Data Center Access Control Market Size & Share, 2030
Data Center Access Control Market by Offering (Hardware - Card-based, Biometric, & Multi-technology Readers, Electronics Locks, Controllers; Software; Services), ACaaS, Data Center Type, Data Center Size, Vertical, and Region - Forecast to 2030




OVERVIEW
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
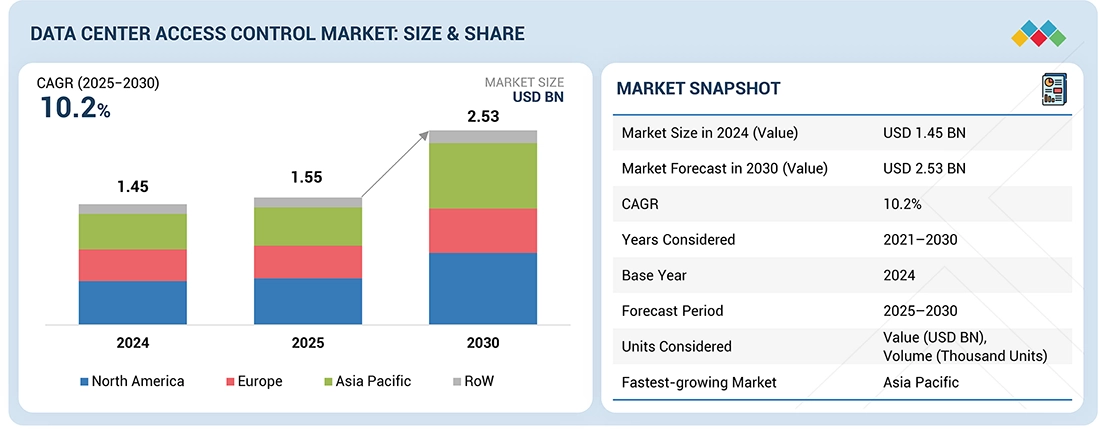
The data center access control market is projected to reach USD 2.53 billion by 2030 from USD 1.55 billion in 2025, at a CAGR of 10.2% from 2025 to 2030. The data center access control industry is growing due to the rapid expansion of hyperscale, colocation, and edge facilities, along with rising regulatory mandates, cyber-physical security risks, and the need for multi-layer authentication, are driving strong demand for advanced physical access solutions.
KEY TAKEAWAYS
-
BY REGIONThe Asia Pacific is expected to account for 30–35% of the data center access control market by 2030.
-
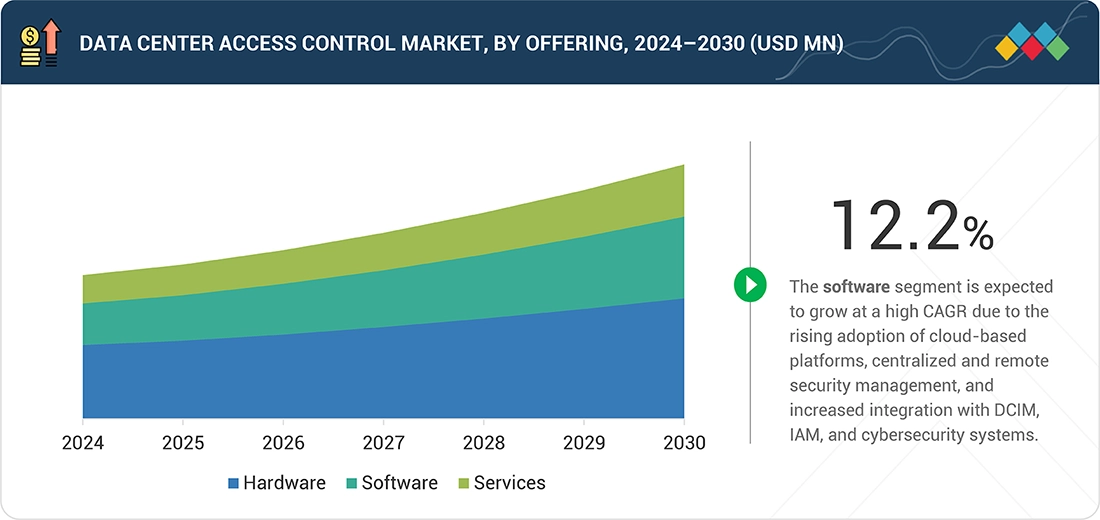
BY OFFERINGBy offering, the software segment is expected to register the highest CAGR of 12.2% during the forecast period.
