
Middle East & Africa (MEA) Operational Technology (OT) Security Market
Middle East & Africa (MEA) Operational Technology (OT) Security Market by Solution (SIEM, Network Security, Vulnerability Management, IAM, Data Security), Service (Incident Response, Risk & Threat Management, Managed Security) - Forecast to 2030




OVERVIEW
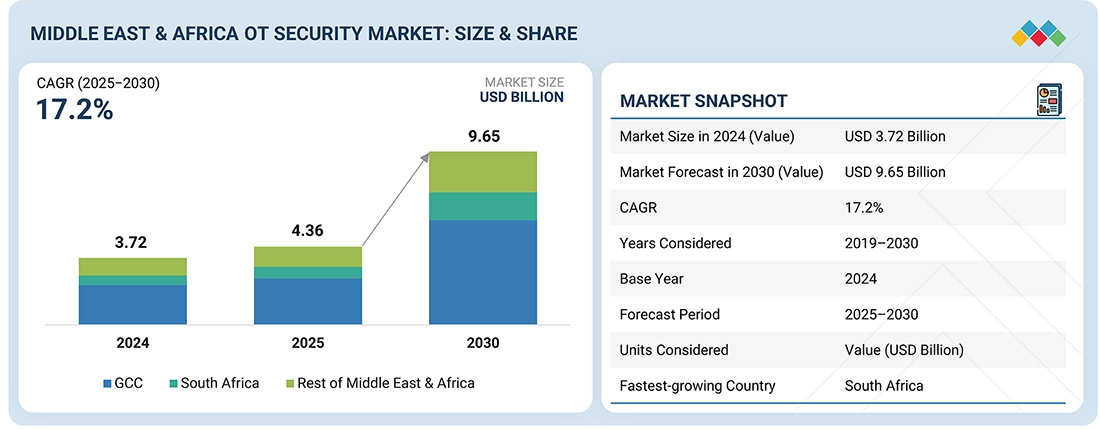
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
The Middle East & Africa (MEA) OT security market is projected to grow from USD 4.36 billion in 2025 to USD 9.65 billion by 2030, at a CAGR of 17.2%. The growing cyber threats to critical infrastructure in the MEA are raising awareness of the vulnerabilities of power grids, oil and gas infrastructure, transportation systems, and water systems. The GCC, Israel, and the northern part of Africa have been experiencing high-profile incidents that are forcing operators to implement intrusion detection, asset visibility, and continuous monitoring solutions. At the same time, large-scale infrastructure initiatives and industrial digitalization efforts are expanding connectivity across OT environments, intensifying the need for robust OT security to safeguard industrial control systems and maintain operational reliability.
KEY TAKEAWAYS
-
BY OFFERINGBy offering, solutions are expected to dominate the OT security market in the MEA region in 2025.
-
BY SOLUTIONSBy solution, the IAM segment is likely to witness the highest CAGR during the forecast period.
-
BY SERVICESBy service type, consulting & integration services are likely to capture the largest market share in 2025.
-
BY DEPLOYMENT MODEBy deployment mode, cloud-based OT security solutions are projected to exhibit a higher CAGR of 18.4% from 2025 to 2030.
-
BY ORGANIZATION SIZEBy organization size, SMEs are projected to record a higher CAGR of 19.1% during the forecast period.
-
BY VERTICALBy vertical, the energy & power segment is likely to register the fastest growth rate of 19.0% during the forecast period.
-
COMPETITIVE LANDSCAPE - KEY PLAYERSCheck Point, Radiflow, and Help AG are leaders in the Middle East & Africa OT security market, offering comprehensive portfolios of network security solutions, OT risk management solutions, and managed security services. Their regional focus, understanding of the industrial domain, and focus on meeting key infrastructure needs make them preferred partners of energy, utility, transportation, and government operators in the region.
-
COMPETITIVE LANDSCAPE - STARTUPSCydome and Shield-IoT are emerging among the OT security startups in the MEA region with specialized security models. These organizations provide dedicated offerings including maritime OT security, embedded security, asset monitoring, and lightweight monitoring to assist organizations in search of flexible, scalable, and cost-effective OT security to fit particular operational settings.
