
Security Testing Market
Security Testing Market by Type (Network, Application, Device, Social Engineering), Network Security Testing (Penetration Testing, Vulnerability Scanning, Firewall), Application Testing Tool (RASP, SAST, DAST, IAST) - Global Forecast to 2031




OVERVIEW
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
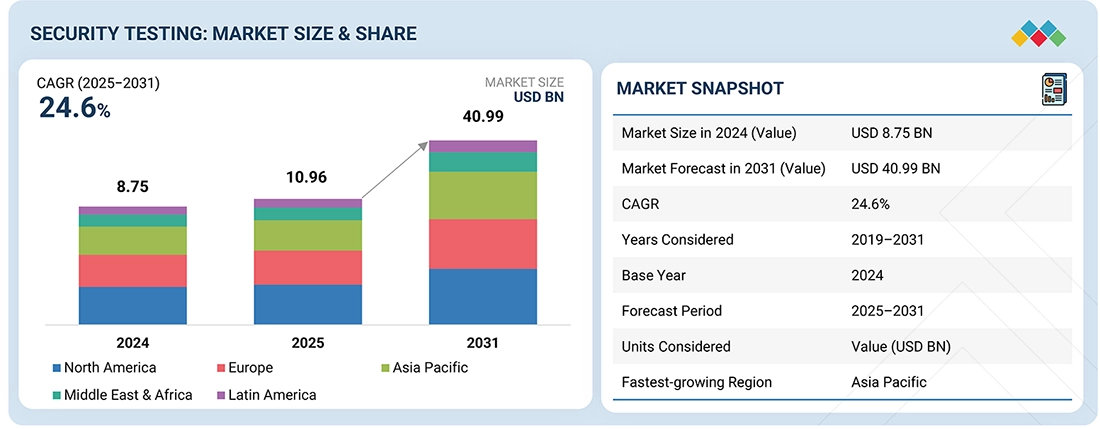
The security testing market is projected to reach USD 40.99 billion by 2031 from USD 10.96 billion in 2025, at a CAGR of 24.6% from 2025 to 2031. The high rate of adoption of web and mobile applications drives the market as it expands the application attack surface and exposes organizations to more vulnerabilities that can be exploited by cyberattacks. This compels organizations to invest in continuous security testing. Simultaneously, the growing use of third-party and open-source components also creates software supply chain risks, where vulnerabilities in external libraries may be brought into an application. This can lead to the need to use security testing solutions to detect, evaluate, and address these vulnerabilities at all stages of the development process.
KEY TAKEAWAYS
-
BY REGIONNorth America accounted for the largest market share in 2025.
-
BY SECURITY TESTING TYPEThe network security type segment is expected to dominate the market in terms of market share in 2025.
-
BY NETWORK SECURITY TESTING TYPEThe WiFi/wireless security testing segment is expected to grow at the highest CAGR during the forecast period.
-
BY APPLICATION SECURITY TESTING TYPEThe mobile application security testing segment is expected to be the fastest-growing during the forecast period.
-
BY APPLICATION SECURITY TESTING TOOLThe interactive application security testing (IAST) segment is expected to grow at the highest rate during the forecast period.
-
BY DEPLOYMENT MODEThe on-premises segment is expected to dominate the market in terms of market share during the forecast period.
-
BY ORGANIZATION SIZEThe SMEs segment will grow at the highest CAGR.
-
BY VERTICALThe healthcare segment will grow the fastest during the forecast period.
-
COMPETITIVE LANDSCAPE - KEY PLAYERSIBM, Cigniti Technologies (Coforge), and Black Duck dominate the security testing market, with platforms of application security testing that combine SAST, DAST, SCA, and DevSecOps features to assist enterprises in identifying vulnerabilities at the earliest stage and securing modern software development processes.
-
COMPETITIVE LANDSCAPE - STARTUPSInvicti, BreachLock, and Cobalt are emerging innovators, with automated, cloud-based, and penetration-testing-as-a-service designs that respond to the emerging and increasing need to scale security testing continuously and cost-effectively among mid-sized and fast-growing companies.