-
BY DATA CENTER TYPEHyperscale data centers are expected to hold the largest share of the data center access control market in 2030.
-
BY VERTICALBy vertical, the commercial segment is expected to hold a significant market share of 38–42% by 2030.
-
COMPETITIVE LANDSCAPEASSA ABLOY (Sweden), dormakaba Group (Switzerland), and Johnson Controls (Ireland) were identified as some of the star players in the data center access control market, given their strong market share and product footprint.
-
COMPETITIVE LANDSCAPESalto Systems, S.L. (Spain), GALLAGHER GROUP LIMITED (New Zealand), and Brivo Systems, LLC (US), among others, have distinguished themselves among startups and SMEs by securing strong footholds in specialized niche areas, underscoring their potential as emerging market leaders.
The data center access control market is growing as operators strengthen physical security to counter rising insider and intrusion risks. Data localization mandates, the spread of multi-tenant colocation facilities, and the adoption of AI-driven identity and monitoring systems are further accelerating the need for advanced and compliant access control solutions.
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
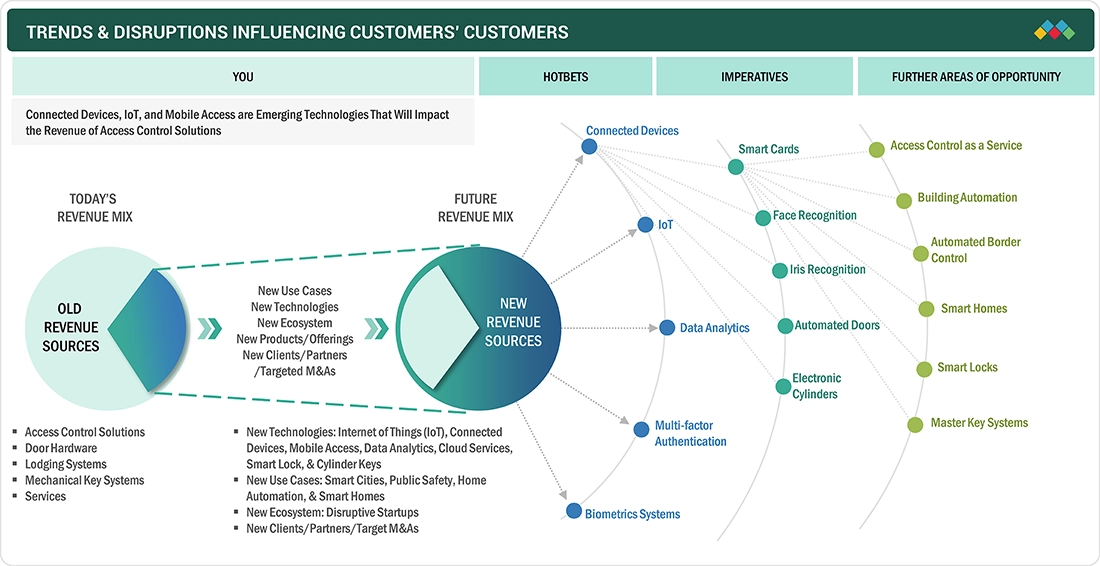
The data center access control market is experiencing a rapid transformation, with future revenue increasingly driven by emerging technologies. While traditional solutions currently account for around 20% of the market, innovations such as IoT-enabled systems, connected devices, mobile access, cloud services, data analytics, and smart locks are expected to generate 80% of future revenue. Key growth segments include biometrics, multi-factor authentication, and automated doors, supporting applications across smart cities, residential automation, public safety, and commercial infrastructure. This shift is further accelerated by the emergence of disruptive startups, strategic partnerships, and evolving technology ecosystems, positioning the region to implement next-generation access control solutions.
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Rising need to secure mission-critical infrastructure

-
Expansion of hyperscale and colocation data centers
Level
-
High deployment and integration costs
-
Complexity of retrofitting legacy facilities
Level
-
Adoption of Zero Trust Physical Security Models
-
Rising investments in edge data centers
Level
-
Ensuring seamless integration with DCIM and cybersecurity systems
-
Increasing sophistication of insider threats
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Rising need to secure mission-critical infrastructure
Data centers manage highly sensitive digital assets, making physical security a top priority. Increasing cyber-physical threats, stricter compliance mandates (ISO 27001, SOC 2, PCI-DSS), and growing risks of unauthorized access are pushing operators to invest heavily in advanced access control solutions, including biometrics, MFA, and continuous monitoring.
