
Government & Public Sector Cybersecurity Market
Government & Public Sector Cybersecurity Market by Solution Type (IAM, Firewall & VPN, Log Management & SIEM), Security Type (Cloud, Application, Network), End Use Vertical (Federal/National, State & Local, Defense & Intelligence) - Forecast to 2030




OVERVIEW
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
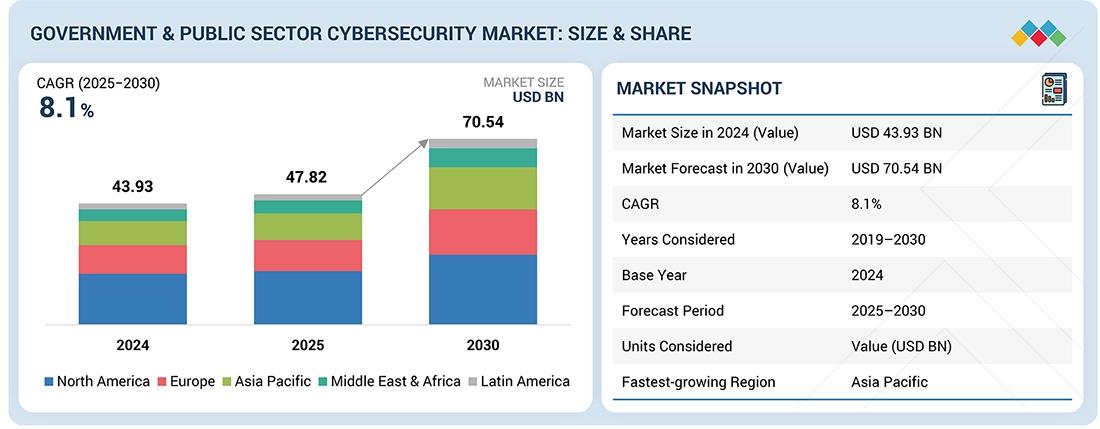
The government and public sector cybersecurity market is expected to rise from USD 47.82 billion in 2025 to USD 70.54 billion by 2030 at a CAGR of 8.1%. This growth is mainly led by government-driven, stronger cross-border partnerships and regional cybersecurity alliances. Agencies are working more closely together to tackle advanced and coordinated cyber threats. For instance, trilateral defence research between the United States, the United Kingdom, and Canada is helping propel shared cyber defence capabilities. Additionally, Australia-led partnerships across the Asia Pacific are enhancing coordination for threat detection and response. Collectively, there is a rise in interoperable cybersecurity solutions and managed services in public-sector organizations.
KEY TAKEAWAYS
-
BY REGIONBy region, North America is projected to have the largest market share in 2025.
-
BY OFFERINGBy offering, solutions are projected to dominate the market in terms of market share during the forecast period.
-
BY SOLUTION TYPEBy solution type, the log management & SIEM segment is projected to lead in terms of growth rate.
-
BY SECURITY TYPEBy security type, network security is estimated to dominate the market in 2025.
-
BY DEPLOYMENT MODECloud deployment is projected to grow at the fastest rate from 2025 to 2030.
-
BY END USE VERTICALBy end use vertical, the state & local government segment is projected to grow the fastest during the forecast period.
-
COMPETITIVE LANDSCAPE - KEY PLAYERSPalo Alto Networks, Fortinet, Cisco, Microsoft, and Check Point lead the government and public sector cybersecurity landscape with mature, interoperable platforms that span network defense, secure cloud access, identity governance, endpoint protection, and AI-driven threat detection. The companies' extensive certification portfolios, including FedRAMP, StateRAMP, DoD Impact Levels, and regional compliance standards, position them as trusted vendors for national cyber programmes and mission-critical public infrastructure.
-
COMPETITIVE LANDSCAPE - STARTUPSDragos, Claroty, Recorded Future, Vectra AI, and Magnet Forensics are among the fastest-growing cybersecurity specialists supporting government and public sector missions. The companies' expertise spans OT and ICS security for critical infrastructure, AI-driven network detection, cyber-threat intelligence for national security operations, and digital forensics tooling for law enforcement agencies. These companies offer rapid deployment, high-fidelity analytics, and mission-focused solutions that address emerging government priorities, such as critical infrastructure resilience, intelligence-led threat hunting, and secure service modernization.
