IoT IAM Market by Component (Solutions and Services), Security Type (Network Security, Endpoint Security, Application Security, and Cloud Security), Deployment Mode, Organization Size, Vertical and Region - Global Forecast to 2027
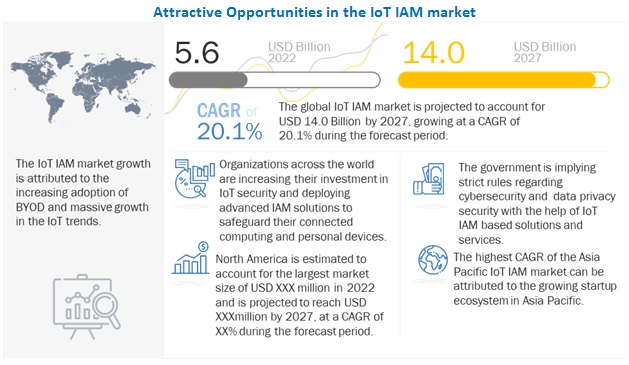
[306 Pages Report] The global IoT IAM market size to grow from USD 5.6 billion in 2022 to USD 14.0 billion by 2027, at a Compound Annual Growth Rate (CAGR) of 20.1% during the forecast period. The increased integration of IAM with IoT devices is driving the IoT IAM market.
To know about the assumptions considered for the study, Request for Free Sample Report
COVID-19 Impact
In a short time, the COVID-19 outbreak has resulted in global lockdown due to which the dependency on digital platform has increased significantly for all businesses across the globe to operate their daily operations. various sectors like healthcare, telecommunication, media and entertainment, utilities, and government verticals function day and night to stabilize conditions and facilitate prerequisite services to every individual. With increasing use of IoT devices, businesses are at a risk of losing their critical corporate data due to weak security infrastructure and increasing cyberattacks, here IoT identity access management strengthens security and businesses control over their corporate data. Thus, COVID-19 has a positive impact in terms of adoption of IoT IAM.
Market Dynamics
Driver: Increased integration of IAM with IoT Devices
IoT has been implemented across all the industry verticals, along with personal and home usage within a very short period. According to the 2016 Symantec Internet Threat Report, there are 25 connected devices per 100 people, and billions of devices are expected to be connected in the upcoming years. IoT has transformed various imaginary tasks into reality, such as smart homes, intelligent industrial systems, smart grids, medical devices, smart TVs, and driverless cars. This is the reason why this trend has been accepted dramatically. However, along with the diversified reach of IoT, the threat of attacks has also increased. Several advanced threats, such as ransomware, malware, bots, and Distributed Denial of Service (DDoS) attack, causes a huge financial, personal, and corporate data loss. The extended growth of IoT across all the industry verticals faces critical challenges of managing identities and governing access to vital business processes and information. IoT IAM vendors are enhancing their solutions portfolio to help their clients confront these challenges and benefit the most from their digital ecosystems.
Restraint: Cost and budget concerns of IoT IAM solutions
Due to the continuous rise in security breaches, it becomes essential for organizations to secure their computing devices and corporate data from getting damaged. Therefore, managing the identities of every device has occupied a major concern when IoT security comes into the picture. Organizations have increased their IoT security investments to deploy solutions, such as access control, SSO, Application Program Interface (API) management, directory services, and identity management. However, for many enterprises, including SMEs, these investment costs are a matter of concern. For strong and advanced security, innovation costs are still high, and many organizations view budgetary constraints as barriers to growth in the IoT IAM market. According to EYs Global Information Security Survey 2015, about 62% of information security professionals said budget constraints are their biggest concern. Companies must think twice about investing in regions with developing economies, such as Latin America and Middle East & Africa, due to lower cyber defense budgets. Even if the security budget is rising each year, there is a lack of strategy and correct implementation of security solutions.
Opportunity: Adoption of Bring your Own Identity (BYOI) approach
The BYOI approach allows access to multiple services using single credential details, in which the user only must remember one strong password. As businesses are shifting towards the enormous usage of IoT applications, the need for securing identities to connected devices is also increasing. Managing multiple details of various devices becomes hectic. Therefore, organizations will be adopting advanced technologies, such as BYOI, to maintain the identities of the devices. BYOI is a technological evolution in access control and authentication processes that provides security with a better user experience. In the upcoming years, organizations will invest in adopting BYOI approaches to secure their IoT devices. Therefore, the need for integrated & advanced identity solutions, such as BYOI, is expected to increase and eventually lead to a higher IoT IAM market growth for all the individual security components.
Challenge: Lack of security, expertise, and awareness
Even though the popularity of IoT has gained considerable growth, the constraints such as lack of relevant technical expertise, security management time, technical knowledge, and awareness of IoT security professionals, are the major issues businesses face. Most IoT devices are based on non-traditional Operating Systems (OS), such as Android, iOS, and newer versions of Windows. Therefore, people are not familiar with the security concerns rising in such OS. According to the Cybrarys 2016 Cyber Security Job Trends Report, 68% of the respondents said there is a shortage of skilled security professionals globally and 74% of the respondents said there is a lack of talent in a specific security area. This research survey was conducted with 435 senior-level technology and security professionals. Advanced cyber threats are diverse in nature. Cybercriminals use advanced attack techniques to penetrate an organizations network. As the IoT IAM market is ever increasing with more threats evolving, the market cannot mitigate or respond to such attacks due to the lack of awareness. A holistic approach is now essential in terms of awareness and knowledge about such advanced threats and attacks to secure the network infrastructure.
Large enterprises are expected account for the largest market share during 2022
In large enterprises many IoT applications are prone to cyberattacks. And these enterprises have large IT infrastructures and are large, and security is a challenge for such enterprises therefore, large enterprises have adopted IAM solutions to ensure security and reliability. There is also an increase in BYOD trend; hence, large enterprises need authentication and adopt IoT IAM solutions.
Healthcare and lifesciences is expected to account for a higher CAGR during the forecast period
Healthcare cybersecurity is a growing concern. There has been a steady rise in hacking and IT security incidents. The healthcare industry has been slow to respond and lagged other industries related to cybersecurity. Nevertheless, cybersecurity budgets have improved as new technology has been purchased, and healthcare organizations are getting better at blocking attacks and securing their networks. Medical data is also becoming one of the profitable targets. Healthcare organizations face several challenges, such as preserving the privacy of Electronic Health Record (EHR) and meeting various compliances set by the Healthcare Information Portability and Accountability Act (HIPAA). The healthcare industry requires security solutions for monitoring, reporting, and management, including secure remote access, backup and recovery, and a secure wireless connection.
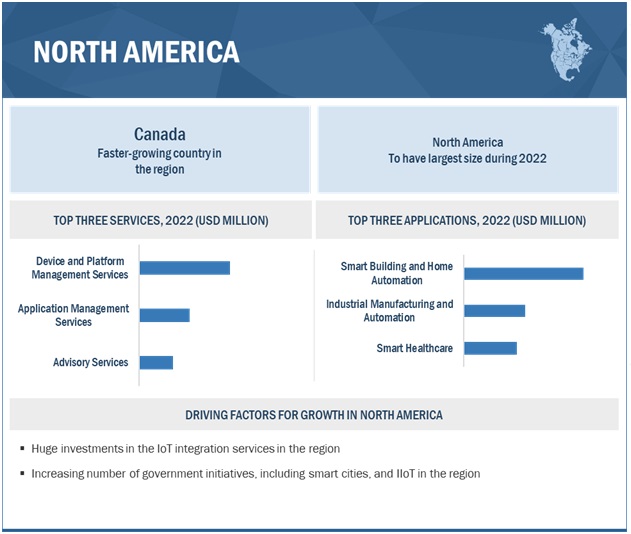
North America to account for the largest market share during the forecast period
North America is estimated to hold the highest market share during the forecast period in the IoT IAM market, due to the large-scale technological adoption by people, and the presence of key market players in the region. The penetration of the internet, increasing acceptance of the BYOD concept in organizations, and heightened use of mobile applications are increasing in this region, leading to the high requirement for IAM solutions. The US holds a major portion of the market in this region. North America leads the global market in terms of the usage of IoT IAM based solutions and services. The US and Canada are prominent countries contributing to technology development in this region.