There is an increasing pressure on organizations to guarantee the integrity and security of multifaceted software ecosystems constituted of numerous external dependencies. With an increasingly modular and interconnected application environment, security testing is increasingly important in offering a view into the concealed vulnerabilities, validating code quality, and assisting in proactive risk management throughout the software development and deployment life cycle.
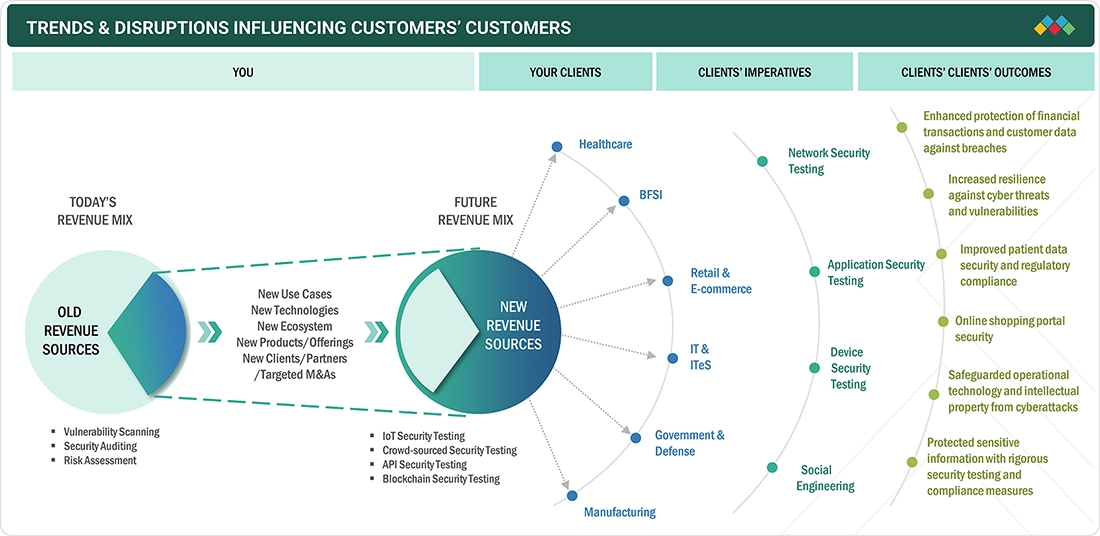
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
Since enterprises are moving beyond simple vulnerability scanning to more complex testing use cases, new technologies, wider ecosystems, and wider industry adoption are helping revenue grow. Increased demands in BFSI, healthcare, retail, and government industries are accelerating investments in end-to-end security testing to increase resilience, regulatory adherence, and protection of sensitive data and critical digital processes.
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Rapid adoption of web and mobile applications vulnerable to cyberattacks

-
Increasing reliance on third-party and open-source components
Level
-
High false-positive rates from automated testing tools
Level
-
Increased adoption of cloud-based security testing
-
Growth of Security Testing as a Service (STaaS)
Level
-
Fragmentation of security testing tools and platforms
-
Lack of skilled cybersecurity professionals
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Rapid adoption of web and mobile applications vulnerable to cyberattacks
The rapid use of web and mobile applications is increasing enterprise attack surfaces. Veracode notes that more than 70% of the applications scanned by the company in the last evaluations had at least one vulnerability upon release. The exposure to vulnerability is rising with the frequent updates and short release cycles, which are forcing organizations to invest in ongoing security testing to safeguard customer data and digital services.
Restraint: High false-positive rates from automated testing tools
Automated security testing tools have high false positive rates, which is a major limitation. Checkmarx states that in most cases, security teams identify over 500 issues to be manually verified prior to remediation. This validation process increases the workload of developers, delays release schedules, and decreases the trust in automated testing results in large development systems.