Cybersecurity demand is also rising as more government services go online and cyber threats become more complex. Systems like taxation platforms, identity management tools, and citizen portals are being digitalized, which naturally increases exposure to attacks. Ongoing ransomware attacks, espionage efforts, and increasingly advanced malware operations are pushing government agencies to reinforce their cybersecurity posture. Because many organizations lack sufficient in-house expertise, they are turning to third-party tools and managed security services for support. At the same time, governments are placing greater emphasis on zero-trust models, AI-enabled threat detection, and cloud-compatible security solutions to strengthen overall resilience. Compliance requirements, data protection regulations, and the need for round-the-clock monitoring are also influencing how agencies allocate their security budgets. In parallel, there is growing interest in cybersecurity automation, shared threat intelligence, and secure remote access technologies to ensure continuity of operations and safeguard sensitive citizen information.
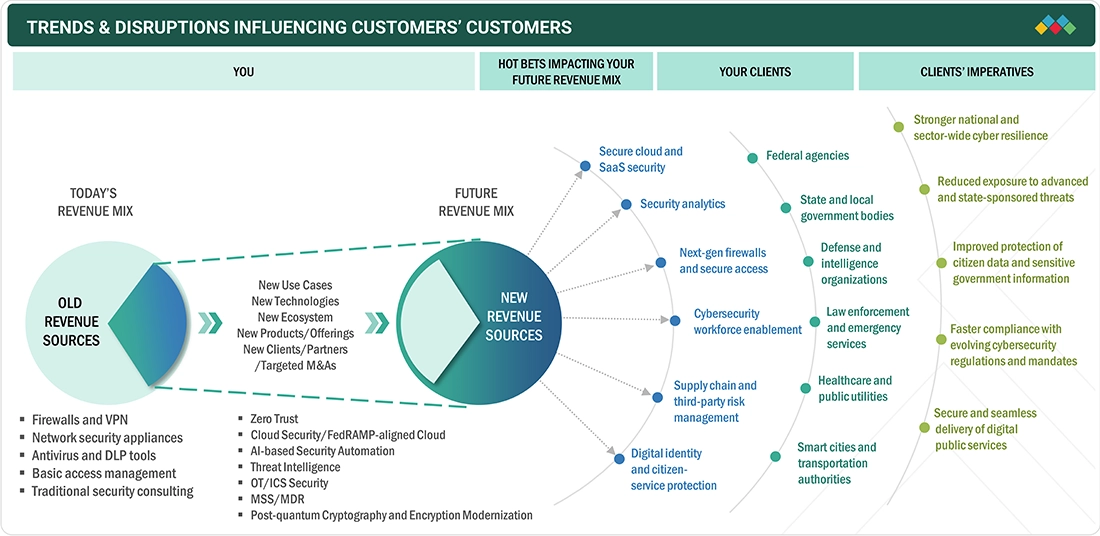
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
This figure illustrates how the evolving threat environment, new compliance regulations, and the rapid digitalization of government services are reshaping spending priorities in public-sector cybersecurity. Traditional security tools are being replaced by cloud-ready platforms, Zero Trust models, and analytics-driven solutions that better support essential government operations. Advances such as AI-powered automation, post-quantum encryption, and improved threat intelligence are accelerating this shift. Agencies are investing in cloud and SaaS security, next-generation firewalls, workforce enablement, and digital identity protection to secure citizen data, maintain service continuity, strengthen resilience, meet regulatory demands, and deliver reliable digital services across government sectors.
