Edge Security Market by Component (Solutions (CASB, SD-WAN, SASE) and Services), Organization Size (Large Enterprises, SMEs), Deployment Mode, Vertical (BFSI, Government & Defense, and IT & Telecom) and Region - Global Forecast to 2027
Updated on : Nov 17, 2025
Edge Security Market - Worldwide | Future Scope & Trends
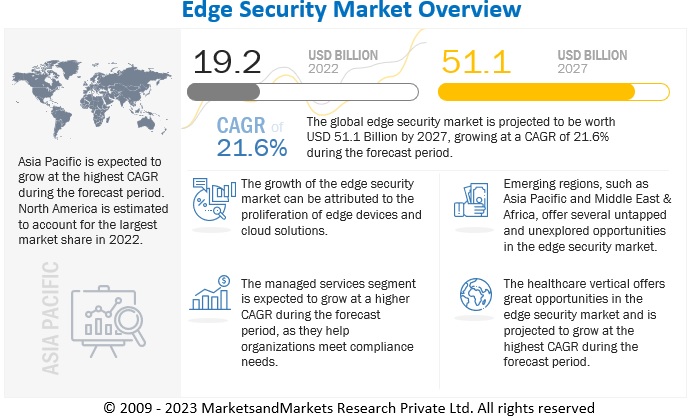
The global edge security market size was estimated at USD 19.2 billion in 2022 and is projected to reach USD 51.1 billion by 2027, growing at a CAGR of 21.6% from 2022 to 2027. The need for edge device security to protect the endpoints and the need for connecting and protecting the remote workforce is driving the demand for edge security solutions and services.
To know about the assumptions considered for the study, Request for Free Sample Report
Edge Security Market Dynamics
Driver: Need for secure access to cloud services and websites
Enforcing policy control over user access to the internet, web, and cloud applications (historically performed by an SWG) is one of the primary use cases for the security service edge. SSE policy control helps mitigate risk as end users access content on and off-network. Enforcing corporate internet and access control policies for compliance is also a key driver for secure access to IaaS, PaaS, and SaaS. Another key capability is Cloud Security Posture Management (CSPM), which protects organizations from risky misconfigurations that can lead to breaches. As per the AT&T Cybersecurity Insights Report 2022, 5G and cloud are the most preferred edge networks. The report found that over 93% of respondents researched, implemented, and completed 5G implementations, and 58% believed the cellular edge would enable near-real-time cloud services. Thus, the growing usage of web applications and cloud services is expected to boost the adoption of edge security solutions during the forecast period.
Restraint: Lack of awareness and education about SASE security architecture
The COVID-19 pandemic forced many organizations around the globe to accelerate their digital transformation activities to support work from anywhere and remote operations. According to Versa Networks Global Transformation Survey 2021, security and IT professionals disclosed that 84% of organizations have recently accelerated their digital transformation adoption initiatives and moved to the cloud. During this transformation, the main challenges experienced were network performance and security. With countless new devices connected to organizations' networks, this overloaded the systems and caused a dramatic increase in security risks. Organizations have rolled out the SASE approach to offer improved security of applications and devices used by the work-from-anywhere user. Despite growing adoption, the survey found that only 31% of teams know the accurate definition of SASE. As a result of this lack of understanding, some organizations may not be able to realize all the true benefits of their SASE implementations. As per the survey, a lack of budget and other business plans are also hindering the adoption of SASE technology.
Opportunity: Rising adoption of 5G services to improve communication infrastructure
5G and edge computing are two linked technologies. They are both poised to significantly improve the performance of applications and enable huge amounts of data to be processed in real-time. 5G increases speed by up to ten times that of 4G, whereas mobile edge computing reduces latency by bringing compute capabilities into the network closer to the end user. 5G will provide the technology boost to support Ultra Reliable Low Latency Communication (URLLC) that enables applications such as V2X and Telesurgery, Cobots. These applications require end-to-end latency to be in milliseconds. 5G will also provide Enhanced Mobile Broadband (eMBB) capability for use cases that involve large data rates, such as augmented reality and virtual reality. As per the Ericsson Mobility Report November 2022, North America and Northeast Asia are expected to have the highest 5G subscription penetration by the end of 2022, followed by the Gulf Cooperation Council countries at 20% and Western Europe at 11%. In the Gulf Cooperation Council, the demand is driven by the increased vigorous competition combined with the right regulatory environment, have contributed to the fast acceleration of the 5G market. The report also states that 5G subscriptions are forecast to reach 5 billion in 2028. The key factors to drive this include the availability of devices from vendors, falling prices, and early 5G developments in China. The developments in 5G will likely boost edge security solutions' adoption during the forecast period.
Challenge: Managing highly distributed environments
Managing any large-scale edge architecture is managing hundreds or even thousands of smaller IT environments. Manually updating tasks, such as configuration management, OS patches, and other software updates, is tedious. Deploying and operating large-scale distributed infrastructures is challenging enough without throwing randomness and silos into the mix. Thus, automation and management are essential for tasks such as mass configuration, taking actions in response to events, and centralized application updates. Standardized operating system configurations and cluster orchestration are essential for managing edge computing environments.
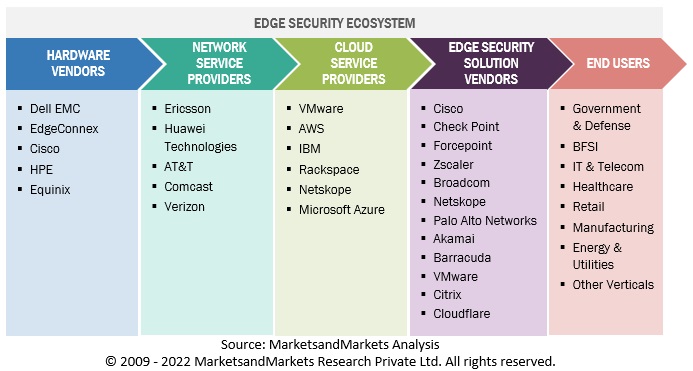
Edge Security Market Ecosystem
To know about the assumptions considered for the study, download the pdf brochure
Based on services, managed services segment to grow at a higher CAGR during the forecast period
Managed services mostly revolve around the term "outsourcing." Managed services, including managing databases and collecting data, are outsourced to Managed Service Providers (MSPs). Managed Security Service Providers (MSSPs) provide specialized security services to other companies. Managed Security Services (MSSs) are available in many forms, such as pure system management, sophisticated fraud investigators, on-premises device monitoring and management services, and cloud services. The managed services market is highly fragmented and comprises vendors from diverse backgrounds, ranging from specialized MSS providers to security professionals, system integrators, and VARs. Since these services require attention regularly, it becomes difficult for enterprises to manage them and their core business operations. As a result, companies are rapidly outsourcing their edge security services to specialized providers known as MSSPs.