Restraint: High deployment and integration costs
Implementing advanced biometric systems, real-time access logging, and integrated physical-digital security platforms is expensive. Data centers often require custom installation, multi-door authentication, and redundancy-driven systems, resulting in significant upfront and maintenance costs that can slow adoption.
Opportunity: Adoption of Zero-Trust Physical Security models
Data centers are increasingly shifting toward Zero-Trust frameworks, where every access attempt must be authenticated, authorized, and continuously verified. This trend is driving the adoption of AI-enabled identity management, behavior-based authentication, and centralized monitoring platforms, creating strong market opportunities for next-generation access control providers.
Challenge: Ensuring seamless integration with DCIM and cybersecurity systems
Data center environments require unified management across physical access, network security, and IT operations. Integrating access control with DCIM, IAM, SIEM, and cybersecurity tools is often complex, requiring interoperability, API support, and real-time synchronization to maintain comprehensive security visibility.
DATA CENTER ACCESS CONTROL MARKET: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
dormakaba physical access control systems deployed in hyperscale, colocation, and enterprise data centers, integrating biometric readers, mantrap portals, mobile credentials, and multi-factor authentication to secure server rooms, equipment zones, and restricted racks with centralized monitoring. | Enhanced perimeter and interior security, reduced risk of unauthorized access, streamlined identity verification, and improved compliance with data center security standards, including ISO 27001 and SOC 2. |
 |
HID access control solutions implemented across data center facilities for unified identity management using smart cards, mobile IDs, PKI authentication, and biometric verification, integrated with DCIM and cybersecurity platforms for end-to-end security governance. | Frictionless and secure authentication, centralized user provisioning, enhanced audit trail management, and strong alignment with zero-trust physical security frameworks. |
 |
Allegion’s electronic locking systems and secure door hardware deployed in data center corridors, cages, and restricted cabinets, combined with IoT-enabled access devices to support multi-tenant and multi-zone access control within colocation environments. | Higher operational efficiency, reduced on-site management complexity, scalable access for multiple tenants, and improved monitoring of technician, vendor, and contractor movements within sensitive areas. |
 |
Johnson Controls integrated access control platforms used in data centers for centralized command-center operations, combining physical access, video surveillance, environmental monitoring, and intrusion detection through a unified security dashboard. | Stronger protection of mission-critical assets, real-time situational awareness, faster incident detection and response, and seamless interoperability with existing DCIM and building management systems. |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The data center access control market ecosystem involves hardware providers, software & cloud-based access control providers, system integrators & service providers, distribution & channel partners, and end users. Each section collaborates to advance the market by sharing knowledge, resources, and expertise to attain end innovation in this field.

Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Data Center Access Control Market, by Offering
The hardware segment is expected to hold the largest market share in the data center access control market in 2030 as data centers rely heavily on physical access components such as biometric readers, electronic locks, controllers, mantraps, and surveillance-integrated systems. The need for robust, tamper-resistant infrastructure to secure critical facilities drives higher spending on hardware compared to software or services.
Data Center Access Control Market, by Data Center Type
Hyperscale data centers will dominate the data center access control market as global cloud providers continue rapid expansion, requiring advanced multi-layered access control systems. Their large-scale operations, high rack density, and stringent security standards significantly increase demand for sophisticated hardware and integrated monitoring solutions.
Data Center Access Control Market, by Vertical
The commercial sector is expected to hold the largest share in 2025, driven by the growing number of colocation facilities and enterprise data centers operated by IT, BFSI, telecom, and cloud service providers. These organizations prioritize strict physical security, regulatory compliance, and continuous monitoring, driving strong adoption of advanced access control systems.
REGION
Asia Pacific is expected to be the fastest-growing region in the data center access control market during the forecast period
Asia Pacific is expected to grow at a high CAGR in the data center access control market due to rapid hyperscale and colocation expansion, strict data sovereignty regulations, rising cloud adoption, and increasing investments in secure digital infrastructure across China, India, Japan, and South Korea.
DATA CENTER ACCESS CONTROL MARKET: COMPANY EVALUATION MATRIX
In the data center access control market matrix, ASSA ABLOY (Sweden) and dormakaba Group (Switzerland) lead with a strong market presence and a wide product portfolio, driving large-scale adoption across various industries, including commercial and residential.
