
Non-Human Identity (NHI) Access Management Market
Non-Human Identity (NHI) Access Management Market by Identity Type (Application-to-Application & API Identities, Machine & Device Identities, Cryptographic Access Identities), Deployment Mode (Cloud, On-Premises, Hybrid) - Global Forecast to 2030




OVERVIEW
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
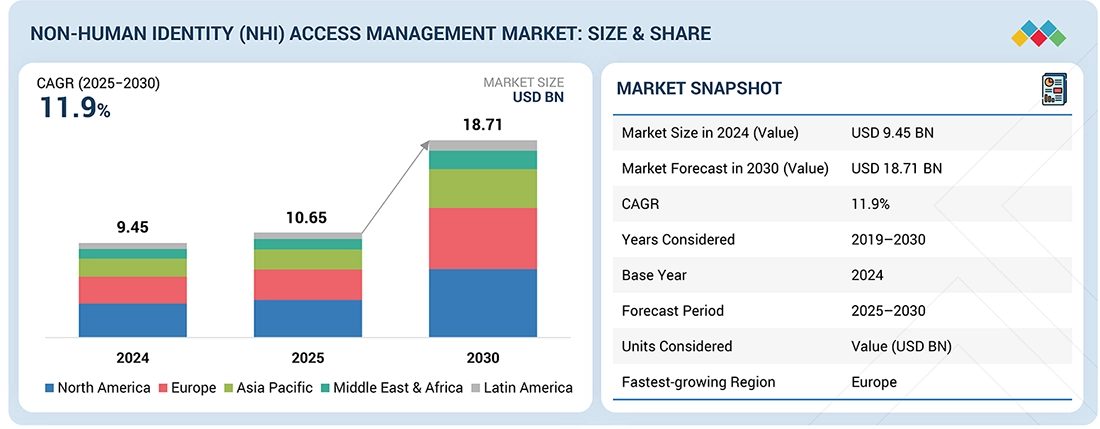
The non-human identity (NHI) access management market will expand rapidly over the next five years from approximately USD 9.45 billion in 2024 to reach USD 18.71 billion in 2030 at an CAGR of 11.9%, driven primarily by increased use of cloud workloads, application programming interfaces (APIs), automated applications, and machine-to-machine (M2M) communications, resulting in a dramatic increase in the number of NHI. Organizations are increasingly implementing authentication, authorization, and policy-based access control techniques to secure their service accounts (e.g., workloads, containers, and devices). Additionally, demand will remain high as enterprises continue to seek ways to minimize credential exposure and enforce the principle of least privilege for access to dynamic information technology (IT) environments through the use of NHI access management solutions.
KEY TAKEAWAYS
-
BY REGIONThe North America region accounted for the highest market share in 2025.
-
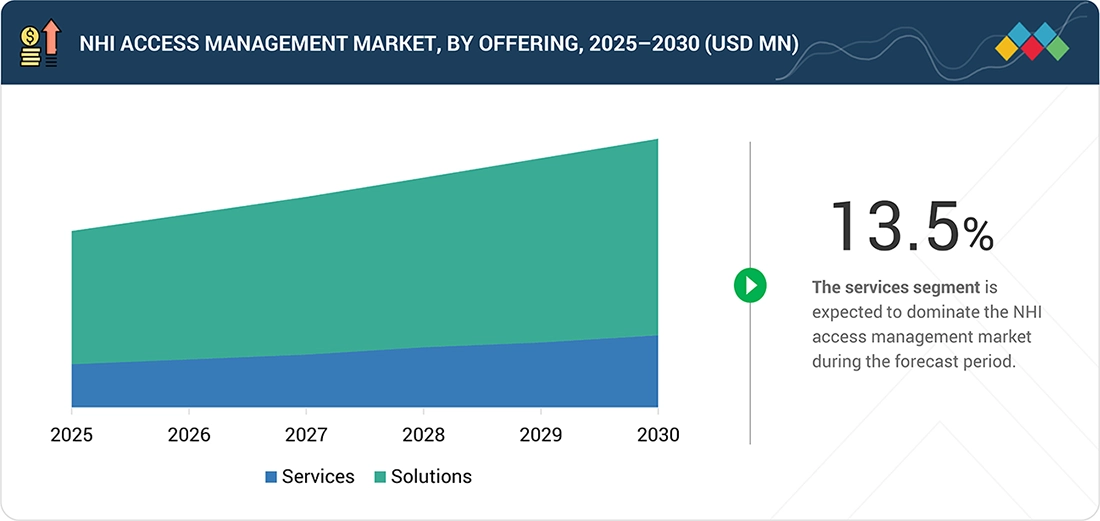
BY OFFERINGBy offering, the services segment is projected to register the highest CAGR of 13.5% during the forecast period, driven by growing demand for consulting, integration, and managed services for NHI access deployments.
