
US Cybersecurity Market Size, Share, Opportunities & Latest Trends
US Cybersecurity Market by Solution Type (IAM, Firewall & VPN, Log Management & SIEM, Antivirus/Antimalware), Services (Professional [Risk & Threat Assessment, Training & Education], Managed), Security Type (Cloud, Application, Network) - Forecast to 2030




OVERVIEW
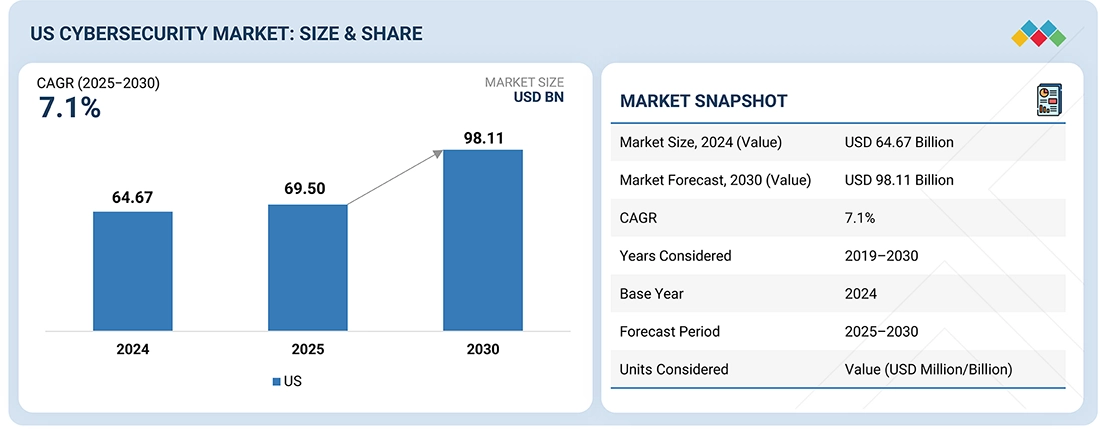
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
The US cybersecurity market size is projected to grow from USD 69.50 billion in 2025 to USD 98.11 billion by 2030, with a compound annual growth rate (CAGR) of 7.1%. The growing hybrid work culture in the US, combined with increasing cybersecurity needs, is driving the cybersecurity market. Employees have begun to care more about work-life balance than pay, which indicates a broad acceptance of hybrid working models. As a result, organizations need secure remote access, secure endpoints, and data flows, which drives the demand for cybersecurity solutions in the US.
KEY TAKEAWAYS
-
BY OFFERINGBy offering, cybersecurity solutions are projected to dominate the US market in terms of market share in the forecast period.
-
BY SOLUTION TYPEBy solution type, the log management & SIEM segment is projected to lead in terms of growth rate of 7.8%.
-
BY SECURITY TYPEBy security type, network security is estimated to dominate the market with 40.5% in 2025.
-
BY ORGANIZATION SIZEBy organization size, the SMEs type segment is projected to grow at the highest CAGR.
-
BY DEPLOYMENT MODECloud deployment of cybersecurity is projected to grow at the fastest rate of 8.4% from 2025 to 2030.
-
BY VERTICALBy vertical, the healthcare & life sciences segment is projected to grow the fastest during the forecast period at the highest CAGR.
-
COMPETITIVE LANDSCAPE - KEY PLAYERSPalo Alto Networks, Cisco, and Fortinet lead the US cybersecurity landscape with mature, scalable platforms spanning network defense, cloud security, identity-centric architectures, and AI-driven threat detection and response. The companies' extensive enterprise footprints, strong regulatory alignment, and broad system integrations make them preferred vendors for large financial institutions, healthcare organizations, federal agencies, and Fortune 500 enterprises.
-
COMPETITIVE LANDSCAPE - STARTUPSWiz, Arctic Wolf, and Axonius represent fast-growing US cybersecurity startups delivering cloud-native protection with rapid deployment, simplified security operations, and seamless multicloud integrations. The companies' SaaS-first models and automation-focused architectures appeal to mid-market companies and digital-first organizations seeking scalable security without high implementation overhead.