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Zero-Trust mandates accelerating nationwide government network modernization initiatives

-
Sovereign cloud and FedRAMP-aligned platforms accelerating government modernization
Level
-
Legacy OT systems limit integration with modern cyber-defense stacks
-
Fragmented procurement slows deployment of cloud-secure infrastructures across agencies
Level
-
Rapid digital-government expansion increasing demand for cyber-resilient citizen services
-
Quantum-resilient encryption adoption enabling long-term sovereign cyber readiness
Level
-
AI-powered phishing and deepfake attacks overwhelming government SOC capacity
-
Critical infrastructure OT remains exposed due to low cyber visibility
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Zero-Trust mandates accelerating nationwide government network modernization initiatives
Zero Trust is quickly becoming a major driver of cybersecurity investment. Governments want continuous verification, identity-focused controls, and micro-segmented networks. In the US, for instance, CISA’s Zero Trust Maturity Model offers a roadmap guiding agencies on phishing-resistant MFA, network segmentation, and real-time monitoring to reduce credential misuse and lateral movement. Similar strategies are being picked up around the world, as governments update older systems and shore up defences against sophisticated attacks. This is helping to keep cybersecurity spending steady.
Restraint: Legacy OT systems limit integration with modern cyber-defense stacks
Despite modernization efforts, many departments still rely on older on-premises systems. These systems aren’t compatible with cloud-native architectures, automated workflows, or Zero Trust controls. A recent GAO review found that multiple US federal agencies continue to use decades-old systems, which limit advanced threat detection, secure APIs, and modern identity services. These outdated setups add operational risk and slow modernization, forcing agencies to balance transformation with keeping public services running smoothly.
Opportunity: Quantum-resilient encryption adoption enabling long-term sovereign cyber readiness
Governments are beginning to realize the need to step up their game when it comes to securing data against the future risks posed by quantum computers. Australia, for instance, is backing companies like QuintessenceLabs, which are at the forefront of developing quantum-safe encryption and technologies like quantum key distribution. By investing in these innovations, they’re aiming to stay ahead of the curve and protect sensitive national data from future threats, especially from potential "harvest now, decrypt later" attacks. This is particularly important in sectors like defense, public administration, and critical infrastructure, where security is non-negotiable.
Challenge: AI-powered phishing and deepfake attacks overwhelming government SOC capacity
Government agencies are seeing more AI-enabled cyberattacks. These include automated phishing, realistic deepfake impersonations, and generative malware that can bypass traditional defenses. Europol reports that AI is helping attackers craft highly targeted campaigns that exploit both human and procedural weaknesses. These threats put extra pressure on SOC teams, who now rely on advanced detection tools, behavioral analytics, and AI-assisted threat hunting to keep operations resilient.
GOVERNMENT & PUBLIC SECTOR CYBERSECURITY MARKET: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
The London Borough of Hounslow replaced its remote-site networks with Cisco technology, enabling “smart-borough” services like environmental sensors, automated service workflows, and improved resident data protection. | Faster deployment of smart services and digital governance. Stronger network security — internal tests failed unauthorized access attempts. Improved attractiveness as employer helps retain/attract talent |
 |
Hornsby Shire Council modernized its aging IT infrastructure using Fortinet Secure SD-WAN and next-gen firewall/SD-Branch, enabling central network segmentation, 4G/5G backup for mobile teams, unified policy enforcement, and support for digital services. | ~50% reduction in communications costs. Enhanced resilience and redundancy of council networks. Improved readiness for Zero-Trust access and IoT integration. Better user experience and stronger cybersecurity posture |
 |
A central government department implemented a “simple, secure, connected cybersecurity” framework using Palo Alto Networks solutions to streamline operations, enforce Zero Trust, and consolidate security stacks across agencies. | Efficient unified security architecture reducing complexity. Enhanced data protection, compliance, and secure hybrid-work/cloud access. Stronger incident response and continuous threat defence, optimizing public-sector security posture |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The cybersecurity ecosystem reflects the combined capabilities of key solution and service providers. Core vendors help with secure infrastructure, cloud adoption, and threat prevention, while specialized service providers cover intelligence, OT security, forensics, and managed operations. Together, they form the backbone of resilient digital governance and stronger national cyber defense.

Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
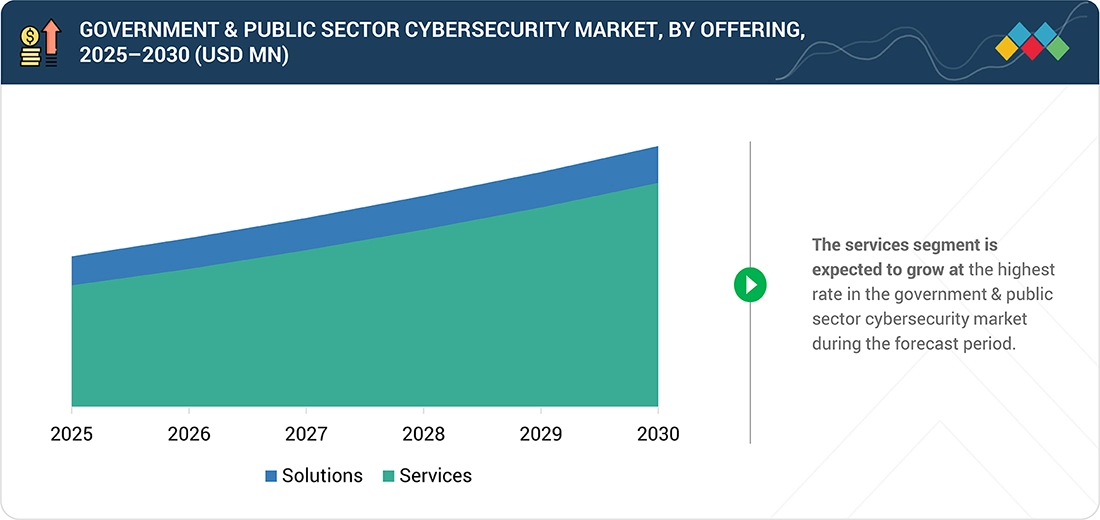
Government & Public Sector Cybersecurity Market, by Offering
Solutions dominate because government agencies need hardened, certifiable, and scalable tools that can protect complex systems consistently. From firewalls and endpoint protection to identity platforms and analytics, these tools form the backbone of digital-government operations. Agencies often prefer products validated by vendors and certified under FedRAMP, StateRAMP, or national security standards. For instance, US federal departments widely use platforms from Palo Alto Networks, Cisco, and Microsoft to secure cloud workloads, automate SOC operations, and implement Zero Trust across multiple agencies.
Government & Public Sector Cybersecurity Market, by Solution Type
Firewalls and VPNs hold the largest market share because many government networks still rely on hybrid or legacy environments that need strong perimeter protection and secure remote access. These tools are critical for safeguarding classified networks, inter-agency data transfers, and sensitive workflows. During the pandemic, many agencies expanded VPN capacity to support remote staff and field personnel, reinforcing reliance on these tools. Modern next-generation firewalls now combine intrusion prevention, deep packet inspection, and encrypted tunnels to keep communications secure across distributed public-sector networks.
Government & Public Sector Cybersecurity Market, by Security Type
Network security dominates due to the size and sensitivity of public-sector networks connecting ministries, defense units, critical infrastructure, and public service platforms. Governments need to protect high-value assets like citizen registries, intelligence databases, and national communications against intrusions. National CERTs and defense cyber commands continue using monitoring, segmentation, and intrusion-prevention tools to counter advanced persistent threats. For example, several European governments stepped up network security after noticing increased state-sponsored scanning, prompting further investment in foundational capabilities.
Government & Public Sector Cybersecurity Market, by Deployment Mode
On-premises deployments still account for the largest share because many government workloads, especially those involving national security, law enforcement, defense logistics, or classified intelligence, can’t be moved to commercial cloud environments. Sovereign data requirements, internal audits, and mission-critical operations require secure on-site hosting. Defence ministries continue to maintain air-gapped or restricted networks for command-and-control operations. Even with growing cloud adoption, agencies rely on on-premises systems for encryption key management, secure processing, and national cyber operations, keeping demand for these setups high.
Government & Public Sector Cybersecurity Market, by End Use Vertical
Federal and national governments hold the largest market share because they manage the most complex and high-value cyber environments. These include defense networks, border control systems, intelligence platforms, and citizen databases. These institutions are frequent targets for nation-state attacks, prompting heavy investment in Zero Trust, sovereign cloud, and advanced threat detection. For instance, the US federal government’s Executive Order 14028 launched a multi-year modernization program, speeding up upgrades in identity security, software supply chain protection, and cyber readiness nationwide. Similar programs in Europe, India, and the Middle East continue to reinforce the segment’s dominance.