-
BY IDENTITY TYPEBy identity type, Application-to-Application and API identities are projected to grow at the fastest CAGR of 13.2% from 2025 to 2030, supported by increasing automation and machine-to-machine interactions.
-
BY DEPLOYMENT MODEBy deployment mode, the hybrid segment is projected to register a highest CAGR of 12.5%.
-
BY VERTICALBy vertical, the IT & ITeS segment is expected to grow at the highest CAGR of 13.0% during the forecast period, supported by widespread adoption of cloud-native applications, APIs, and automated workflows.
-
COMPETITIVE LANDSCAPE - KEY PLAYERSThe key companies involved in NHI access management are: Microsoft, AWS, Google, Okta, Ping Identity, IBM, Oracle, CyberArk, Red Hat, Thales and Entrust. These vendors provide comprehensive IAM and access management solutions that can secure access for non-human users in a range of environments including cloud, hybrid and traditional data centres (enterprise), which is why they are some of the most used access control software by large companies.
-
COMPETITIVE LANDSCAPE - STARTUP & SMEAembit, HashiCorp, and Kong are all part of the NHI access management provider ecosystem targeting the small and mid-sized business (SMB) and start-up segments. They are continuing to be widely adopted by SMBs and start-ups within the following specific areas of NHI access: workspace identity access, cryptographic access control, and API access level permissioning.
The NHI access management market is gaining traction as multiple companies struggle with visibility and control over the increasing number of machine identities in IT environments. Companies are deploying more short-lived credentials, dynamic workloads, and automated system interactions, requiring customers to enhance access control in ways beyond traditional access management methods that have generally been focused on employees. Buyers are seeking a centralized policy control, secure machine authentication, and reduced operational risk from orphaned and/or over-privileged NHI. Adoption is accelerating in complex enterprise environments where scale, automation, and system reliability are vital components of doing business.
TRENDS & DISRUPTIONS IMPACTING CUSTOMERS' CUSTOMERS
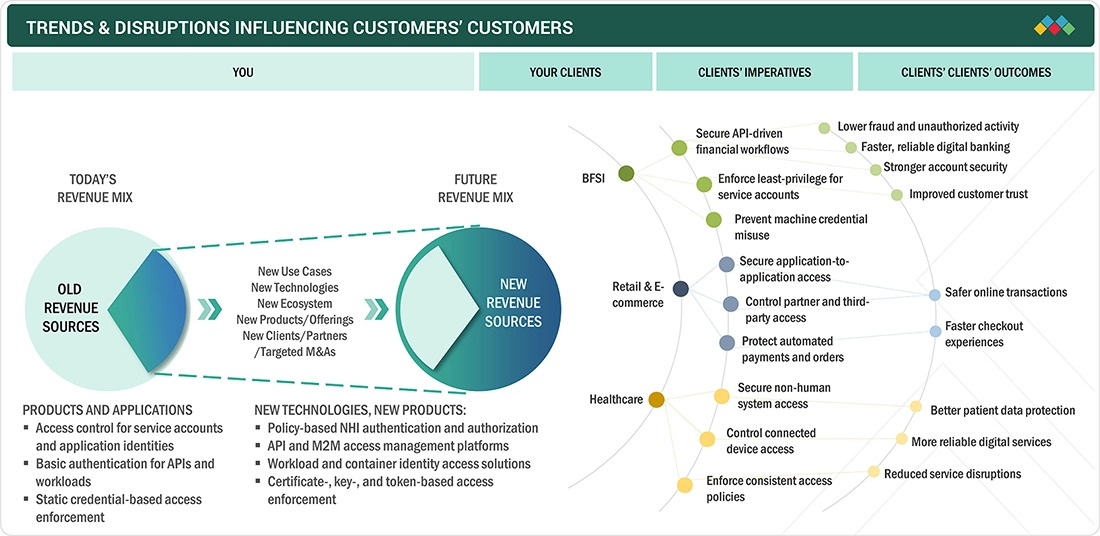
The figure illustrates the shift in revenue mix in the NHI access management market from basic access controls toward policy-driven solutions for non-human identities. Current demand is driven by access control for service accounts, APIs, and workloads, while future growth will come from API and machine-to-machine access management, workload and container identities, and cryptographic access enforcement. Adoption is strongest across BFSI, retail & e-commerce, and healthcare, where securing automated workflows and non-human system access is becoming critical.