The cybersecurity market in the US is being driven by rapid cloud adoption across enterprises. According to CloudZero, in 2025, nearly 60% of C-suite leaders state that cloud computing improves security, reflecting growing reliance on cloud platforms. As more workloads shift to hybrid and multi-cloud environments, organizations are increasing investment in cloud security solutions and managed services to protect data, access, and applications.
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
The US cybersecurity market is shifting from traditional appliance-based protection toward AI-enabled security analytics, cloud-native automation, and proactive threat prevention. Increasing adoption of zero-trust, identity security, and IoT security in industries such as IT, BFSI, telecom, healthcare, and manufacturing is creating new revenue opportunities. As organizations enhance cyber-resilience and regulatory compliance, demand for scalable platforms that improve visibility, automate response, and safeguard distributed digital environments is expanding.
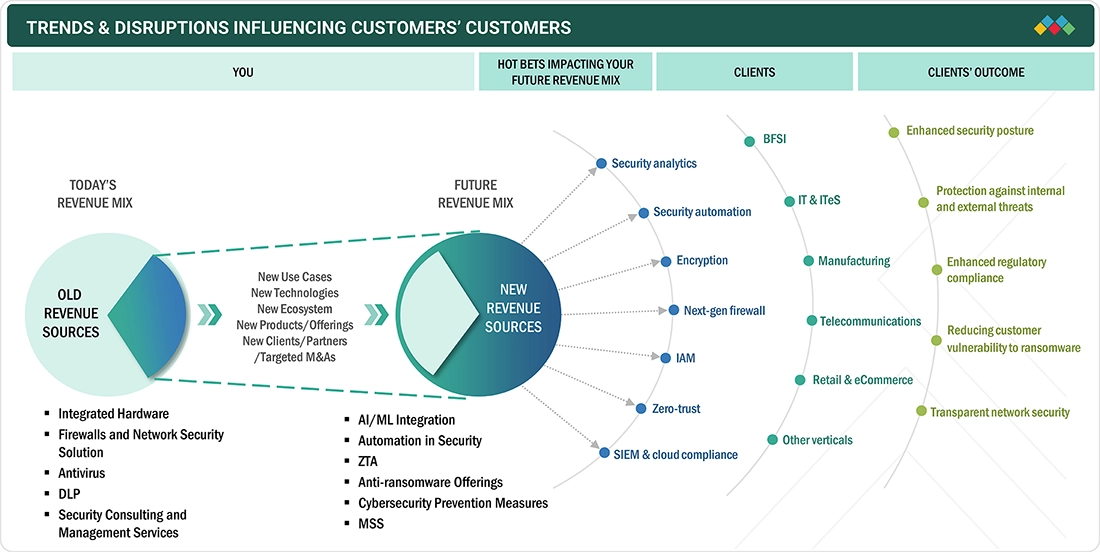
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Surge in ransomware and nation-state attacks

-
Increasing federal mandates and compliance pressure
Level
-
High cost of cybersecurity deployment
-
Shortage of skilled professionals
Level
-
Expansion of federal cybersecurity grant programs
-
Rising demand for cloud-native security solutions
Level
-
Rapid evolution of adversarial attack techniques
-
Complexity of integrating multi-vendor security tools
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Surge in ransomware and nation-state attacks
The US cybersecurity market continues to expand as ransomware groups and nation-state actors increasingly target critical infrastructure, financial institutions, healthcare networks, and government systems. According to Cyble, ransomware attacks on US organizations increased by around 149 percent year over year in early 2025. These attacks are prompting organizations to invest more in threat detection, incident response automation, and resilience measures, thereby minimizing service disruptions caused by cyberattacks.
Restraint: High cost of cybersecurity deployment
Large-scale cybersecurity upgrades in the US have led to significant investments in cloud usage, zero-trust security, and AI-based protection. However, the upgrade costs are high for the small and medium-sized organizations. As a result, many delay or reduce the use of advanced cybersecurity tools, even as cyber risks continue to grow.