Based on deployment modes, the cloud deployment model to grow at a higher CAGR during the forecast period
A distributed edge evolution increases the attack surface and reinforces the need for security at each location. Cloud-based edge security solutions offer a solution for multi-cloud, hybrid-cloud, and multi-tenant edge deployments. It offers proven solutions for IoT, API, LAN, and application security by enabling a zero-trust security model across all edge locations. Cloud-based edge security solutions eliminate the challenges of managing legacy application-based solutions.
Based on verticals, healthcare vertical to grow at the highest CAGR during the forecast period
The healthcare vertical covers personal health information and critical patient data. Data security is, therefore, of utmost importance to healthcare organizations. Healthcare organizations use network security technology to prevent the theft of patients' medical records. Edge security solutions help healthcare professionals secure personal health information stored on edge devices, such as IoT devices and sensors. Furthermore, data, file, and folder network security help healthcare professionals ensure the security and privacy of confidential data, financial transactions, and medical records related to patients. Moreover, using edge security technology helps improve the proficiency of the clinical and IT staff and provides real-time access in case of emergencies.
Additionally, implementing regulatory standards, such as HIPAA, is driving healthcare organizations' adoption of edge security. The regulatory standards also help secure sensitive data, protect identities by providing digital signatures, secure network gateways, and encrypting databases. With the rising use of edge security solutions and increasing awareness of regulatory compliances, the adoption of edge security technology is expected to grow in developing countries.
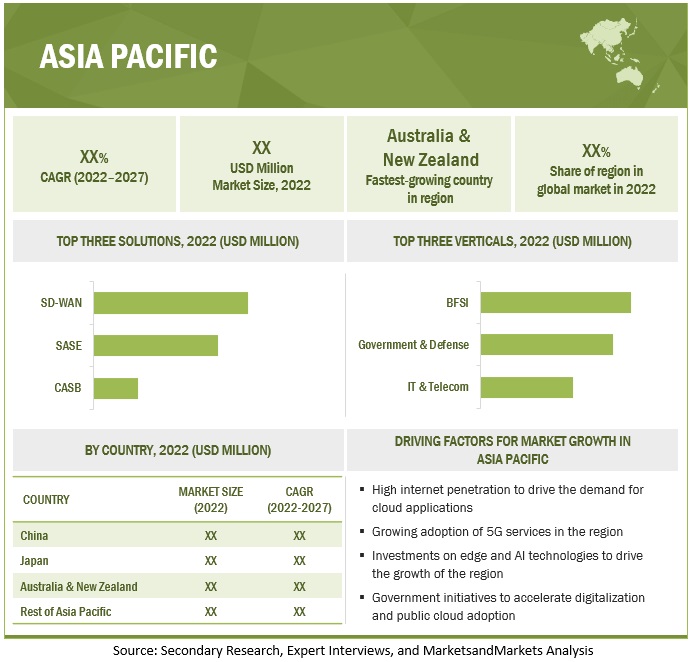
Asia Pacific to grow at highest CAGR during the forecast period
Digital technology has expanded the growth opportunities in the Asia Pacific region. The region comprises various developed economies such as China, Japan, Australia & New Zealand. As a region, there is significant strength and expertise in Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS). This is likely to drive the edge security market growth in the region. However, the adoption rate is low in the Asia Pacific region compared to North America and Europe. This is mainly due to the lack of skilled cybersecurity professionals and awareness among top IT professionals as per the Sophos Future of Cybersecurity Asia Pacific and Japan 2022.
The growing demand for cloud computing across the Asia Pacific region is driving the demand for cloud networking services, particularly with the outbreak of COVID-19. In Asia Pacific, organizations across telecommunications, government and defense, financial services, manufacturing, and sovereign cloud providers have been the most receptive to adopting cloud networking. Cloud networking can play a vital role in addressing growing infrastructure needs and regional expansion challenges in the region. Further, the smart city initiative in the region is driving investments in AI and connected devices. SASE solution providers are entering the region to support remote operations. For instance, in January 2021, Sangfor Technologies expanded its SASE services in the Asia Pacific region.
Key Market Players
The edge security market is dominated by companies such as Palo Alto Networks (US), Check Point (Israel), Broadcom (US), Fortinet (US), Cisco (US), Zscaler (US), Cloudflare (US), Forcepoint (US), VMware (US), Citrix (US), Akamai (US), Juniper Networks (US), Netskope (US), Trend Micro (Japan), Proofpoint (US), Barracuda (US), Sophos (UK), SonicWall (US), Infoblox (US), Open Systems (US), F5 (US), Lookout (US), and iboss (US). These vendors have a large customer base and a strong geographic presence with distribution channels globally to drive business revenue and growth.
Scope of the Report
|
Report Metrics |
Details |
|
Market size value in 2022 |
USD 19.2 billion |
|
Revenue forecast for 2027 |
USD 51.1 billion |
|
Growth Rate |
21.6% CAGR |
|
Forecast units |
Value (USD Billion) |
|
Key Market Drivers |
|
|
Key Market Opportunities |
|
|
Segments covered |
Component, Organization Size, Deployment Mode, Vertical, and Region |
|
Regions covered |
North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
|
Companies covered |
Palo Alto Networks (US), Check Point (Israel), Broadcom (US), Fortinet (US), Cisco (US), Zscaler (US), Cloudflare (US), Forcepoint (US) |
Edge Security Market Highlights
This research report categorizes the Edge Security Market to forecast revenues and analyze trends in each of the following submarkets:
|
Segment |
Subsegment |
|
Based on Component: |
|
|
Based on Deployment Mode: |
|
|
Based on organization size: |
|
|
Based on the vertical: |
|
|
Based on the Region: |
|
Recent Developments
- In October 2022, Fortinet announced significant cloud-delivered enhancements to FortiSASE to enable secure internet access that ensures consistent security for all user traffic to and from the internet. FortiSASE now includes new updates enhancing support for secure private and SaaS access cases.
- In February 2022, Check Point acquired Spectral, an innovator in automated code security. With this acquisition, Check Point would enhance its Cloud Guard solution with a developer-first security platform and provide the widest range of cloud application security.
- In November 2021, Palo Alto Networks launched Next-Generation CASB to help organizations secure high SaaS usage. The solution would offer a cloud access security broker to align with changing enterprise needs.
- In March 2021, Cisco launched the SASE offering with the ability to offer all core components in a single solution. It also provides the flexibility to transit to a unified subscription service in the future. Cisco simplifies networking and security operations with an expanded SASE architecture and unveils innovations to the cloud-native platform, SecureX.
- In March 2020, Broadcom updated its previous software Symantec Endpoint with new features where admins can now add privileges, such as running a live update, quick and full scan, quarantine, and reboot. FDR and EDR searches are also updated. The company is also launching a policy update soon.