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
MARKET DYNAMICS
Level
-
Rapid expansion of APIs, workloads, and machine-to-machine interactions

-
Rising security incidents linked to over-privileged non-human identities
Level
-
Absence of standardized access controls for non-human identities
-
Higher integration effort across legacy and hybrid IT environments
Level
-
Growing demand for policy-based and automated NHI access enforcement
-
Increased adoption of cloud-native and containerized workloads
Level
-
Limited visibility into dynamic and ephemeral non-human access
-
Enforcing consistent policies across multi-cloud and on-prem systems
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
Driver: Expansion of APIs, workloads, and machine-to-machine interactions
The adoption of NHI access management is driven by the rapid increase in APIs, cloud workloads, containers, and automated system interactions across enterprises. As organizations rely more on machine-to-machine communication to support digital services and application integration, the number of non-human identities has increased significantly. This has expanded the non-human attack surface, making traditional IAM controls inadequate. As a result, enterprises are adopting dedicated access controls to secure non-human identities.
Restraint: Absence of standardized access controls for non-human identities
The lack of standardized access control frameworks for non-human identities remains a key restraint for market adoption. Non-human identities differ widely in structure, lifespan, and authentication methods, leading to inconsistent access enforcement across environments. Organizations often depend on fragmented tools or custom approaches, which increases deployment complexity. This slows large-scale implementation of NHI access management solutions.
Opportunity: Demand for policy-based and automated NHI access enforcement
The growing shift toward policy-based and automated access controls presents a major opportunity for the NHI access management market. Enterprises are moving away from static credentials and manual controls toward dynamic access models that support automation. Policy-driven enforcement enables consistent and scalable access control for non-human identities across cloud and hybrid environments. This is driving demand for advanced NHI access management solutions.
Challenge: Limited visibility into dynamic and ephemeral non-human access
Maintaining visibility over dynamic and short-lived non-human identities is a key challenge in NHI access management. Cloud-native workloads and containers frequently create and remove identities, making access tracking difficult. Limited visibility increases the risk of unused or unmanaged credentials. Addressing this challenge requires continuous monitoring and real-time access enforcement, which adds operational complexity.
NON-HUMAN IDENTITY (NHI) ACCESS MANAGEMENT MARKET: COMMERCIAL USE CASES ACROSS INDUSTRIES
| COMPANY | USE CASE DESCRIPTION | BENEFITS |
|---|---|---|
 |
A large enterprise implemented Microsoft Entra ID to secure service accounts, APIs, and cloud workloads across Azure environments. The organization enforced policy-based authentication for non-human identities supporting automated applications and DevOps pipelines. | Improved control over non-human access, reduced credential misuse, consistent access enforcement across cloud workloads, and lower operational overhead |
 |
A global financial services firm used CyberArk to manage access for application service accounts and automated processes supporting core banking and backend systems. The solution enabled secure credential usage and controlled privileged non-human access. | Reduced risk of credential compromise, improved visibility into non-human access activity, and stronger enforcement of least-privilege policies |
 |
A digital commerce platform deployed Kong to secure API and application-to-application, access across microservices. The organization implemented centralized access control for machine-to-machine communication supporting payment and order management systems. | Safer API transactions, improved reliability of automated services, reduced unauthorized access, and better scalability of application integrations |
Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET ECOSYSTEM
The Non-Human Identity Access Management Market ecosystem includes providers of solutions and services that support authentication, authorisation and controlled access to non-human identities across hybrid and cloud environments. Secure access is provided to operations processes, service accounts, API interfaces, work loads, and devices to support organizations in securing their mission-critical and automated operations. With the rise in computer automation and machine-to-machine (M2M) interaction by regulated industries and digital-first industries, many organizations now use NHI access management systems.

Logos and trademarks shown above are the property of their respective owners. Their use here is for informational and illustrative purposes only.
MARKET SEGMENTS
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
NHI Access Management Market, By Offering
By offering, the solutions segment is estimated to dominate the NHI access management market during the forecast period, driven by higher adoption of authentication, authorization, and access control solutions for non-human identities.
