEWX: OTHERS
- TABLE 354 VENAFI: BUSINESS OVERVIEW
- TABLE 355 VENAFI: SOLUTIONS OFFERED
- TABLE 356 VENAFI: SERVICES OFFERED
- TABLE 357 VENAFI: PRODUCT LAUNCHES
- TABLE 358 VENAFI: DEALS
- TABLE 359 NEXUS: BUSINESS OVERVIEW
- TABLE 360 NEXUS: SOLUTIONS OFFERED
- TABLE 361 NEXUS: DEALS
- TABLE 362 ADJACENT MARKETS AND FORECASTS
- TABLE 363 DIGITAL SIGNATURE MARKET, BY COMPONENT, 2016–2021 (USD MILLION)
- TABLE 364 DIGITAL SIGNATURE MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 365 DIGITAL SIGNATURE MARKET, BY VERTICAL, 2016–2021 (USD MILLION)
- TABLE 366 DIGITAL SIGNATURE MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 367 CERTIFICATE AUTHORITY MARKET, BY OFFERING, 2017–2022 (USD MILLION)
- TABLE 368 CERTIFICATE AUTHORITY MARKET, BY OFFERING, 2023–2028 (USD MILLION)
- TABLE 369 CERTIFICATE AUTHORITY MARKET, BY VERTICAL, 2017–2022 (USD MILLION)
- TABLE 370 CERTIFICATE AUTHORITY MARKET, BY VERTICAL, 2023–2028 (USD MILLION)
- FIGURE 1 RESEARCH DESIGN
- FIGURE 2 DATA TRIANGULATION
- FIGURE 3 MARKET SIZE ESTIMATION METHODOLOGY, APPROACH 1 (SUPPLY SIDE): REVENUE OF HARDWARE SECURITY MODULES, SOLUTIONS, AND SERVICES IN PUBLIC KEY INFRASTRUCTURE MARKET
- FIGURE 4 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 1, SUPPLY-SIDE ANALYSIS
- FIGURE 5 MARKET ESTIMATION APPROACH: SUPPLY-SIDE ANALYSIS (COMPANY REVENUE ESTIMATION [ILLUSTRATION OF REVENUE ESTIMATION FOR THALES])
- FIGURE 6 MARKET SIZE ESTIMATION METHODOLOGY: APPROACH 2, BOTTOM-UP (DEMAND SIDE), BY VERTICAL
- FIGURE 7 RECESSION IMPACT ANALYSIS
- FIGURE 8 PUBLIC KEY INFRASTRUCTURE MARKET TO WITNESS SIGNIFICANT GROWTH DURING FORECAST PERIOD
- FIGURE 9 MARKET: MAJOR SUBSEGMENTS, 2023–2028
- FIGURE 10 NORTH AMERICA TO ACCOUNT FOR LARGEST SHARE IN 2023
- FIGURE 11 RISING CASES OF MALWARE AND FILE-BASED ATTACKS AND STRINGENT REGULATORY NORMS TO DRIVE MARKET
- FIGURE 12 SOLUTIONS SEGMENT TO ACCOUNT FOR LARGEST SHARE DURING FORECAST PERIOD
- FIGURE 13 PROFESSIONAL SERVICES SEGMENT TO ACCOUNT FOR LARGER MARKET DURING FORECAST PERIOD
- FIGURE 14 ON-PREMISES SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 15 LARGE ENTERPRISES SEGMENT TO LEAD MARKET DURING FORECAST PERIOD
- FIGURE 16 BFSI SEGMENT TO ACCOUNT FOR LARGEST MARKET BY 2028
- FIGURE 17 ASIA PACIFIC TO EMERGE AS BEST MARKET FOR INVESTMENT
- FIGURE 18 PKI MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 19 TOP CHALLENGES IN PKI DEPLOYMENT AND MANAGEMENT, 2018
- FIGURE 20 KEY COMPANIES’ ECOSYSTEM ANALYSIS
- FIGURE 21 VALUE CHAIN ANALYSIS
- FIGURE 22 NUMBER OF PATENTS GRANTED, 2013–2022
- FIGURE 23 TOP 10 COMPANIES WITH HIGHEST NUMBER OF PATENT APPLICATIONS
- FIGURE 24 PORTER’S FIVE FORCES MODEL
- FIGURE 25 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP 3 VERTICALS
- FIGURE 26 KEY BUYING CRITERIA FOR TOP 3 VERTICALS
- FIGURE 27 TRENDS AND DISRUPTIONS IMPACTING CUSTOMERS
- FIGURE 28 SOLUTIONS SEGMENT TO ACCOUNT FOR LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 29 ON-PREMISES SEGMENT TO HOLD LARGER MARKET SIZE DURING FORECAST PERIOD
- FIGURE 30 LARGE ENTERPRISES SEGMENT TO HOLD LARGER MARKET SIZE DURING FORECAST PERIOD