To know about the assumptions considered for the study, download the pdf brochure
Key Market Players
The IoT IAM market vendors have implemented various types of organic and inorganic growth strategies, such as new product launches, product upgradations, partnerships and agreements, business expansions, and mergers and acquisitions to strengthen their offerings in the market. The major vendors in the global IoT IAM market AWS (US), Thales (France), IBM (US), Microsoft (US), Broadcom (US), Open Text (Canada), Cisco Systems (US), Ericsson (Sweden), Google (US), Micro Focus (UK), Ping Identity (US), Oracle (US), Entrust (US), HID Global (US), DigiCert (US), Okta (US), SailPoint (US), Dell EMC (US), Optiv Security (US), CyberArk (US), ForgeRock (US), One Identity (US), Verimatrix (France), KaaIoT (US), Identity Fusion (US), Keyfactor (US), GlobalSign (US), Blue Ridge (US), Sectigo (US), and FusionAuth (US). The study includes an in-depth competitive analysis of these key players in the IoT IAM market with their company profiles, recent developments, and key market strategies.
Scope of the Report
|
Report Metrics |
Details |
|
Market size available for years |
2016-2027 |
|
Base year considered |
2022 |
|
Forecast period |
2022-2027 |
|
Forecast units |
Value (USD Million/Billion) |
|
Segments covered |
By component, deployment mode, security type, organization size, verticals, and region |
|
Regions covered |
North America, Europe, Asia Pacific, Middle East and Africa, Latin America |
|
Companies covered |
AWS (US), Thales (France), IBM (US), Microsoft (US), Broadcom (US), Open Text (Canada), Cisco Systems (US), Ericsson (Sweden), Google (US), Micro Focus (UK), Ping Identity (US), Oracle (US), Entrust (US), HID Global (US), DigiCert (US), Okta (US), SailPoint (US), Dell EMC (US), Optiv Security (US), CyberArk (US), ForgeRock (US), One Identity (US), Verimatrix (France), KaaIoT (US), Identity Fusion (US), Keyfactor (US), GlobalSign (US), Blue Ridge (US), Sectigo (US), and FusionAuth (US). |
This research report categorizes the IoT IAM market to forecast revenues and analyze trends in each of the following subsegments:
By Component:
- Solutions
- Lifecycle Management
- Provisioning
- De provisioning
- Digital Certificate
- API Management/API Gateway
- Authentication
- Single Factor Authentication
- Two Factor Authentication
- Multi Factor Authentiction
- Lifecycle Management
- Single Sign-On
- Enterprise SSO
- Web Federated SSO
- Directory Services
- Storage
- Meta Directories
- Virtual Directories
- Access Management and Authorization
- Password Management
- Self Service Password Reset
- Password Reset
- Password Synchronization
- Audit, Compliance and Governance
- Services
- Professional Services
- Integration and Implementation
- Consulting
- Support and Maintenance
- Managed Services
- Professional Services
By Security type:
- Network security
- Endpoint Security
- Application Security
- Cloud Security
- Other Security Types (Database and Web Security)
By Deployment mode:
- Cloud
- On-premises
By Organization size:
- SMEs
- Large enterprises
By Verticals:
- Banking, Finance services, and Insurance (BFSI)
- Automotive
- Telecom
- IT and ITeS
- Retail and Consumer Goods
- Energy and Utilities
- Healthcare
- Oil and Gas
- Manufacturing
- Other Verticals (Education, Travel and Hospitality)
By Region:
- North America
- US
- Canada
- Europe
- UK
- France
- Germany
- Rest of Europe
- Asia Pacific
- China
- Australia
- Japan
- Rest of APAC
- Middle East and Africa
- Middle East
- Africa
- Latin America
- Brazil
- Mexico
- Rest of Latin America
Recent Developments:
- In May 2022, Thales acquired S21sec and Excellium, two major players in cybersecurity consulting, integration, and managed services in Europe. With this acquisition, Thales accelerates its cybersecurity development roadmap and expands its footprint in Spain, Portugal, Luxembourg, and Belgium.
- In October 2021, IBM collaborated with Apptio, a leading technology business management (TBM) SaaS application provider, to help clients enhance hybrid cloud technology decision-making.
- In December 2020, AWS helped Okta to bring together the availability of the Okta Identity Cloud and its products in AWS Marketplace to provide proper infrastructure for those organizations migrating to the cloud.
Frequently Asked Questions (FAQ):
What is IoT IAM?
IoT identity & access management (IAM) is managing the identities and relationships between employees, users, and connected devices. IoT IAM platforms are used to manage millions of identities and policies that are associated with devices within enterprises. As per Onelogin by One Identity, IAM ensures that the right people and job roles in organization (identities) can access the tools they need to do their jobs.
Which countries are considered in the European region?
The report includes an analysis of the UK, France, Germany in the European region.
Which are the key drivers supporting the growth of the IoT IAM market?
The key drivers supporting the growth of the IoT IAM market include rise in adoption of BYOD trend, increase in frequency of cybersecurity breaches and cyberattacks, increased integration of IAM with IoT devices.
Who are the key vendors in the IoT IAM market?
The key vendors operating in the IoT IAM market include. AWS (US), Thales (France), IBM (US), Microsoft (US), Broadcom (US), Open Text (Canada), Cisco Systems (US), Ericsson (Sweden), Google (US), Micro Focus (UK), Ping Identity (US), Oracle (US), Entrust (US), HID Global (US), DigiCert (US), Okta (US), SailPoint (US), Dell EMC (US), Optiv Security (US), CyberArk (US), ForgeRock (US), One Identity (US), Verimatrix (France), KaaIoT (US), Identity Fusion (US), Keyfactor (US), GlobalSign (US), Blue Ridge (US), Sectigo (US), and FusionAuth (US). .
To speak to our analyst for a discussion on the above findings, click Speak to Analyst

TABLE OF CONTENTS
1 INTRODUCTION (Page No. - 44)
1.1 STUDY OBJECTIVES
1.2 MARKET DEFINITION
1.3 STUDY SCOPE
1.3.1 MARKETS COVERED
FIGURE 1 IOT IAM MARKET SEGMENTATION
1.3.2 GEOGRAPHIC SCOPE
FIGURE 2 MARKET: GEOGRAPHIC SCOPE
1.3.3 INCLUSIONS AND EXCLUSIONS
1.3.4 YEARS CONSIDERED
1.4 CURRENCY
TABLE 1 USD EXCHANGE RATES, 20192021
1.5 LIMITATIONS
1.6 SUMMARY OF CHANGES
1.7 STAKEHOLDERS
2 RESEARCH METHODOLOGY (Page No. - 49)
2.1 RESEARCH DATA
FIGURE 3 IOT IAM MARKET: RESEARCH DESIGN
2.1.1 SECONDARY DATA
2.1.1.1 Secondary sources
2.1.2 PRIMARY DATA
2.1.2.1 Primary interviews with experts
2.1.2.2 List of key primary interview participants
2.1.2.3 Breakdown of primaries
2.1.2.4 Primary sources
2.1.2.5 Key industry insights
2.2 MARKET SIZE ESTIMATION
2.2.1 BOTTOM-UP APPROACH
FIGURE 4 BOTTOM-UP APPROACH
FIGURE 5 MARKET SIZE ESTIMATION METHODOLOGY, BOTTOM-UP (SUPPLY-SIDE): COLLECTIVE REVENUE FROM ALL SOLUTIONS/SERVICES OF THE IOT IAM MARKET
2.2.2 TOP-DOWN APPROACH
FIGURE 6 TOP-DOWN APPROACH
2.2.3 MARKET ESTIMATION: DEMAND-SIDE ANALYSIS
FIGURE 7 MARKET SIZE ESTIMATION METHODOLOGY: DEMAND-SIDE ANALYSIS
2.2.4 MARKET ESTIMATION: SUPPLY-SIDE ANALYSIS
FIGURE 8 MARKET SIZE ESTIMATION METHODOLOGY: SUPPLY-SIDE ANALYSIS
2.2.5 GROWTH FORECAST ASSUMPTIONS
TABLE 2 MARKET GROWTH ASSUMPTIONS
2.3 MARKET BREAKDOWN AND DATA TRIANGULATION
FIGURE 9 DATA TRIANGULATION
2.4 RESEARCH ASSUMPTIONS
2.4.1 RISK ASSESSMENT
TABLE 3 RISK ASSESSMENT: IOT IAM MARKET
3 EXECUTIVE SUMMARY (Page No. - 60)
FIGURE 10 MARKET, BY COMPONENT, 2022 VS. 2027 (USD MILLION)
FIGURE 11 MARKET, BY DEPLOYMENT MODE, 2022 VS. 2027 (USD MILLION)
FIGURE 12 MARKET, BY ORGANIZATION SIZE, 2022 VS. 2027 (USD MILLION)