NHI Access Management Market, By Identity Type
By identity type, the application and service identities segment is expected to account for the largest market share in 2025, driven by widespread use of service accounts, background processes, bots, and automated system identities across enterprise IT environments.
NHI Access Management Market, By Deployment Mode
By deployment mode, the cloud segment is expected to account for the largest market share in 2025, driven by widespread deployment of cloud-native applications, APIs, and automated workloads requiring scalable non-human access controls.
NHI Access Management Market, By Vertical
By vertical, the BFSI segment is projected to hold the largest market share in 2025, supported by extensive use of service accounts, APIs, and automated processes across core banking, payments, and digital financial platforms.
REGION
Europe to be fastest-growing region in global NHI access management market during forecast period
The NHI access management market in Europe is growing quickly due to an increased number of companies using cloud based software applications, implementing Application Programming Interfaces (APIs) as well as utilizing automated IT environments. In addition, due to more stringent regulations related to data protection and security and growing concerns about increased risk due to unmanaged non-human identities, many organizations are implementing stronger access controls on Service Accounts, workloads and machine to machine interactions. Organizations in regulated industries continue to purchase NHI access management systems for security and compliance purposes and to strengthen their operational resiliency.
NON-HUMAN IDENTITY (NHI) ACCESS MANAGEMENT MARKET: COMPANY EVALUATION MATRIX
Microsoft is one of the leading players in the NHI access management space, mainly because of its very broad IAM product offering as well as strong service account, API and workload security capabilities when using Cloud Services. Furthermore, Microsoft's integration of their IAM offerings into Cloud Native Platforms and ability to implement policy based access controls has led to increased adoption rates by enterprise size companies. Due to the increase in popularity of secure machine to machine communications, Kong's position as a growing leader in the market is increased with their concentration on both API and application to application access management, and building microservices, both of which are part of Kong's growth within this area of emerging vendor.
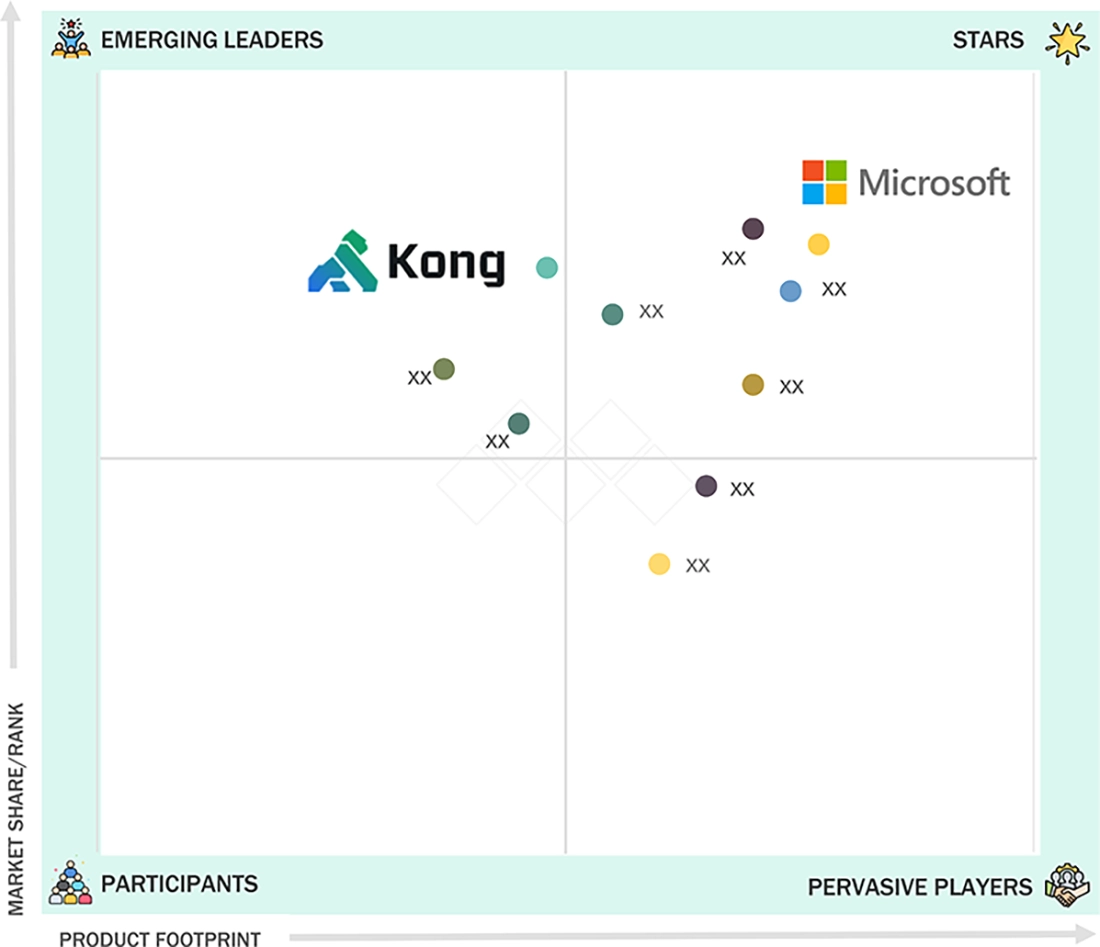
Source: Secondary Research, Interviews with Experts, MarketsandMarkets Analysis
KEY MARKET PLAYERS
- Microsoft (US)
- Amazon Web Services – AWS (US)
- Google (US)
- Okta (US)
- Ping Identity (US)
- IBM (US)
- Oracle (US)
- CyberArk (US)
- HashiCorp (US)
- Aembit (US)
- Red Hat (US)
- Thales (France)
- Entrust (US)
- Kong (US)
MARKET SCOPE
| REPORT METRIC | DETAILS |
|---|---|
| Market Size in 2024 (Value) | USD 9.45 Billion |
| Market Forecast in 2030 (value) | USD 18.71 Billion |
| Growth Rate | CAGR of 11.9% from 2025-2030 |