- FIGURE 31 AUTHENTICATION SEGMENT TO HOLD A LARGER MARKET SIZE DURING THE FORECAST PERIOD
- FIGURE 32 BANKING, FINANCIAL SERVICES, AND INSURANCE SEGMENT TO ACCOUNT FOR LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 33 NORTH AMERICA: MARKET SNAPSHOT
- FIGURE 34 ASIA PACIFIC: MARKET SNAPSHOT
- FIGURE 35 PUBLIC KEY INFRASTRUCTURE MARKET (GLOBAL): COMPANY EVALUATION MATRIX, 2023
- FIGURE 36 PRODUCT FOOTPRINT OF KEY COMPANIES
- FIGURE 37 MARKET (GLOBAL): STARTUP EVALUATION MATRIX, 2023
- FIGURE 38 PRODUCT FOOTPRINT OF STARTUPS
- FIGURE 39 REVENUE ANALYSIS OF KEY PUBLIC KEY INFRASTRUCTURE VENDORS
- FIGURE 40 PUBLIC KEY INFRASTRUCTURE MARKET (GLOBAL): MARKET SHARE, 2023
- FIGURE 41 MARKET RANKING IN 2022
- FIGURE 42 THALES: COMPANY SNAPSHOT
- FIGURE 43 MICROSOFT: COMPANY SNAPSHOT
- FIGURE 44 GOOGLE: COMPANY SNAPSHOT
- FIGURE 45 AMAZON WEB SERVICES: COMPANY SNAPSHOT
The research study involved four major activities in estimating the public key infrastructure market size. Exhaustive secondary research has been done to collect important information about the market and peer markets. The next step has been to validate these findings, assumptions, and sizing with the help of primary research with industry experts across the value chain. Both top-down and bottom-up approaches have been used to estimate the market size. Post which the market breakdown and data triangulation have been adopted to estimate the market sizes of segments and sub-segments.
Secondary Research
In the secondary research process, various secondary sources were referred to identify and collect information for the study. These included journals, annual reports, press releases, investor presentations of companies and white papers, certified publications, and articles from recognized associations and government publishing sources. Secondary research was mainly used to obtain key information about industry insights, the market’s monetary chain, the overall pool of key players, market classification, and segmentation according to industry trends to the bottom-most level, regional markets, and key developments from both market and technology-oriented perspectives.
Primary Research
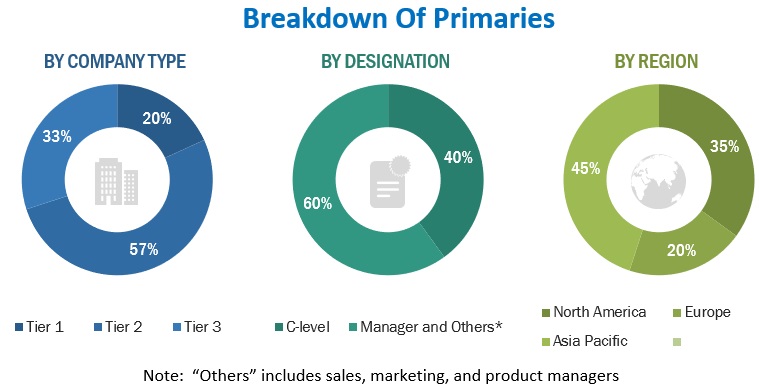
In the primary research process, various primary sources from both the supply and demand sides were interviewed to obtain qualitative and quantitative information for the report. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Chief Technology Officers (CTOs), Chief Operating Officers (COOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various companies and organizations operating in the public key infrastructure market. The primary sources from the demand side included consultants/specialists, Chief Information Officers (CIOs), and subject-matter experts.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Multiple approaches were adopted to estimate and forecast the public key infrastructure market. The first approach involved estimating the market size by summating companies’ revenue generated through public key infrastructure solutions.