Stringent regulatory oversight and national cybersecurity strategies are reinforcing the need for robust OT protection across the MEA. Governments are introducing mandates to secure critical infrastructure, enforce risk assessments, and improve incident response readiness. These measures are prompting utilities, oil and gas operators, and transportation authorities to invest in structured OT security frameworks. Compliance requirements, combined with rising accountability for service disruptions, are encouraging long-term spending on monitoring, access control, and resilience-focused OT security solutions across the region.
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
The Middle East & Africa OT security market is shifting from traditional, appliance-based security toward advanced, service-driven revenue models. As critical infrastructure operators accelerate digital transformation, demand is rising for unified asset visibility, zero-trust access, and AI-driven threat analytics. Energy, oil & gas, transportation, and water utilities are driving adoption of modern OT security capabilities that improve safety, uptime, and compliance. These changes are reshaping vendor offerings and creating new growth opportunities across the regional OT security ecosystem.
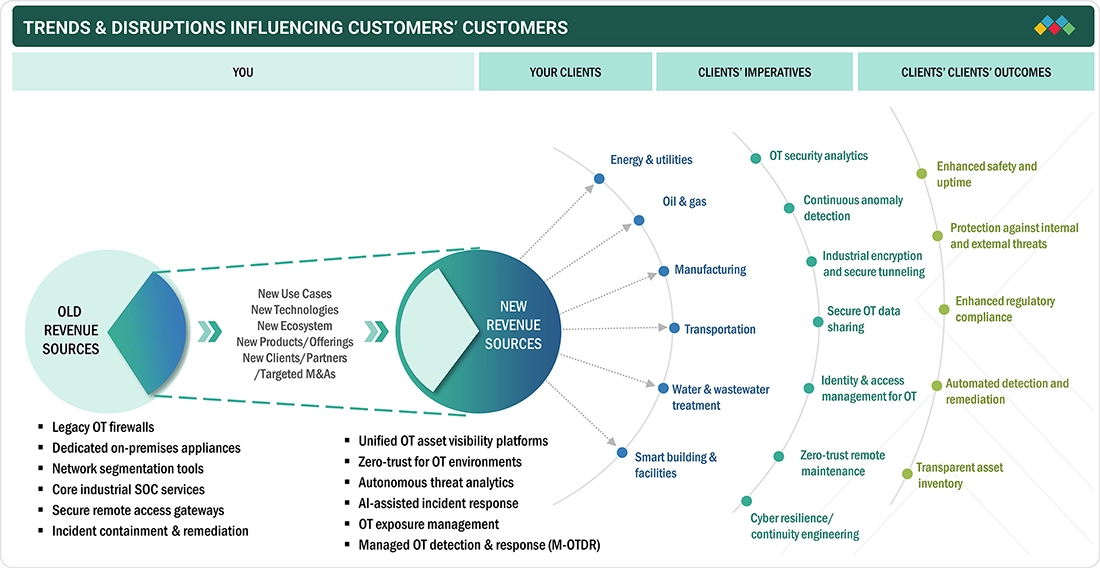
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Large-scale investments in smart cities, energy transition, rail networks, and utilities

-
National cybersecurity mandates for critical infrastructure protection
Level
-
High dependence of oil & gas and utilities sectors on legacy OT systems
-
Shortage of OT-specific security expertise in industrial operators
Level
-
Government funding to enhance critical infrastructure resilience and support digital transformation initiatives
-
Rapid adoption of managed OT security services and SOC-based monitoring solutions
Level
-
Multi-vendor industrial environments
-
Geopolitical tensions and targeted cyber campaigns
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Larg- scale investments in smart cities, energy transition, rail networks, and utilities
Large-scale investments in smart cities, energy transition projects, rail networks, and utilities are driving the growth of the Middle East & Africa OT security market. GCC countries are expanding interconnected infrastructure that relies on industrial control systems and remote operations. These environments face rising cyber exposure, increasing demand for asset visibility, network monitoring, and threat detection to protect operational continuity across critical infrastructure sectors.