Opportunity: Expansion of federal cybersecurity grant programs
Federal funding and public-sector grant programs are creating strong growth opportunities as state, local, and tribal agencies improve cybersecurity defenses. These grants support workforce training, cloud security upgrades, and protection of critical systems. By lowering cost pressure on resource-limited agencies, funding programs are encouraging wider use of managed security services and AI-based monitoring tools.
Challenge: Rapid evolution of adversarial attack techniques
Attackers in the US are using advanced attack methods, including AI-based phishing, supply-chain attacks, and zero-day exploits. As these threats become increasingly difficult to detect, security teams struggle to keep their defenses up to date across complex environments. This challenge is driving the need for continuous threat intelligence, automated analysis, and faster response tools to stop attacks before they spread across digital systems.
US CYBERSECURITY MARKET: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
The City of Oak Creek deployed Fortinet Security Fabric, including FortiGate NGFW firewalls at internal and external boundaries, to modernize and secure its digital infrastructure while operating with a lean two-person IT team | Achieved 50–75% cost savings on hardware and maintenance | Improved real-time visibility and threat detection | Reduced issue resolution times by roughly 50% |
 |
A US financial-services management firm suffered a state-sponsored cyberattack that resulted in large cryptocurrency losses | Unit 42 conducted a breach investigation, identified attack vectors, guided remediation, and helped the firm harden defenses | Restored security posture, closed exploited vulnerabilities, and provided detailed after-action reporting to prevent future breaches, enabling renewed stakeholder confidence and regulatory readiness |
 |
Multiple US customers used Cisco networking and security solutions (networking infrastructure, secure access, unified management) for enterprise-wide digital transformation, supporting cloud migration, remote access, and unified threat management | Delivered scalable, integrated security and network infrastructure | Streamlined management | Improved resilience and compliance posture across large distributed organizations |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The US cybersecurity market ecosystem comprises a diverse set of technology vendors delivering layered protection across identity and access management, endpoint security, log management and SIEM, network security, data protection, and patch management. Each category plays a critical role in defending distributed digital environments as organizations adopt cloud, hybrid IT, and remote workforce models. Leading providers compete and collaborate to offer integrated, AI-enabled security platforms that enhance detection, automate response, and reduce operational risk across enterprise, government, and critical infrastructure sectors.
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
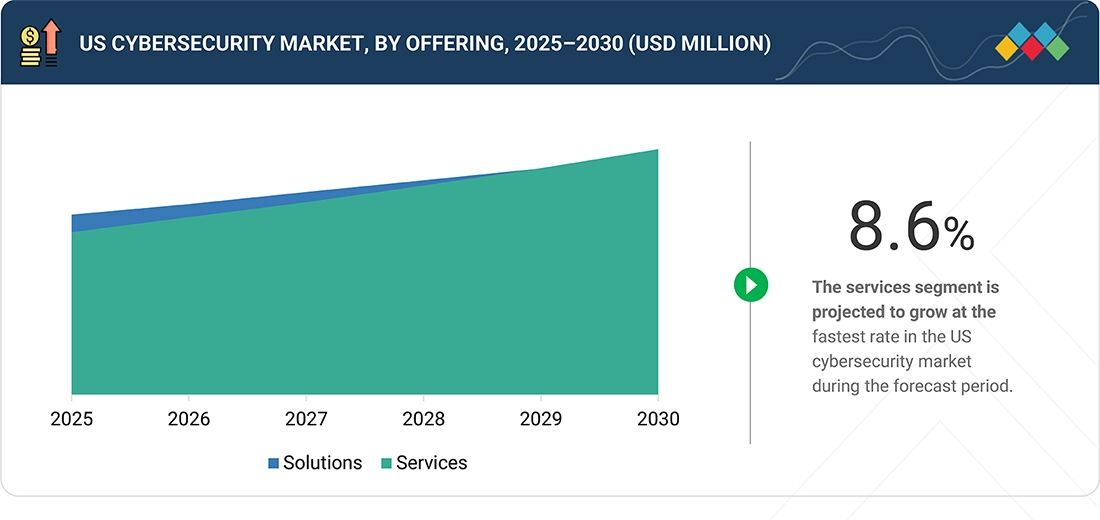
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
US Cybersecurity Market, by Offering
Solutions are estimated to account for the largest share as US organizations prioritize advanced cybersecurity technologies such as identity security, network protection, data governance, and threat detection to counter rising cyberattacks. Major platform investments from vendors like Microsoft, Palo Alto Networks, Cisco, and IBM further strengthen solution-driven spending across critical sectors.