FIGURE 13 MARKET, BY SECURITY TYPE, 2022 VS. 2027 (USD MILLION)
FIGURE 14 MARKET, BY VERTICAL, 2022 VS. 2027 (USD MILLION)
FIGURE 15 MARKET, BY REGION, 2022 VS. 2027 (USD MILLION)
4 PREMIUM INSIGHTS (Page No. - 64)
4.1 IOT IAM MARKET OVERVIEW
FIGURE 16 INCREASING ADOPTION OF BYOD AND MASSIVE GROWTH IN IOT TRENDS TO DRIVE THE MARKET GROWTH
4.2 MARKET SHARE OF TOP THREE VERTICALS AND SOLUTIONS, 2022
FIGURE 17 BFSI SEGMENT AND LIFECYCLE MANAGEMENT SOLUTION TO HOLD THE LARGEST MARKET SHARE IN 2022
4.3 GEOGRAPHICAL SNAPSHOT OF THE MARKET
FIGURE 18 ASIA PACIFIC EXPECTED TO ACHIEVE THE HIGHEST GROWTH DURING THE FORECAST PERIOD
5 MARKET OVERVIEW AND INDUSTRY TRENDS (Page No. - 66)
5.1 INTRODUCTION
5.2 MARKET DYNAMICS
FIGURE 19 DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES: IOT IAM MARKET
5.2.1 DRIVERS
5.2.1.1 Rise in adoption of BYOD trend
5.2.1.2 Increase in frequency of cybersecurity breaches and cyberattacks
5.2.1.3 Increased integration of IAM with IoT devices
5.2.2 RESTRAINTS
5.2.2.1 Cost and budget concerns of IoT IAM solutions
5.2.3 OPPORTUNITIES
5.2.3.1 Adoption of Bring your Own Identity (BYOI) approach
5.2.3.2 Rise in adoption of biometric technologies through smartphones, laptops, and tablets
5.2.3.3 Government and private sector cyber security mandates
5.2.4 CHALLENGES
5.2.4.1 Lack of security, expertise, and awareness
FIGURE 20 TOP SOURCE COUNTRIES FOR IOT ATTACKS (%), 2019
5.3 IMPACT OF COVID-19 ON MARKET DYNAMICS
5.3.1 DRIVERS AND OPPORTUNITIES
5.3.2 RESTRAINTS AND CHALLENGES
5.3.3 CUMULATIVE GROWTH ANALYSIS
5.4 IOT IAM MARKET: VALUE CHAIN ANALYSIS
FIGURE 21 MARKET: VALUE CHAIN
5.5 ECOSYSTEM
TABLE 4 MARKET: ECOSYSTEM
5.6 PRICING MODEL OF MARKET PLAYERS
TABLE 5 PRICING MODELS AND INDICATIVE PRICE POINTS, 20212022
5.7 TECHNOLOGY ANALYSIS
5.7.1 INTRODUCTION
5.7.2 ARTIFICIAL INTELLIGENCE
5.7.3 BLOCKCHAIN
5.7.4 CLOUD COMPUTING
5.7.5 DIGITAL TWIN
5.8 CASE STUDY ANALYSIS
5.8.1 CASE STUDY 1: THE AUTO CLUB GROUP (ACG) USED OPENTEXT IDENTITY AND ACCESS MANAGEMENT SOLUTION
5.8.2 CASE STUDY 2: THE CITY AND COUNTY OF SAN FRANCISCO (CCSF) UTILIZED ORACLES IAM SOLUTION
5.8.3 CASE STUDY 3: SOTI WORKS WITH ONELOGIN FOR SSO AND PROVISIONING AS IT MOVES TO THE CLOUD
5.8.4 CASE STUDY 4: ENTRUST HELPS BANCO BICE COMPLY WITH SBIF SECURITY REGULATIONS
5.8.5 CASE STUDY 5: THE CITY OF MESA OPTED FOR ASPECT UNIFIED IP SOLUTIONS FROM ALVARIA TO OFFER STRONG INTERACTION CHOICES
5.9 REVENUE SHIFT FOR THE IOT IAM MARKET
FIGURE 22 REVENUE IMPACT ON THE MARKET
5.10 PATENT ANALYSIS
5.10.1 METHODOLOGY
5.10.2 TYPES OF PATENTS
TABLE 6 PATENTS FILED, 20192022
5.10.3 INNOVATION AND PATENT APPLICATIONS
FIGURE 23 TOTAL NUMBER OF PATENTS GRANTED IN A YEAR, 20192022
5.10.4 TOP APPLICANTS
FIGURE 24 TOP TEN COMPANIES WITH THE HIGHEST NUMBER OF PATENT APPLICATIONS, 20192022
TABLE 7 TOP TEN PATENT OWNERS IN THE MARKET, 20192022
TABLE 8 LIST OF A FEW PATENTS IN THE MARKET, 20202022
5.11 PORTERS FIVE FORCES ANALYSIS
TABLE 9 IOT IAM MARKET: PORTERS FIVE FORCES MODEL
5.11.1 THREAT OF NEW ENTRANTS
5.11.2 THREAT OF SUBSTITUTES
5.11.3 BARGAINING POWER OF BUYERS
5.11.4 BARGAINING POWER OF SUPPLIERS
5.11.5 DEGREE OF COMPETITION
5.12 REGULATORY LANDSCAPE
5.12.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 10 NORTH AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 11 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 12 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
TABLE 13 REST OF THE WORLD: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
5.12.1.1 North America
5.12.1.1.1 US
5.12.1.1.2 Canada
5.12.1.2 Europe
5.12.1.3 Asia Pacific
5.12.1.3.1 China
5.12.1.3.2 India
5.12.1.3.3 Australia
5.12.1.3.4 Japan
5.12.1.4 Middle East and Africa
5.12.1.4.1 Middle East
5.12.1.4.2 South Africa
5.12.1.5 Latin America
5.12.1.5.1 Brazil
5.12.1.5.2 Mexico
5.13 KEY STAKEHOLDERS AND BUYING CRITERIA
5.13.1 KEY STAKEHOLDERS IN BUYING PROCESS
FIGURE 25 INFLUENCE OF STAKEHOLDERS IN THE BUYING PROCESS FOR THE TOP THREE VERTICALS
TABLE 14 INFLUENCE OF STAKEHOLDERS IN BUYING PROCESS FOR THE TOP THREE VERTICALS
5.13.2 BUYING CRITERIA
FIGURE 26 KEY BUYING CRITERIA FOR THE TOP THREE VERTICALS
TABLE 15 KEY BUYING CRITERIA FOR THE TOP 3 END USERS
5.14 KEY CONFERENCES AND EVENTS IN 2022-2023
TABLE 16 IOT IAM MARKET: DETAILED LIST OF CONFERENCES AND EVENTS
6 GLOBAL IOT IAM MARKET, BY COMPONENT (Page No. - 93)
6.1 INTRODUCTION
6.1.1 COMPONENT: MARKET DRIVERS
6.1.2 COMPONENT: COVID-19 IMPACT
6.2 SOLUTIONS
TABLE 22 SOLUTION: MARKET, BY TYPE, 20222027 (USD MILLION)
6.2.1 LIFECYCLE MANAGEMENT
TABLE 23 LIFECYCLE MANAGEMENT: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 24 LIFECYCLE MANAGEMENT: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.1.1 Provisioning
6.2.1.1.1 Increase In security with automated provisioning
TABLE 25 PROVISIONING: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 26 PROVISIONING: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.1.2 De-Provisioning
6.2.1.2.1 Vital security protocol that ensures protection of data
TABLE 27 DE-PROVISIONING: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 28 DE-PROVISIONING: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.2 DIGITAL CERTIFICATE
6.2.2.1 To perform functions of identification, integrity, and authentication
TABLE 29 DIGITAL CERTIFICATE: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 30 DIGITAL CERTIFICATE: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.3 API MANAGEMENT/API GATEWAYS
6.2.3.1 To secure IoT applications and connected devices
TABLE 31 API MANAGEMENT/API GATEWAYS: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 32 API MANAGEMENT/API GATEWAYS: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.4 AUTHENTICATION
TABLE 33 AUTHENTICATION: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 34 AUTHENTICATION: IOT IAM MARKET, BY REGION, 20222027 (USD MILLION)
6.2.4.1 Single-factor authentication
6.2.4.1.1 Smart passwords and usernames for single-factor authentication
TABLE 35 SINGLE-FACTOR AUTHENTICATION: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 36 SINGLE-FACTOR AUTHENTICATION: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.4.2 Two-factor authentication
6.2.4.2.1 Adoption of two-factor authentication for better protection
TABLE 37 TWO-FACTOR AUTHENTICATION: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 38 TWO-FACTOR AUTHENTICATION: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.4.3 Multi-factor authentication
6.2.4.3.1 Multiple layers of verification for device protection
TABLE 39 MULTI-FACTOR AUTHENTICATION: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 40 MULTI-FACTOR AUTHENTICATION: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.5 SINGLE SIGN-ON
TABLE 41 SINGLE SIGN-ON: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 42 SINGLE SIGN-ON: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.5.1 Enterprise SSO
6.2.5.1.1 One-click access to all enterprise applications
TABLE 43 ENTERPRISE SSO: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 44 ENTERPRISE SSO: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.5.2 Web and federated SSO
6.2.5.2.1 Single point of access to all applications across different organizations
TABLE 45 WEB AND FEDERATED SSO: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 46 WEB AND FEDERATED SSO: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.6 DIRECTORY SERVICES
TABLE 47 DIRECTORY SERVICES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 48 DIRECTORY SERVICES: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.6.1 Storage
6.2.6.1.1 Directory server offers a central source for storing and handling information