Frequently Asked Questions (FAQ):
What is the projected market value of the edge security market?
The edge security market size is expected to grow from USD 19.2 billion in 2022 to USD 51.1 billion by 2027, at a Compound Annual Growth Rate (CAGR) of 21.6% during the forecast period.
Which region has the highest market share in the edge security market?
The North America region has a higher market share in the edge security market.
Which solution is expected to witness high adoption in the coming years?
SASE will witness the highest adoption rate in the coming five years.
Which are the major vendors in the edge security market?
Palo Alto Networks (US), Check Point (Israel), Broadcom (US), Fortinet (US), and Cisco (US)are major vendors in the edge security market.
What are some of the drivers in the edge security market?
A surge in remote workforce with the adoption of work from home models.
The increase in adoption of IoT, AI, 5G and cloud offerings.
To speak to our analyst for a discussion on the above findings, click Speak to Analyst


- 5.1 INTRODUCTION
-
5.2 MARKET DYNAMICSDRIVERS- Need for secure access to cloud services and websites- Need for connecting and securing remote workforce- Need for edge device security to protect endpointsRESTRAINTS- Lack of awareness and education about SASE security architectureOPPORTUNITIES- Rising adoption of 5G services to improve communication infrastructure- Accelerated adoption of IoT and edge solutions across business functionsCHALLENGES- Managing highly distributed environments- Limited capability and scaling complexities
-
5.3 CASE STUDY ANALYSISCASE STUDY 1: BOMBARDIER ENHANCED SECURITY WITH ZSCALER TO EXPAND ZERO-TRUST ARCHITECTURECASE STUDY 2: HITACHI LIMITED ADOPTED CISCO SASE SOLUTIONS TO IMPLEMENT ZERO-TRUST MODELCASE STUDY 3: CATO SASE CLOUD SECURED NETWORKING OF BANK AVERA LOCATIONS AND ITS MOBILE EMPLOYEESCASE STUDY 4: NEW YORK BANK STRENGTHENED BANDWIDTH AND SERVICES WITH VMWARE SD-WAN
- 5.4 SUPPLY CHAIN ANALYSIS
-
5.5 ECOSYSTEM
-
5.6 TECHNOLOGY ANALYSISBIG DATA AND ANALYTICSARTIFICIAL INTELLIGENCEMACHINE LEARNING
- 5.7 PRICING ANALYSIS
-
5.8 PATENT ANALYSIS
-
5.9 PORTER’S FIVE FORCES ANALYSISTHREAT OF NEW ENTRANTSTHREAT OF SUBSTITUTESBARGAINING POWER OF SUPPLIERSBARGAINING POWER OF BUYERSINTENSITY OF COMPETITIVE RIVALRY
- 5.10 KEY CONFERENCES AND EVENTS IN 2022–2023
-
5.11 TARIFF AND REGULATORY LANDSCAPEREGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONSREGULATIONS
-
5.12 TRENDS/DISRUPTIONS IMPACTING BUYERS
-
5.13 KEY STAKEHOLDERS & BUYING CRITERIAKEY STAKEHOLDERS IN BUYING PROCESSBUYING CRITERIA
-
6.1 INTRODUCTIONCOMPONENT: MARKET DRIVERS
-
6.2 SOLUTIONSCLOUD ACCESS SECURITY BROKER- Wide adoption of CASB for ensuring control of data loss and real-time data monitoring to boost market growthSOFTWARE-DEFINED WIDE AREA NETWORK- Growing adoption of SD-WAN for addressing enterprise network traffic growth cost-efficiently to drive marketSECURE ACCESS SERVICE EDGE- Need to simplify IT infrastructure and facilitate updating multiple security systems to drive marketOTHER SOLUTIONS
-
6.3 SERVICESPROFESSIONAL SERVICES- Lack of technical expertise to drive adoption of professional services- Implementation & integration services- Training & consulting services- Support & maintenance servicesMANAGED SERVICES- Managed services to gain popularity for helping organizations meet compliance needs
-
7.1 INTRODUCTIONORGANIZATION SIZE: MARKET DRIVERS
-
7.2 LARGE ENTERPRISESGROWING NEED FOR SECURING DATA FROM VULNERABILITIES TO FUEL ADOPTION OF EDGE SECURITY SOLUTIONS
-
7.3 SMALL AND MEDIUM-SIZED ENTERPRISESRISING SECURITY ISSUES TO GROW ADOPTION OF EDGE SECURITY SOLUTIONS
-
8.1 INTRODUCTIONDEPLOYMENT MODE: MARKET DRIVERS
-
8.2 ON-PREMISESGROWING CONCERNS OVER PRIVACY AND SECURITY OF CONFIDENTIAL DATA TO DRIVE MARKET
-
8.3 CLOUDNEED TO MANAGE DISTRIBUTED EDGE LOCATIONS TO BOOST MARKET GROWTH
-
9.1 INTRODUCTIONVERTICAL: MARKET DRIVERS
-
9.2 GOVERNMENT & DEFENSENEED TO IMPROVE CRITICAL INFORMATION SECURITY AND REDUCE THREAT OF UNAUTHORIZED ACCESS TO DRIVE MARKET
-
9.3 BANKING, FINANCIAL SERVICES, & INSURANCEEFFECTIVELY SECURING SENSITIVE INFORMATION AND ENSURING DATA PRIVACY TO PROPEL MARKET GROWTH
-
9.4 IT & TELECOMGROWING NEED FOR PROVIDING SECURED INFORMATION AND EDGE SECURITY SERVICES TO FUEL MARKET GROWTH
-
9.5 HEALTHCAREGROWING NEED FOR SECURING PATIENTS’ DATA TO BOOST ADOPTION OF EDGE SECURITY SOLUTIONS
-
9.6 RETAILDEMAND FOR EDGE SECURITY TO SAFEGUARD SENSITIVE INFORMATION TO PROPEL MARKET GROWTH
-
9.7 MANUFACTURINGRISING MANUFACTURING UNITS SPURRING DEMAND FOR SUPERIOR CONNECTIVITY TO PROPEL MARKET GROWTH
-
9.8 ENERGY & UTILITIESEVOLVING VOLUMETRIC NETWORK-BASED ATTACKS TO FUEL ADOPTION OF EDGE SECURITY SOLUTIONS
- 9.9 OTHER VERTICALS
- 10.1 INTRODUCTION
-
10.2 NORTH AMERICANORTH AMERICA: MARKET DRIVERSUS- Increasing use of broadband services and other technologies to drive marketCANADA- Technological advancements to fuel adoption of edge security solutions
-
10.3 EUROPEEUROPE: MARKET DRIVERSUK- Growing adoption of cloud to drive demand for security solutionsGERMANY- Growing dependence on public cloud services for managing applications to propel market growthFRANCE- Huge investments in cloud computing projects to drive demand for edge security solutionsREST OF EUROPE
-
10.4 ASIA PACIFICASIA PACIFIC: MARKET DRIVERSCHINA- Growing adoption of 5G services to drive marketJAPAN- Growing investment in new technologies to propel growth of global edge security marketAUSTRALIA & NEW ZEALAND- Presence of several telecom service providers to boost market growthREST OF ASIA PACIFIC
-
10.5 MIDDLE EAST & AFRICAMIDDLE EAST & AFRICA: MARKET DRIVERSUAE- Growing developments in ICT industry to drive demand for edge security solutionsSAUDI ARABIA- Inclination toward advanced technologies to propel market growthSOUTH AFRICA- Growing adoption of advanced technologies by several organizations to drive marketREST OF MIDDLE EAST & AFRICA
-
10.6 LATIN AMERICALATIN AMERICA: EDGE SECURITY MARKET DRIVERSBRAZIL- Growing complexity in cloud environment and expanding cloud computing solutions to drive marketMEXICO- Growing developments in cloud to drive digital innovation and technological advancementREST OF LATIN AMERICA

- 11.1 OVERVIEW
- 11.2 MARKET EVALUATION FRAMEWORK
- 11.3 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 11.4 REVENUE ANALYSIS
- 11.5 MARKET SHARE ANALYSIS
-
11.6 COMPANY EVALUATION QUADRANTSTARSEMERGING LEADERSPERVASIVE PLAYERSPARTICIPANTSCOMPANY PRODUCT FOOTPRINT ANALYSIS
- 11.7 RANKING OF KEY PLAYERS