Restraint: High dependence of oil & gas and utilities sectors on legacy OT systems
High dependence on legacy OT systems across oil & gas, power, and water utilities remains a key restraint for the OT security market in the MEA region. Many industrial environments operate aging control systems that lack native security features and cannot support modern monitoring tools. This limits visibility, increases deployment complexity, and raises concerns around operational disruption during security upgrades.
Opportunity: Government funding to enhance critical infrastructure resilience and support digital transformation initiatives
Government-funded initiatives offer a strong opportunity in the OT security market in the MEA region, as national policies focus on infrastructure resiliency, cybersecurity preparedness, and digitalization. GCC countries are channeling government investments into securing energy, transport, and water systems. For example, Saudi Arabia’s Vision 2030 programs continue to fund cybersecurity upgrades for critical infrastructure operators, accelerating the adoption of OT monitoring and protection solutions.
Challenge: Multi-vendor industrial environments
Managing multi-vendor industrial environments remains a structural challenge in the Middle East and Africa OT security market. Industrial operations typically rely on a heterogeneous mix of PLCs, SCADA platforms, and proprietary systems sourced from both global and regional suppliers. This fragmentation limits interoperability, constrains standardization efforts, and increases the complexity of implementing consistent, centralized security policies across geographically distributed industrial assets.
MIDDLE EAST & AFRICA (MEA) OPERATIONAL TECHNOLOGY (OT) SECURITY MARKET: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
Securing converged IT and OT networks across refineries and pipelines, protection against ransomware and lateral movement, visibility gaps in SCADA and industrial gateways, regulatory compliance pressure | Reduced OT attack surface | unified IT and OT security visibility | improved ransomware protection | stronger access control | enhanced regulatory compliance | improved operational continuity |
 |
Lack of OT asset visibility, unmanaged PLCs and substations, risk from legacy ICS, need for compliance aligned risk assessment and threat modeling | Comprehensive OT asset discovery | improved risk prioritization | early anomaly detection | strengthened grid resilience | improved compliance readiness |
 |
OT and IT exposure across maritime systems, vessel connectivity risks, lack of continuous monitoring of port operations | Improved maritime OT visibility | real-time threat detection | reduced operational disruption |enhanced safety of port infrastructure |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The Middle East & Africa OT security market is shaped by a diverse ecosystem of global cybersecurity leaders, regional specialists, and OT-focused innovators addressing the protection needs of critical infrastructure. As industries across energy, utilities, transportation, and smart cities increase connectivity, demand for OT security solutions and related services, including identity and access management, vulnerability management, asset discovery, network security, data protection, and SIEM, is increasing. This ecosystem reflects the region’s focus on securing complex, multi-vendor industrial environments while supporting regulatory compliance, operational resilience, and large-scale digital transformation initiatives.

Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
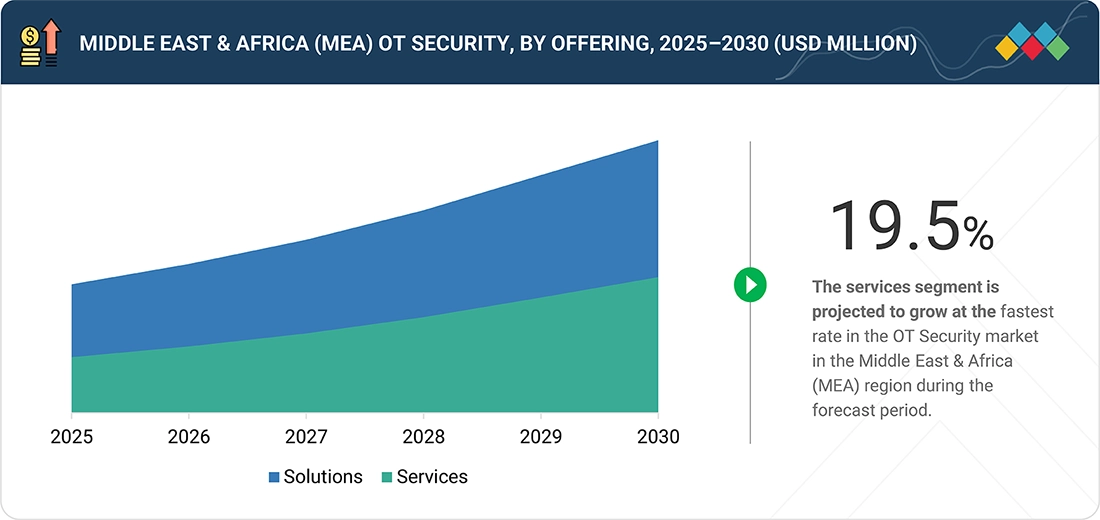
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Middle East & Africa OT Security Market, by Offering
Solutions account for the largest share, as governments and enterprises prioritize securing critical infrastructure in oil and gas facilities, power generation plants, water utilities, and transportation systems. Key focus areas include asset visibility, network monitoring, anomaly detection, and secure remote access, reflecting the growing interconnectedness of industrial environments. Ongoing infrastructure modernization across GCC countries and select African regions is further driving investment in OT security platforms, which protect ICS and SCADA networks, improve operational efficiency, and support compliance with national cybersecurity regulations.