REGION
Asia Pacific to be fastest-growing region in government & public sector cybersecurity market during forecast period
The Asia Pacific region is growing the fastest because of rapid digital-government expansion, accelerated cloud adoption, and rising cyber threats targeting national infrastructure. Governments here are heavily investing in Zero Trust, SOC modernization, and cyber-resilience programs, while public-private partnerships strengthen capabilities across defense, critical infrastructure, and citizen services. For example, Singapore’s Government Technology Agency (GovTech) is implementing advanced cybersecurity frameworks for smart city projects, India is scaling its National Cyber Security Strategy to protect digital services, and Australia is modernizing its federal SOCs as a core part of its 2023-2030 Cyber Security Strategy to respond to growing cyber threats.
GOVERNMENT & PUBLIC SECTOR CYBERSECURITY MARKET: COMPANY EVALUATION MATRIX
The government and public sector cybersecurity market features a balanced mix of dominant platform providers and rapidly advancing innovators. Leading players such as Palo Alto Networks continue to strengthen their position through comprehensive cloud, network, and Zero Trust capabilities tailored for federal and national security environments, placing them firmly in the “Stars” quadrant. Emerging leaders like Zscaler are gaining momentum by enabling secure cloud transformation, identity-first access, and scalable Zero Trust architectures widely adopted by public agencies. Across the broader landscape, vendors are expanding threat intelligence, OT security, and AI-driven detection to meet stringent government compliance requirements and protect mission-critical infrastructure.
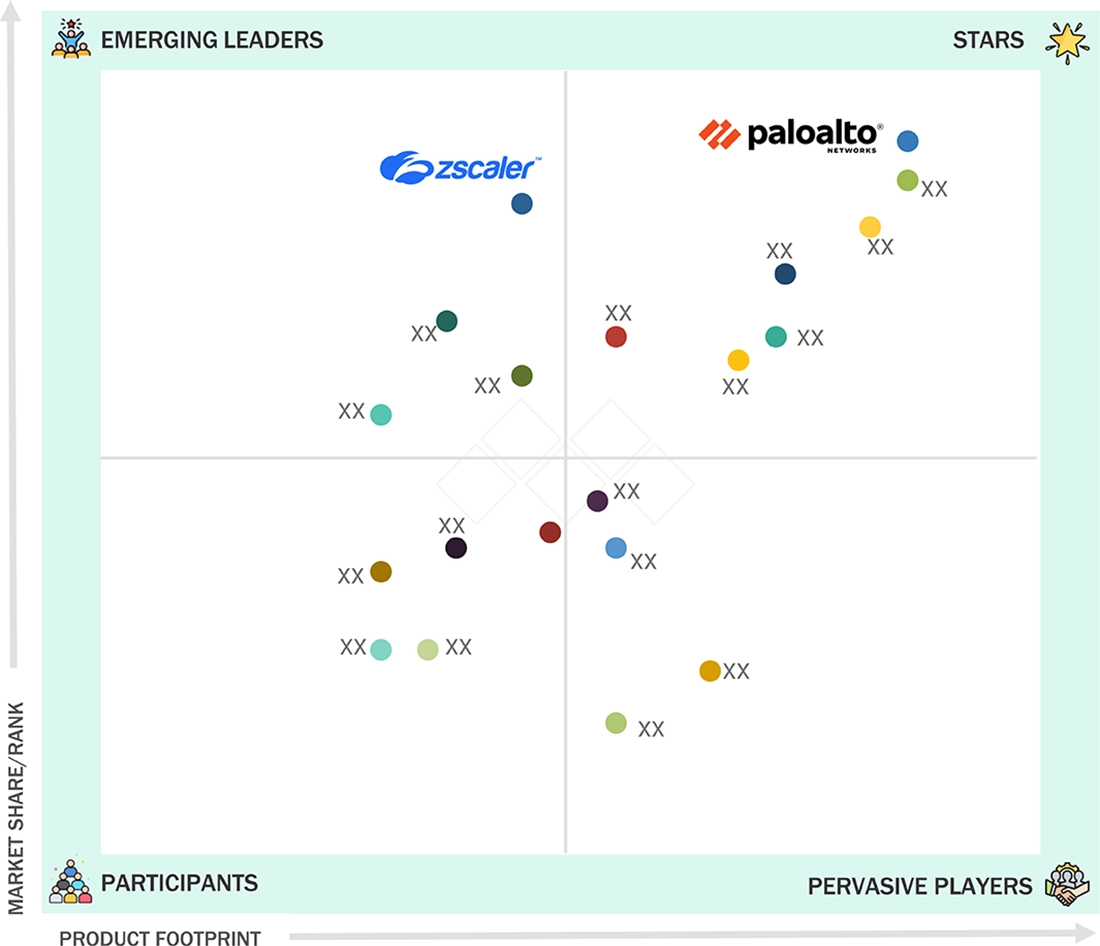
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
- Palo Alto Networks (US)
- Fortinet (US)
- Cisco (US)
- CrowdStrike (US)
- Check Point (Israel)
- Microsoft (US)
- Zscaler (US)
- Tenable (US)
- CyberArk (US)
- BAE Systems (UK)
- Honeywell (US)
- Dragos (US)
- Claroty (US)
- Forescout (US)
- Vectra AI (US)
- Magnet Forensics (Canada)
- Recorded Future (US)
- Cydome (Israel)
- Heimdal Security (Denmark)
- Cybereason (US)
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size, 2024 (Value) | USD 43.93 Billion |
| Market Forecast, 2030 (Value) | USD 70.54 Billion |
| Growth Rate | CAGR of 8.1% from 2025 to 2030 |
| Years Considered | 2019–2030 |
| Base Year | 2024 |
| Forecast Period | 2025–2030 |
| Units Considered | Value (USD Billion) |