-
11.8 STARTUP/SME EVALUATION MATRIXPROGRESSIVE COMPANIESRESPONSIVE COMPANIESDYNAMIC COMPANIESSTARTING BLOCKSCOMPETITIVE BENCHMARKING
-
11.9 KEY MARKET DEVELOPMENTSPRODUCT LAUNCHES & ENHANCEMENTSDEALS
- 12.1 INTRODUCTION
-
12.2 KEY PLAYERSPALO ALTO NETWORKS- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewCHECK POINT- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewBROADCOM- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewFORTINET- Business overview- Products/Solutions/Services offered- Recent developments- MNM viewCISCO- Business overview- Products/Solutions/Services offered- Recent developments- MnM viewVMWARE- Business overview- Products/Solutions/Services offered- Recent developmentsCITRIX- Business overview- Products/Solutions/Services offered- Recent developmentsZSCALER- Business overview- Products/Solutions/Services offered- Recent developmentsCLOUDFLARE- Business overview- Products/Solutions/Services offered- Recent developmentsFORCEPOINT- Business overview- Products/Solutions/Services offered- Recent developmentsAKAMAIJUNIPER NETWORKSNETSKOPETREND MICROPROOFPOINTBARRACUDASOPHOSSONICWALLINFOBLOXOPEN SYSTEMSF5LOOKOUTIBOSS
-
12.3 SMES/STARTUPSVERSA NETWORKSMENLO SECURITYCATO NETWORKSPERIMETER 81SKYHIGH SECURITYAXIS SECURITYTWINGATEWEBSCALEARYAKAGRIP SECURITY
-
13.1 INTRODUCTIONRELATED MARKET
- 13.2 SECURE ACCESS SERVICE EDGE MARKET
- 13.3 EDGE COMPUTING MARKET
- 14.1 DISCUSSION GUIDE
- 14.2 KNOWLEDGESTORE: MARKETSANDMARKETS’ SUBSCRIPTION PORTAL
- 14.3 CUSTOMIZATION OPTIONS
- 14.4 RELATED REPORTS
- 14.5 AUTHOR DETAILS
- TABLE 1 US DOLLAR EXCHANGE RATE, 2018–2021
- TABLE 2 LIST OF KEY PRIMARY INTERVIEW PARTICIPANTS
- TABLE 3 FACTOR ANALYSIS
- TABLE 4 PERIMETER 81: PRICING ANALYSIS OF VENDORS IN EDGE SECURITY MARKET
- TABLE 5 TWINGATE: PRICING ANALYSIS OF VENDORS IN MARKET
- TABLE 6 TOP TEN PATENT APPLICANTS (US)
- TABLE 7 EDGE SECURITY MARKET: PATENTS
- TABLE 8 MARKET: PORTER’S FIVE FORCES ANALYSIS
- TABLE 9 EDGE SECURITY MARKET: KEY CONFERENCES AND EVENTS IN 2022–2023
- TABLE 10 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 11 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 12 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 13 REST OF WORLD: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 14 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR END USERS (%)
- TABLE 15 KEY BUYING CRITERIA FOR END USERS
- TABLE 16 EDGE SECURITY MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 17 MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 18 MARKET, BY SOLUTION, 2018–2021 (USD MILLION)
- TABLE 19 EDGE SECURITY MARKET, BY SOLUTION, 2022–2027 (USD MILLION)
- TABLE 20 CLOUD ACCESS SECURITY BROKER: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 21 CLOUD ACCESS SECURITY BROKER: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 22 SOFTWARE-DEFINED WIDE AREA NETWORK: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 23 SOFTWARE-DEFINED WIDE AREA NETWORK: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 24 SECURE ACCESS SERVICE EDGE: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 25 SECURE ACCESS SERVICE EDGE: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 26 OTHER SOLUTIONS: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 27 OTHER SOLUTIONS: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 28 EDGE SECURITY MARKET, BY SERVICE, 2018–2021 (USD MILLION)
- TABLE 29 MARKET, BY SERVICE, 2022–2027 (USD MILLION)
- TABLE 30 MARKET, BY PROFESSIONAL SERVICE, 2018–2021 (USD MILLION)
- TABLE 31 MARKET, BY PROFESSIONAL SERVICE, 2022–2027 (USD MILLION)
- TABLE 32 IMPLEMENTATION & INTEGRATION SERVICES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 33 IMPLEMENTATION & INTEGRATION SERVICES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 34 TRAINING & CONSULTING SERVICES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 35 TRAINING & CONSULTING SERVICES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 36 SUPPORT & MAINTENANCE SERVICES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 37 SUPPORT & MAINTENANCE SERVICES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 38 MANAGED SERVICES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 39 MANAGED SERVICES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 40 MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 41 EDGE SECURITY MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 42 LARGE ENTERPRISES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 43 LARGE ENTERPRISES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 44 SMALL AND MEDIUM-SIZED ENTERPRISES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 45 SMALL AND MEDIUM-SIZED ENTERPRISES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 46 EDGE SECURITY MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 47 MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 48 ON-PREMISES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 49 ON-PREMISES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 50 CLOUD: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 51 CLOUD: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 52 EDGE SECURITY MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 53 MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 54 GOVERNMENT & DEFENSE: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 55 GOVERNMENT & DEFENSE: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 56 BANKING, FINANCIAL SERVICES, AND INSURANCE: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 57 BANKING, FINANCIAL SERVICES, AND INSURANCE: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 58 IT & TELECOM: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 59 IT & TELECOM: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 60 HEALTHCARE: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 61 HEALTHCARE: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 62 RETAIL: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 63 RETAIL: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 64 MANUFACTURING: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 65 MANUFACTURING: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 66 ENERGY & UTILITIES: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 67 ENERGY & UTILITIES: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 68 OTHER VERTICALS: MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 69 OTHER VERTICALS: MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 70 EDGE SECURITY MARKET, BY REGION, 2018–2021 (USD MILLION)
- TABLE 71 MARKET, BY REGION, 2022–2027 (USD MILLION)