Middle East & Africa OT Security Market, by Solution
IAM solutions lead the market due to the growing need to control access to geographically distributed industrial assets and third-party contractors. Remote operations and maintenance are common across oil and gas fields, utilities, and transport networks, increasing the risk of unauthorized access. IAM supports role-based access control, session monitoring, and zero-trust principles, enabling organizations to reduce insider risks, strengthen safety, and secure critical operational systems within complex industrial environments.
Middle East & Africa OT Security Market, by Service
Consulting and integration services account for a dominant share of the market, as many organizations depend on external expertise to secure legacy industrial environments. Service providers support OT risk assessments, security architecture design, and the integration of security solutions with existing control systems. Strong regulatory pressure, combined with limited in-house OT security capabilities, is further driving demand for advisory and integration services. These offerings help organizations align cybersecurity programs with operational continuity and safety requirements, particularly across the energy, utilities, and transportation sectors.
Middle East & Africa OT Security Market, by Deployment Mode
Cloud deployment represents the fastest-growing deployment model, as organizations pursue centralized visibility across geographically distributed industrial assets. Cloud-based platforms support remote monitoring, accelerated threat analysis, and coordinated incident response across multiple sites. Hybrid deployments that combine on-site controls with cloud-based analytics are gaining adoption, particularly within energy and infrastructure projects. These capabilities enable digital transformation while improving the efficiency and scalability of security operations.
Middle East & Africa OT Security Market, by Organization Size
SMEs are projected to register the fastest growth, driven by increasing adoption of cost-effective security solutions among smaller manufacturers, utilities, and infrastructure operators. Constraints such as limited cybersecurity personnel and growing compliance obligations are encouraging SMEs to adopt simplified OT security platforms and managed services. These offerings deliver essential visibility, monitoring, and protection without significant upfront investment, allowing smaller organizations to safeguard critical operations and mitigate cyber risk.
Middle East & Africa OT Security Market, by Vertical
The energy & power vertical is projected to record the fastest growth rate in the Middle East & Africa OT security market due to the region’s dependence on oil, gas, and electricity infrastructure. Grid modernization, remote asset management, and increased cyber threats are driving investments in monitoring and anomaly detection solutions and services. Utilities and energy operators are strengthening OT security to protect operational continuity, ensure safety, and meet stringent national cybersecurity and reliability standards.
REGION
South Africa to be fastest-growing country in Middle East & Africa OT security market during forecast period
South Africa is likely to be the fastest-growing country in the Middle East & Africa OT security market due to rising cyber risks targeting energy, mining, transportation, and water infrastructure. Increased industrial automation, grid modernization initiatives, and stronger cybersecurity regulations are driving demand for asset visibility, network monitoring, and managed OT security solutions/services across critical sectors.
MIDDLE EAST & AFRICA (MEA) OPERATIONAL TECHNOLOGY (OT) SECURITY MARKET: COMPANY EVALUATION MATRIX
The Middle East and Africa OT security market comprises established cybersecurity vendors alongside specialized OT security providers that deliver asset visibility, threat detection, and protection for critical infrastructure. Companies such as Check Point (Star) and Radiflow (Emerging Leader) play a significant role by offering advanced network security, OT risk assessment, and asset discovery solutions. Their portfolios support secure operations across energy, oil and gas, utilities, and transportation sectors, aligning with the region’s increasing emphasis on industrial resilience, regulatory compliance, and the protection of highly interconnected operational environments.