US Cybersecurity Market, by Solution Type
Log management and SIEM lead due to the need for centralized visibility, real-time threat correlation, and faster investigations. US regulatory oversight and strict incident reporting expectations make SIEM essential for SOC operations, driving continued adoption in both enterprise and government environments.
US Cybersecurity Market, by Security Type
Network security dominates because US enterprises and public agencies rely on secure, segmented network architectures to protect data flows across cloud, on-prem, and OT systems. Persistent ransomware and supply chain threats reinforce demand for firewalls, secure gateways, ZTNA, and advanced intrusion defense.
US Cybersecurity Market, by Deployment Mode
On-premises remains the largest deployment mode as government, defense, and highly regulated industries require full data control, low-latency protection, and compliance with national security standards. Sensitive environments, such as federal facilities and critical infrastructure, continue to rely on locally managed cybersecurity controls.
US Cybersecurity Market, by Organization Size
Large enterprises account for the largest share due to high-value digital assets, distributed operations, and complex compliance mandates. Their ability to invest in comprehensive cybersecurity stacks and advanced analytics makes them primary adopters of leading US security technologies and managed SOC services.
US Cybersecurity Market, by Vertical
Government is estimated to account for the largest vertical share because federal and state agencies continuously expand investments to protect critical infrastructure, citizen data, and mission-critical systems. National cyber strategies, federal funding programs, and infrastructure modernization initiatives sustain strong spending across the US public sector cybersecurity.
US CYBERSECURITY MARKET: COMPANY EVALUATION MATRIX
The US cybersecurity market features a mix of established, full-stack platforms and rapidly expanding cloud-native security solutions. Leaders such as Palo Alto Networks and NETSCOUT deliver broad threat protection, network visibility, and SOC automation, while other vendors strengthen portfolios with identity, data, and cloud security capabilities. Market momentum is driven by AI-enabled detection, simplified security operations, and deeper integration across cloud, endpoint, and network environments to address the evolving threat landscape and modernization needs of US enterprises.