- TABLE 72 NORTH AMERICA: PESTLE ANALYSIS
- TABLE 73 NORTH AMERICA: EDGE SECURITY MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 74 NORTH AMERICA: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 75 NORTH AMERICA: MARKET, BY SOLUTION, 2018–2021 (USD MILLION)
- TABLE 76 NORTH AMERICA: MARKET, BY SOLUTION, 2022–2027 (USD MILLION)
- TABLE 77 NORTH AMERICA: MARKET, BY SERVICE, 2018–2021 (USD MILLION)
- TABLE 78 NORTH AMERICA: MARKET, BY SERVICE, 2022–2027 (USD MILLION)
- TABLE 79 NORTH AMERICA: MARKET, BY PROFESSIONAL SERVICE, 2018–2021 (USD MILLION)
- TABLE 80 NORTH AMERICA: MARKET, BY PROFESSIONAL SERVICE, 2022–2027 (USD MILLION)
- TABLE 81 NORTH AMERICA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 82 NORTH AMERICA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 83 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 84 NORTH AMERICA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 85 NORTH AMERICA: MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 86 NORTH AMERICA: MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 87 NORTH AMERICA: MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
- TABLE 88 NORTH AMERICA: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
- TABLE 89 US: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 90 US: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 91 US: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 92 US: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 93 US: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 94 US: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 95 CANADA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 96 CANADA: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 97 CANADA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 98 CANADA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 99 CANADA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 100 CANADA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 101 EUROPE: PESTLE ANALYSIS
- TABLE 102 EUROPE: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 103 EUROPE: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 104 EUROPE: MARKET, BY SOLUTION, 2018–2021 (USD MILLION)
- TABLE 105 EUROPE: MARKET, BY SOLUTION, 2022–2027 (USD MILLION)
- TABLE 106 EUROPE: MARKET, BY SERVICE, 2018–2021 (USD MILLION)
- TABLE 107 EUROPE: MARKET, BY SERVICE, 2022–2027 (USD MILLION)
- TABLE 108 EUROPE: MARKET, BY PROFESSIONAL SERVICE, 2018–2021 (USD MILLION)
- TABLE 109 EUROPE: MARKET, BY PROFESSIONAL SERVICE, 2022–2027 (USD MILLION)
- TABLE 110 EUROPE: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 111 EUROPE: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 112 EUROPE: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 113 EUROPE: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 114 EUROPE: MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 115 EUROPE: MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 116 EUROPE: MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
- TABLE 117 EUROPE: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
- TABLE 118 UK: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 119 UK: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 120 UK: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 121 UK: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 122 UK: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 123 UK: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 124 GERMANY: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 125 GERMANY: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 126 GERMANY: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 127 GERMANY: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 128 GERMANY: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 129 GERMANY: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 130 FRANCE: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 131 FRANCE: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 132 FRANCE: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 133 FRANCE: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 134 FRANCE: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 135 FRANCE: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 136 REST OF EUROPE: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 137 REST OF EUROPE: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 138 REST OF EUROPE: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 139 REST OF EUROPE: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 140 REST OF EUROPE: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 141 REST OF EUROPE: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 142 ASIA PACIFIC: PESTLE ANALYSIS
- TABLE 143 ASIA PACIFIC: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 144 ASIA PACIFIC: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 145 ASIA PACIFIC: MARKET, BY SOLUTION, 2018–2021 (USD MILLION)
- TABLE 146 ASIA PACIFIC: MARKET, BY SOLUTION, 2022–2027 (USD MILLION)
- TABLE 147 ASIA PACIFIC: MARKET, BY SERVICE, 2018–2021 (USD MILLION)
- TABLE 148 ASIA PACIFIC: MARKET, BY SERVICE, 2022–2027 (USD MILLION)
- TABLE 149 ASIA PACIFIC: MARKET, BY PROFESSIONAL SERVICE, 2018–2021 (USD MILLION)
- TABLE 150 ASIA PACIFIC: MARKET, BY PROFESSIONAL SERVICE, 2022–2027 (USD MILLION)
- TABLE 151 ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 152 ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 153 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 154 ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 155 ASIA PACIFIC: MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 156 ASIA PACIFIC: MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 157 ASIA PACIFIC: MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
- TABLE 158 ASIA PACIFIC: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