| Report Coverage | Revenue Forecast, Company Ranking, Competitive Landscape, Growth Factors, and Trends |
| Segments Covered |
|
| Regions Covered | North America, Europe, Asia Pacific, Middle East & Africa, Latin America |
WHAT IS IN IT FOR YOU: GOVERNMENT & PUBLIC SECTOR CYBERSECURITY MARKET REPORT CONTENT GUIDE
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Leading Solution Provider (US) | Solution Benchmarking: Comprehensive evaluation of government-grade cybersecurity portfolios across top vendors, covering network security, cloud, and Zero Trust architectures, identity governance, SIEM/SOC analytics, and secure infrastructure solutions aligned with national cybersecurity frameworks and compliance mandates. | Enhanced visibility into competitive strengths, compliance readiness, and technology differentiation, enabling prioritization of investments for stronger positioning in federal, state, and critical-infrastructure cybersecurity programs. |
| Leading Service Provider (EU) | Company Profiles: Detailed profiling of top service-focused cybersecurity providers (up to 5), including managed detection and response, SOC modernization, incident response, OT/ICS security services, and integration capabilities supporting government agencies and public-sector institutions. | Actionable insights into partnership potential, service delivery gaps, and go-to-market strategies to expand presence across high-demand public-sector segments such as national agencies, defense organizations, and critical infrastructure operators. |
RECENT DEVELOPMENTS
- December 2025: Palo Alto Networks received a U.S. General Services Administration OneGov agreement that provides federal agencies with discounted access to its AI-driven security, cloud protection, Zero Trust, and next-generation firewall capabilities to accelerate secure government modernization.
- September 2025: Microsoft secured a multi-billion-dollar OneGov agreement with the US General Services Administration, offering steep discounts on Microsoft 365, Copilot, and Azure services to strengthen secure, AI-enabled federal digital transformation.
- September 2025: Zscaler launched FedRAMP Moderate-aligned international data centers and an enhanced government experience designed to support Zero Trust adoption and operational resilience for US federal and defense customers.
- June 2025: Forescout announced a partnership with Coalfire to deliver FedRAMP-authorized cybersecurity solutions for US public sector agencies, enabling cloud-ready device visibility and strengthened Zero Trust-based device security.