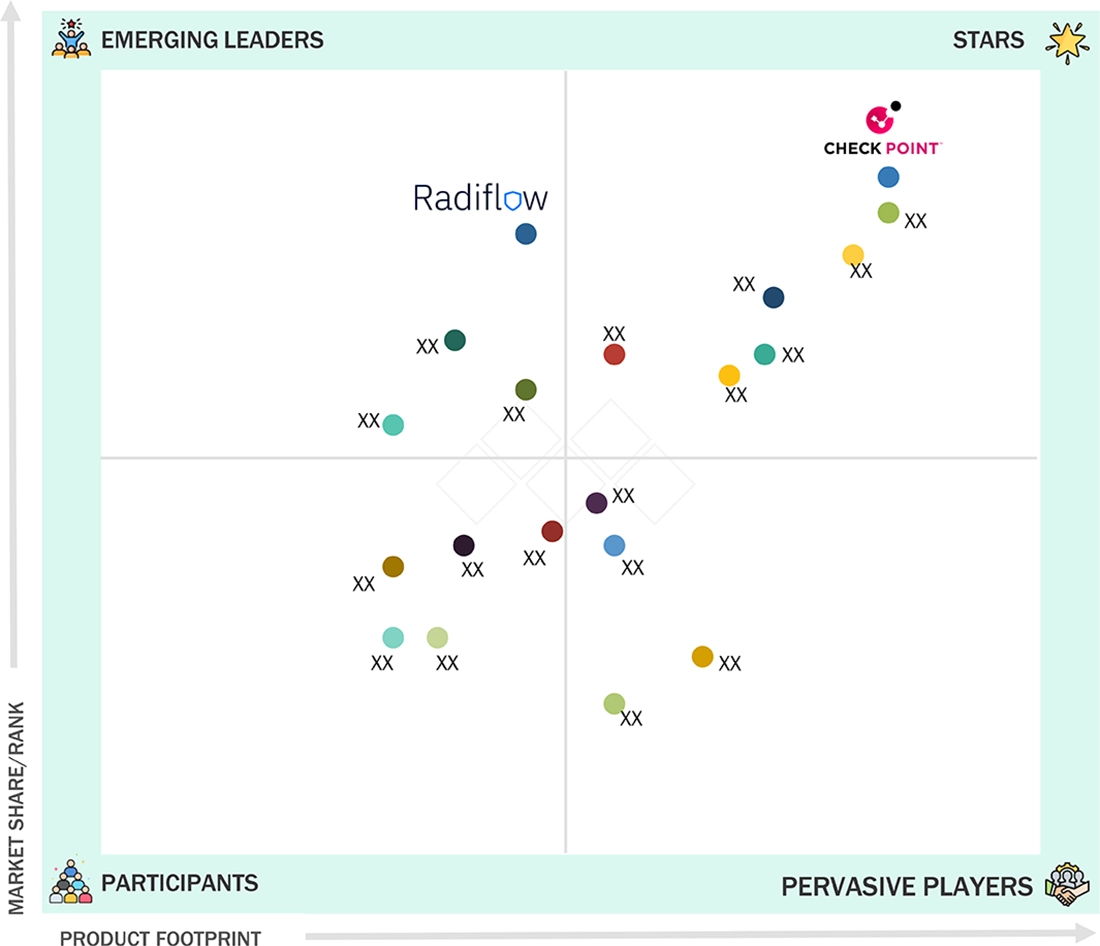
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
- Check Point (Israel)
- Radiflow (Israel)
- Shield-IoT (Israel)
- Help AG (Israel)
- Waterfall Security (Israel)
- Cisco (US)
- Fortinet (US)
- Cyberani (Israel)
- Cydome (UAE)
- CyberKnight (UAE)
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size in 2024 (Value) | USD 3.72 Billion |
| Market Size in 2030 (Value) | USD 9.65 Billion |
| Growth Rate | CAGR of 17.2% from 2025 to 2030 |
| Years Considered | 2019–2030 |
| Base Year | 2024 |
| Forecast Period | 2025–2030 |
| Units Considered | Value (USD Million/Billion) |
| Report Coverage | Revenue Forecast, Company Ranking, Competitive Landscape, Growth Factors, and Trends |
| Segments Covered |
|
WHAT IS IN IT FOR YOU: MIDDLE EAST & AFRICA (MEA) OPERATIONAL TECHNOLOGY (OT) SECURITY MARKET REPORT CONTENT GUIDE
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Leading Solution Provider (MEA) | Solution Benchmarking: Comprehensive comparison of OT security portfolios across leading vendors in the Middle East & Africa (MEA), covering asset discovery, network security, threat detection, SIEM integration, identity and access management, and OT specific analytics aligned with regional regulatory and infrastructure requirements | Enhanced clarity on competitive positioning, technology differentiation, and investment priorities for stronger regional market expansion |
| Leading Service Provider (MEA) | Company Profiles: In-depth profiling of leading OT security service providers in the MEA, covering managed OT security services, incident response, consulting, and IT OT integration capabilities across key industrial markets | Actionable insights into partnership opportunities, capability gaps, and go-to-market strategies to strengthen presence in high-growth Middle East & Africa industries. |
RECENT DEVELOPMENTS
- December 2025 : Help AG expanded its OT security managed services portfolio across the GCC by integrating advanced OT network monitoring and incident response capabilities to support energy, utilities, and transportation operators.
- October 2025 : Check Point strengthened its OT and industrial cybersecurity offerings in the Middle East by enhancing firewall and intrusion prevention capabilities tailored for ICS and SCADA environments in oil and gas facilities.
- August 2025 : Radiflow partnered with a regional system integrator in the UAE to deploy OT risk assessment and asset visibility platforms across critical infrastructure projects, supporting compliance and cyber resilience initiatives.
- May 2025 : Waterfall Security Solutions expanded deployments of its unidirectional security gateways across power and water utilities in Israel and the GCC to secure segmented OT networks from external threats.