TABLE 49 STORAGE: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 50 STORAGE: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.6.2 Meta directories
6.2.6.2.1 To create a consolidated view of identity information
TABLE 51 META DIRECTORIES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 52 META DIRECTORIES: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.6.3 Virtual directories
6.2.6.3.1 Supports various protocols, such as LDAP, SQL, DSML, SPML
TABLE 53 VIRTUAL DIRECTORIES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 54 VIRTUAL DIRECTORIES: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.7 ACCESS MANAGEMENT AND AUTHORIZATION
6.2.7.1 To manage multiple identities across devices and domains
TABLE 55 ACCESS MANAGEMENT AND AUTHORIZATION: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 56 ACCESS MANAGEMENT AND AUTHORIZATION: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.8 PASSWORD MANAGEMENT
TABLE 57 PASSWORD MANAGEMENT: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 58 PASSWORD MANAGEMENT: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.8.1 Self-service password reset
6.2.8.1.1 Reset of the password by user securely
TABLE 59 SELF SERVICE PASSWORD RESET: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 60 SELF SERVICE PASSWORD RESET: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.8.2 Password reset
6.2.8.2.1 Create and reset a new password by invalidating the current password
TABLE 61 PASSWORD RESET: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 62 PASSWORD RESET: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.8.3 Password synchronization
6.2.8.3.1 Process of accomplishing Single Sign-On (SSO)
TABLE 63 PASSWORD SYNCHRONIZATION: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 64 PASSWORD SYNCHRONIZATION: MARKET, BY REGION, 20222027 (USD MILLION)
6.2.9 AUDIT, COMPLIANCE, AND GOVERNANCE
6.2.9.1 Solutions providing comprehensive support for auditing
TABLE 65 AUDIT, COMPLIANCE AND GOVERNANCE: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 66 AUDIT, COMPLIANCE AND GOVERNANCE: MARKET, BY REGION, 20222027 (USD MILLION)
6.3 SERVICES
TABLE 67 SERVICES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 68 SERVICES: MARKET, BY REGION, 20222027 (USD MILLION)
TABLE 69 SERVICES: MARKET, BY TYPE, 20162021 (USD MILLION)
TABLE 70 SERVICES: MARKET, BY TYPE, 20222027 (USD MILLION)
6.3.1 PROFESSIONAL SERVICES
TABLE 71 PROFESSIONAL SERVICES: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 72 PROFESSIONAL SERVICES: MARKET, BY REGION, 20222027 (USD MILLION)
TABLE 73 PROFESSIONAL SERVICES: MARKET, BY TYPE, 20162021 (USD MILLION)
TABLE 74 PROFESSIONAL SERVICES: MARKET, BY TYPE, 20222027 (USD MILLION)
6.3.1.1 Integration and implementation
6.3.1.1.1 Implementation services facilitate the integration of IoT IAM solutions into IoT infrastructure
TABLE 75 INTEGRATION AND IMPLEMENTATION: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 76 INTEGRATION AND IMPLEMENTATION: MARKET, BY REGION, 20222027 (USD MILLION)
6.3.1.2 Consulting
6.3.1.2.1 Advice and knowledge to clients on critical issues
TABLE 77 CONSULTING: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 78 CONSULTING: MARKET, BY REGION, 20222027 (USD MILLION)
6.3.1.3 Support and maintenance
6.3.1.3.1 Deployment of advanced IAM solutions to secure networking devices
TABLE 79 SUPPORT AND MAINTENANCE: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 80 SUPPORT AND MAINTENANCE: MARKET, BY REGION, 20222027 (USD MILLION)
6.3.2 MANAGED SERVICES
6.3.2.1 Outsourcing to third-party service providers to manage efficiently and reduce cost
TABLE 81 MANAGED SERVICES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 82 MANAGED SERVICES: MARKET, BY REGION, 20222027 (USD MILLION)
7 GLOBAL IOT IAM MARKET, BY SECURITY TYPE (Page No. - 121)
7.1 INTRODUCTION
7.1.1 SECURITY TYPE: MARKET DRIVERS
7.1.2 SECURITY TYPE: COVID-19 IMPACT
TABLE 83 MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 84 MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
7.2 NETWORK SECURITY
7.2.1 ADOPTION OF IAM SOLUTIONS TO ENHANCE NETWORK SECURITY
TABLE 85 NETWORK SECURITY: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 86 NETWORK SECURITY: MARKET, BY REGION, 20222027 (USD MILLION)
7.3 ENDPOINT SECURITY
7.3.1 ENHANCING ENDPOINT SECURITY WITH AUTHENTICATION SOLUTIONS
TABLE 87 ENDPOINT SECURITY: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 88 ENDPOINT SECURITY: MARKET, BY REGION, 20222027 (USD MILLION)
7.4 APPLICATION SECURITY
7.4.1 ADOPTION OF IAM SOLUTIONS TO ENSURE SECURITY
TABLE 89 APPLICATION SECURITY: IOT IAM MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 90 APPLICATION SECURITY: MARKET, BY REGION, 20222027 (USD MILLION)
7.5 CLOUD SECURITY
7.5.1 ENHANCING CLOUD SECURITY WITH IAM SOLUTIONS
TABLE 91 CLOUD SECURITY: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 92 CLOUD SECURITY: MARKET, BY REGION, 20222027 (USD MILLION)
7.6 OTHER SECURITY TYPES
7.6.1 BOOSTING DATABASE AND WEB SECURITY WITH IAM SOLUTIONS
TABLE 93 OTHER SECURITY TYPES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 94 OTHER SECURITY TYPES: MARKET, BY REGION, 20222027 (USD MILLION)
8 GLOBAL IOT IAM MARKET, BY DEPLOYMENT TYPE (Page No. - 128)
8.1 INTRODUCTION
8.1.1 DEPLOYMENT TYPE: IOT IAM MARKET DRIVERS
8.1.2 DEPLOYMENT TYPE: COVID-19 IMPACT
TABLE 95 MARKET, BY DEPLOYMENT MODE, 20162021 (USD MILLION)
TABLE 96 MARKET, BY DEPLOYMENT MODE, 20222027 (USD MILLION)
8.2 CLOUD
8.2.1 EASY ACCESS TO COMPUTING RESOURCES AND IT SERVICES
TABLE 97 CLOUD: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 98 CLOUD: MARKET, BY REGION, 20222027 (USD MILLION)
8.3 ON-PREMISES
8.3.1 ON-PREMISES SOLUTIONS OPTED FOR CRITICAL USER CREDENTIALS
TABLE 99 ON-PREMISES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 100 ON-PREMISES: MARKET, BY REGION, 20222027 (USD MILLION)
9 GLOBAL IOT IAM MARKET, BY ORGANIZATION SIZE (Page No. - 132)
9.1 INTRODUCTION
9.1.1 ORGANIZATION SIZE: MARKET DRIVERS
9.1.2 ORGANIZATION SIZE: COVID-19 IMPACT
TABLE 101 MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 102 MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
9.2 SMES
9.2.1 TO INCREASE THE SECURITY OF IOT APPLICATIONS SMES OPT FOR IAM SOLUTIONS
TABLE 103 SMES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 104 SMES: MARKET, BY REGION, 20222027 (USD MILLION)
9.3 LARGE ENTERPRISES
9.3.1 LARGE ENTERPRISES HAVE ADOPTED IAM SOLUTIONS TO ENSURE SECURITY
TABLE 105 LARGE ENTERPRISES: MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 106 LARGE ENTERPRISES: MARKET, BY REGION, 20222027 (USD MILLION)
10 GLOBAL IOT IAM MARKET, BY VERTICAL (Page No. - 136)
10.1 INTRODUCTION
10.1.1 VERTICAL: MARKET DRIVERS
10.1.2 VERTICAL: COVID-19 IMPACT
FIGURE 31 GLOBAL MARKET, BY VERTICAL, 2022 AND 2027 (USD MILLION)
TABLE 107 GLOBAL MARKET SIZE, BY VERTICAL, 20162021 (USD MILLION)
TABLE 108 GLOBAL MARKET SIZE, BY VERTICAL, 20222027 (USD MILLION)
10.2 BFSI
10.2.1 BFSI INDUSTRY TO CHOOSE IAM SOLUTIONS TO BOOST SECURITY
TABLE 109 BFSI: MARKET, BY REGION, 20162021(USD MILLION)
TABLE 110 BFSI: MARKET, BY REGION, 20222027 (USD MILLION)
10.3 AUTOMOTIVE
10.3.1 WITH INCREASING INNOVATION IN THE INDUSTRY, THERE IS A NEED FOR IAM SOLUTIONS FOR SECURITY
TABLE 111 AUTOMOTIVE: IOT IAM MARKET, BY REGION, 20162021(USD MILLION)
TABLE 112 AUTOMOTIVE: MARKET, BY REGION, 20222027 (USD MILLION)
10.4 TELECOM
10.4.1 IDENTITY SOLUTIONS TO CREATE A SEAMLESS AND SECURE CUSTOMER EXPERIENCE
TABLE 113 TELECOM: MARKET, BY REGION, 20162021(USD MILLION)
TABLE 114 TELECOM: MARKET, BY REGION, 20222027 (USD MILLION)
10.5 IT AND ITES