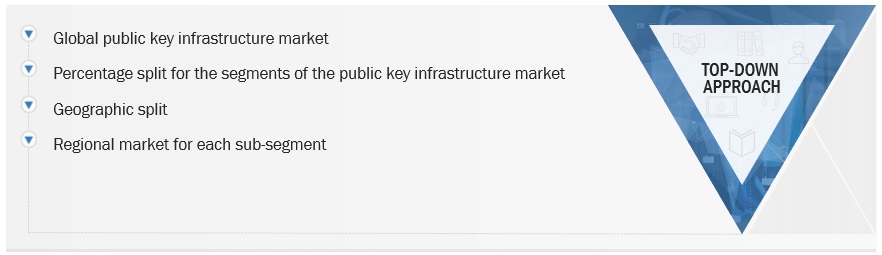
Both top-down and bottom-up approaches were used to estimate and validate the total size of the public key infrastructure market. The research methodology used to estimate the market size includes the following:
- Key players in the market have been identified through extensive secondary research.
- In terms of value, the industry’s supply chain and market size have been determined through primary and secondary research processes.
- All percentage shares, splits, and breakups have been determined using secondary sources and verified through primary sources.
Market Size Estimation Methodology-Bottom-up approach

To know about the assumptions considered for the study, Request for Free Sample Report
Market Size Estimation Methodology-top-down approach
Data Triangulation
The data triangulation procedures were used to complete the overall market engineering process and arrive at the exact statistics for all segments and subsegments. The data was triangulated by studying various factors and trends from the demand and supply sides. Along with data triangulation and market breakdown, the market size was validated by the top-down and bottom-up approaches.
Market Definition
Public Key Infrastructure serves as a robust framework for establishing trust and security in the digital world. It encompasses a comprehensive system of hardware, software, policies, and standards designed to manage and safeguard digital certificates and associated cryptographic keys. At its core, PKI enables secure communication, authentication, encryption, and digital signatures by binding users and entities to their unique digital identities through the issuance of digital certificates. These certificates, along with public and private keys, form the cornerstone of PKI, allowing for secure data exchange and identity verification.
Key Stakeholders
- Chief technology and data officers
- Software and solution developers
- Integration and deployment service providers
- Business analysts
- Information Technology (IT) professionals
- Investors and venture capitalists
- Third-party providers
- Consultants/consultancies/advisory firms
- Cyber-security firms
- Value-added Resellers (VARs)
- PKI Certificate authorities (CA)
- SSL/TLS Certificate providers
- Digital certificate providers
- PKI’s registration authorities (RA)
The main objectives of this study are as follows:
- To define, describe, and forecast the public key infrastructure market based on segments based on offering, deployment mode, organization size, application, and vertical with regions covered.
- To forecast the size of the market segments with respect to five regions: North America, Europe, Asia Pacific (APAC), Middle East and Africa (MEA), and Latin America.
- To provide detailed information on the major factors (drivers, opportunities, threats, and challenges) influencing the growth of the public key infrastructure market.
- To analyze each submarket with respect to individual growth trends, prospects, and contributions to the global market.
- To analyze opportunities in the market for stakeholders by identifying high-growth segments of the global market.
- To profile the key market players, such as top and emerging vendors; provide a comparative analysis based on their business overviews, product offerings, and business strategies; and illustrate the market’s competitive landscape.
- To track and analyze competitive developments in the market, such as new product launches, product enhancements, partnerships, acquisitions, and agreements and collaborations.
Available Customizations
With the given market data, MarketsandMarkets offers customizations as per the company’s specific needs. The following customization options are available for the report:
Company Information
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...










Growth opportunities and latent adjacency in Public Key Infrastructure (PKI) Market
what are the major challenges in Public Key Infrastructure Market?