- March 2025 : CyberKnight entered a strategic distribution agreement with an OT security vendor to expand access to OT network monitoring and anomaly detection solutions across Saudi Arabia and the wider Middle East.
Table of Contents

Methodology
This study involved estimating the current Middle East & Africa (MEA) Operational Technology (OT) security market size. Exhaustive secondary research was carried out to collect information on the Middle East & Africa (MEA) OT security industry. The next step was to validate these findings, assumptions, and sizing with industry experts across the value chain using primary research. Different approaches, such as top-down and bottom-up, were employed to estimate the total market size. After that, the market breakup and data triangulation procedures were used to estimate the size of the segments and subsegments of the Middle East & Africa (MEA) Operational Technology (OT) security market.
Secondary Research
The market for companies providing Middle East & Africa (MEA) OT security solutions and services was determined by analyzing secondary data from both paid and unpaid sources. This included reviewing the product portfolios of major companies in the ecosystem and evaluating their performance and quality. Various sources were referred to in the secondary research process to identify and collect information for this study. The secondary sources included annual reports, press releases, investor presentations of companies, white papers, journals, certified publications, and articles from recognized authors, directories, and databases.
In the secondary research process, various secondary sources were referred to to identify and collect information related to the study. Secondary sources included annual reports, press releases, and investor presentations of Middle East & Africa (MEA) OT security vendors, forums, certified publications, and whitepapers. The secondary research was used to obtain essential information on the industry’s value chain, the total pool of key players, market classification, and segmentation from the market and technology-oriented perspectives.
Primary Research
In the primary research process, various supply and demand sources were interviewed to obtain qualitative and quantitative information for this report. The primary sources from the supply side included industry experts, such as Chief Executive Officers (CEOs), Vice Presidents (VPs), marketing directors, technology and innovation directors, and related key executives from various key companies and organizations operating in the Middle East & Africa (MEA) Operational Technology (OT) security market.