Opportunity: Increased adoption of cloud-based security testing
Cloud-based security testing solutions are getting solid opportunities due to cloud adoption. Qualys found that most enterprise workloads are now being deployed to cloud environments and many are being distributed across multiple clouds. This change is driving the need to have scalable testing environments that can facilitate centralized visibility, ongoing evaluation, and integration with DevOps pipelines.
Challenge: Fragmentation of security testing tools and platforms
Tool fragmentation in security testing is a prominent challenge to businesses. Rapid7 states that organizations typically have 5 or more distinct security tools at the application and infrastructure layers. Such a fragmented approach makes it difficult to prioritize risks, adds to operational overheads, and reduces the capacity to have a single perspective on security posture.
SECURITY TESTING MARKET: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
Insecure source code, late-stage vulnerability discovery, lack of developer security awareness, slow remediation cycles, and compliance pressure. | Early vulnerability identification, reduced remediation effort, improved secure coding practices, faster release timelines, and lower application risk. |
 |
High false positives, limited visibility into open-source risks, DevSecOps integration challenges, and developer productivity impact. | Accurate vulnerability detection, reduced false positives, improved developer efficiency, and enhanced software security posture. |
 |
Limited visibility into application attack surface, difficulty simulating real-world attacks, and inconsistent security testing frequency. | Improved risk visibility, continuous security validation, faster vulnerability remediation, and reduced breach exposure. |
 |
Unmanaged third-party components, open-source vulnerabilities, license compliance risks, and a lack of supply chain transparency. | Reduced software supply chain risk, improved compliance management, enhanced application integrity, and proactive vulnerability mitigation. |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The security testing ecosystem revolves around application testing, network testing, device testing, and social engineering testing based on the diverse and ever-growing spectrum of threats that modern businesses must contend with. The vendors in these segments provide specialized services and tools to detect vulnerabilities, test security controls, and create simulated real-world attack scenarios. This ecosystem helps organizations to enhance cyber resilience, enhance risk visibility, and secure digital assets in complex, cloud-driven, and highly interconnected environments.

Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
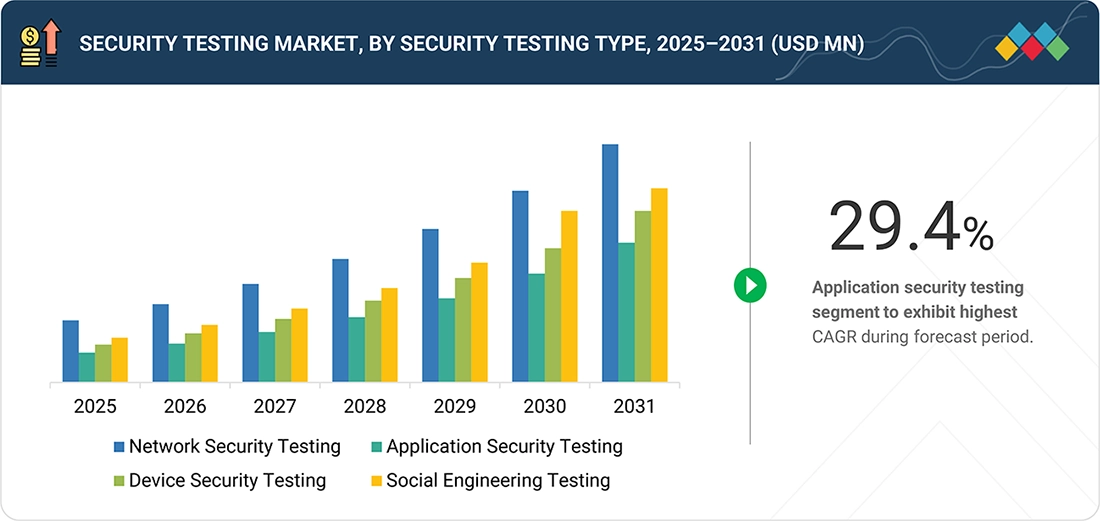
Security Testing Market, By Security Testing Type
Network security testing is the biggest segment because enterprises still focus on the protection of core infrastructure that supports hybrid and multi-cloud environments. In February 2025, according to Qualys, organizations are increasingly concerned with justifying network configurations and exposure paths, as cloud connectivity grows. This continued focus on infrastructure resiliency remains the force behind robust usage of network security testing in industries.