10.5.1 IT AND ITES ARE ADOPTING IOT SOLUTIONS FOR TECHNOLOGICAL INNOVATION
TABLE 115 IT AND ITES: MARKET, BY REGION, 20162021(USD MILLION)
TABLE 116 IT AND ITES: MARKET, BY REGION, 20222027 (USD MILLION)
10.6 RETAIL AND CONSUMER GOODS
10.6.1 INCREASE IN ADOPTION OF IAM SOLUTIONS TO PROTECT CRUCIAL DATA FROM HACKERS
TABLE 117 RETAIL AND CONSUMER GOODS: IOT IAM MARKET, BY REGION, 20162021(USD MILLION)
TABLE 118 RETAIL AND CONSUMER GOODS: MARKET, BY REGION, 20222027 (USD MILLION)
10.7 ENERGY AND UTILITIES
10.7.1 IAM SOLUTIONS TO ELIMINATE CYBER ATTACKS
TABLE 119 ENERGY AND UTILITIES: MARKET, BY REGION, 20162021(USD MILLION)
TABLE 120 ENERGY AND UTILITIES: MARKET, BY REGION, 20222027 (USD MILLION)
10.8 HEALTHCARE
10.8.1 SECURITY SOLUTION TO PRESERVE PRIVACY OF PATIENTS
TABLE 121 HEALTHCARE: MARKET, BY REGION, 20162021(USD MILLION)
TABLE 122 HEALTHCARE: MARKET, BY REGION, 20222027 (USD MILLION)
10.9 OIL AND GAS
10.9.1 WITH RAPID TECHNOLOGICAL ADVANCEMENTS, THERE IS ADOPTION OF CYBER SECURITY SOLUTIONS
TABLE 123 OIL AND GAS: IOT IAM MARKET, BY REGION, 20162021(USD MILLION)
TABLE 124 OIL AND GAS: MARKET, BY REGION, 20222027 (USD MILLION)
10.10 MANUFACTURING
10.10.1 VAST INDUSTRY ADOPTS SECURITY SOLUTIONS TO ENABLE BETTER PROTECTION
TABLE 125 MANUFACTURING: MARKET, BY REGION, 20162021(USD MILLION)
TABLE 126 MANUFACTURING: MARKET, BY REGION, 20222027 (USD MILLION)
10.11 OTHER VERTICALS (EDUCATION, TRAVEL, AND HOSPITALITY)
10.11.1 ADOPTION OF IDENTITY ACCESS SOLUTIONS TO ENHANCE SECURITY ACROSS VERTICALS
TABLE 127 OTHER VERTICALS: MARKET, BY REGION, 20162021(USD MILLION)
TABLE 128 OTHER VERTICALS: MARKET, BY REGION, 20222027 (USD MILLION)
11 IOT IAM MARKET, BY REGION (Page No. - 149)
11.1 INTRODUCTION
11.2 COVID-19 IMPACT ON THE MARKET
FIGURE 32 MARKET: REGIONAL SNAPSHOT (2022)
TABLE 129 MARKET, BY REGION, 20162021 (USD MILLION)
TABLE 130 MARKET, BY REGION, 20222027 (USD MILLION)
11.3 NORTH AMERICA
11.3.1 PESTLE ANALYSIS: NORTH AMERICA
FIGURE 33 NORTH AMERICA: MARKET SNAPSHOT
TABLE 131 NORTH AMERICA: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 132 NORTH AMERICA: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 133 NORTH AMERICA: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 134 NORTH AMERICA: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 135 NORTH AMERICA: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 136 NORTH AMERICA: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 137 NORTH AMERICA: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 138 NORTH AMERICA: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 139 NORTH AMERICA: IOT IAM MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 140 NORTH AMERICA: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 141 NORTH AMERICA: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 142 NORTH AMERICA: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 143 NORTH AMERICA: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 144 NORTH AMERICA: MARKET, BY VERTICAL, 20222027 (USD MILLION)
TABLE 145 NORTH AMERICA: MARKET, BY COUNTRY, 20162021 (USD MILLION)
TABLE 146 NORTH AMERICA: MARKET, BY COUNTRY, 20222027 (USD MILLION)
11.3.2 CANADA
11.3.2.1 Government initiatives such as the cyber Incident Response Centre
TABLE 147 CANADA: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 148 CANADA: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 149 CANADA: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 150 CANADA: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 151 CANADA: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 152 CANADA: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 153 CANADA: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 154 CANADA: IOT IAM MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 155 CANADA: MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 156 CANADA: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 157 CANADA: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 158 CANADA: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 159 CANADA: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 160 CANADA: MARKET, BY VERTICAL, 20222027 (USD MILLION)
11.3.3 UNITED STATES
11.3.3.1 Adoption of advanced IAM solutions to protect IoT applications
11.4 EUROPE
11.4.1 PESTLE ANALYSIS: EUROPE
TABLE 161 EUROPE: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 162 EUROPE: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 163 EUROPE: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 164 EUROPE: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 165 EUROPE: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 166 EUROPE: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 167 EUROPE: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 168 EUROPE: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 169 EUROPE: IOT IAM MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 170 EUROPE: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 171 EUROPE: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 172 EUROPE: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 173 EUROPE: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 174 EUROPE: MARKET, BY VERTICAL, 20222027 (USD MILLION)
TABLE 175 EUROPE: MARKET, BY COUNTRY, 20162021 (USD MILLION)
TABLE 176 EUROPE: MARKET, BY COUNTRY, 20222027 (USD MILLION)
11.4.2 FRANCE
11.4.2.1 Digitization and electronic communication networks
TABLE 177 FRANCE: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 178 FRANCE: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 179 FRANCE: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 180 FRANCE: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 181 FRANCE: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 182 FRANCE: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 183 FRANCE: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 184 FRANCE: IOT IAM MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 185 FRANCE: MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 186 FRANCE: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 187 FRANCE: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 188 FRANCE: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 189 FRANCE: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 190 FRANCE: MARKET, BY VERTICAL, 20222027 (USD MILLION)
11.4.3 UNITED KINGDOM
11.4.3.1 Increase in security breaches and incidents
11.4.4 GERMANY
11.4.4.1 Major players expanding their presence in various industry verticals
11.4.5 REST OF EUROPE
11.5 ASIA PACIFIC
11.5.1 PESTLE ANALYSIS: ASIA PACIFIC
FIGURE 34 ASIA PACIFIC: MARKET SNAPSHOT
TABLE 191 ASIA PACIFIC: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 192 ASIA PACIFIC: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 193 ASIA PACIFIC: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 194 ASIA PACIFIC: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 195 ASIA PACIFIC: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 196 ASIA PACIFIC: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 197 ASIA PACIFIC: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 198 ASIA PACIFIC: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 199 ASIA PACIFIC: MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 200 ASIA PACIFIC: IOT IAM MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 201 ASIA PACIFIC: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 202 ASIA PACIFIC: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 203 ASIA PACIFIC: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 204 ASIA PACIFIC: MARKET, BY VERTICAL, 20222027 (USD MILLION)