Table of Contents

Methodology
Secondary research was conducted to collect information useful for this technical, market-oriented, and commercial study of the global Government & Public Sector Cybersecurity Market . The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, such as top-down and bottom-up, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the market size of the segments and subsegments of the Government & Public Sector Cybersecurity Market .
Secondary Research
In the secondary research process, various secondary sources were referred to for identifying and collecting information regarding the study. The secondary sources included annual reports, press releases, investor presentations of cybersecurity solution and service vendors, forums, certified publications, and whitepapers. The secondary research was mainly used to obtain key information about the industry’s supply chain, the total pool of key players, market classification and segmentation according to industry trends to the bottom-most level, regional markets, and key developments from both market- and technology-oriented perspectives, all of which were further validated by primary sources.
Primary Research
In the primary research process, various primary sources from both the supply and demand sides were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included various industry experts, including Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the Government & Public Sector Cybersecurity Market .
In the market engineering process, top-down and bottom-up approaches were extensively used, along with several data triangulation methods, to perform the market estimation and market forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list key information/insights throughout the report.
After the complete market engineering process (including calculations for market statistics, market breakups, market size estimations, market forecasts, and data triangulation), extensive primary research was conducted to gather information and verify & validate the critical numbers arrived at. The primary research was also conducted to identify the segmentation, industry trends, competitive landscape of Government & Public Sector Cybersecurity Market players, and key market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key strategies.
Market Size Estimation
Top-down and bottom-up approaches were used to estimate and validate the size of the Government & Public Sector Cybersecurity Market and the size of various dependent sub-segments in the overall Government & Public Sector Cybersecurity Market . The research methodology used to estimate the market size includes the following details: critical players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure included the study of the annual and financial reports of the top market players, and extensive interviews were conducted for key insights from the industry leaders, such as CEOs, VPs, directors, and marketing executives.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study have been accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data is consolidated and added to detailed input and analysis from MarketsandMarkets.
Data Triangulation
The market was split into several segments and subsegments after arriving at the overall market size using the market size estimation processes explained above. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
According to MarketsandMarkets, cybersecurity is a set of technologies, processes, and practices to fortify critical systems, such as networks, physical devices, programs, and information, from unauthorized access, insider threats, and malicious attacks. These cyberattacks can affect data transmission across the networks, cause operational disruptions, and result in money extortion/ransomware. Cybersecurity, or information security, can be provided through hardware, software, and services.
Stakeholders
- Chief Technology and Data Officers
- Consulting Service Providers
- Managed Security Services Professionals
- Business Analysts
- Information Technology (IT) Professionals
- Government Agencies
- Investors and Venture Capitalists
- Small and Medium-sized Enterprises (SMEs) and Large Enterprises
- Third-party Providers
- Consultants/Consultancies/Advisory Firms
- Managed and Professional Service Providers
Report Objectives
- To describe and forecast the global Government & Public Sector Cybersecurity Market by offering, solution type, security type, deployment mode, organization size, vertical, and region from 2025 to 2030, and analyze the various macroeconomic and microeconomic factors that affect market growth
- To forecast the market size of five main regions: North America, Europe, Asia Pacific, the Middle East & Africa, and Latin America
- To analyze the subsegments of the market with respect to individual growth trends, prospects, and contributions to the overall market
- To provide detailed information regarding major factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
- To analyze opportunities in the market for stakeholders and provide details of the competitive landscape of major players
- To profile key market players; provide a comparative analysis based on the business overviews, regional presence, product offerings, business strategies, and key financials; and illustrate the competitive landscape of the marketTo analyze competitive developments, such as mergers & acquisitions, product developments, partnerships and collaborations, and research & development (R&D) activities, in the market
Available Customizations
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis as per Feasibility
- Further breakup of the Asia Pacific market into countries contributes to the rest of the regional market size
- Further breakup of the North American market into countries contributes to the rest of the regional market size
- Further breakup of the Latin American market into countries contributing to the rest of the regional market size
- Further breakup of the Middle East & African market into countries contributing to the rest of the regional market size
- Further breakup of the European market into countries contributes to the rest of the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)
Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the Government & Public Sector Cybersecurity Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free Customisation














Growth opportunities and latent adjacency in Government & Public Sector Cybersecurity Market