- TABLE 159 CHINA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 160 CHINA: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 161 CHINA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 162 CHINA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 163 CHINA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 164 CHINA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 165 JAPAN: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 166 JAPAN: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 167 JAPAN: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 168 JAPAN: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 169 JAPAN: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 170 JAPAN: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 171 AUSTRALIA & NEW ZEALAND: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 172 AUSTRALIA & NEW ZEALAND: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 173 AUSTRALIA & NEW ZEALAND: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 174 AUSTRALIA & NEW ZEALAND: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 175 AUSTRALIA & NEW ZEALAND: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 176 AUSTRALIA & NEW ZEALAND: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 177 REST OF ASIA PACIFIC: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 178 REST OF ASIA PACIFIC: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 179 REST OF ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 180 REST OF ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 181 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 182 REST OF ASIA PACIFIC: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 183 MIDDLE EAST & AFRICA: PESTLE ANALYSIS
- TABLE 184 MIDDLE EAST & AFRICA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 185 MIDDLE EAST & AFRICA: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 186 MIDDLE EAST & AFRICA: MARKET, BY SOLUTION, 2018–2021 (USD MILLION)
- TABLE 187 MIDDLE EAST & AFRICA: MARKET, BY SOLUTION, 2022–2027 (USD MILLION)
- TABLE 188 MIDDLE EAST & AFRICA: MARKET, BY SERVICE, 2018–2021 (USD MILLION)
- TABLE 189 MIDDLE EAST & AFRICA: MARKET, BY SERVICE, 2022–2027 (USD MILLION)
- TABLE 190 MIDDLE EAST & AFRICA: MARKET, BY PROFESSIONAL SERVICE, 2018–2021 (USD MILLION)
- TABLE 191 MIDDLE EAST & AFRICA: MARKET, BY PROFESSIONAL SERVICE, 2022–2027 (USD MILLION)
- TABLE 192 MIDDLE EAST & AFRICA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 193 MIDDLE EAST & AFRICA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 194 MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 195 MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 196 MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 197 MIDDLE EAST & AFRICA: MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 198 MIDDLE EAST & AFRICA: MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
- TABLE 199 MIDDLE EAST & AFRICA: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
- TABLE 200 UAE: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 201 UAE: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 202 UAE: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 203 UAE: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 204 UAE: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 205 UAE: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 206 SAUDI ARABIA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 207 SAUDI ARABIA: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 208 SAUDI ARABIA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 209 SAUDI ARABIA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 210 SAUDI ARABIA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 211 SAUDI ARABIA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 212 SOUTH AFRICA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 213 SOUTH AFRICA: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 214 SOUTH AFRICA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 215 SOUTH AFRICA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 216 SOUTH AFRICA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 217 SOUTH AFRICA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 218 REST OF MIDDLE EAST & AFRICA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 219 REST OF MIDDLE EAST & AFRICA: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 220 REST OF MIDDLE EAST & AFRICA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 221 REST OF MIDDLE EAST & AFRICA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 222 REST OF MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 223 REST OF MIDDLE EAST & AFRICA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 224 LATIN AMERICA: PESTLE ANALYSIS
- TABLE 225 LATIN AMERICA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 226 LATIN AMERICA: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 227 LATIN AMERICA: MARKET, BY SOLUTION, 2018–2021 (USD MILLION)
- TABLE 228 LATIN AMERICA: MARKET, BY SOLUTION, 2022–2027 (USD MILLION)
- TABLE 229 LATIN AMERICA: MARKET, BY SERVICE, 2018–2021 (USD MILLION)
- TABLE 230 LATIN AMERICA: MARKET, BY SERVICE, 2022–2027 (USD MILLION)
- TABLE 231 LATIN AMERICA: MARKET, BY PROFESSIONAL SERVICE, 2018–2021 (USD MILLION)
- TABLE 232 LATIN AMERICA: MARKET, BY PROFESSIONAL SERVICE, 2022–2027 (USD MILLION)
- TABLE 233 LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 234 LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 235 LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 236 LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 237 LATIN AMERICA: MARKET, BY VERTICAL, 2018–2021 (USD MILLION)
- TABLE 238 LATIN AMERICA: MARKET, BY VERTICAL, 2022–2027 (USD MILLION)
- TABLE 239 LATIN AMERICA: MARKET, BY COUNTRY, 2018–2021 (USD MILLION)
- TABLE 240 LATIN AMERICA: MARKET, BY COUNTRY, 2022–2027 (USD MILLION)
- TABLE 241 BRAZIL: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 242 BRAZIL: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 243 BRAZIL: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 244 BRAZIL: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 245 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 246 BRAZIL: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 247 MEXICO: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 248 MEXICO: MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 249 MEXICO: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 250 MEXICO: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 251 MEXICO: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 252 MEXICO: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 253 REST OF LATIN AMERICA: MARKET, BY COMPONENT, 2018–2021 (USD MILLION)
- TABLE 254 REST OF LATIN AMERICA: EDGE SECURITY MARKET, BY COMPONENT, 2022–2027 (USD MILLION)
- TABLE 255 REST OF LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 2018–2021 (USD MILLION)
- TABLE 256 REST OF LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 2022–2027 (USD MILLION)
- TABLE 257 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2018–2021 (USD MILLION)
- TABLE 258 REST OF LATIN AMERICA: MARKET, BY DEPLOYMENT MODE, 2022–2027 (USD MILLION)
- TABLE 259 OVERVIEW OF STRATEGIES ADOPTED BY KEY EDGE SECURITY VENDORS
- TABLE 260 MARKET: DEGREE OF COMPETITION