TABLE 205 ASIA PACIFIC: MARKET, BY COUNTRY, 20162021 (USD MILLION)
TABLE 206 ASIA PACIFIC: MARKET, BY COUNTRY, 20222027 (USD MILLION)
11.5.2 AUSTRALIA
11.5.2.1 Government formed the Australian criminal intelligence commission
TABLE 207 AUSTRALIA: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 208 AUSTRALIA: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 209 AUSTRALIA: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 210 AUSTRALIA: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 211 AUSTRALIA: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 212 AUSTRALIA: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 213 AUSTRALIA: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 214 AUSTRALIA: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 215 AUSTRALIA: IOT IAM MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 216 AUSTRALIA: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 217 AUSTRALIA: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 218 AUSTRALIA: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 219 AUSTRALIA: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 220 AUSTRALIA: MARKET, BY VERTICAL, 20222027 (USD MILLION)
11.5.3 CHINA
11.5.3.1 Emerging technologies to increase productivity
11.5.4 JAPAN
11.5.4.1 R&D capabilities and regulatory reforms by the government to drive growth in Japan
11.5.5 REST OF ASIA PACIFIC
11.6 MIDDLE EAST AND AFRICA
11.6.1 PESTLE ANALYSIS: MIDDLE EAST AND AFRICA
TABLE 221 MIDDLE EAST AND AFRICA: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 222 MIDDLE EAST AND AFRICA: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 223 MIDDLE EAST AND AFRICA: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 224 MIDDLE EAST AND AFRICA: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 225 MIDDLE EAST AND AFRICA: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 226 MIDDLE EAST AND AFRICA: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 227 MIDDLE EAST AND AFRICA: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 228 MIDDLE EAST AND AFRICA: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 229 MIDDLE EAST AND AFRICA: IOT IAM MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 230 MIDDLE EAST AND AFRICA: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 231 MIDDLE EAST AND AFRICA: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 232 MIDDLE EAST AND AFRICA: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 233 MIDDLE EAST AND AFRICA: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 234 MIDDLE EAST AND AFRICA: MARKET, BY VERTICAL, 20222027 (USD MILLION)
TABLE 235 MIDDLE EAST AND AFRICA: MARKET, BY COUNTRY, 20162021 (USD MILLION)
TABLE 236 MIDDLE EAST AND AFRICA: MARKET, BY COUNTRY, 20222027 (USD MILLION)
11.6.2 MIDDLE EAST
11.6.2.1 Increased adoption of IoT IAM solutions due to cybercrime
TABLE 237 MIDDLE EAST: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 238 MIDDLE EAST: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 239 MIDDLE EAST: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 240 MIDDLE EAST: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 241 MIDDLE EAST: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 242 MIDDLE EAST: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 243 MIDDLE EAST: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 244 MIDDLE EAST: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 245 MIDDLE EAST: IOT IAM MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 246 MIDDLE EAST: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 247 MIDDLE EAST: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 248 MIDDLE EAST: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 249 MIDDLE EAST: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 250 MIDDLE EAST: MARKET, BY VERTICAL, 20222027 (USD MILLION)
11.6.3 AFRICA
11.6.3.1 Increasing internet penetration across SMEs and large enterprises
TABLE 251 AFRICA: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 252 AFRICA: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 253 AFRICA: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 254 AFRICA: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 255 AFRICA: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 256 AFRICA: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 257 AFRICA: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 258 AFRICA: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 259 AFRICA: IOT IAM MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 260 AFRICA: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 261 AFRICA: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 262 AFRICA: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 263 AFRICA: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 264 AFRICA: MARKET, BY VERTICAL, 20222027 (USD MILLION)
11.7 LATIN AMERICA
11.7.1 PESTLE ANALYSIS: LATIN AMERICA
TABLE 265 LATIN AMERICA: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 266 LATIN AMERICA: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 267 LATIN AMERICA: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 268 LATIN AMERICA: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 269 LATIN AMERICA: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 270 LATIN AMERICA: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 271 LATIN AMERICA: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 272 LATIN AMERICA: MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 273 LATIN AMERICA: IOT IAM MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 274 LATIN AMERICA: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 275 LATIN AMERICA: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 276 LATIN AMERICA: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 277 LATIN AMERICA: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 278 LATIN AMERICA: MARKET, BY VERTICAL, 20222027 (USD MILLION)
TABLE 279 LATIN AMERICA: MARKET, BY COUNTRY, 20162021 (USD MILLION)
TABLE 280 LATIN AMERICA: MARKET, BY COUNTRY, 20222027 (USD MILLION)
11.7.2 BRAZIL
11.7.2.1 Higher use of the Internet and smartphones to drive market growth in Brazil
TABLE 281 BRAZIL: IOT IAM MARKET, BY COMPONENT, 20162021 (USD MILLION)
TABLE 282 BRAZIL: MARKET, BY COMPONENT, 20222027 (USD MILLION)
TABLE 283 BRAZIL: MARKET, BY SOLUTION TYPE, 20162021 (USD MILLION)
TABLE 284 BRAZIL: MARKET, BY SOLUTION TYPE, 20222027 (USD MILLION)
TABLE 285 BRAZIL: MARKET, BY SERVICE TYPE, 20162021 (USD MILLION)
TABLE 286 BRAZIL: MARKET, BY SERVICE TYPE, 20222027 (USD MILLION)
TABLE 287 BRAZIL: MARKET, BY SECURITY TYPE, 20162021 (USD MILLION)
TABLE 288 BRAZIL: IOT IAM MARKET, BY SECURITY TYPE, 20222027 (USD MILLION)
TABLE 289 BRAZIL: MARKET, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 290 BRAZIL: MARKET, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
TABLE 291 BRAZIL: MARKET, BY DEPLOYMENT TYPE, 20162021 (USD MILLION)
TABLE 292 BRAZIL: MARKET, BY DEPLOYMENT TYPE, 20222027 (USD MILLION)
TABLE 293 BRAZIL: MARKET, BY VERTICAL, 20162021 (USD MILLION)
TABLE 294 BRAZIL: MARKET, BY VERTICAL, 20222027 (USD MILLION)
11.7.3 MEXICO
11.7.3.1 Digital transformation and adoption of mobile applications to drive growth in Mexico
11.7.4 REST OF LATIN AMERICA
12 COMPETITIVE LANDSCAPE (Page No. - 212)
12.1 INTRODUCTION
12.2 KEY PLAYER STRATEGIES
TABLE 295 OVERVIEW OF STRATEGIES DEPLOYED BY KEY PLAYERS IN THE IOT IAM MARKET
12.3 MARKET SHARE ANALYSIS OF TOP PLAYERS
TABLE 296 MARKET: DEGREE OF COMPETITION
12.4 HISTORICAL REVENUE ANALYSIS