Security Testing Market, By Network Security Testing Type
Network penetration testing takes the lead in network security testing because it can be used to model actual attack scenarios in the real world. Rapid7 states that by March 2025, companies will be using penetration testing to confirm that security controls are more than an automated scan and that they satisfy the regulatory and audit criteria. This validation practice makes network defenses more robust and helps in the ongoing security improvement efforts.
Security Testing Market, By Application Security Testing Type
Web application security testing is the biggest application testing segment because web applications constitute the main digital frontier of customers and partners. OWASP reports that in January 2025, web-based vulnerabilities were still being reported as the most prevalent application risks. This constant exposure compels organizations to focus on constant testing of the production web applications and interfaces.
Security Testing Market, By Application Security Testing Tool
Static application security testing (SAST) leads among testing tools as organizations seek to identify vulnerabilities early in the development lifecycle. According to Checkmarx, in April 2025, development teams increasingly integrated SAST into CI pipelines to reduce downstream remediation efforts. Early code-level detection supports secure development practices and accelerates application release cycles.
Security Testing Market, By Deployment Mode
On-premises deployment continues to dominate as organizations in regulated sectors prioritize control over sensitive testing data. According to IBM, in May 2025, enterprises in banking and government environments favored on-premises security testing to meet data residency and compliance requirements. Legacy application environments also reinforce the continued relevance of on-premises deployments.
Security Testing, By Organization Size
Large enterprises represent the largest adopter segment due to their complex digital environments and regulatory exposure. According to Veracode, in February 2025, large organizations conducted security testing more frequently across development stages to manage risk at scale. Their need for continuous validation across multiple applications sustains higher adoption of security testing solutions.
Security Testing Market, By Vertical
The BFSI vertical leads security testing adoption due to strict regulatory oversight and high exposure to cyber threats. According to Synopsys, in March 2025, financial institutions continued to identify vulnerabilities across both proprietary and third-party software components. This persistent risk environment drives consistent investment in application and network security testing.
REGION
Asia Pacific to be the fastest-growing region in the global security testing market during the forecast period.
The Asia Pacific region is the fastest-growing market for security testing, driven by rapid digitalization, cloud adoption, and expanding web and mobile application usage across enterprises. According to IBM, in April 2025, organizations in the Asia Pacific region reported rising security risks linked to accelerated application deployment and hybrid IT environments. Growing regulatory focus on data protection, increasing cyber incidents, and strong investments by BFSI, government, and technology sectors are accelerating demand for comprehensive security testing solutions across the region.