- TABLE 261 COMPANY EVALUATION QUADRANT: CRITERIA
- TABLE 262 COMPANY PRODUCT FOOTPRINT
- TABLE 263 COMPANY COMPONENT FOOTPRINT
- TABLE 264 COMPANY VERTICAL FOOTPRINT
- TABLE 265 COMPANY REGION FOOTPRINT
- TABLE 266 EDGE SECURITY MARKET: DETAILED LIST OF KEY STARTUP/SMES
- TABLE 267 STARTUP/SME: PRODUCT FOOTPRINT
- TABLE 268 STARTUP/SME: COMPONENT FOOTPRINT
- TABLE 269 STARTUP/SME: VERTICAL FOOTPRINT
- TABLE 270 STARTUP/SME: REGION FOOTPRINT
- TABLE 271 PRODUCT LAUNCHES & ENHANCEMENTS, 2020–2022
- TABLE 272 DEALS, 2020–2022
- TABLE 273 PALO ALTO NETWORKS: BUSINESS OVERVIEW
- TABLE 274 PALO ALTO NETWORKS: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 275 PALO ALTO NETWORKS: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 276 PALO ALTO NETWORKS: DEALS
- TABLE 277 CHECK POINT: BUSINESS OVERVIEW
- TABLE 278 CHECK POINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 279 CHECK POINT: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 280 CHECK POINT: DEALS
- TABLE 281 BROADCOM: BUSINESS OVERVIEW
- TABLE 282 BROADCOM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 283 BROADCOM: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 284 BROADCOM: DEALS
- TABLE 285 FORTINET: BUSINESS OVERVIEW
- TABLE 286 FORTINET: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 287 FORTINET: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 288 FORTINET: DEALS
- TABLE 289 CISCO: BUSINESS OVERVIEW
- TABLE 290 CISCO: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 291 CISCO: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 292 CISCO: DEALS
- TABLE 293 VMWARE: BUSINESS OVERVIEW
- TABLE 294 VMWARE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 295 VMWARE: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 296 VMWARE: DEALS
- TABLE 297 CITRIX: BUSINESS OVERVIEW
- TABLE 298 CITRIX: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 299 CITRIX: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 300 ZSCALER: BUSINESS OVERVIEW
- TABLE 301 ZSCALER: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 302 ZSCALER: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 303 ZSCALER: DEALS
- TABLE 304 CLOUDFLARE: BUSINESS OVERVIEW
- TABLE 305 CLOUDFLARE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 306 CLOUDFLARE: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 307 CLOUDFLARE: DEALS
- TABLE 308 FORCEPOINT: BUSINESS OVERVIEW
- TABLE 309 FORCEPOINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 310 FORCEPOINT: PRODUCT LAUNCHES AND ENHANCEMENTS
- TABLE 311 FORCEPOINT: DEALS
- TABLE 312 SECURE ACCESS SERVICE EDGE MARKET, BY OFFERING, 2016–2020 (USD MILLION)
- TABLE 313 SECURE ACCESS SERVICE EDGE MARKET, BY OFFERING, 2021–2026 (USD MILLION)
- TABLE 314 SECURE ACCESS SERVICE EDGE MARKET, BY ORGANIZATION SIZE, 2016–2020 (USD MILLION)
- TABLE 315 SECURE ACCESS SERVICE EDGE MARKET, BY ORGANIZATION SIZE, 2021–2026 (USD MILLION)
- TABLE 316 SECURE ACCESS SERVICE EDGE MARKET, BY VERTICAL, 2016–2020 (USD MILLION)
- TABLE 317 SECURE ACCESS SERVICE EDGE MARKET, BY VERTICAL, 2021–2026 (USD MILLION)
- TABLE 318 SECURE ACCESS SERVICE EDGE MARKET, BY REGION, 2016–2020 (USD MILLION)
- TABLE 319 SECURE ACCESS SERVICE EDGE MARKET, BY REGION, 2021–2026 (USD MILLION)
- TABLE 320 EDGE COMPUTING MARKET, BY COMPONENT, 2016–2020 (USD MILLION)
- TABLE 321 EDGE COMPUTING MARKET, BY COMPONENT, 2021–2027 (USD MILLION)
- TABLE 322 EDGE COMPUTING MARKET, BY APPLICATION, 2016–2020 (USD MILLION)
- TABLE 323 EDGE COMPUTING MARKET, BY APPLICATION, 2021–2027 (USD MILLION)
- TABLE 324 EDGE COMPUTING MARKET, BY ORGANIZATION SIZE, 2016–2020 (USD MILLION)
- TABLE 325 EDGE COMPUTING MARKET, BY ORGANIZATION SIZE, 2021–2027 (USD MILLION)
- TABLE 326 EDGE COMPUTING MARKET, BY VERTICAL, 2016–2020 (USD MILLION)
- TABLE 327 EDGE COMPUTING MARKET, BY VERTICAL, 2021–2027 (USD MILLION)
- TABLE 328 EDGE COMPUTING MARKET, BY REGION, 2016–2020 (USD MILLION)
- TABLE 329 EDGE COMPUTING MARKET, BY REGION, 2021–2027 (USD MILLION)
- FIGURE 1 EDGE SECURITY MARKET: RESEARCH DESIGN
- FIGURE 2 BREAKUP OF PRIMARY INTERVIEWS: BY COMPANY TYPE, DESIGNATION, AND REGION
- FIGURE 3 DATA TRIANGULATION
- FIGURE 4 EDGE SECURITY MARKET: TOP-DOWN AND BOTTOM-UP APPROACHES
- FIGURE 5 MARKET SIZE ESTIMATION METHODOLOGY – APPROACH 1 (SUPPLY SIDE): REVENUE OF SOLUTIONS AND SERVICES FROM EDGE SECURITY VENDORS
- FIGURE 6 MARKET SIZE ESTIMATION METHODOLOGY: BOTTOM-UP APPROACH (SUPPLY SIDE): COLLECTIVE REVENUE OF EDGE SECURITY VENDORS
- FIGURE 7 MARKET SIZE ESTIMATION METHODOLOGY – (SUPPLY SIDE): CAGR PROJECTIONS FROM SUPPLY SIDE
- FIGURE 8 MARKET SIZE ESTIMATION METHODOLOGY ? BOTTOM-UP: REVENUE GENERATED BY EDGE SECURITY VENDORS FROM EACH COMPONENT
- FIGURE 9 MARKET SIZE ESTIMATION METHODOLOGY–APPROACH 2 (DEMAND SIDE): REVENUE GENERATED FROM DIFFERENT EDGE SECURITY SOLUTIONS
- FIGURE 10 GLOBAL EDGE SECURITY MARKET, 2019–2027 (USD MILLION)
- FIGURE 11 FASTEST-GROWING SEGMENTS IN MARKET, 2022–2027
- FIGURE 12 SOLUTIONS SEGMENT TO ACCOUNT FOR LARGER MARKET SIZE DURING FORECAST PERIOD
- FIGURE 13 SASE SEGMENT TO ACCOUNT FOR LARGEST MARKET SIZE IN 2027
- FIGURE 14 PROFESSIONAL SERVICES SEGMENT TO ACCOUNT FOR LARGER MARKET SIZE DURING FORECAST PERIOD
- FIGURE 15 IMPLEMENTATION & INTEGRATION SEGMENT TO ACCOUNT FOR LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 16 LARGE ENTERPRISES SEGMENT TO ACCOUNT FOR LARGER MARKET SIZE DURING FORECAST PERIOD
- FIGURE 17 TOP VERTICALS IN EDGE SECURITY MARKET
- FIGURE 18 EDGE SECURITY MARKET: REGIONAL SNAPSHOT
- FIGURE 19 PROLIFERATION OF EDGE DEVICES AND CLOUD SOLUTIONS TO BOOST EDGE SECURITY MARKET
- FIGURE 20 SOLUTIONS SEGMENT TO ACCOUNT FOR LARGER MARKET SHARE DURING FORECAST PERIOD
- FIGURE 21 SD-WAN SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE IN 2022
- FIGURE 22 PROFESSIONAL SERVICES SEGMENT TO ACCOUNT FOR LARGER MARKET SHARE DURING FORECAST PERIOD
- FIGURE 23 IMPLEMENTATION & INTEGRATION SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE DURING FORECAST PERIOD
- FIGURE 24 LARGE ENTERPRISES SEGMENT TO ACCOUNT FOR LARGER MARKET SHARE DURING FORECAST PERIOD
- FIGURE 25 CLOUD SEGMENT TO ACCOUNT FOR LARGER MARKET SHARE DURING FORECAST PERIOD
- FIGURE 26 BANKING, FINANCIAL SERVICES, AND INSURANCE SEGMENT TO ACCOUNT FOR LARGEST MARKET SHARE DURING FORECAST PERIOD
- FIGURE 27 ASIA PACIFIC TO EMERGE AS BEST MARKET FOR INVESTMENTS IN NEXT FIVE YEARS
- FIGURE 28 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES: EDGE SECURITY MARKET
- FIGURE 29 EDGE NETWORK ENVIRONMENT TO SUPPORT PRIMARY USE CASES