After the complete market engineering (calculations for market statistics, market breakdown, market size estimations, market forecasting, and data triangulation), extensive primary research was conducted to gather information and verify and validate the critical numbers arrived at. Primary research was also undertaken to identify the segmentation types, industry trends, competitive landscape of middle east & africa (MEA) OT security solutions offered by various market players, and fundamental market dynamics, such as drivers, restraints, opportunities, challenges, industry trends, and key player strategies.
In the complete market engineering process, the top-down and bottom-up approaches and several data triangulation methods were extensively used to perform the market estimation and market forecasting for the overall market segments and subsegments listed in this report. Extensive qualitative and quantitative analysis was performed on the complete market engineering process to list the key information/insights throughout the report.
To know about the assumptions considered for the study, download the pdf brochure
Market Size Estimation
Top-down and bottom-up approaches were used to estimate and validate the size of the Middle East & Africa (MEA) Operational Technology (OT) security market and the size of various other dependent sub-segments in the overall Middle East & Africa (MEA) Operational Technology (OT) security market. The research methodology used to estimate the market size included the following details: key players in the market were identified through secondary research, and their market shares in the respective regions were determined through primary and secondary research. This entire procedure included the study of the annual and financial reports of the top market players, with extensive interviews conducted for key insights from the industry leaders, such as CEOs, VPs, directors, and marketing executives.
All percentage splits and breakdowns were determined using secondary sources and verified through primary sources. All possible parameters that affect the market covered in this research study were accounted for, viewed in extensive detail, verified through primary research, and analyzed to get the final quantitative and qualitative data. This data was consolidated and added with detailed inputs and analysis from MarketsandMarkets.
Middle East & Africa (MEA) Operational Technology (OT) Security Market : Top-Down and Bottom-Up Approach

Data Triangulation
After arriving at the overall market size using the market size estimation processes explained above, the market was split into several segments and subsegments. The data triangulation and market breakup procedures were employed, wherever applicable, to complete the overall market engineering process and arrive at the exact statistics of each market segment and subsegment. The data was triangulated by studying various factors and trends from both the demand and supply sides.
Market Definition
According to MnM, Operational Technology (OT) Security is the use of hardware and software to monitor, detect, and control physical devices, processes, and events in enterprises. Operational Technology (OT) Security includes a broad array of security solutions, such as NGFWs, IAM, and SIEM, among others, which are used to protect people, physical assets, processes, and information.
Stakeholders
- Government bodies and public safety agencies
- Project managers
- Developers
- Business analysts
- Quality assurance (QA)/test engineers
- OT security specialists
- OT security solution and service providers
- Consulting firms
- Third-party vendors
- Investors and venture capitalists
- System integrators (SIs)
- Technology providers
Report Objectives
- To define, describe, and forecast the Middle East & Africa (MEA) Operational Technology (OT) security market based on offering, deployment mode, organization size, vertical, and region
- To analyze the subsegments of the market concerning individual growth trends, prospects, and contributions to the overall market
- To provide detailed information related to the primary factors (drivers, restraints, opportunities, and challenges) influencing the growth of the market
- To analyze opportunities in the market for stakeholders by identifying high-growth segments of the market
- To profile the key players of the market and comprehensively analyze their market size and core competencies.
- To track and analyze competitive developments, such as product launches, mergers & acquisitions, partnerships, agreements, and collaborations in the Middle East & Africa (MEA) Operational Technology (OT) security market
Available Customizations
With the given market data, MarketsandMarkets offers customizations based on company-specific needs. The following customization options are available for the report:
Geographic Analysis as per Feasibility
- Further breakup of the Asia Pacific market into countries contributing 75% to the regional market size
- Further breakup of the North American market into countries contributing 75% to the regional market size
- Further breakup of the Latin American market into countries contributing 75% to the regional market size
- Further breakup of the Middle Eastern and African market into countries contributing 75% to the regional market size
- Further breakup of the European market into countries contributing 75% to the regional market size
Company Information
- Detailed analysis and profiling of additional market players (up to 5)
Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the Middle East & Africa (MEA) Operational Technology (OT) Security Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free Customisation














Growth opportunities and latent adjacency in Middle East & Africa (MEA) Operational Technology (OT) Security Market