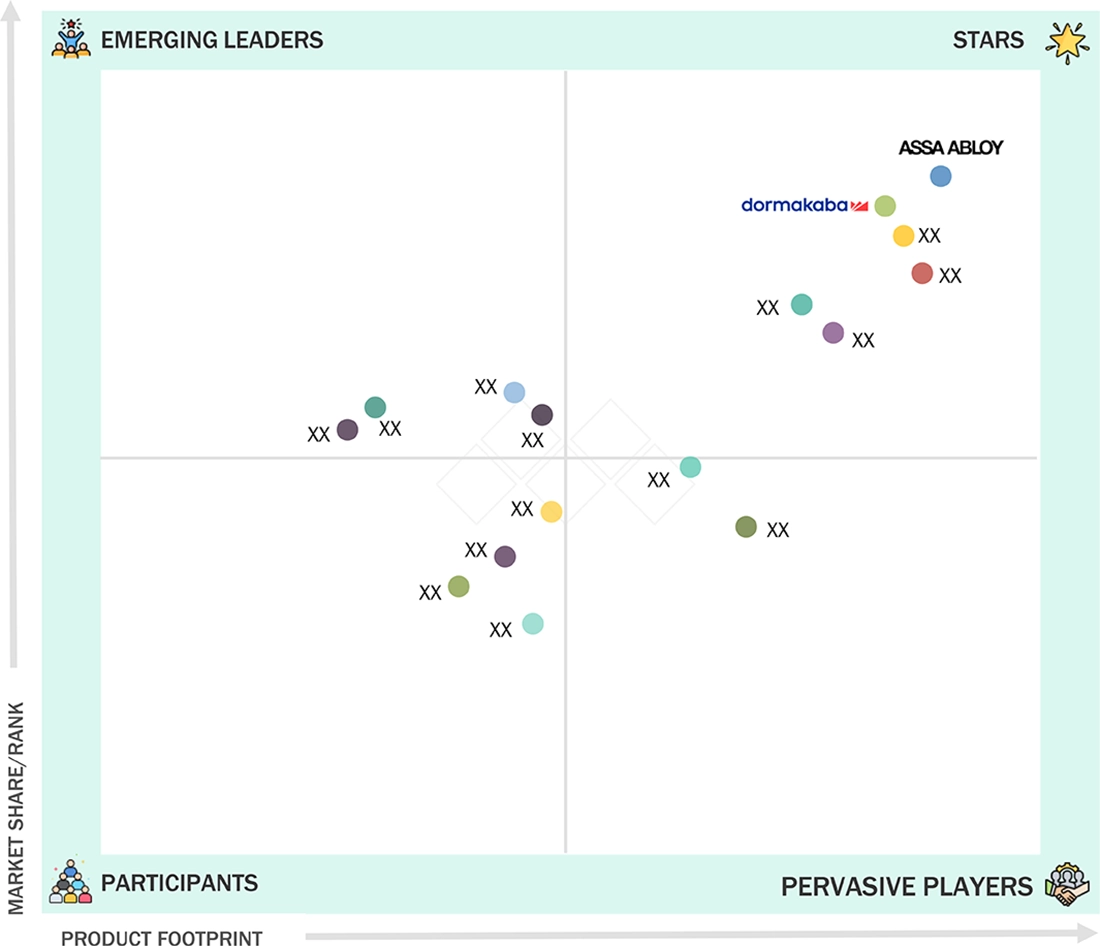
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
- ASSA ABLOY (Sweden)
- dormakaba Group (Switzerland)
- Johnson Controls (Ireland)
- Allegion plc (Ireland)
- Honeywell International Inc. (US)
- Nedap N.V. (Netherlands)
- Suprema Inc. (South Korea)
- Axis Communications AB (Sweden)
- NEC Corporation (Japan)
- Brivo Systems, LLC. (US)
- Salto Systems, S.L. (Spain)
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size in 2024 (Value) | USD 1.45 Billion |
| Market Forecast in 2030 (Value) | USD 2.53 Billion |
| Growth Rate | CAGR of 10.2% from 2025–2030 |
| Years Considered | 2021–2030 |
| Base Year | 2024 |
| Forecast Period | 2025–2030 |
| Units Considered | Value (USD Billion), Volume (Thousand Units) |
| Report Coverage | Revenue forecast, company ranking, competitive landscape, growth factors, and trends. |
| Segments Covered |
|
| Regional Scope | North America, Europe, Asia Pacific, and the RoW |
WHAT IS IN IT FOR YOU: DATA CENTER ACCESS CONTROL MARKET REPORT CONTENT GUIDE
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Security System OEM/Hardware Manufacturer |
|
Strengthens product roadmap planning, supports certification and compliance readiness, and enhances competitive positioning across global data center hubs. |
| Software Vendor/System Integrator |
|
Enables development of unified security platforms, improves GTM strategies for ACaaS and zero-trust solutions, and accelerates enterprise adoption through stronger interoperability insights. |
| Distributor/Channel Partner |
|
Optimizes channel strategies, strengthens inventory and pricing decisions, and enhances profitability by aligning with global demand patterns and hyperscale procurement cycles more effectively. |
RECENT DEVELOPMENTS
- August 2025 : ASSA ABLOY acquired SiteOwl, a US-based cloud platform for physical security lifecycle management. The move strengthens ASSA ABLOY’s access control offering by enhancing how integrators, service providers, and end users manage infrastructure. Combining SiteOwl’s digital platform with ASSA ABLOY’s expertise enables new growth opportunities, streamlined lifecycle management, and positions the company as a leader in security’s digital transformation.