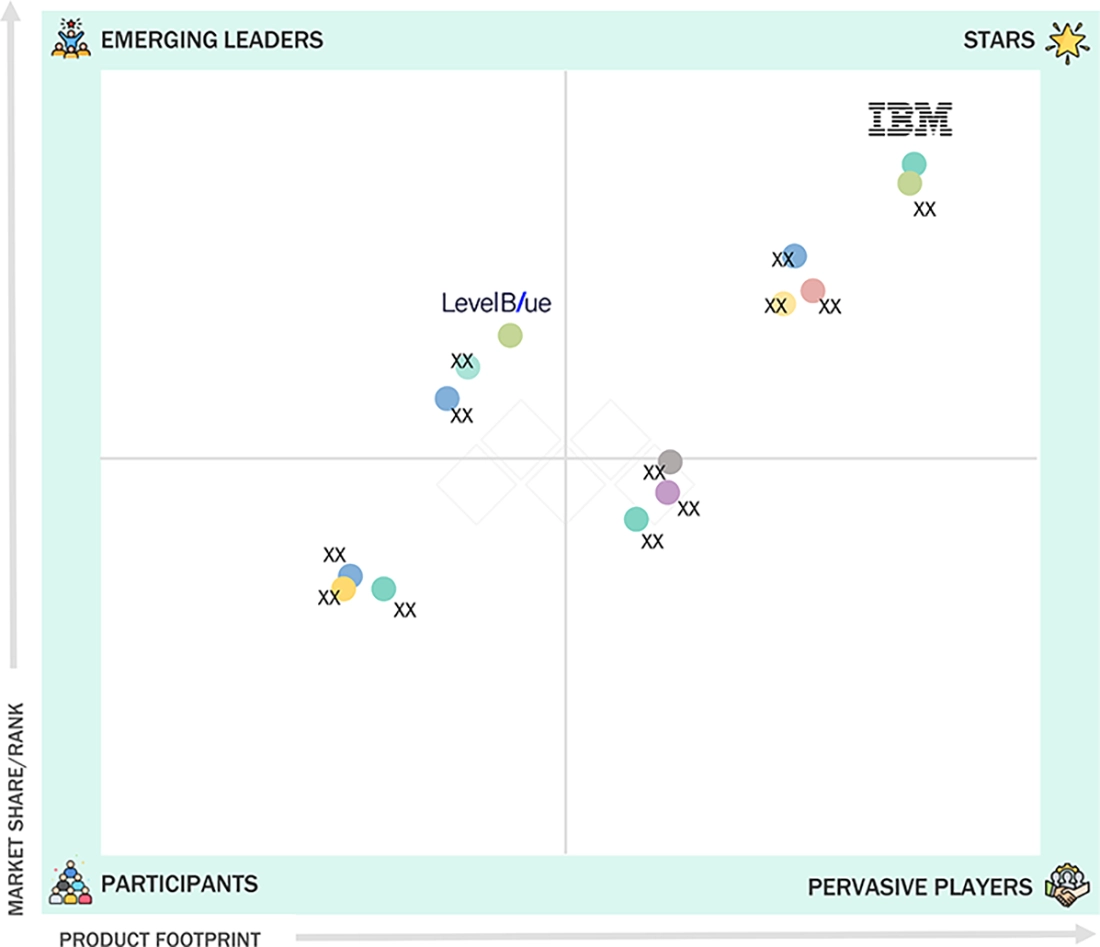
SECURITY TESTING MARKET: COMPANY EVALUATION MATRIX
In the security testing market matrix, IBM (Star Player) leads with its broad security testing portfolio that spans network, application, and infrastructure testing, supported by strong consulting expertise, global delivery capabilities, and deep integration with enterprise security and risk frameworks. LevelBlue (Trustwave) (Emerging Player) is gaining traction by expanding its security testing and managed security services through cloud-driven platforms, threat intelligence capabilities, and strong expertise in penetration testing and compliance-driven security assessments, aligned with evolving enterprise cybersecurity needs.