- FIGURE 30 COMBINED INVESTMENT ALLOCATED TO SECURITY BY INDUSTRY
- FIGURE 31 FACTORS IMPACTING ADOPTION OF SASE ARCHITECTURE IN ORGANIZATIONS
- FIGURE 32 MOBILE SUBSCRIPTIONS BY REGION AND TECHNOLOGY, 2022 VS 2028
- FIGURE 33 INTERNET OF THINGS AND EDGE SOLUTIONS TO DRIVE IMPACT ACROSS MULTIPLE BUSINESS FUNCTIONS
- FIGURE 34 EDGE SECURITY MARKET: SUPPLY CHAIN
- FIGURE 35 EDGE SECURITY MARKET: ECOSYSTEM
- FIGURE 36 NUMBER OF PATENTS PUBLISHED, 2011–2021
- FIGURE 37 TOP FIVE PATENT OWNERS (GLOBAL)
- FIGURE 38 EDGE SECURITY MARKET: PORTER’S FIVE FORCES ANALYSIS
- FIGURE 39 EDGE SECURITY MARKET: TRENDS/DISRUPTIONS IMPACTING BUYERS
- FIGURE 40 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR END USERS
- FIGURE 41 KEY BUYING CRITERIA FOR END USERS
- FIGURE 42 SERVICES SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 43 SASE SEGMENT TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 44 MANAGED SERVICES SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 45 SUPPORT & MAINTENANCE SEGMENT TO GROW AT HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 46 SMALL AND MEDIUM-SIZED ENTERPRISES SEGMENT TO GROW AT HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 47 CLOUD DEPLOYMENT MODE TO RECORD HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 48 BANKING, FINANCIAL SERVICES, AND INSURANCE SEGMENT TO GROW AT LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 49 NORTH AMERICA TO HOLD LARGEST MARKET SIZE DURING FORECAST PERIOD
- FIGURE 50 NORTH AMERICA: MARKET SNAPSHOT
- FIGURE 51 ASIA PACIFIC: MARKET SNAPSHOT
- FIGURE 52 MARKET EVALUATION FRAMEWORK, 2020–2022
- FIGURE 53 HISTORICAL FOUR-YEAR REVENUE ANALYSIS OF LEADING PLAYERS, 2018–2021 (USD BILLION)
- FIGURE 54 EDGE SECURITY MARKET: MARKET SHARE ANALYSIS, 2021
- FIGURE 55 EDGE SECURITY MARKET: KEY COMPANY EVALUATION QUADRANT, 2022
- FIGURE 56 RANKING OF KEY PLAYERS IN EDGE SECURITY MARKET, 2021
- FIGURE 57 STARTUP/SME EVALUATION MATRIX: CRITERIA WEIGHTAGE
- FIGURE 58 EDGE SECURITY MARKET (GLOBAL): STARTUP/SME COMPANY EVALUATION QUADRANT, 2022
- FIGURE 59 PALO ALTO NETWORKS: COMPANY SNAPSHOT
- FIGURE 60 CHECK POINT: COMPANY SNAPSHOT
- FIGURE 61 BROADCOM: COMPANY SNAPSHOT
- FIGURE 62 FORTINET: COMPANY SNAPSHOT
- FIGURE 63 CISCO: COMPANY SNAPSHOT
- FIGURE 64 VMWARE: COMPANY SNAPSHOT
- FIGURE 65 ZSCALER: COMPANY SNAPSHOT
- FIGURE 66 CLOUDFLARE: COMPANY SNAPSHOT
The study involved four major activities in estimating the current market size of the edge security market. Extensive secondary research was done to collect information on the market, the competitive market, and the parent market. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain through primary research. Both top-down and bottom-up approaches were employed to estimate the complete market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the various segments in the edge security market.
Secondary Research
This research study used extensive secondary sources, directories, and databases, such as D&B Hoovers, DiscoverOrg, Factiva, vendor data sheets, product demos, Cloud Computing Association (CCA), Vendor Surveys, Asia Cloud Computing Association, and The Software Alliance. All these sources were referred to for identifying and collecting information useful for this technical, market-oriented, and commercial study of the edge security market.
Primary Research
Primary sources were several industry experts from the core and related industries, preferred software providers, hardware manufacturers, distributors, service providers, technology developers, alliances, and organizations related to all segments of the industry’s value chain. In-depth interviews were conducted with various primary respondents, including key industry participants, subject-matter experts, C-level executives of key market players, and industry consultants, to obtain and verify critical qualitative and quantitative information and assess the market’s prospects.
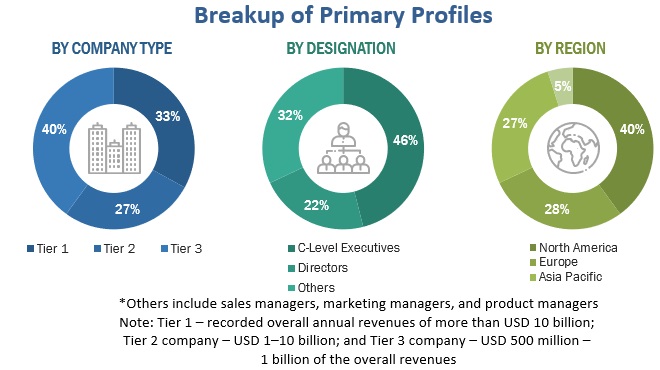
The following figure depicts the breakup of the primary profiles:
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
The bottom-up and top-down approaches were utilized to estimate and validate the total edge security market. They were also used extensively to estimate the size of various subsegments in the market. The research methodology used to estimate the market size includes the following:
- The key players in the industry and markets have been identified through paid and unpaid secondary resources.
- The industry’s supply chain and market size, in terms of value, have been determined through primary and secondary research processes.
- All percentage shares, splits, and breakdowns have been determined using secondary sources and verified through primary sources.
Data Triangulation
After arriving at the overall market size using the market size estimation processes as explained above the market was split into several segments and subsegments. To complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment, data triangulation and market breakup procedures were employed, wherever applicable. The data was triangulated by studying several factors and trends from both the demand and supply sides, in the edge security market.
Report Objectives
- To define, describe, and forecast the edge security market based on component, deployment mode, organization size, industry vertical, and region.
- To provide detailed information about the major factors (drivers, restraints, opportunities, and industry-specific challenges) influencing the growth of the market
- To analyze the market with respect to individual growth trends, prospects, and contributions to the overall market
- To analyze the impact of the recession on the global market
- To forecast the market size of main regions: North America, Europe, Asia Pacific (APAC), Middle East & Africa (MEA), and Latin America
- To analyze the opportunities in the market for stakeholders by identifying the high-growth segments of the market
- To profile the key players in the edge security market and comprehensively analyze their core competencies in each subsegment.
- To track and analyze competitive developments, such as mergers and acquisitions, new product launches, and partnerships and collaborations, in the market.
Available Customizations
With the given market data, MarketsandMarkets offers customizations per the company’s specific needs and on best effort basis for profiling additional market players.



 Generating Response ...
Generating Response ...










Growth opportunities and latent adjacency in Edge Security Market