- August 2025 : Allegion acquired Brisant Secure Limited, a UK-based provider of residential security hardware known for its Ultion high-security locks and key systems. The deal strengthens Allegion’s European portfolio, complementing Allegion UK’s non-residential offerings and recent UAP acquisition.
- June 2025 : Suprema expanded its Access Control Unit (ACU) portfolio with the CoreStation 20 (CS-20) and Door Interface (DI-24) module. The CS-20 is a compact RFID controller supporting 500,000 users with PoE+ and encrypted communication, while the DI-24 manages two doors and four readers. These devices enhance scalability, security, and deployment flexibility for diverse facilities.
Table of Contents

Methodology
The research process for this technical, market-oriented, and commercial study of the Data Center Access Control Market included the systematic gathering, recording, and analysis of data about companies operating in the market. It involved the extensive use of secondary sources, directories, and databases (Factiva, Oanda, and OneSource) to identify and collect relevant information. In-depth interviews were conducted with various primary respondents, including experts from core and related industries and preferred manufacturers, to obtain and verify critical qualitative and quantitative information as well as to assess the growth prospects of the market. Key players in the Data Center Access Control Market were identified through secondary research, and their market rankings were determined through primary and secondary research. This included studying annual reports of top players and interviewing key industry experts, such as CEOs, directors, and marketing executives.
Secondary Research
In the secondary research process, various secondary sources were used to identify and collect information for this study. These include annual reports, press releases, and investor presentations of companies, whitepapers, certified publications, and articles from recognized associations and government publishing sources. Research reports from a few consortiums and councils were also consulted to structure qualitative content. Secondary sources included corporate filings (such as annual reports, investor presentations, and financial statements); trade, business, and professional associations; white papers; Journals and certified publications; articles by recognized authors; gold-standard and silver-standard websites; directories; and databases.
Primary Research
Primary research was also conducted to identify the segmentation types, key players, competitive landscape, and key market dynamics, such as drivers, restraints, opportunities, challenges, and industry trends, along with key strategies adopted by players operating in the Data Center Access Control Market. Extensive qualitative and quantitative analyses were performed on the complete market engineering process to list key information and insights throughout the report.
Extensive primary research has been conducted after acquiring knowledge about the Data Center Access Control Market scenario through secondary research. Several primary interviews have been conducted with experts from both the demand (end users) and supply side (access control manufacturers/providers) across four major geographic regions: North America, Europe, Asia Pacific, and RoW. Approximately 80% and 20% of the primary interviews were conducted from the supply and demand side, respectively. These primary data have been collected through questionnaires, emails, and telephonic interviews.
Market Size Estimation
In the complete market engineering process, both top-down and bottom-up approaches were implemented, along with several data triangulation methods, to estimate and validate the size of the Data Center Access Control Market and various other dependent submarkets. Key players in the market were identified through secondary research, and their market share in the respective regions was determined through primary and secondary research. This entire research methodology included the study of annual and financial reports of the top players, as well as interviews with experts (such as CEOs, VPs, directors, and marketing executives) for key insights (quantitative and qualitative).
All percentage shares, splits, and breakdowns were determined using secondary sources and verified through primary sources. All the possible parameters that affect the markets covered in this research study were accounted for, viewed in detail, verified through primary research, and analyzed to obtain the final quantitative and qualitative data. This data was consolidated and supplemented with detailed inputs and analysis from MarketsandMarkets and presented in this report.