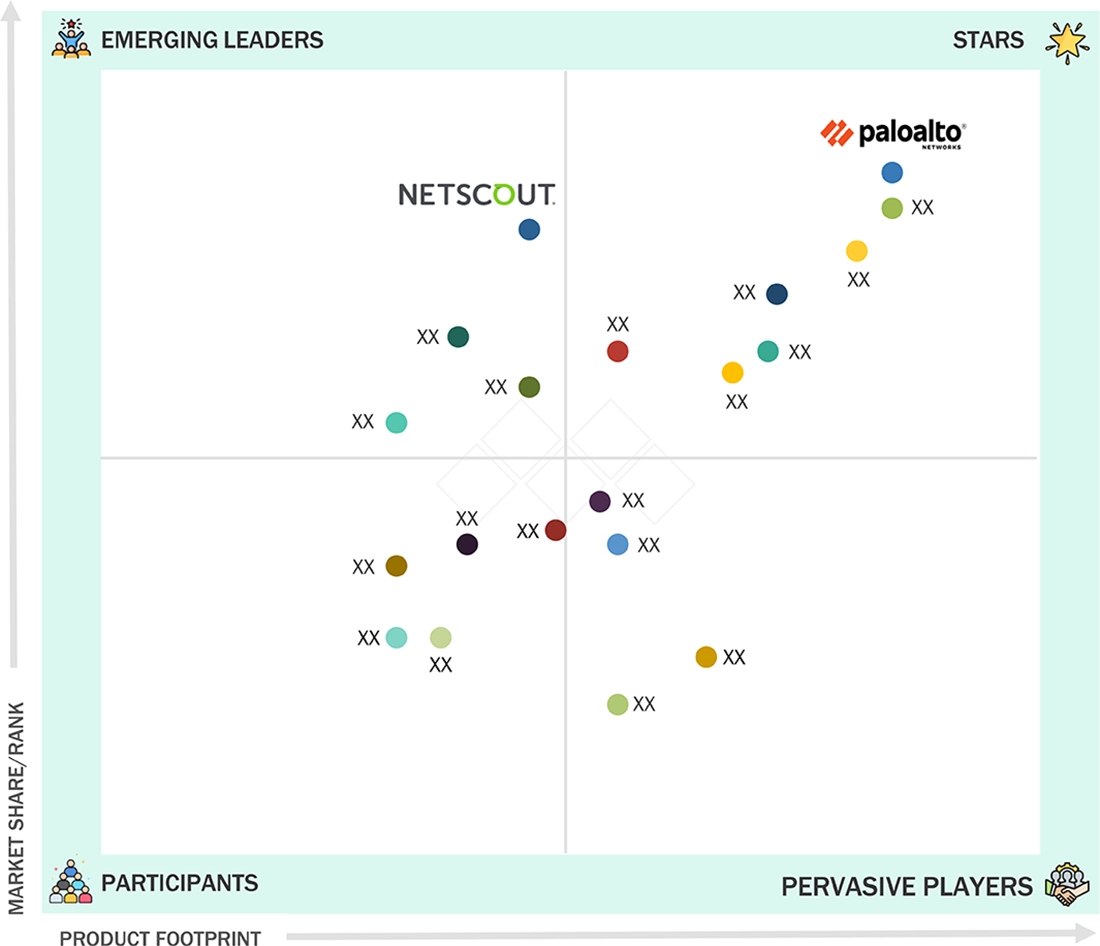
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
- IBM (US)
- Cisco (US)
- Microsoft (US)
- Palo Alto Networks (US)
- Fortinet (US)
- Trellix (US)
- Rapid7 (US)
- Google (US)
- NETSCOUT (US)
- Cloudflare (US)
- Gen (US)
- Proofpoint (US)
- CyberArk (US)
- SentinelOne (US)
- Arctic Wolf (US)
- Wiz (US)
- Axonius (US)
- F5 (US)
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size, 2024 (Value) | USD 64.67 Billion |
| Market Forecast, 2030 (Value) | USD 98.11 Billion |
| Growth Rate | CAGR of 7.1% from 2025 to 2030 |
| Years Considered | 2019–2030 |
| Base Year | 2024 |
| Forecast Period | 2025–2030 |
| Units Considered | Value (USD Million/Billion) |
| Report Coverage | Revenue Forecast, Company Ranking, Competitive Landscape, Growth Factors, and Trends |
| Segments Covered |
|
WHAT IS IN IT FOR YOU: US CYBERSECURITY MARKET REPORT CONTENT GUIDE
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Leading Solution Provider (US) | Product Analysis: US Cybersecurity Solution Matrix comparing vendors across network, cloud, endpoint, identity, data security, SIEM/log management, XDR, threat intelligence, Zero Trust, OT/IoT security, vulnerability analytics, and SOC automation, along with deployment flexibility across cloud, hybrid, and on-premise models | Enabled clearer visibility into competitive positioning, product breadth, integration maturity, and automation strength to support strategic portfolio decisions, roadmap planning, and multi-year cybersecurity modernization initiatives across US enterprises and government organizations |
RECENT DEVELOPMENTS
- June 2025 : IBM acquired Seek Al to support the launch of Watsonx Al Labs in New York, enhancing its agentic Al development for cybersecurity and beyond.
- May 2025 : Palo Alto Networks partnered with Cribl to integrate Cribl's telemetry management with Cortex XSIAM, enhancing SOC data pipelines and reducing alert fatigue.