| Years Considered | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/Billion) |
| Report Coverage | Revenue forecast, company ranking, competitive landscape, growth factors, and trends |
| Segments Covered |
|
| Regions Covered | North America, Europe, Asia Pacific, Middle East & Africa, Latin America |
WHAT IS IN IT FOR YOU: NON-HUMAN IDENTITY (NHI) ACCESS MANAGEMENT MARKET REPORT CONTENT GUIDE
DELIVERED CUSTOMIZATIONS
We have successfully delivered the following deep-dive customizations:
| CLIENT REQUEST | CUSTOMIZATION DELIVERED | VALUE ADDS |
|---|---|---|
| Leading Solution Provider (US) | Product Analysis: NHI Access Management Solution Matrix providing an in-depth comparison of vendors’ capabilities, including non-human identity authentication, authorization and policy enforcement, API and machine-to-machine access control, workload and container identity access, cryptographic access mechanisms (certificates, keys, tokens), integration with cloud and hybrid environments, and deployment flexibility. |
|
RECENT DEVELOPMENTS
- October 2025 : Saviynt unveiled major AI-powered identity security capabilities, including expanded Identity Security Posture Management for unified governance of human, non-human, and AI identities.
- October 2025 : Microsoft added Delinea to its Security Store ecosystem, enhancing Microsoft Entra with privileged access management, AI-driven governance, and unified hybrid IAM capabilities.
- July 2025 : Okta acquired Axiom Security, expanding its identity security portfolio into SaaS security posture management and real-time identity threat detection to better support customers with cloud and identity risk analytics.
- June 2025 : IBM launched AskIAM, a generative AI capability within its Consulting Advantage platform to automate IAM workflows, streamline access requests, and strengthen identity protection with advanced AI support in hybrid and cloud environments.
- June 2025 : Ping Identity partnered with Island (the Enterprise Browser company) to incorporate device posture and browser context, supporting real-time Zero Trust decisions and stronger adaptive access controls.
Table of Contents

Need a Tailored Report?
Customize this report to your needs
Get 10% FREE Customization
Customize This ReportPersonalize This Research
- Triangulate with your Own Data
- Get Data as per your Format and Definition
- Gain a Deeper Dive on a Specific Application, Geography, Customer or Competitor
- Any level of Personalization
Let Us Help You
- What are the Known and Unknown Adjacencies Impacting the Non-Human Identity (NHI) Access Management Market
- What will your New Revenue Sources be?
- Who will be your Top Customer; what will make them switch?
- Defend your Market Share or Win Competitors
- Get a Scorecard for Target Partners
Custom Market Research Services
We Will Customise The Research For You, In Case The Report Listed Above Does Not Meet With Your Requirements
Get 10% Free Customisation














Growth opportunities and latent adjacency in Non-Human Identity (NHI) Access Management Market