Bottom-Up Approach
- Identifying various verticals wherein access control systems are implemented
- Analyzing each vertical and identifying the providers of access control systems and services to these verticals
- Understanding the demand generated by companies in each vertical
- Tracking the ongoing and upcoming implementation of access control systems by various companies in each region and forecasting the size of the Data Center Access Control Market based on these developments and other critical parameters
- Analyzing major companies in the access control ecosystem, studying their portfolios, and understanding different types of access control solutions
- Estimating the market for access control systems for each vertical
- Multiplying the penetration of access control technology by the estimated revenue generated from access control solutions to arrive at the expected market size of access control in 2024
- Tracking the ongoing and upcoming developments in the market, such as investments, R&D activities, product developments, and partnerships, and forecasting the market based on these developments and other critical parameters
- Studying various paid and unpaid sources of information, such as annual reports, press releases, white papers, and databases
- Carrying out multiple discussions with key opinion leaders to understand different access control offerings, services, verticals, and recent trends in the market, and analyzing the breakup of the scope of work carried out by major companies
- Verifying and cross-checking the estimates at every level through discussion with key opinion leaders such as CXOs, directors, and operations managers, and finally with the domain experts in MarketsandMarkets
Top-Down Approach
- Focusing initially on the top-line investments and expenditures made in the access control ecosystem, further splitting the key market areas into offerings, verticals, and regions, and listing key developments
- Identifying all leading players and end users in the Data Center Access Control Market based on type and offering, through secondary research, and fully verifying them through a brief discussion with industry experts
- Analyzing revenues, product mixes, geographic presence, and key applications served by all identified players to estimate and arrive at percentage splits for all key segments
- Discussing splits with the industry experts to validate the information and identify key growth pockets across all key segments
- Breaking down the total market based on verified splits and key growth pockets across all segments
Data Triangulation
After arriving at the overall market size from the market size estimation process, as explained above, the total market has been split into several segments and subsegments. To complete the overall market engineering process and arrive at the exact statistics for all segments and subsegments, market breakdown and data triangulation procedures have been employed, wherever applicable. The data have been triangulated by studying various factors and trends from both the demand and supply sides. Along with this, the market has been validated using top-down and bottom-up approaches.
Market Definition
Access control is a security technique that regulates communication between users and systems. It restricts the entry of unauthorized individuals into restricted areas to protect people and assets. An access control system provides secure access to physical resources by validating user credentials. Every vertical has specific security requirements—from excluding intruders and limiting access to dangerous or sensitive areas to protecting valuable assets and equipment or ensuring the safety of secluded areas.
Key Stakeholders
- Suppliers of raw materials and manufacturing equipment
- Providers and manufacturers of components
- Providers of software solutions
- Manufacturers and providers of devices
- Original equipment manufacturers (OEMs)
- ODM and OEM technology solution providers
- Suppliers and distributors of access control devices
- System integrators
- Middleware providers
- Assembly, testing, and packaging vendors
- Market research and consulting firms
- Associations, organizations, forums, and alliances related to the access control industry
- Technology investors
- Governments, regulatory bodies, and financial institutions
- Venture capitalists, private equity firms, and startups
- End users
Report Objectives
- To define, describe, segment, and forecast the size of the Data Center Access Control Market, in terms of offering, access control as a service, vertical, and region
- To forecast the size of the market segments for four major regions: North America, Europe, Asia Pacific, and RoW
- To give detailed information regarding drivers, restraints, opportunities, and challenges influencing the growth of the market
- To provide value chain analysis, ecosystem analysis, case study analysis, patent analysis, trade analysis, technology analysis, pricing analysis, key conferences and events, key stakeholders and buying criteria, Porter's five forces analysis, investment and funding scenario, and regulations pertaining to the market
- To strategically analyze micromarkets with regard to individual growth trends, prospects, and contributions to the total market
- To analyze opportunities for stakeholders by identifying high-growth segments of the market
- To strategically profile the key players, comprehensively analyze their market positions in terms of ranking and core competencies, and provide a competitive market landscape
- To analyze strategic approaches, such as product launches, acquisitions, agreements, and partnerships, in the Data Center Access Control Market
Available Customizations
With the given market data, MarketsandMarkets offers customizations according to the company's specific needs. The following customization options are available for the report:
Company Information:
- Detailed analysis and profiling of additional market players (up to 7)
Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the Data Center Access Control Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free Customisation














Growth opportunities and latent adjacency in Data Center Access Control Market