- January 2025 : Cisco completed the acquisition of SnapAttack to enhance threat detection engineering workflows for Splunk deployments.
- July 2024 : IBM and Microsoft's cybersecurity collaboration aimed to help clients modernize security operations and protect against cloud identity threats, combining IBM's consulting services with Microsoft's security technologies to enhance threat detection and response across hybrid cloud environments.
Table of Contents

Methodology
Secondary research was conducted to collect information useful for this technical, market-oriented, and commercial study of the US Cybersecurity Market . The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, such as top-down and bottom-up, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and subsegments of the US Cybersecurity Market .
Secondary Research
In the secondary research process, various secondary sources were referred to for identifying and collecting information regarding the study. The secondary sources included annual reports, press releases, investor presentations of cybersecurity solution and service vendors, forums, certified publications, and whitepapers. The secondary research was mainly used to obtain key information about the industry’s supply chain, the total pool of key players, market classification and segmentation according to industry trends to the bottom-most level, regional markets, and key developments from both market- and technology-oriented perspectives, all of which were further validated by primary sources.
Primary Research
In the primary research process, various primary sources from both the supply and demand sides were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included various industry experts, including Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the US Cybersecurity Market .
In the market engineering process, top-down and bottom-up approaches were extensively used, along with several data triangulation methods, to perform the market estimation and market forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list key information/insights throughout the report.
After the complete market engineering process (including calculations for market statistics, market breakups, market size estimations, market forecasts, and data triangulation), extensive primary research was conducted to gather information and verify & validate the critical numbers arrived at. The primary research was also conducted to identify the segmentation, industry trends, competitive landscape of US Cybersecurity Market players, and key market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key strategies.
Market Size Estimation
Top-down and bottom-up approaches were used to estimate and validate the size of the US Cybersecurity Market and the size of various dependent sub-segments in the overall US Cybersecurity Market . The research methodology used to estimate the market size includes the following details: critical players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure included the study of the annual and financial reports of the top market players, and extensive interviews were conducted for key insights from the industry leaders, such as CEOs, VPs, directors, and marketing executives.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data is consolidated and added to detailed input and analysis from MarketsandMarkets.
Data Triangulation
The market was split into several segments and subsegments after arriving at the overall market size using the market size estimation processes explained above. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
According to MarketsandMarkets, cybersecurity is a set of technologies, processes, and practices to fortify critical systems, such as networks, physical devices, programs, and information, from unauthorized access, insider threats, and malicious attacks. These cyberattacks can affect data transmission across the networks, cause operational disruptions, and result in money extortion/ransomware. Cybersecurity, or information security, can be provided through hardware, software, and services.
Stakeholders
- Chief Technology and Data Officers
- Consulting Service Providers
- Managed Security Services Professionals
- Business Analysts
- Information Technology (IT) Professionals
- Government Agencies
- Investors and Venture Capitalists
- Small and Medium-sized Enterprises (SMEs) and Large Enterprises
- Third-party Providers
- Consultants/Consultancies/Advisory Firms
- Managed and Professional Service Providers
Report Objectives
- To describe and forecast the US Cybersecurity Market by offering, solution type, security type, deployment mode, organization size, vertical, and region from 2025 to 2030, and analyze the various macroeconomic and microeconomic factors that affect market growth
- To analyze the subsegments of the market with respect to individual growth trends, prospects, and contributions to the overall market
- To provide detailed information regarding major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
- To analyze opportunities in the market for stakeholders and provide details of the competitive landscape of major players
- To profile key market players; provide a comparative analysis based on the business overviews, regional presence, product offerings, business strategies, and key financials; and illustrate the competitive landscape of the marketTo analyze competitive developments, such as mergers & acquisitions, product developments, partnerships and collaborations, and research & development (R&D) activities, in the market
Available Customizations
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Company Information
- Detailed analysis and profiling of additional market players (up to 5)
Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the US Cybersecurity Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free Customisation














Growth opportunities and latent adjacency in US Cybersecurity Market