FIGURE 35 HISTORICAL THREE-YEAR REVENUE ANALYSIS OF LEADING PLAYERS, 20192021 (USD MILLION)
12.5 COMPANY PRODUCT FOOTPRINT ANALYSIS
TABLE 297 COMPANY VERTICAL PRODUCT FOOTPRINT
TABLE 298 COMPANY SOLUTION FOOTPRINT
TABLE 299 COMPANY REGION FOOTPRINT
12.6 MARKET RANKING OF KEY PLAYERS IN IOT IAM MARKET, 2022
FIGURE 36 MARKET RANKING OF KEY PLAYERS, 2022
12.7 COMPANY EVALUATION QUADRANT
12.7.1 STARS
12.7.2 EMERGING LEADERS
12.7.3 PERVASIVE PLAYERS
12.7.4 PARTICIPANTS
FIGURE 37 MARKET (GLOBAL), COMPANY EVALUATION MATRIX, 2022
12.8 STARTUP/SME EVALUATION QUADRANT
12.8.1 PROGRESSIVE COMPANIES
12.8.2 RESPONSIVE COMPANIES
12.8.3 DYNAMIC COMPANIES
12.8.4 STARTING BLOCKS
FIGURE 38 IOT IAM MARKET (STARTUP): COMPANY EVALUATION MATRIX, 2022
12.9 COMPETITIVE SCENARIO
12.9.1 PRODUCT LAUNCHES
TABLE 300 PRODUCT LAUNCHES, 20192022
12.9.2 DEALS
TABLE 301 DEALS, 20202022
12.9.3 OTHERS
TABLE 302 OTHERS, 20202022
13 COMPANY PROFILES (Page No. - 224)
13.1 MAJOR PLAYERS
(Business overview, Products offered, Recent developments, MNM view, Key strengths/Right to win, Strategic choices made, and Weaknesses and competitive threats)*
13.1.1 AWS
TABLE 303 AWS: BUSINESS OVERVIEW
FIGURE 39 AWS: COMPANY SNAPSHOT
TABLE 304 AWS: PRODUCTS OFFERED
TABLE 305 AWS: LAUNCHES
TABLE 306 AWS: DEALS
13.1.2 THALES
TABLE 307 THALES: BUSINESS OVERVIEW
FIGURE 40 THALES: COMPANY SNAPSHOT
TABLE 308 THALES: PRODUCTS OFFERED
TABLE 309 THALES: PRODUCT LAUNCHES
TABLE 310 THALES: DEALS
13.1.3 IBM
TABLE 311 IBM: BUSINESS OVERVIEW
FIGURE 41 IBM: COMPANY SNAPSHOT
TABLE 312 IBM: PRODUCTS OFFERED
TABLE 313 IBM: PRODUCT LAUNCHES
TABLE 314 IBM: DEALS
13.1.4 MICROSOFT
TABLE 315 MICROSOFT: BUSINESS OVERVIEW
FIGURE 42 MICROSOFT: COMPANY SNAPSHOT
TABLE 316 MICROSOFT: PRODUCTS OFFERED
TABLE 317 MICROSOFT: PRODUCT LAUNCHES
TABLE 318 MICROSOFT: DEALS
TABLE 319 MICROSOFT: IOT IAM MARKET: OTHERS
13.1.5 BROADCOM
TABLE 320 BROADCOM: BUSINESS OVERVIEW
FIGURE 43 BROADCOM: COMPANY SNAPSHOT
TABLE 321 BROADCOM: PRODUCTS OFFERED
TABLE 322 BROADCOM: DEALS
13.1.6 OPENTEXT
TABLE 323 OPENTEXT: BUSINESS OVERVIEW
FIGURE 44 OPENTEXT: COMPANY SNAPSHOT
TABLE 324 OPENTEXT: PRODUCTS OFFERED
TABLE 325 OPENTEXT: DEALS
13.1.7 CISCO SYSTEMS
TABLE 326 CISCO SYSTEMS: BUSINESS OVERVIEW
FIGURE 45 CISCO SYSTEMS: COMPANY SNAPSHOT
TABLE 327 CISCO SYSTEMS: PRODUCTS OFFERED
TABLE 328 CISCO SYSTEM: DEALS
13.1.8 ERICSSON
TABLE 329 ERICSSON: BUSINESS OVERVIEW
FIGURE 46 ERICSSON: COMPANY SNAPSHOT
TABLE 330 ERICSSON: PRODUCTS OFFERED
TABLE 331 ERICSSON: PRODUCT LAUNCHES
TABLE 332 ERICSSON: DEALS
13.1.9 GOOGLE
TABLE 333 GOOGLE: BUSINESS OVERVIEW
FIGURE 47 GOOGLE: COMPANY SNAPSHOT
TABLE 334 GOOGLE: PRODUCTS OFFERED
TABLE 335 GOOGLE: DEALS
13.1.10 MICRO FOCUS
TABLE 336 MICRO FOCUS: BUSINESS OVERVIEW
FIGURE 48 MICRO FOCUS: COMPANY SNAPSHOT
TABLE 337 MICRO FOCUS: PRODUCTS OFFERED
TABLE 338 MICRO FOCUS: DEALS
13.1.11 PING IDENTITY
TABLE 339 PING IDENTITY: BUSINESS OVERVIEW
FIGURE 49 PING IDENTITY: COMPANY SNAPSHOT
TABLE 340 PING IDENTITY: PRODUCTS OFFERED
TABLE 341 PING IDENTITY: PRODUCT LAUNCHES
TABLE 342 PING IDENTITY: DEALS
13.1.12 ORACLE
TABLE 343 ORACLE: BUSINESS OVERVIEW
FIGURE 50 ORACLE: COMPANY SNAPSHOT
TABLE 344 ORACLE: PRODUCTS OFFERED
13.1.13 ENTRUST
13.1.14 HID GLOBAL
13.1.15 DIGICERT
13.1.16 OKTA
13.1.17 SAILPOINT
13.1.18 DELL EMC
13.1.19 OPTIV SECURITY
13.1.20 CYBERARK
13.2 STARTUP/SMES
13.2.1 FORGEROCK
13.2.2 ONE IDENTITY
13.2.3 VERIMATRIX
13.2.4 KAAIOT
13.2.5 IDENTITY FUSION
13.2.6 KEYFACTOR
13.2.7 GLOBALSIGN
13.2.8 BLUE RIDGE NETWORKS
13.2.9 SECTIGO
13.2.10 FUSIONAUTH
*Details on Business overview, Products offered, Recent developments, MNM view, Key strengths/Right to win, Strategic choices made, and Weaknesses and competitive threats might not be captured in case of unlisted companies.
14 ADJACENT/RELATED MARKETS (Page No. - 279)
14.1 IDENTITY AND ACCESS MANAGEMENT MARKET
14.1.1 MARKET DEFINITION
14.1.2 MARKET OVERVIEW
14.1.3 IDENTITY AND ACCESS MANAGEMENT MARKET, BY COMPONENT
TABLE 345 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY COMPONENT, 20162021 (USD MILLION)
TABLE 346 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY COMPONENT, 20222027 (USD MILLION)
14.1.4 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SOLUTION
TABLE 347 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SOLUTION, 20162021 (USD MILLION)
TABLE 348 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SOLUTION, 20222027 (USD MILLION)
14.1.5 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE
TABLE 349 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SERVICE, 20162021 (USD MILLION)
TABLE 350 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SERVICE, 20222027 (USD MILLION)
14.1.6 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE
TABLE 351 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY DEPLOYMENT MODE, 20162021 (USD MILLION)
TABLE 352 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY DEPLOYMENT MODE, 20222027 (USD MILLION)
14.1.7 IDENTITY AND ACCESS MANAGEMENT MARKET, BY ORGANIZATION SIZE
TABLE 353 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY ORGANIZATION SIZE, 20162021 (USD MILLION)
TABLE 354 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY ORGANIZATION SIZE, 20222027 (USD MILLION)
14.1.8 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL
TABLE 355 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY VERTICAL, 20162021 (USD MILLION)
TABLE 356 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY VERTICAL, 20222027 (USD MILLION)
14.1.9 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION
TABLE 357 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY REGION, 20162021 (USD MILLION)
TABLE 358 IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY REGION, 20222027 (USD MILLION)
14.2 CONSUMER IAM MARKET
14.2.1 MARKET DEFINITION
14.2.2 MARKET OVERVIEW
14.2.3 CONSUMER IAM MARKET, BY COMPONENT
TABLE 359 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY COMPONENT, 20152020 (USD MILLION)
TABLE 360 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY COMPONENT, 20212026 (USD MILLION)
TABLE 361 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SOLUTION, 20152020 (USD MILLION)
TABLE 362 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SOLUTION, 20212026 (USD MILLION)
TABLE 363 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY SERVICE, 20152020 (USD MILLION)
TABLE 364 CONSUMER MANAGEMENT AND ACCESS MANAGEMENT MARKET SIZE, BY SERVICE, 20212026 (USD MILLION)
14.2.4 CONSUMER IAM MARKET, BY DEPLOYMENT MODE
TABLE 365 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY DEPLOYMENT MODE, 20152020 (USD MILLION)
TABLE 366 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY DEPLOYMENT MODE, 20212026 (USD MILLION)
14.2.5 CONSUMER IAM MARKET, BY ORGANIZATION SIZE
TABLE 367 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY ORGANIZATION SIZE, 20152020 (USD MILLION)
TABLE 368 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY ORGANIZATION SIZE, 20212026 (USD MILLION)
14.2.6 CONSUMER IAM MARKET, BY VERTICAL
TABLE 369 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY VERTICAL, 20152020 (USD MILLION)
TABLE 370 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY VERTICAL, 20212026 (USD MILLION)
14.2.7 CONSUMER IAM MARKET, BY REGION
TABLE 371 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY REGION, 20152020 (USD MILLION)
TABLE 372 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET SIZE, BY REGION, 20212026 (USD MILLION)
14.3 IOT SECURITY MARKET
14.3.1 MARKET DEFINITION
14.3.2 MARKET OVERVIEW
14.3.3 IOT SECURITY MARKET, BY COMPONENT
TABLE 373 IOT SECURITY MARKET SIZE, BY COMPONENT, 20172020 (USD MILLION)