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
- IBM (US)
- OpenText (Canada)
- Cigniti Technologies (Coforge) (India)
- Intertek (UK)
- Qualitest (UK)
- Intertek (UK)
- HCLTech (India)
- Black Duck (US)
- DXC Technology (US)
- eInfochips (US)
- Checkmarx (US)
- Qualys (US)
- HackerOne (US)
- Invicti (US)
- DataArt (US)
- Cobalt (US)
- Contrast Security (US)
- Veracode (US)
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size in 2024 (Value) | USD 8.75 Billion |
| Market Forecast in 2031 (Value) | USD 40.99 Billion |
| Growth Rate | CAGR of 24.6% during 2025-2031 |
| Years Considered | 2019-2031 |
| Base Year | 2024 |
| Forecast Period | 2025-2031 |
| Units Considered | Value (USD Billion) |
| Report Coverage | Revenue forecast, company ranking, competitive landscape, growth factors, and trends |
| Segments Covered |
|
| Regions Covered | North America, Europe, Asia Pacific, Middle East & Africa, Latin America |
WHAT IS IN IT FOR YOU: SECURITY TESTING MARKET REPORT CONTENT GUIDE
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Leading Solution Provider (US) | Product Analysis: Security Testing Matrix providing an in-depth comparison of leading vendors’ capabilities, including application security testing (SAST, DAST, SCA), network and penetration testing, cloud and API security testing, automation and CI/CD integration, reporting and analytics, compliance alignment, and on-premises and cloud deployment flexibility. | Stronger understanding of competitive security testing positioning, product breadth, testing depth, automation maturity, and integration capabilities, supporting informed investment decisions, platform consolidation strategies, and long-term application and infrastructure security roadmaps. |
| Leading Service Provider (EU) | Company Information: Detailed profiling and evaluation of additional security testing vendors and service providers (up to 5), covering testing methodologies, penetration testing frameworks, DevSecOps alignment, managed security testing services, industry certifications, regional delivery capabilities, and strategic partnerships across regulated industries and hybrid IT environments. | Comprehensive view of the evolving security testing services landscape, highlighting managed testing growth opportunities, increasing demand for continuous testing, vendor differentiation potential, and expansion areas driven by cloud adoption, regulatory requirements, and enterprise digital transformation initiatives. |
RECENT DEVELOPMENTS
- June 2025 : Rapid7 expanded its managed penetration testing and application security testing services, enabling enterprises to align continuous security validation with agile development and DevSecOps practices.
- March 2024 : HackerOne partnered with enterprise DevSecOps teams to expand continuous crowdsourced security testing programs, supporting the identification of complex and real-world application vulnerabilities beyond automated testing tools.
- February 2025 : Checkmarx introduced advanced cloud-native and API security testing features designed to improve risk visibility across microservices-based architectures and support continuous security testing in DevSecOps environments.
Table of Contents

Methodology
Secondary research was conducted to collect information useful for this technical, market-oriented, and commercial study of the security testing market. The next step involved validating these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, including top-down and bottom-up methods, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and subsegments of the security testing market.
Secondary Research
During the secondary research process, various secondary sources were consulted to identify and collect information relevant to the study. The secondary sources included annual reports, press releases, investor presentations of security testing vendors, forums, certified publications, and whitepapers. The secondary research was mainly used to obtain key information about the industry’s supply chain, the total pool of key players, market classification and segmentation according to industry trends to the bottom-most level, regional markets, and key developments from both market- and technology-oriented perspectives, all of which were further validated by primary sources.
Primary Research
In the primary research process, various primary sources from both the supply and demand sides were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included various industry experts, including chief executive officers (CEOs), vice presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the security testing market.
In the market engineering process, top-down and bottom-up approaches were extensively used, along with several data triangulation methods, to perform market estimation and forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was conducted across the complete market engineering process to present key information/insights throughout the report.
After the complete market engineering process (including calculations for market statistics, market breakups, market size estimations, market forecasts, and data triangulation), extensive primary research was conducted to gather information and verify & validate the critical numbers arrived at. The primary research was also conducted to identify segmentation types, the competitive landscape of security testing market players, and key market dynamics, such as drivers, restraints, opportunities, and challenges, as well as key strategies.