TABLE 374 IOT SECURITY MARKET SIZE, BY COMPONENT, 20212026 (USD MILLION)
TABLE 375 IOT SECURITY MARKET SIZE, BY SOLUTION, 20172020 (USD MILLION)
TABLE 376 IOT SECURITY MARKET SIZE, BY SOLUTION, 20212026 (USD MILLION)
TABLE 377 IOT SECURITY MARKET SIZE, BY SERVICE, 20172020 (USD MILLION)
TABLE 378 IOT SECURITY MARKET SIZE, BY SERVICE, 20212026 (USD MILLION)
14.3.4 IOT SECURITY MARKET, BY TYPE
TABLE 379 IOT SECURITY MARKET SIZE, BY TYPE, 20172020 (USD MILLION)
TABLE 380 IOT SECURITY MARKET SIZE, BY TYPE, 20212026 (USD MILLION)
14.3.5 IOT SECURITY MARKET, BY DEPLOYMENT MODE
TABLE 381 IOT SECURITY MARKET SIZE, BY DEPLOYMENT MODE, 20172020 (USD MILLION)
TABLE 382 IOT SECURITY MARKET SIZE, BY DEPLOYMENT MODE, 20212026 (USD MILLION)
14.3.6 IOT SECURITY MARKET, BY ORGANIZATION SIZE
TABLE 383 IOT SECURITY MARKET SIZE, BY ORGANIZATION SIZE, 20172020 (USD MILLION)
TABLE 384 IOT SECURITY MARKET SIZE, BY ORGANIZATION SIZE, 20212026 (USD MILLION)
14.3.7 IOT SECURITY MARKET, BY APPLICATION AREA
TABLE 385 IOT SECURITY MARKET SIZE, BY APPLICATION AREAS, 20172020 (USD MILLION)
TABLE 386 IOT SECURITY MARKET SIZE, BY APPLICATION AREAS, 20212026 (USD MILLION)
14.3.8 IOT SECURITY MARKET, BY REGION
TABLE 387 IOT SECURITY MARKET SIZE, BY REGION, 20172020 (USD MILLION)
TABLE 388 IOT SECURITY MARKET SIZE, BY REGION, 20212026 (USD MILLION)
15 APPENDIX (Page No. - 298)
15.1 DISCUSSION GUIDE
15.2 KNOWLEDGE STORE: MARKETSANDMARKETS SUBSCRIPTION PORTAL
15.3 AVAILABLE CUSTOMIZATIONS
15.4 RELATED REPORTS
15.5 AUTHOR DETAILS
The study involved four major activities in estimating the current size of the IoT IAM market. Exhaustive secondary research was done to collect information on the lending industry. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Both top-down and bottom-up approaches were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and sub segments of the IoT IAM market.
Secondary Research
The market for the companies offering IoT IAM solutions and services is arrived at based on secondary data available through paid and unpaid sources and by analyzing the product portfolios of the major companies in the ecosystem and rating the companies based on performance and quality. In the secondary research process, various sources were referred to for identifying and collecting information for this study. The secondary sources include annual reports, press releases and investors presentations of companies, white papers, journals, and certified publications and articles from recognized authors, directories, and databases. Research reports from few consortiums and councils, such as RSA Security and the Department of Homeland Security (DHS), have also been referred to for structuring qualitative content.
Secondary research was mainly used to obtain key information about the industrys supply chain, the total pool of key players, market classification, and segmentation according to industry trends to the bottom-most level, regional markets and key developments from both market and technology-oriented perspectives, all of which were further validated by primary sources.
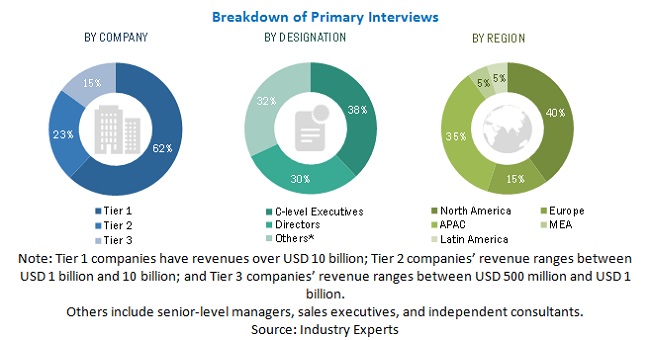
Primary Research
In the primary research process, various primary sources from both supply and demand sides were interviewed to obtain qualitative and quantitative information for the report. The primary sources from the supply side included Chief Executive Officers (CEOs), Chief Technology Officers (CTOs), Chief Operating Officers (COOs), Vice Presidents (VPs), Managing Directors (MDs), technology and innovation directors, and related key executives from various key companies and organizations operating in the IoT IAM market.
Primary interviews were conducted to gather insights, such as market statistics, data of revenue collected from solutions and services, market breakups, market size estimations, market forecasts, and data triangulation. Stakeholders from the demand side, such as Chief Information Officers (CIOs), Chief Finance Officers (CFOs), Chief Strategy Officers (CSOs), and the installation team of end-users who use IoT IAM, were interviewed to understand buyers perspectives on suppliers, products, service providers, and their current usage of IoT IAM, which is expected to affect the overall IoT IAM market growth.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
In the market engineering process, the top-down and bottom-up approaches were used along with multiple data triangulation methods to estimate and validate the size of the IoT IAM market and other dependent submarkets. Key market players were identified through secondary research, and their market share in the targeted regions was determined with the help of primary and secondary research. This entire research methodology included the study of annual and financial presentations of the top market players as well as interviews with experts for key insights (quantitative and qualitative).
The percentage share, splits, and breakdowns were determined using secondary sources and verified through primary research. All the possible parameters that affect the IoT IAM market were verified in detail with the help of primary sources and analyzed to obtain quantitative and qualitative data. This data was supplemented with detailed inputs and analysis from MarketsandMarkets and presented in the report.
IoT IAM market: Bottom-Up Approach
To know about the assumptions considered for the study, Request for Free Sample Report
Data Triangulation
After arriving at the overall market size using the market size estimation processes as explained above, the market was split into several segments and subsegments. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Report Objectives
- To determine and forecast the global IoT IAM market based on component, deployment mode security type, organization size, verticals, and regions from 2022 to 2027, and analyze various macro and microeconomic factors that affect the market growth.
- To forecast the size of the markets segments with respect to five main regions: North America, Europe, Asia Pacific (APAC), Latin America, and Middle East and Africa (MEA).
- To provide detailed information about the major factors (drivers, opportunities, threats, and challenges) influencing the growth of the market.
- To analyze the impact of COVID-19 on the market.
- To analyze each submarket with respect to individual growth trends, prospects, and contributions to the total market.
- To analyze opportunities in the market for stakeholders by identifying the high-growth segments of the IoT IAM market.
- To profile key market players (top vendors and startups); provide a comparative analysis based on their business overviews, regional presence, product offerings, business strategies, and key financials; and illustrate the markets competitive landscape.
- To track and analyze competitive developments, such as mergers and acquisitions, a new product launched and product developments, partnerships, agreements, and collaborations, business expansions, and Research and Development (R&D) activities, in the market
Available Customizations
Along with the market data, MarketsandMarkets offers customizations as per the companys specific needs. The following customization options are available for the report:
Product Analysis
- Product Matrix which gives a detailed comparison of the product portfolio of each company
Company Information
- Detailed analysis and profiling of additional market players (up to 5)



 Generating Response ...
Generating Response ...










Growth opportunities and latent adjacency in IoT IAM Market