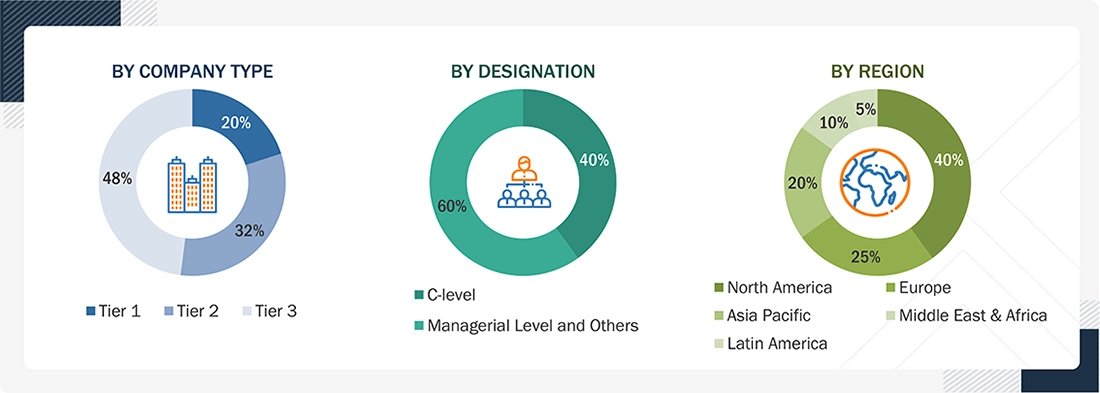
The following is a breakdown of the primary respondents:
Notes:
Tier 1 companies receive revenues higher than USD 10 billion; Tier 2 companies' revenues range between USD 1 and 10 billion; and Tier 3 companies' revenues range between USD 500 million and USD 1 billion.
Other designations include sales, marketing, and product managers.
Source: Industry Experts
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Top-down and bottom-up approaches were employed to estimate and validate the size of the security testing market, as well as the size of various dependent sub-segments within the overall security testing market. The research methodology used to estimate the market size includes the following details: critical players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure involved studying the annual and financial reports of the top market players and conducting extensive interviews with key industry leaders, including CEOs, VPs, directors, and marketing executives, to gather valuable insights.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study were accounted for, examined in detail, verified through primary research, and analyzed to yield final quantitative and qualitative data. This data was consolidated and added to detailed inputs and analysis from MarketsandMarkets.

Source: MarketsandMarkets Analysis
Data Triangulation
The market was split into several segments and subsegments after determining the overall market size using the market sizing processes described above. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
Security testing is an activity that identifies vulnerabilities in software, hardware, and services by using highly automated tools or through manual attacks by skilled information security practitioners. It helps organizations maintain confidentiality, integrity, availability, authentication, authorization, and non-repudiation of sensitive information.
Key Stakeholders
- Chief Technology and Data Officers
- Consulting Service Providers
- Cybersecurity Professionals
- Business Analysts
- Information Technology (IT) Professionals
- Government Agencies
- Investors and Venture Capitalists
- Small and Medium-sized Enterprises (SMEs) and Large Enterprises
- Third-party Providers
- Consultants/Consultancies/Advisory Firms
Report Objectives
- To describe and forecast the security testing market by security testing type, network security testing type, application security testing type, application security testing tool, deployment mode, organization size, vertical, and region from 2025 to 2031, and analyze the various macroeconomic and microeconomic factors that affect market growth
- To forecast the market size of five major regions: North America, Europe, Asia Pacific, the Middle East & Africa, and Latin America
- To analyze the subsegments of the market with respect to individual growth trends, prospects, and contributions to the overall market
- To provide detailed information regarding major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
- To analyze opportunities in the market for stakeholders and provide details of the competitive landscape of major players
- To profile key market players; provide a comparative analysis based on the business overviews, regional presence, product offerings, business strategies, and key financials; and illustrate the competitive landscape of the market
- To analyze competitive developments, such as mergers & acquisitions, product developments, partnerships and collaborations, and research & development (R&D) activities, in the market.
Available customizations:
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
GEOGRAPHIC ANALYSIS
- Further breakup of the Asia Pacific market into countries contributes to the rest of the regional market size.
- Further breakup of the North American market into countries contributes to the rest of the regional market size.
- Further breakup of the Latin American market into countries contributing to the rest of the regional market size.
- Further breakup of the Middle East & African market into countries contributing to the rest of the regional market size.
- Further breakup of the European market into countries contributes to the rest of the regional market size.
Company information
- Detailed analysis and profiling of additional market players (up to 5)
Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the Security Testing Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free Customisation













Growth opportunities and latent adjacency in Security Testing Market